2023-11-25 00:45:40 Author: securityboulevard.com(查看原文) 阅读量:6 收藏
Penetration testing, commonly known as pentesting, involves simulating a real attack on a server to assess its vulnerabilities against potential real-world attacks. While the primary goal is to emulate concrete threats, pentesting can extend beyond, offering insights into the potential consequences if confidential data were to fall into malicious hackers' hands.
Curious about the various categories of pentesting? Dive into this article! (And as a bonus, find guides on how to conduct pentesting yourself at the end 😉)
Different categories of pentesting
Black box
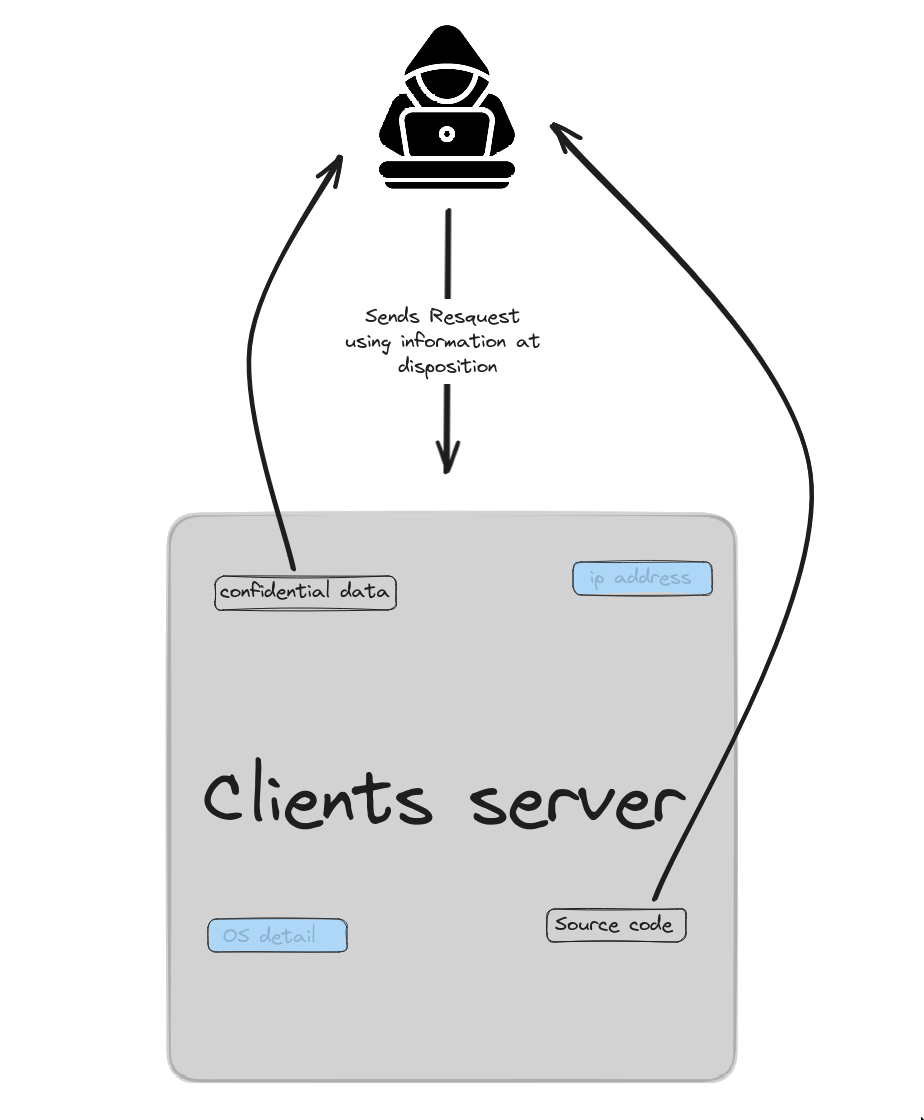
“Black Box Penetration Testing” is a bit like playing a video game where you have to find flaws in a system without any prior information. Imagine that you are a spy and you have to enter an ultra-secure building. But instead of having a map of the building or information on the guards, you arrive with your hands in your pockets, and you have to discover everything on the job.
In the world of cybersecurity, it’s the same. You have a computer system, a website or an app, and you need to test its security. Except you don't know anything about its code or its internal structure. It's like trying to find a back door in a house without knowing where it is.
