Bluetooth technology has become an integral part of our daily lives, from connecting our smartp 2023-11-28 17:1:58 Author: www.mobile-hacker.com(查看原文) 阅读量:46 收藏
![]()
Bluetooth technology has become an integral part of our daily lives, from connecting our smartphones to our cars and headphones to sharing files between devices. However, as with any wireless technology, Bluetooth is vulnerable to hacking attempts. In this blog post, we will discuss the various methods hackers use to exploit Bluetooth technology and the steps you can take to protect yourself and stay safe. So, whether you’re a casual user or a mobile hacker, this post will provide you with the knowledge and tools you need to stay safe and secure in the world of Bluetooth.
Bluetooth Arsenal
This is a collection of tools that allows you to perform various tests using Bluetooth such as recon, spoof, listen to or inject audio to devices. So far, it was necessary to have external and kernel supported Bluetooth dongle connected to device using OTG adapter. However, currently lates Kali NetHunter version 2022.4 supports some internal Bluetooth chips as well.
When you are using Bluetooth Arsenal for the first time, you have to Setup and then Update it first. These options are in top right corner, if you tap on three dots.
If you have an external adapter, plugin it to your Android using OTG adapter. If it is supported, it should appear in Bluetooth interface as hci0.
If you can’t see it there, then you must enable it manually. This method worked for one of my dongles that were supported, but not enabled by NetHunter.
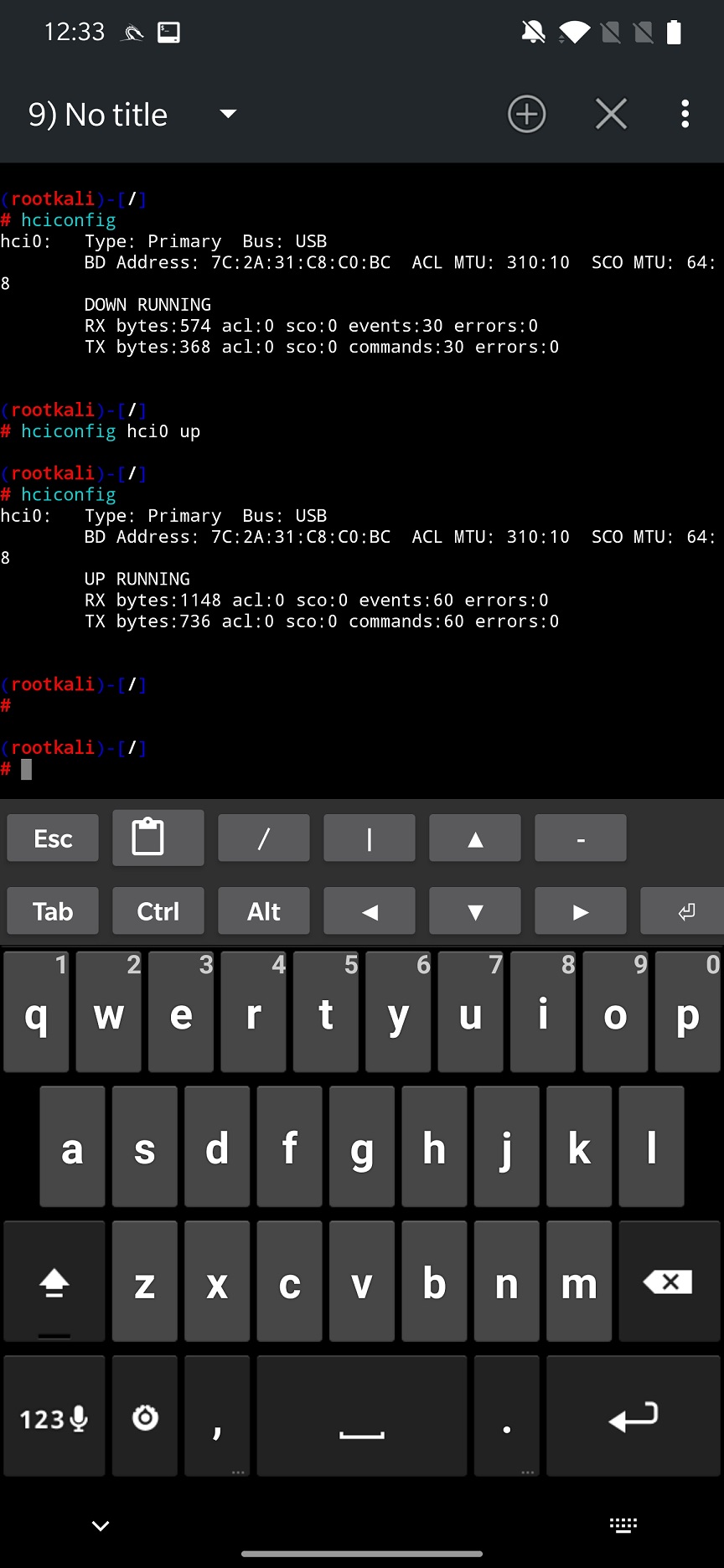
Open NetHunter Terminal app, and type hciconfig command to get information about hci devices. If it appears, try to enable it using hciconfig hci0 up as you can see in Figure 1. If you restart NetHunter app, newly started Bluetooth interface should be there.
