Keeping up with the latest security challenges can feel like you are running a race that has endles 2023-11-30 00:21:52 Author: securityboulevard.com(查看原文) 阅读量:8 收藏
Keeping up with the latest security challenges can feel like you are running a race that has endless hurdles. From rapid advancements in technology – rendering old hardware obsolete – to increasingly stringent requirements and regulations, the time and costs can quickly become enormous.
Many of these challenges are related to the migration of compute, storage, and backup services to cloud services. Picture this, you have moved your databases to the cloud. But are you in control of your encryption keys? Do you know who has a copy or could access a copy?
Today’s solutions offer your organization a choice of how to most effectively secure your encryption keys. You can select a solution that allows your organization to secure your keys in an on-premise HSM or one that allows your organization to protect your keys via a secure connection to a cloud-based HSM with an HSM-as-a-Service (HSMaaS) offering such as Entrust’s nShield-as-a-Service solution.
Entrust recently partnered with TechValidate to conduct a survey to understand how companies view and are implementing HSMaaS solutions.
From On-Premise to the Cloud
For years, the best practice was to use an HSM deployed on-premise. Concerns about security of software based key storage, separation of keys, and sovereignty requirements made it the only viable option. Over time, as-a-service HSM offerings appeared in the market offering lower costs, and a level of security comparable to on-premise HSMs, with more flexibility and quicker implementation.
The Survey Says
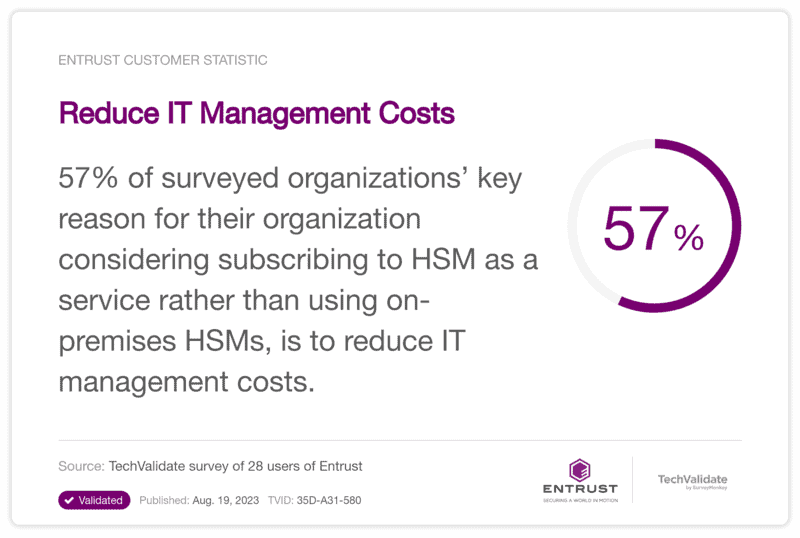
Today’s organizations are looking to save time and money. The survey showed that 57% of organizations said a key reason for considering subscribing to an HSMaaS offering is to reduce IT management costs. Further, 69% of respondents said that their organizations would realize reduced spend on physical infrastructure. The next closest benefit noted was improved efficiency with 46% of the respondents selecting that benefit.
The focus on saving time and reducing expenses has also been a significant driver of cloud adoption. With the rise of cloud service providers, as-a-service-HSM offerings evolved even further. Leading cloud service providers offer their own unique approach to securing your encryption keys. While these offerings provide convenience and cost-effective solutions, they do not always meet internal security requirements set by some organizations adding further to the complexity involved when deciding how to store your encryption keys.
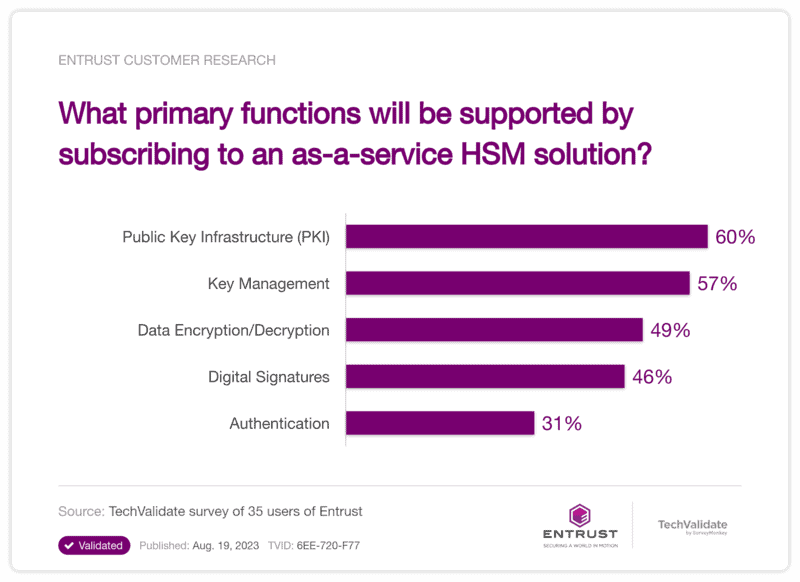
In addition to saving time and money, HSMaaS solutions like Entrust nShield-as-a-Service provide the same level of support for a wide range of applications. This is something that was also reflected in the survey results. Respondents indicated that once onboarded, they would leverage an HSMaaS solution for a variety of functions.
The top functions ranked were public key infrastructure (PKI), which was mentioned by 60% of respondents followed by key management which was selected by 57% of respondents. Data encryption/decryption and digital signatures were also mentioned by nearly half of the respondents (49%). These results reinforce the similarities in functionality between on-premise HSM and HSMaaS offerings.
Important Cloud Key Management Considerations
Saving time and money are necessary criteria when considering implementing an HSMaaS solution. However, they are not the only considerations you should have when deciding what as-a-service HSM offering to use when storing your encryption keys. It is important to also consider:
- Security – Make sure you understand how the HSMaaS offering works. Are you sharing the cloud-based HSM with other users or is it for your exclusive use? This is often referred to as single-tenancy vs multi-tenancy. You must ensure that you chose the right solution to match your risk profile and requirements.
- Sovereignty of keys. Can the HSMaaS provider guarantee what country or region your keys will physically stored in? Will you be compliant with the regulations affecting your organization?
- Integrations and the compatibility of the key management software with other vendors. Does it integrate with the other products and services used by your organization?
- Ease of comprehensive key management for the entire organization. Does the solution give you the ability to rotate, generate, discard, and easily access information required during an audit?
Conclusion
When evaluating these considerations and HSMaaS solutions, partnering with a company that understands your holistic security and encryption needs will simplify this process. While cost is always a driving factor, ensuring you are in control of your keys is the most important. Ensuring where your keys are stored for key sovereignty requirements, the available integrations and the key management capabilities need to be carefully reviewed. The right keys need to be stored in the right places, using a solution that will protect your business and significantly enhance your organization’s security.
To learn more about HSM-as-a-Service and how Entrust can help you save capital expenditures, maintain control of your critical keys, and strengthen the security of your data, visit the Entrust website.
The post Four considerations when selecting as-a-Service Hardware Security Module solutions to secure your encryption keys appeared first on Entrust Blog.
*** This is a Security Bloggers Network syndicated blog from Entrust Blog authored by Andrew Tweedie. Read the original post at: https://www.entrust.com/blog/2023/11/four-considerations-when-selecting-as-a-service-hardware-security-module-solutions-to-secure-your-encryption-keys/
如有侵权请联系:admin#unsafe.sh
