
2023-11-24 22:0:0 Author: www.tenable.com(查看原文) 阅读量:10 收藏

Uncle Sam wants your input on the latest version of the “Secure Software Development Attestation Form” that federal agencies will use to assess the security of software vendors. Plus, it’s warning cyber teams about the threats from the Rhysida and Scattered Spider cybercrime groups. In addition, there’s a new zero trust certification. And much more!
Dive into six things that are top of mind for the week ending November 24.
1 - CISA updates security attestation form draft, seeks more feedback
Looking for guidance and best practices for assessing the security of your organization’s software vendors? Now you can get a peek at how the U.S. government will evaluate the security practices of its software vendors – and offer your two cents.
CISA has just updated a draft of the “Secure Software Development Attestation Form,” which it initially published in April – and is requesting feedback on it. When this questionnaire is finalized, federal agencies and departments will be able to use it to assess the security of software vendors.

The attestation form was developed in consultation with the U.S. Office of Management and Budget (OMB) and based upon the Secure Software Development Framework (SSDF) from the U.S. National Institute of Standards and Technology (NIST).
It broadly focuses on whether and how software producers:
- Build their software products in a secure environment
- Maintain trusted source-code supply chains
- Track the origins of internal code and third-party components contained in their products
- Use automated tools and processes to detect software vulnerabilities in their products
“This form will establish a standardized process for the federal government and software producers that will create transparency on the security of software development efforts,” reads the alert “CISA Requests Comment on Draft Secure Software Development Attestation Form.”
To offer feedback on this latest draft of the attestation form, go to this page and select the option “Currently under Review - Open for Public Comments.” CISA will accept comments until Dec. 18. More than 100 people commented on the first version earlier this year.
To get more details, check out:
- The page “Request for Comment on Secure Software Development Attestation Common Form”
- The “Secure Software Development Attestation Form” itself
For more information about assessing the security practices of prospective software vendors:
- “5 Key Questions When Evaluating Software Supply Chain Security” (Dark Reading)
- “Commercial Software Assessment Guideline” (University of California Berkeley)
- “SaaS and Third-Party Risk: Is Your Organization Asking the Hard Questions?” (Dark Reading)
- “Third-party risks: How to reduce them” (SC Magazine)
- “US government software suppliers must attest their solutions are secure” (Help Net Security)
2 - Advisory issued for Rhysida ransomware group
The U.S. government wants you to take the threat from the Rhysida ransomware group seriously.
Active since May, Rhysida operates using a ransomware-as-a-service (RaaS) model. It primarily targets the education, healthcare, manufacturing, information technology and government sectors.
In their joint “#StopRansomware: Rhysida Ransomware” advisory, the Cybersecurity and Information Security Agency (CISA), the FBI and the Multi-State Information Sharing and Analysis Center (MS-ISAC) detail this variant’s indicators of compromise, detection methods, and tactics, techniques, and procedures.
According to the 16-page document, Rhysida attackers:
- Breach external-facing remote services such as VPNs using compromised valid credentials to gain initial access
- Employ “living off the land” techniques to blend in with the breached environment and avoid detection
- Leverage legitimate tools within the environment, including PowerShell.exe, PxExec.exe and cmd.exe.
- Engage in “double extortion” schemes, in which they demand ransom payments to decrypt the hijacked data and threaten to publish the data publicly
Rhysida Ransom Note
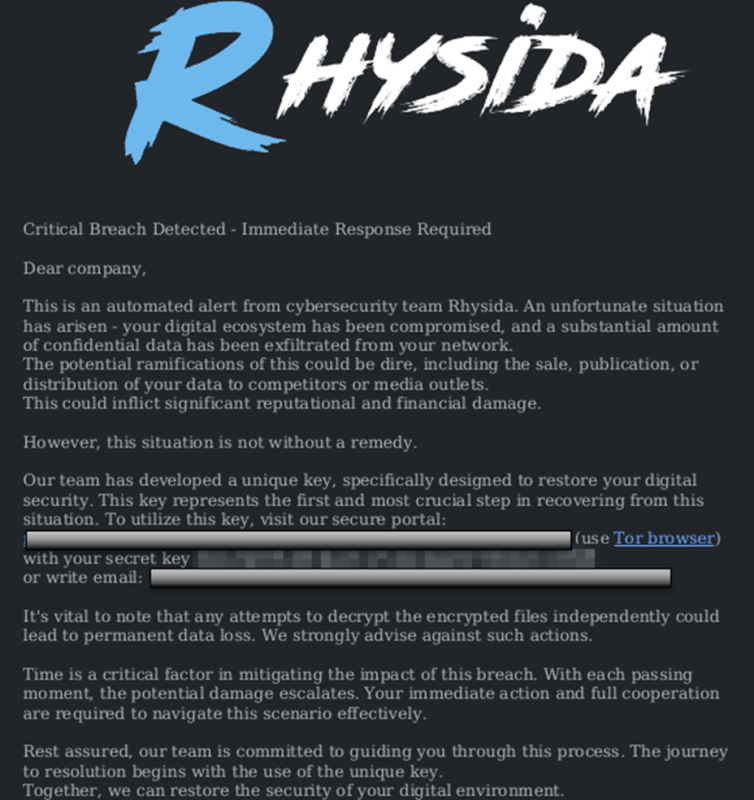
(Credit: CISA)
To get all the details, read the joint alert “CISA, FBI, and MS-ISAC Release Advisory on Rhysida Ransomware” and the full “#StopRansomware: Rhysida Ransomware” advisory.
For more information about Rhysida:
- “Rhysida ransomware gang claims attacks on governments in Portugal, Dominican Republic” (The Record)
- “Rhysida Ransomware Alert” (U.S. Department of Health and Human Services)
- “Meet Rhysida, a New Ransomware Strain That Deletes Itself” (Dark Reading)
- “Rhysida ransomware behind recent attacks on healthcare” (BleepingComputer)
- “Rhysida Ransomware Analysis Reveals Vice Society Connection” (Infosecurity Magazine)
3 - CSA launches zero trust certification
Interested in getting certified in the area of zero trust? The Cloud Security Alliance just launched its Certificate of Competence in Zero Trust (CCZT), which it defines as “a holistic benchmark for measuring zero trust knowledge.”