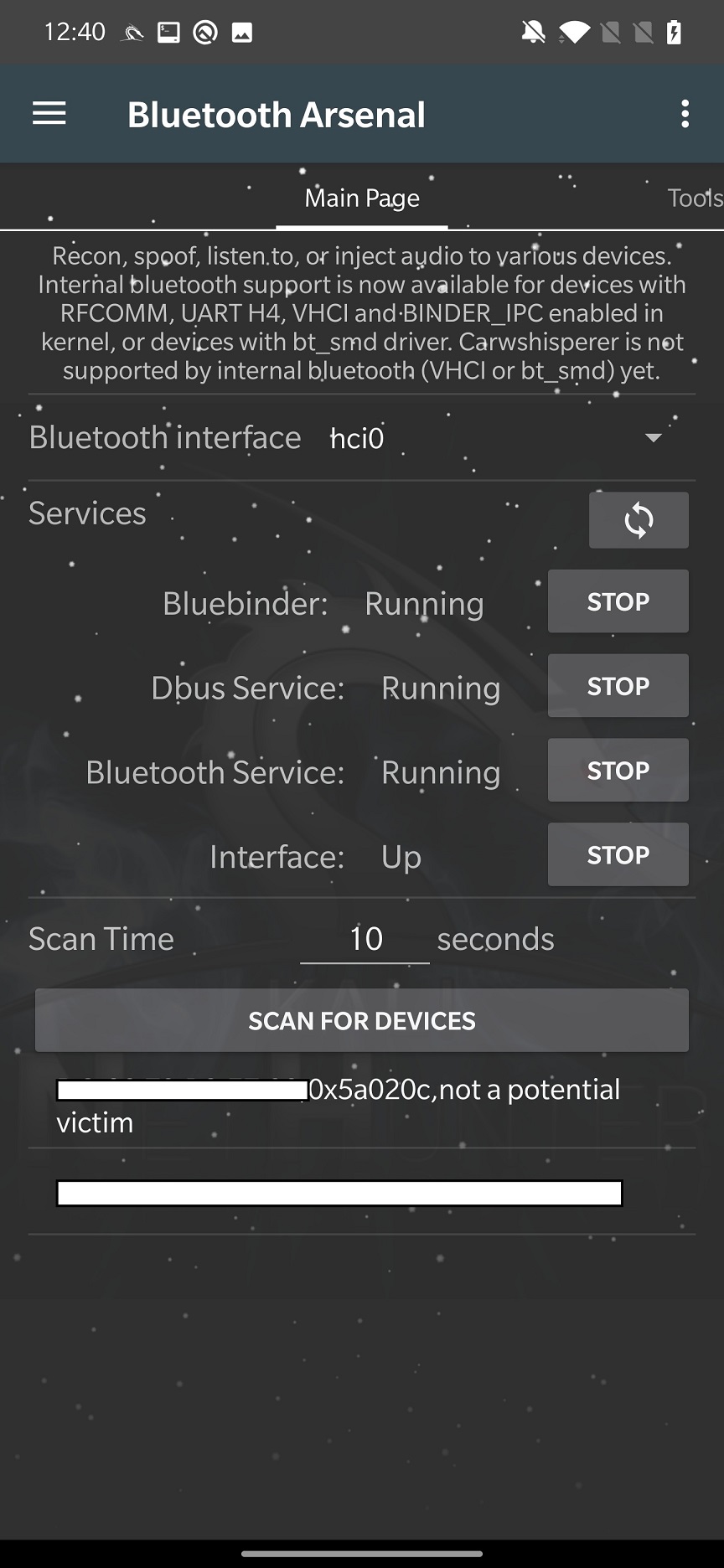
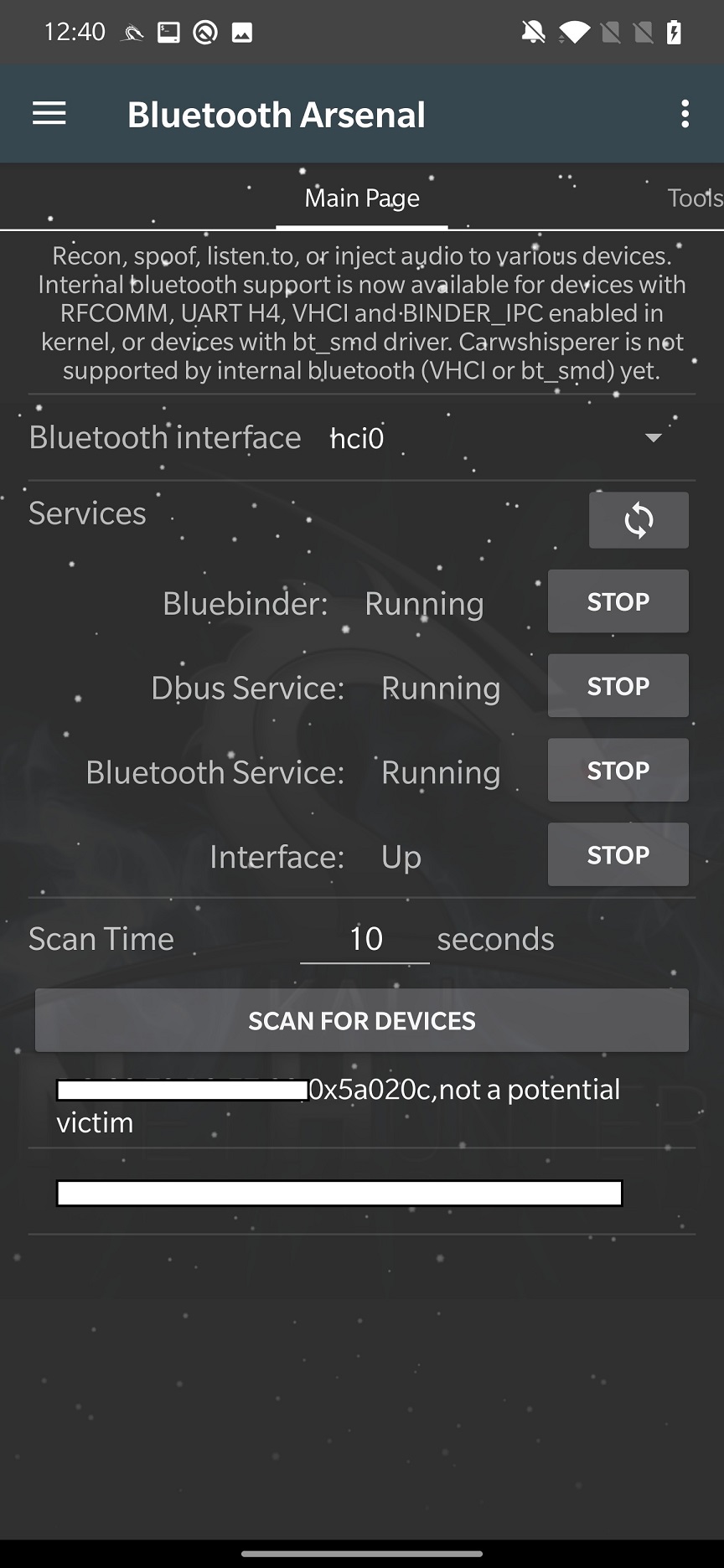
For internal Bluetooth, you first need to start all the services such as Bluebinder, Dbus Service, Bluetooth Service and Interface for an adapter to appear. Once you select it in interface, you can SCAN FOR DEVICES. The arsenal can scan only for Bluetooth not Bluetooth Low Energy (BLE) devices, which means your gadgets and IoT’s will not be discovered. You can see scan result in Figure 2.