For example, you could test an e-commerce site. You start by trying basic things, like putting weird characters in text fields, to see if it causes bugs. Or you can try to guess passwords. The idea is to think like a hacker and look for every possible loophole but without any help or clues about the internal workings of the system. If you are interested in how to find vulnerabilities in GraphQL services from an attacker/pentester point of view, check out this article.
It's a challenge because you're kind of groping in the dark. But it's also super useful because it allows you to find flaws that even the designers of the system had not anticipated. It is the ultimate test for the security of a system.
White Box
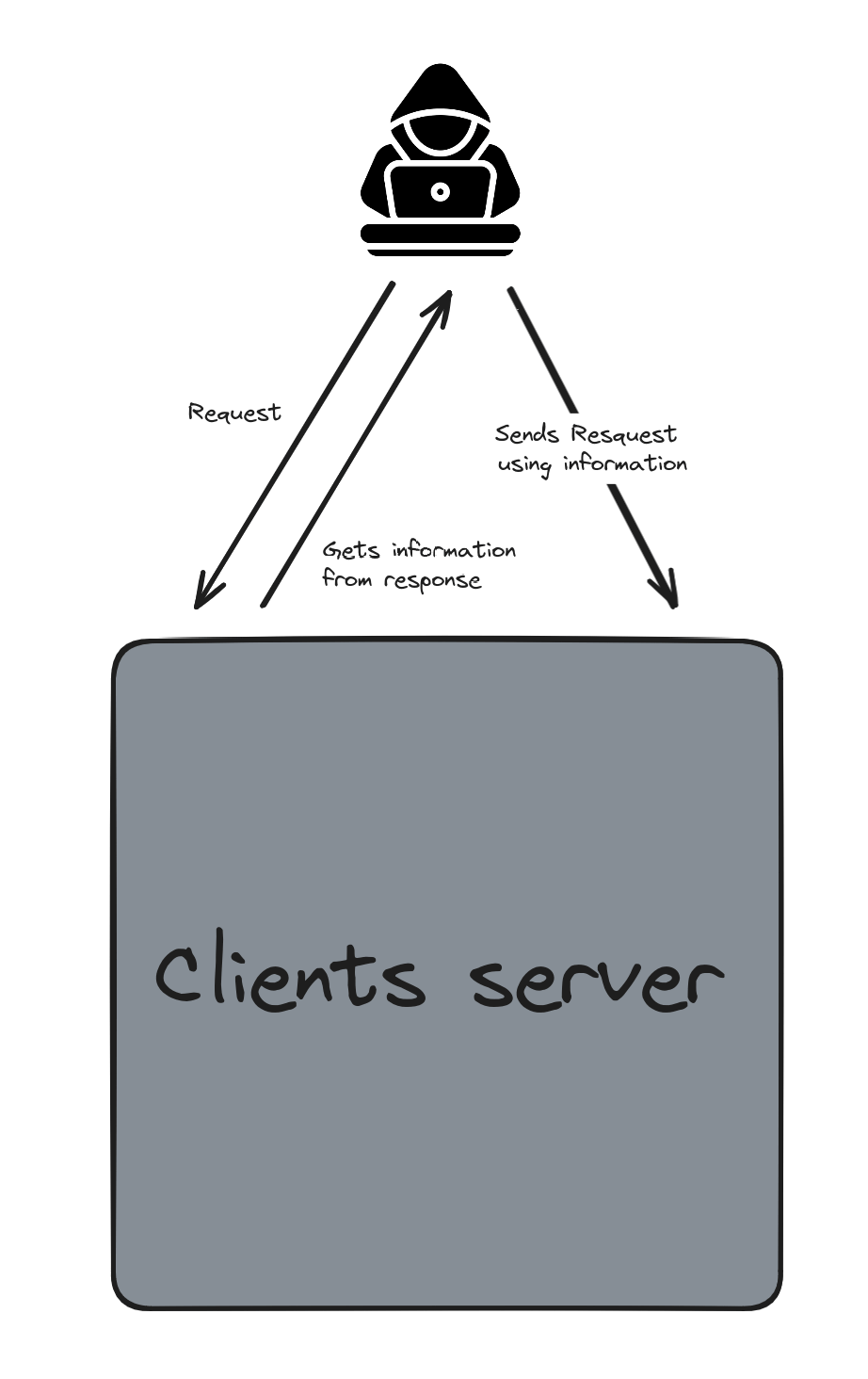
White Box Penetration Testing is like having the treasure map and all the keys to open every door in your spy game. Unlike Black Box Penetration Testing where you enter blindfolded, here, you have all the information about the system you are testing: its code, its structure, its configurations, everything.