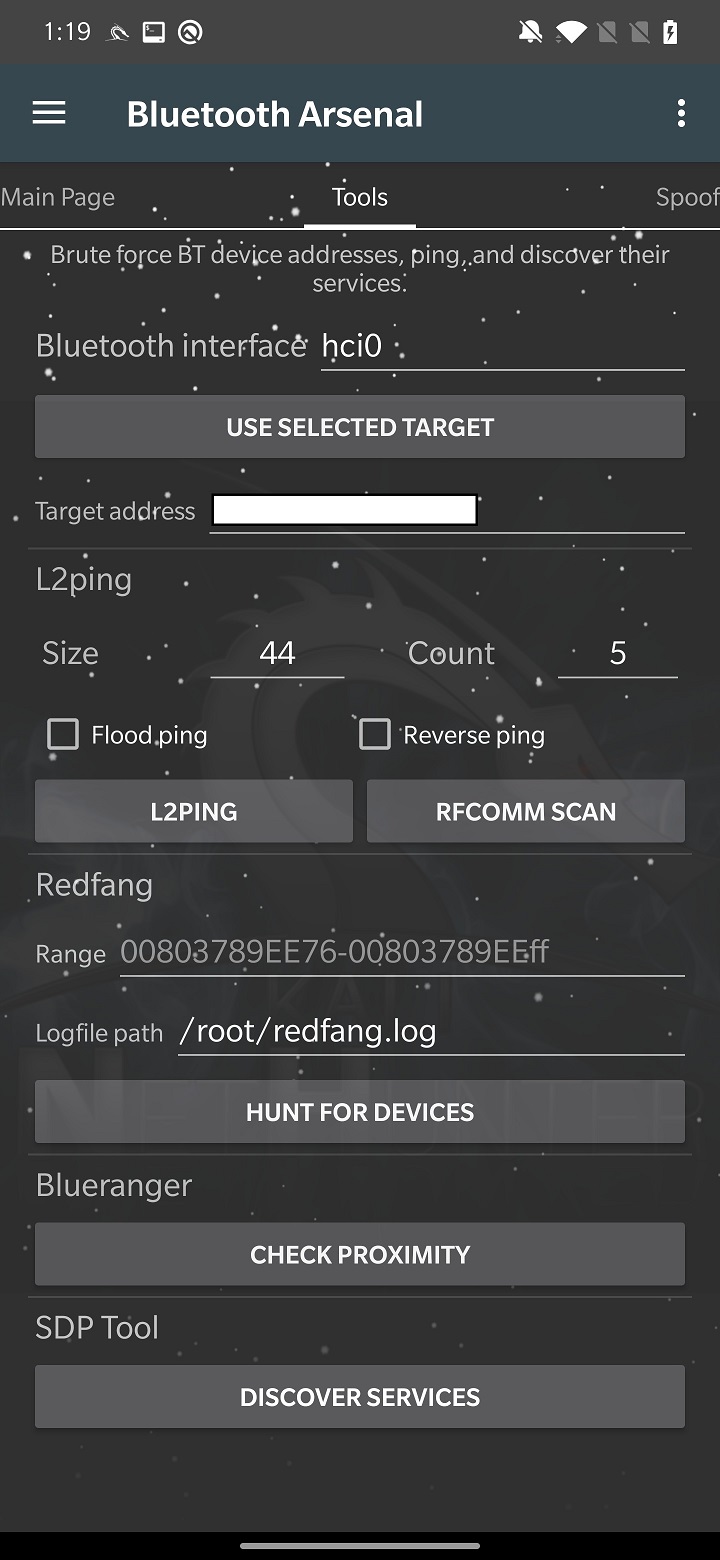
From the scan results, you can select a targeted device, and move to Tools tab.
Tools
In Tools tab you must either manually enter targeted device MAC address or tap on USE SELECTED TARGET from previous tab. Here you can setup and run tools such as L2ping, Redfang, Blueranger and SDP Tool.
L2ping
This is a ping flood tool that can start Denial-of-Service (DoS) attack. It will generate packet with custom size and count to be send to a targeted device. As a result, device will be flooded and might crash.
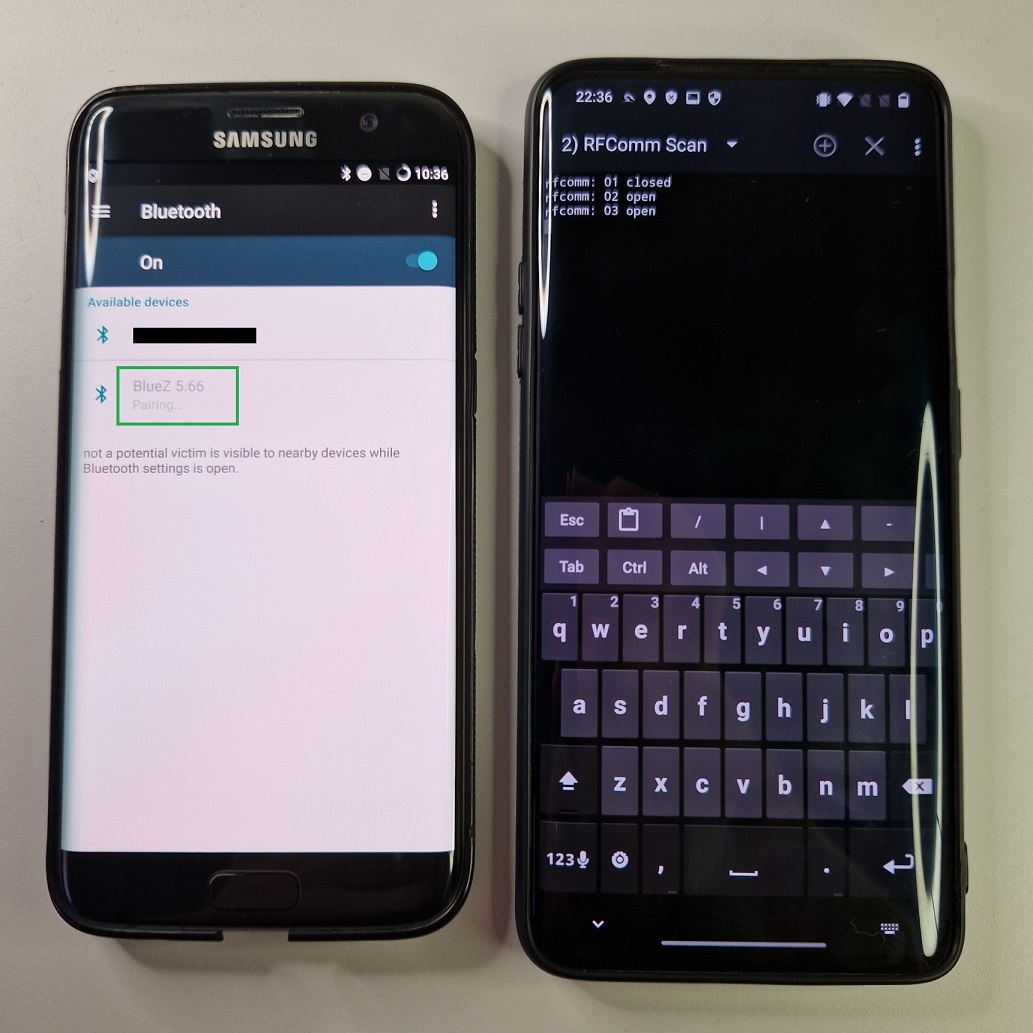
RFCOMM SCAN tries to search for open RFCOMM channels by scanning certain range. Altogether the are 30 channels. RFCOMM scanning is like a port scanner but for Bluetooth. It is making a complete connection to each channel. The owner of the targeted device is prompted to allow it and may even be required to enter a password if it reaches a channel that requires additional authentication. The socket connection is terminated if the owner decides not to approve the connection.
During my test, I was able to partially use the rfcomm_scan tool, but only if targeted device was scanning for Bluetooth devices. Then my targeted device received a pairing and permission request.
Targeted device is already selected by the attacker by tapping on the USE SELECTED TARGET button. When we run the attack by launching RFCOMM SCAN button, new device – be default called BlueZ 5.66 – appears as newly discovered device. By the way, if you would like to change the name of the spoofed device can be modified in Spoof tab. When targeted device tries to pair with it, rfcomm starts to scan, see Figure 4.
In some cases, it might even request to access messages or other permissions, see Figure 5.
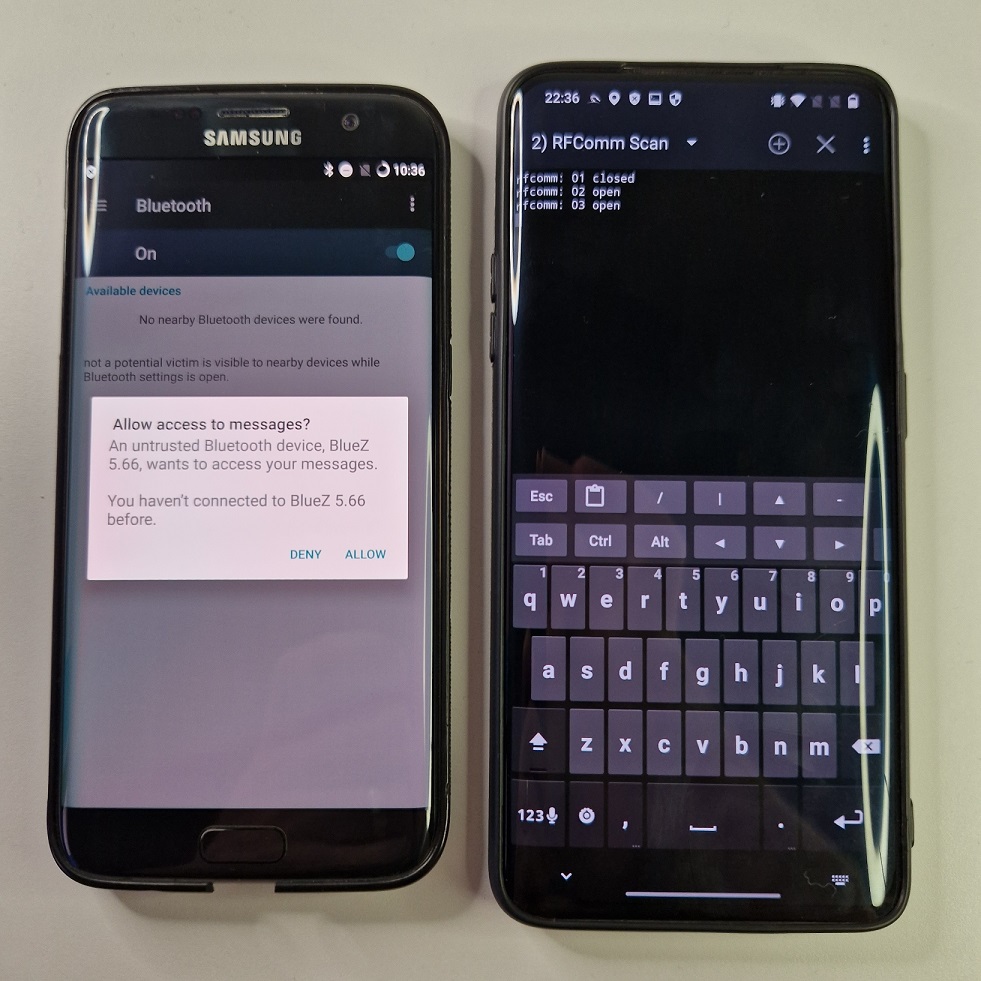
It seems very dangerous, but in all my test cases I wasn’t able to actually exploit this vulnerability. Most of the time – during the attack – Android crashed.
Mobile hacker would allow the NetHunter to connect to a Bluetooth device, simultaneously as the user. As a result, it might either crash the target or you take control of it.
Redfang
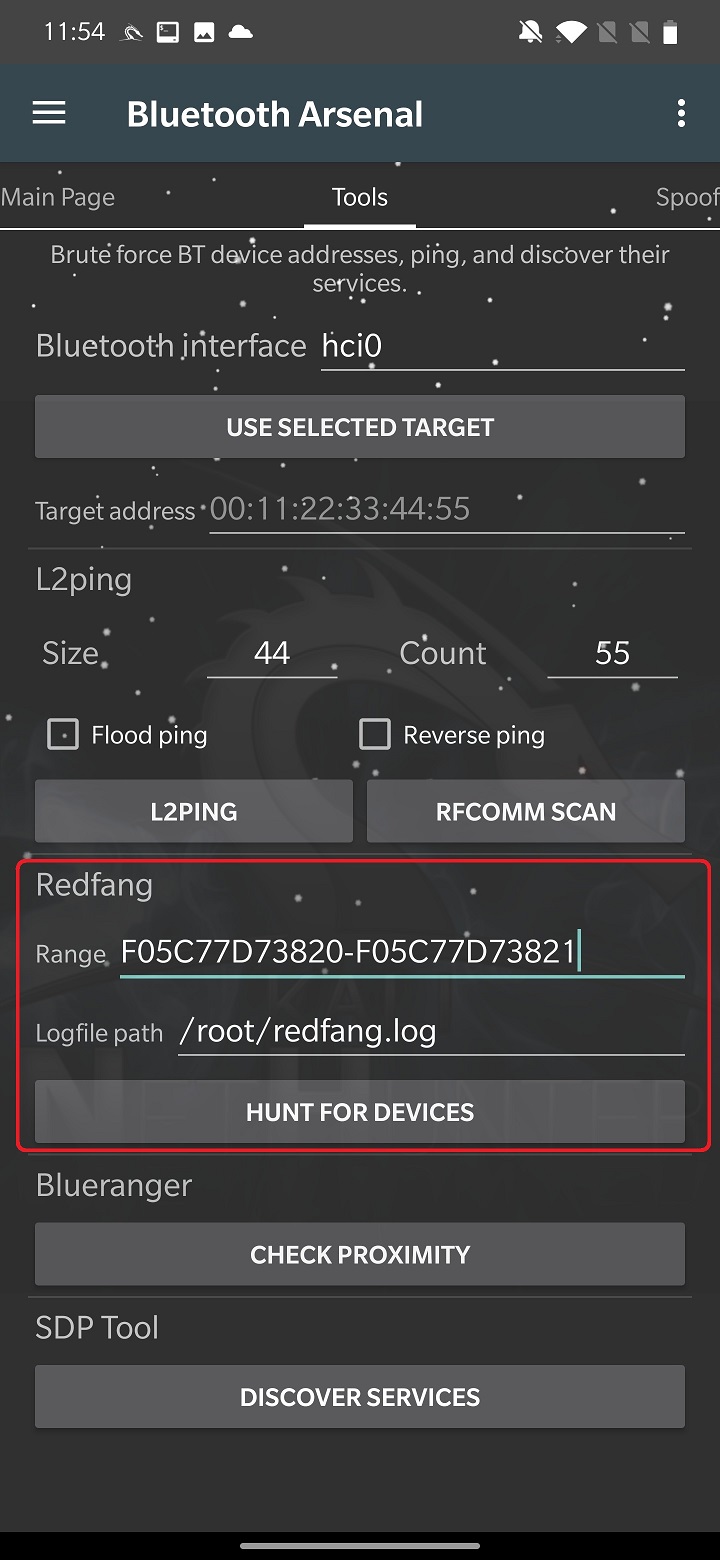
Bluetooth devices have two modes: visible and not visible. Redfang tool focuses on non-visible devices using bruteforce method. It tries to connect to the range of user defined MAC addresses to obtain detailed device information. This information is then stored in redfang.log file.
To launch a Bluetooth recon, you must set the range of MAC addresses to scan and file path to a log output of the scan, default is /root/redfang.log. When you start to HUNT FOR DEVICES, redfang will try to bruteforce each MAC address in the range to discover non-visible Bluetooth devices as you can see in Figure 6.