Imagine that you are still that spy, but this time, you have the plans of the building, you know where the cameras are and you even the codes for the secure doors. In the IT world, it's the same. You have access to the source code of the website, app, or system. You know how data flows where the sensitive points are, and you can even have administrator access.
Let’s take the example of the e-commerce site again. In White Box Penetration Testing, you can directly read the source code to see if there are any flaws. You know exactly where to look for security issues. You could even simulate internal attacks, like if an employee was trying to compromise the system.
The contrast with the Black Box is, therefore enormous. In Black Box, you explore without a map; you look for flaws without knowing where they are. It's more realistic because that's how real hackers operate. But in White Box, you have an overview; you can be much more systematic and in-depth. You can find vulnerabilities that even an experienced hacker could not detect without this information.
Basically, the Black Box pentesting is about testing security from the outside without information, and the White Box pentesting is about examining it from the inside with all possible data. Each has its advantages: Black Box simulates a real attack, while White Box allows for a more complete and detailed analysis.
Grey Box
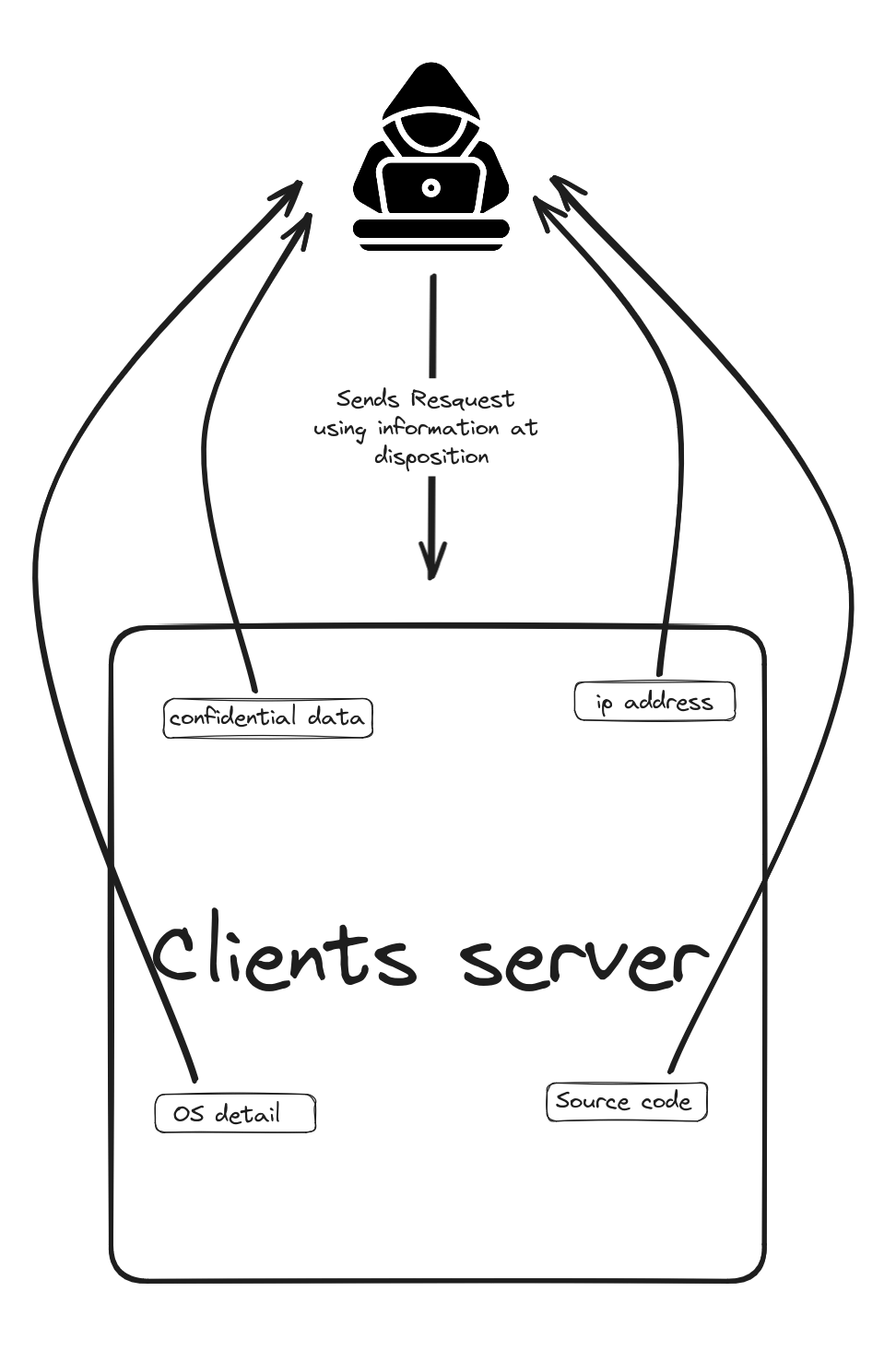
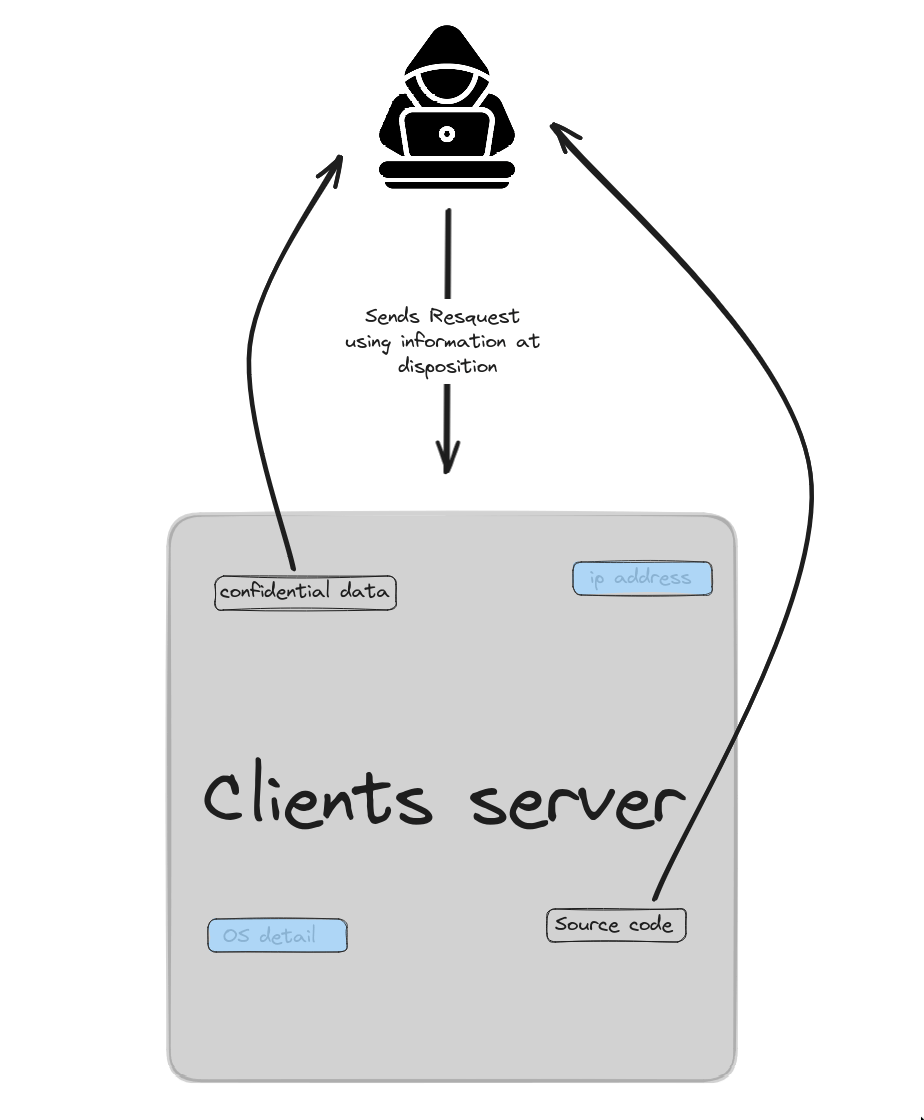
Grey Box Penetration Testing is an IT security testing technique that combines elements of Black Box and White Box Testing. How Grey Box Testing works: you have limited or partial access to information about the system. For example, you might have standard user rights on a website but without knowing the complete source code.
Contrast this with Black Box Testing where you have no prior information and must test the system as a typical user or even as a potential attacker, exploring without knowing where the flaws are. On the other hand, White Box Testing gives you all the cards, with full access to the source code and system configuration, allowing you to examine every aspect in detail.