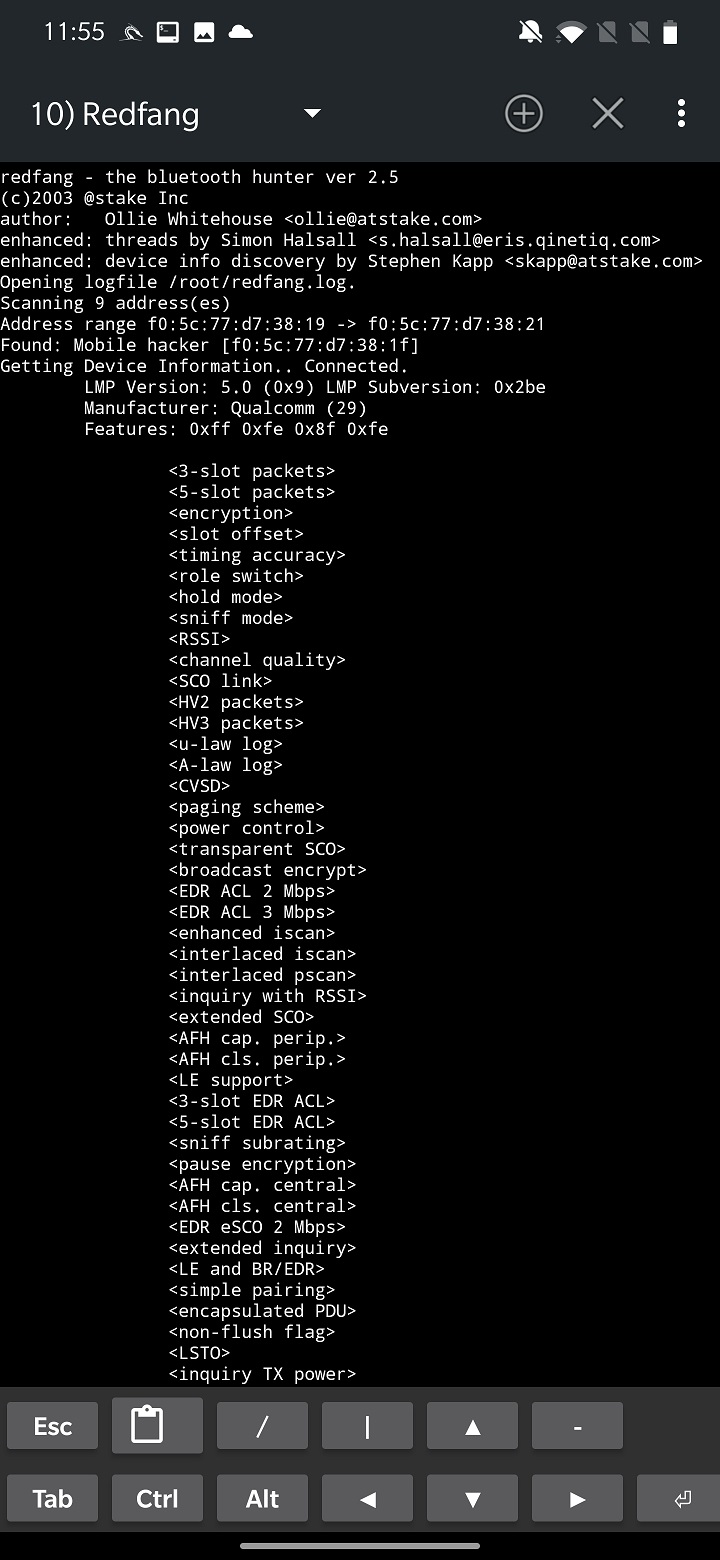
During my tests, when it discovered a devices, it displayed its information and crashed, so it wouldn’t continue in further bruteforce scan.
Blueranger
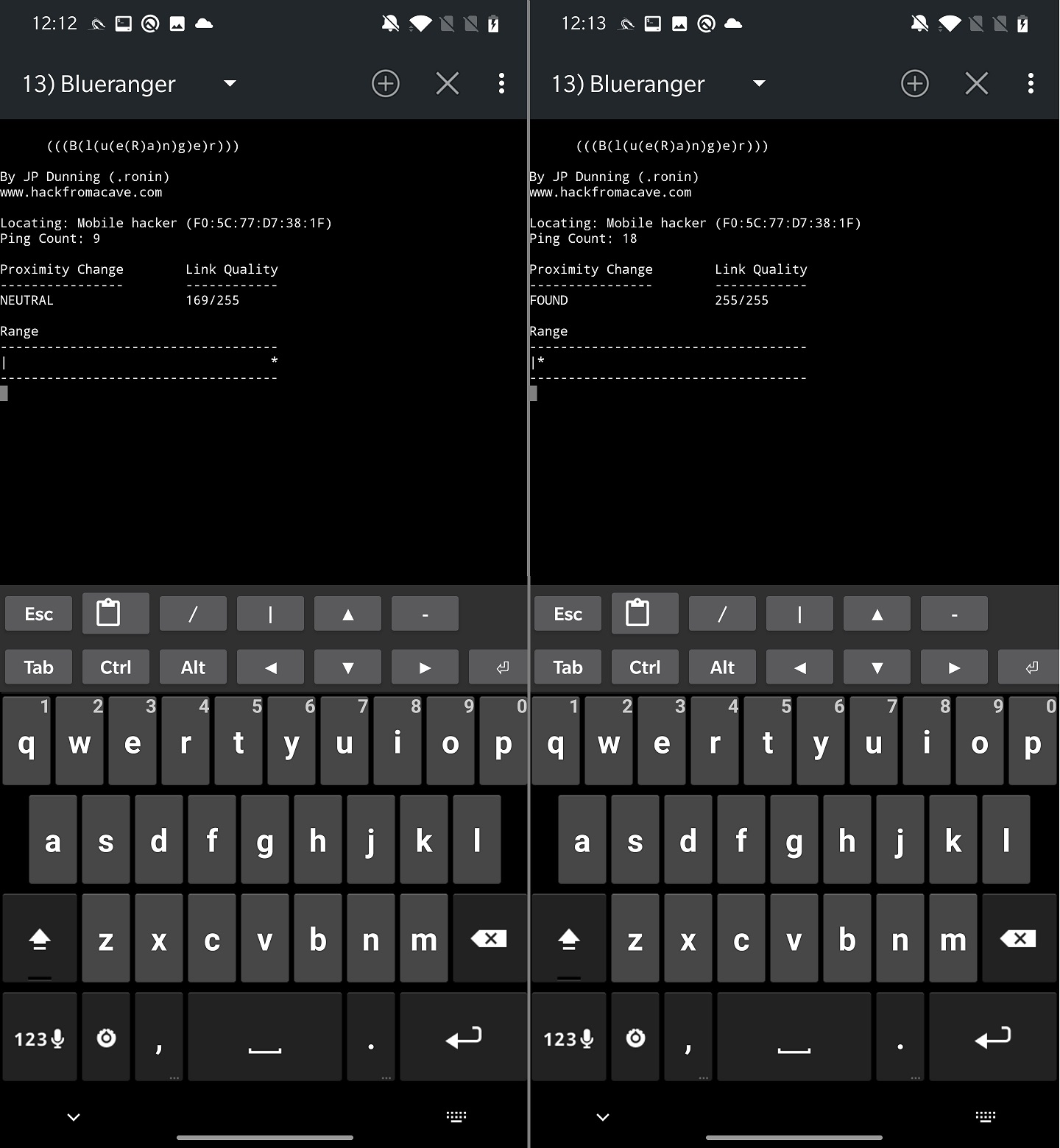
BlueRanger script tries to locate the distance of targeted Bluetooth device. This is done by sending l2cap pings, as we saw in previous tool, to identify a link quality. If the quality is higher, device is closer.
By taping on CHECK PROXIMITY button, you will start the device range analysis as you can see in Figure 8.
SDP Tool
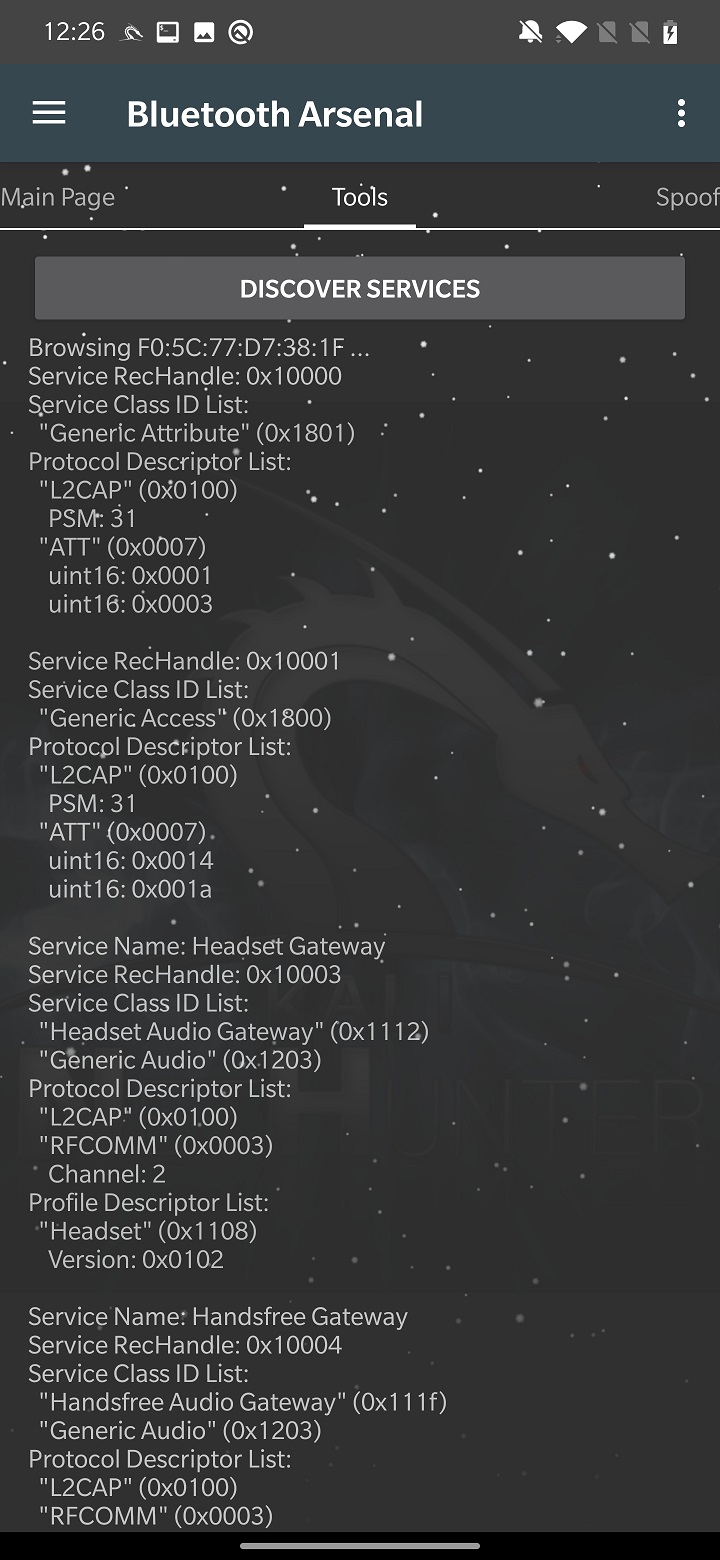
Functionality of SDP tool is to perform Service Discovery on targeted device. It will enumerate all running services to find open one. The result of the scan is displayed under the DISCOVER SERVICES button, as demonstrated on Figure 9.
From Tools tab, continue with Spoof.
Spoof
For spoofing Bluetooth device, NetHunter uses tool called Spooftooph. Its goal is to clone or spoof device name, class and MAC address. Result of spoofing should, allows Bluetooth device to hide in plain site, whatever that means. If you spoof or clone a Bluetooth device, you can’t interact with it such as receive connection, pair with a device, or trigger any type of phishing.
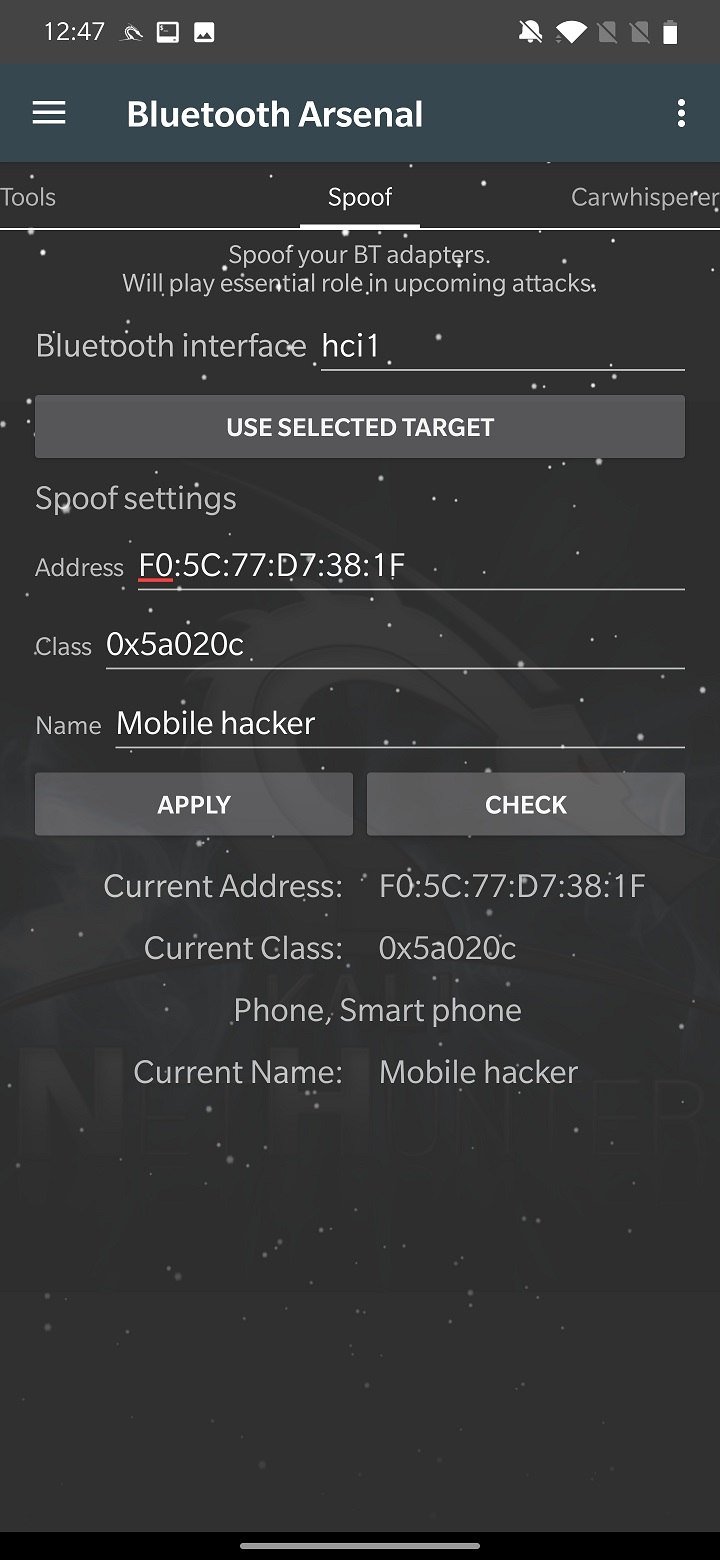
From settings, you need to select Bluetooth interface. In my case, internal hci0 wasn’t supported so I used external adapter that is identified as hci1. Set the target to spoof or clone by USE SELECTED TARGET, that we set from Main Page or type the MAC address, class and name manually. Start spoofing using APPLY button. CHECK button will summarize the spoof settings, as you can see in Figure 10.