The Grey Box is considered a good middle ground between these two extremes. It simulates an attacker with some knowledge of the system but not full access. This allows system strength to be tested both from the outside (as in Black Box) and from the inside (as in White Box), providing a balanced approach that combines depth and realism in penetration testing.
💡
Tools you can use for Grey Box Testing:
– Selenium
– Appium
– Postman
– JUnit
– NUnit
– Burp Suite
– RestAssured
Different attack vectors for pentesting
Network Penetration Testing
Network Penetration Testing is like playing a high-tech detective in computer networks. Imagine you have an extensive network of streets (like the Internet or a company's network), and your job is to find all the dark alleys and back doors that the bad guys could use to infiltrate.
In this test, you focus on the network itself: the routers, switches, servers, firewalls, and everything else that allows data to flow. You're looking for flaws like weak passwords, poorly configured configurations, or outdated software. It's a bit like looking for weaknesses in a city's security.
For example, you could test a company's network. You start by scanning the network to see what services are online (a bit like looking to see which stores are open). Then, you try to see if you can get into these services, like a hacker would. Maybe a web server has an old, vulnerable version, or a router has a default password that no one has changed.
The idea is to think like an attacker and test all possible infiltration methods. This also often includes testing to see if you can get data off the network simulating a data leak.
Basically, network penetration testing tests all doors and windows on the computer network to ensure that they are properly locked and secure against intruders. This is crucial because even a small breach in a network can let hackers in and cause big damage.
Web application Pentesting
Web Application Penetration Testing is a bit like being a detective specializing in investigating websites and online applications. Consider each website or application is a house with its own security systems, and your role is to test how strong and secure they are.
In this type of testing, you focus specifically on web applications – such as e-commerce sites, customer portals, or internal company applications. You look for vulnerabilities like forms that don't properly verify user-entered data, pages that expose sensitive information, or links that can be easily manipulated.
For example, you could test an online shopping site. You would start by trying to place orders with incorrect or malicious information to see if the site accepts them. You could also test if you can access other users' accounts by manipulating the URL or cookies. The goal is to see if you can do things you wouldn't normally be able to do, like see other people's data, modify commands, or even inject malicious code.
What is crucial in Web Application Penetration Testing is to think like a hacker. You need to be creative and test all the possible ways an attacker could use to exploit the application. This ranges from trying classic attacks, like SQL injection or cross-site scripting (XSS) attacks, to looking for lesser-known vulnerabilities.
💡
If you'd like to know the difference between CSRF vs XSS, check out this article.
In summary, Web Application Penetration Testing is like testing every lock, every window, and every back door in a house to make sure no intruder can get in. This is essential for protecting user data and company reputation, as a single flaw in a web application can lead to major losses of data, money, or customer trust.
Wireless Penetration Testing
Wireless Penetration Testing is like being an explorer in the invisible world of wireless signals. You have a detector capable of seeing all the Wi-Fi waves around you, and your mission is to test how secure these wireless networks are.
In this type of test, you focus on Wi-Fi networks in a business or public space, such as cafes, libraries, or offices. You're looking to see if these networks can be easily hacked or intercepted. This might involve testing the strength of Wi-Fi passwords, seeing if the network is vulnerable to certain attacks, or even checking if sensitive information is being transmitted without being properly encrypted.
For example, if you're testing a company's Wi-Fi network, you might start by trying to "crack" the password to see if it's easy to do. If you succeed, you can then see what type of access you have: can you see the connected computers? Can you intercept data? Then you could try more advanced attacks, like creating a fake Wi-Fi hotspot to see if employees connect to it automatically, which could allow you to access confidential information.
Wireless Penetration Testing is crucial because wireless networks are everywhere and often less secure than wired networks. A poorly protected Wi-Fi network can be a gateway for hackers, allowing them to access sensitive data or disrupt a company's operations.
In summary, Wireless Penetration Testing is like testing the invisible walls and backdoors that Wi-Fi waves create around us. It is an essential element in ensuring that the wireless communications of a business or public space are well protected against intrusions and unwanted eavesdropping.
Physical Penetration Testing
Now you are tasked with verifying whether you can enter a secure building, such as a corporate office or data center, without being detected or arrested.
This type of testing involves evaluating all physical security measures in place: locks, alarms, surveillance cameras, security guards, and even procedures like access badges or visitor lists. You have to think like an intruder and try to find ways to get around these measures without being caught.