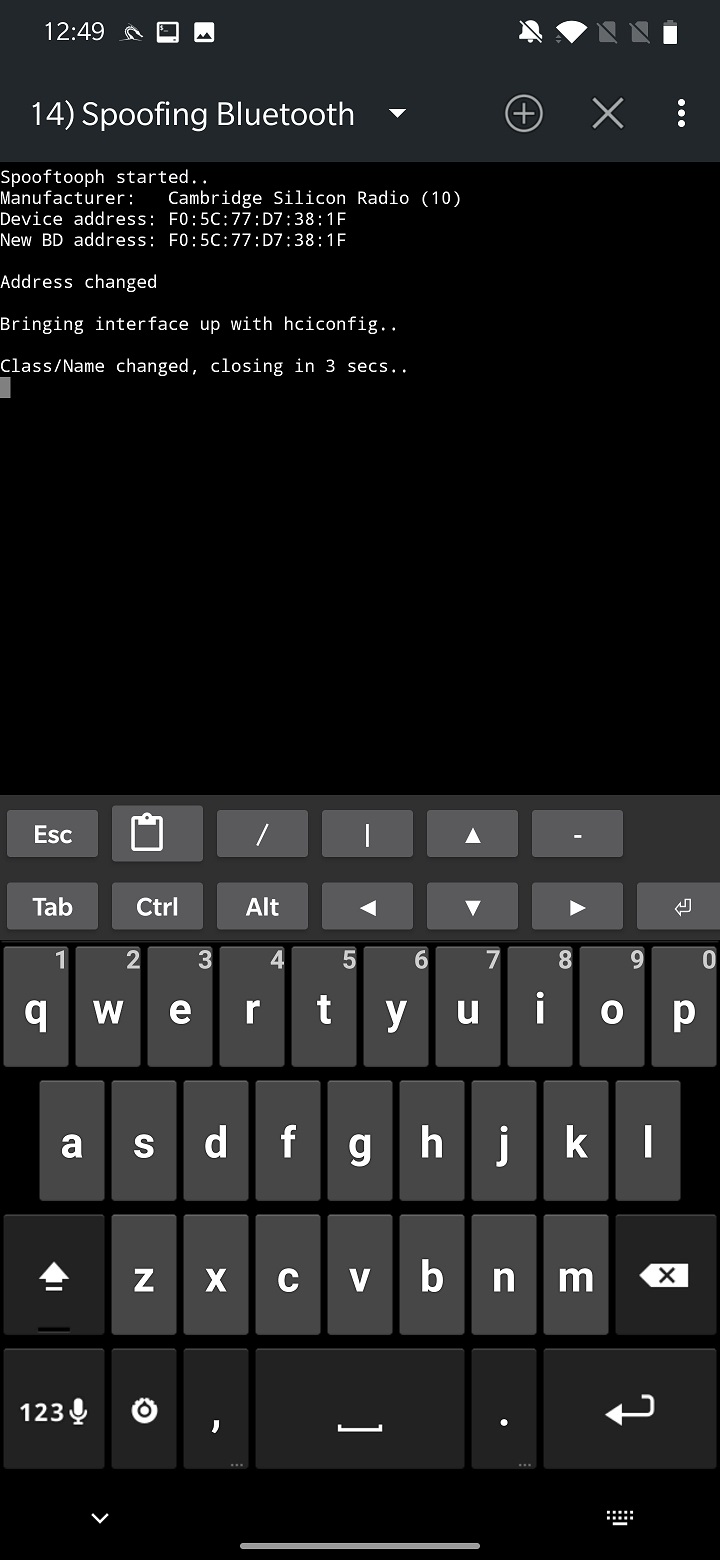
Unfortunately, I couldn’t successfully spoof any of my devices. The tool didn’t crash, rather closed after few seconds without any error.