For example, you could test the security of an office. You might start by seeing if you can get in without a badge by following someone inside or pretending to be a delivery person. Once inside, you would assess whether you can access restricted areas, such as server rooms or management offices. You could also test the responsiveness of guards or staff in the event of suspicious behavior.
The goal is to see how easy or difficult it is for an intruder to gain access to secure areas and compromise the physical security of the business. This may include testing to see if sensitive information is left unattended or if security equipment can be easily disabled or bypassed.
Physical Penetration Testing is essential because even the best IT security cannot protect against a successful physical intrusion. An intruder who physically accesses servers, for example, could cause enormous damage.
In summary, Physical Penetration Testing is testing physical barriers and security procedures to ensure they are effective against actual intrusions. It is a vital aspect of overall security, as it involves protecting not only data and computer systems but also people and physical assets.
Social Engineering Penetration Testing is like being an actor who plays different roles to test people's vulnerability to manipulation and deception. You need to convince employees of a company to give you confidential information or allow you access to secure systems, but without using technology – just using psychological tricks.
In this type of testing, you focus on the human elements of security. You test how easy it is to trick people into obtaining passwords, accessing secure areas, or getting them to install malware. This might involve posing as an employee, technician, or even a senior manager to see if people trust you and give you access to what you want.
For example, you could call employees pretending to be IT support and ask them for their credentials under the pretext of resolving a problem. Or you could show up at the reception of a building pretending to have an appointment with a manager to see if they will let you in without verification. You could even send emails that appear to come from management to see if employees click on links or open questionable attachments.
The goal is to see how aware employees are of security risks and whether they follow appropriate procedures. This is crucial because often, the weakest link in security is not technological, but human. People can easily be tricked, which can lead to serious security breaches.
In summary, Social Engineering Penetration Testing is a test of an organization's resilience to attempts at manipulation and deception. It aims to increase awareness and training of employees so that they are better prepared to identify and respond to social engineering attempts, thus protecting the company against attacks that target its most vulnerable aspects: the people themselves.
Client-Side Penetration Testing
Client-side Penetration Testing is a form of security testing that focuses on vulnerabilities on the client side of an application or system. Imagine you're a security specialist checking the strength of a home's windows and doors, but here, the "windows" and "doors" are web browsers, email applications, and other software people use on their computers or mobile devices.
Penetration
This type of testing aims to find flaws in applications or software used by a company's customers or employees. These flaws can include vulnerabilities in web browsers, plugins, email applications, instant messaging clients, and other software that processes external data. You could test, for example, if a web browser is vulnerable to specific script attacks or if an application can be compromised via an email bomb.
An example of Client-Side Penetration Testing could be sending an email with an attachment or link that appears harmless but contains malicious code. If the user opens the attachment or clicks on the link, the tester can see if the malware can execute and to what extent it can compromise the user's computer. You could also test phishing attacks to see if employees are likely to give away sensitive information.
The goal of this type of testing is to ensure that software used by customers and employees is secure against attacks that can be launched remotely. This is crucial because even if the company's servers and network are well-secured, a vulnerability on the client side can still allow an attacker to access sensitive information or compromise the system.
In summary, Client-Side Penetration Testing is like testing every potential entry point on the user side of an application or system. It helps identify and fix vulnerabilities that could be exploited by attackers to access sensitive data or compromise a company's security from employee or customer endpoints.
Conclusion
In a nutshell, penetration testing comes in different flavors, each tackling security challenges in its own way. From the blind exploration of Black Box Testing to the thorough insights of White Box Testing and the balanced approach of Grey Box Testing, these methods contribute to a strong security strategy.
Then there are specialized tests—Network, Web Application, Wireless, Physical, Social Engineering, and Client-Side Penetration Testing—covering various vulnerability angles.
A mix of these penetration testing techniques will help you protect your organization against potential breaches.
💡 Want to learn more? Check out the following articles:
- Goctopus: Open Source GraphQL endpoint discovery & fingerprinting tool
- Pentesting GraphQL 101 Part 1 – Discovery
- Pentesting GraphQL 101 Part 2 – Interaction
- Pentesting GraphQL 101 Part 3 – Exploitation
- Thinking outside the box when pentesting GraphQL
*** This is a Security Bloggers Network syndicated blog from Escape - The API Security Blog authored by Alexandre Tang. Read the original post at: https://escape.tech/blog/different-types-of-penetration-testing/
如有侵权请联系:admin#unsafe.sh