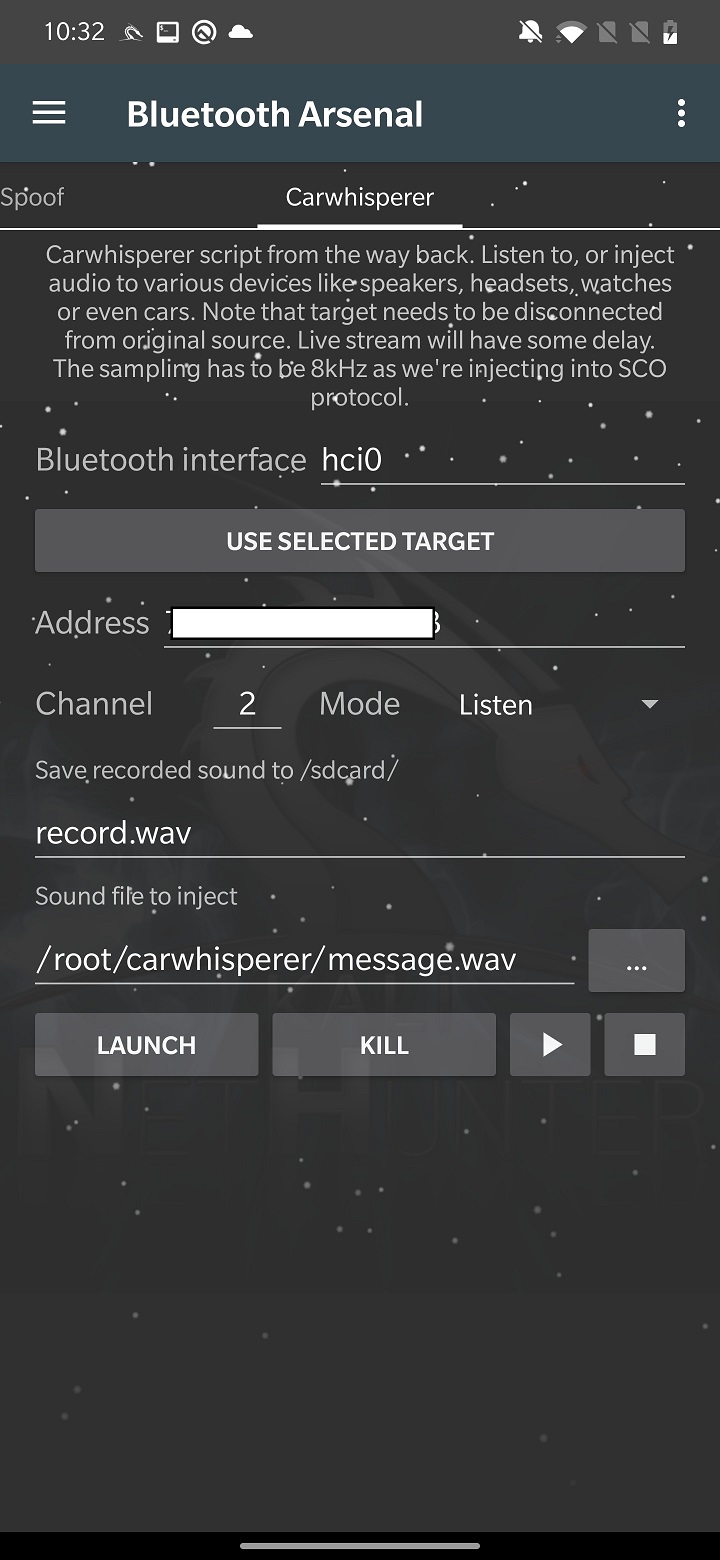
Carwhisperer
This tool is a proof-of-concept from 2005, that allows to either listen audio from headset’s microphone or inject custom sound into car speaker, headset, speakers etc. This is possible because these devices use common security pairing code such as “0000” or “1234”. It connects to a device and opens a control connection. The carwhisperer begins transmitting sounds to the headset and recording audio from it as soon as a connection has been made. It allows you to now inject audio data into the targeted devices.
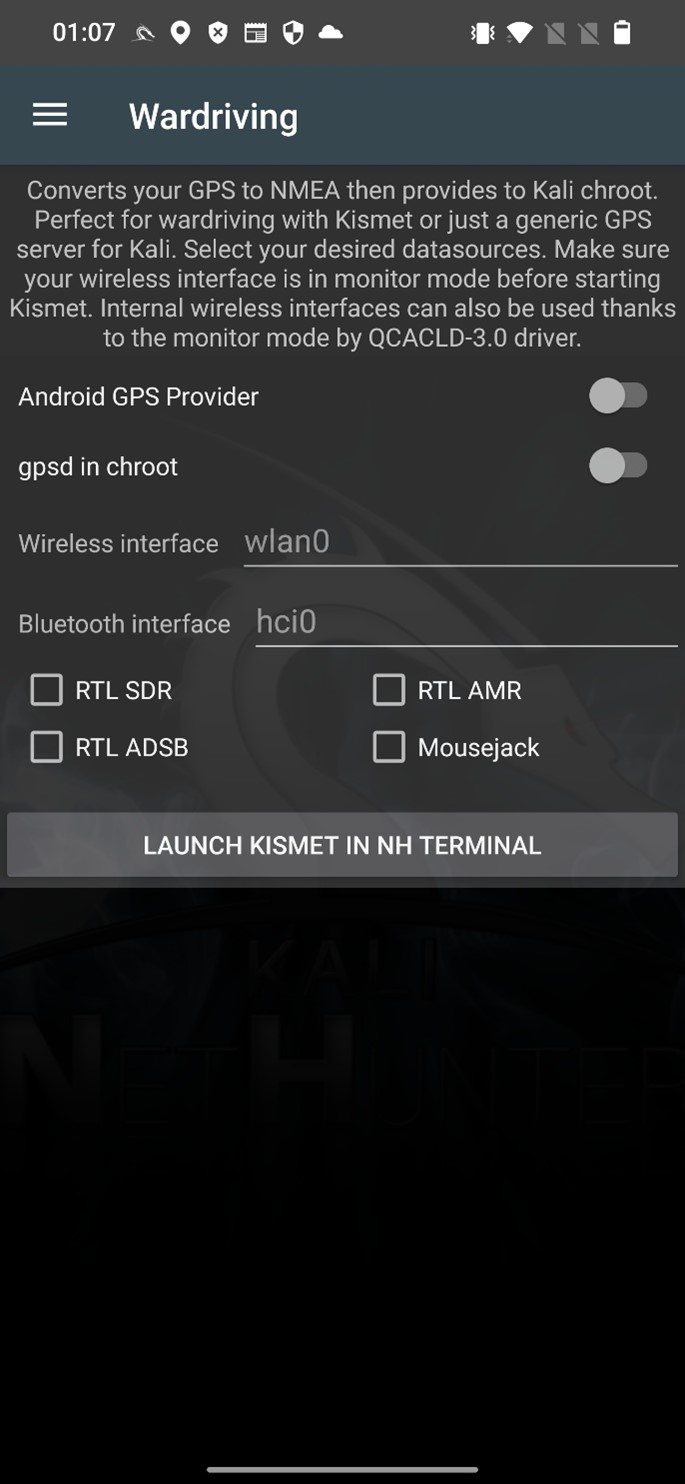
Bluetooth Wardriving
Bluetooth wardriving is the practice of searching for and identifying Bluetooth-enabled devices in a specific area using a mobile device or computer. This can be done with the use of specialized software and hardware, such as a Bluetooth scanner or sniffer. The goal of Bluetooth wardriving is often to identify vulnerable devices that can be exploited or to gather information about the devices and their locations. Bluetooth wardriving using can be done on non-rooted Android device using for example WiGLE WiFi Wardriving app. Using NetHunter, you can wardrive to scan for Bluetooth devices using Kismet. How to setup Kismet for Wi-fi and Bluetooth I already explained in my nethunter wirless hackngn toosl post.
Preventing attacks
Here are a few tips to help prevent and stay safe from Bluetooth attacks:
- Keep your devices operating system updated: Regularly check for and install software updates for your devices to protect against known vulnerabilities.
- Use pairing passwords: Make sure to use pairing passwords when connecting to other devices via Bluetooth, to protect against unauthorized access.
- Disable Bluetooth when not in use: To reduce the risk of an attack, it’s best to disable Bluetooth when you’re not using it.
- Be cautious with public Bluetooth devices: Be wary of connecting to public Bluetooth devices, such as beacons, as they may not be secure. Avoid entering sensitive information while connected to a public Bluetooth device.
Bluetooth technology has become a ubiquitous part of our daily lives, but it also poses a security risk if not properly protected. Hackers can exploit vulnerabilities in Bluetooth to gain unauthorized access to devices, steal personal information, stalk users via broadcasted MAC address, and inject input. It’s important to be aware of the risks and take steps to protect yourself.
如有侵权请联系:admin#unsafe.sh