Cybersecurity professionals who obtain the CCZT will gain in-depth understanding of zero trust architecture, components, planning, implementation and operation, along with zero trust best practices, all with an approach that’s vendor agnostic, according to the CSA.
To get more details, check out:
- The CSA announcement
- The CSA blog “CCZT: A Major Milestone on the Zero Trust Journey”
- The CCZT home page
For more information about zero trust:
- “Top zero-trust certifications and training courses” (TechTarget)
- “5 Best Practices from Industry for Implementing a Zero Trust Architecture” (Carnegie Mellon University)
- “7 steps for implementing zero trust, with real-life examples” (TechTarget)
4 - FBI: Beware of IT help desk impersonators Scattered Spider
Here’s another cybercrime gang to be aware of. Scattered Spider has carried out a rash of recent attacks against large companies in which its members impersonate IT help desk staffers in order to steal data and extort money from victims.
That’s according to a joint advisory from CISA and the FBI which details the hacking group’s techniques, tactics and procedures, including its use of BlackCat/ALPHV ransomware, and offers mitigation recommendations.

Also known as Starfraud, UNC3944, Scatter Swine, and Muddled Libra, Scattered Spider is made up of social engineering experts who use techniques like phishing to swipe credentials, install remote access tools and bypass multi-factor authentication systems.
The advisory recommendations include:
- Implement application controls to prevent, for example, the installation and execution of portable versions of unauthorized remote access software
- Reduce attackers’ ability to maliciously use remote access tools by, for example, auditing these tools on your network; and reviewing these tools’ execution logs
- Implement phishing-resistant MFA systems
- Put strict limits on the use of remote desktop services
To get more details, check out:
- The joint FBI-CISA alert “FBI and CISA Release Advisory on Scattered Spider Group”
- The joint advisory
5 - A peek at cyber insurance issues in the real world
At our recent webinar “Expert Guide: How to Successfully Secure the Best Cyber Insurance Policy at the Best Price for Your Business,” we polled attendees on various cyber insurance topics, such as whether the process is getting more complicated, and to what extent they participated in their organizations’ cyber insurance procurement. Check out what they said.
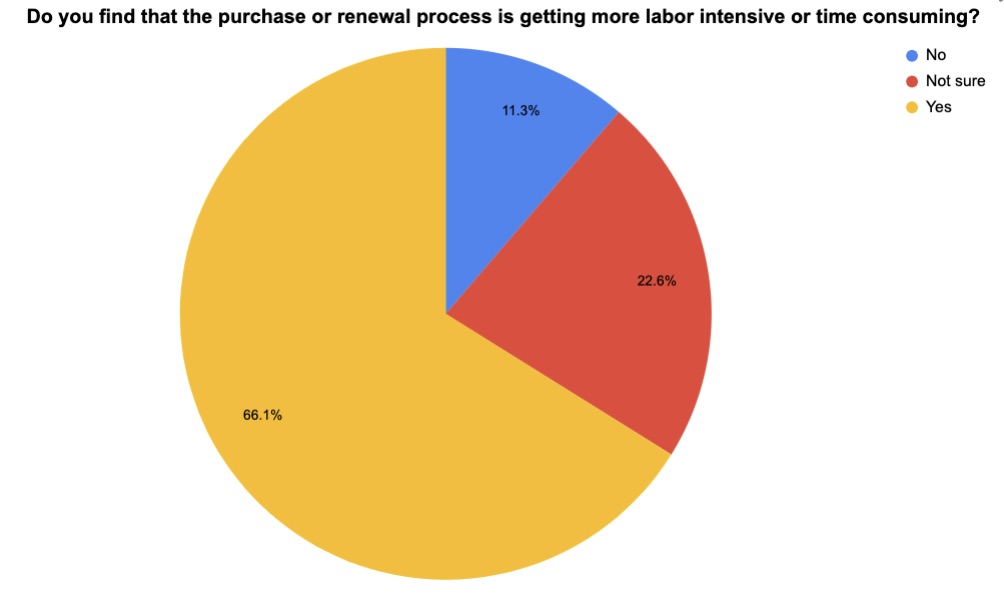
(62 respondents polled by Tenable in November 2023)
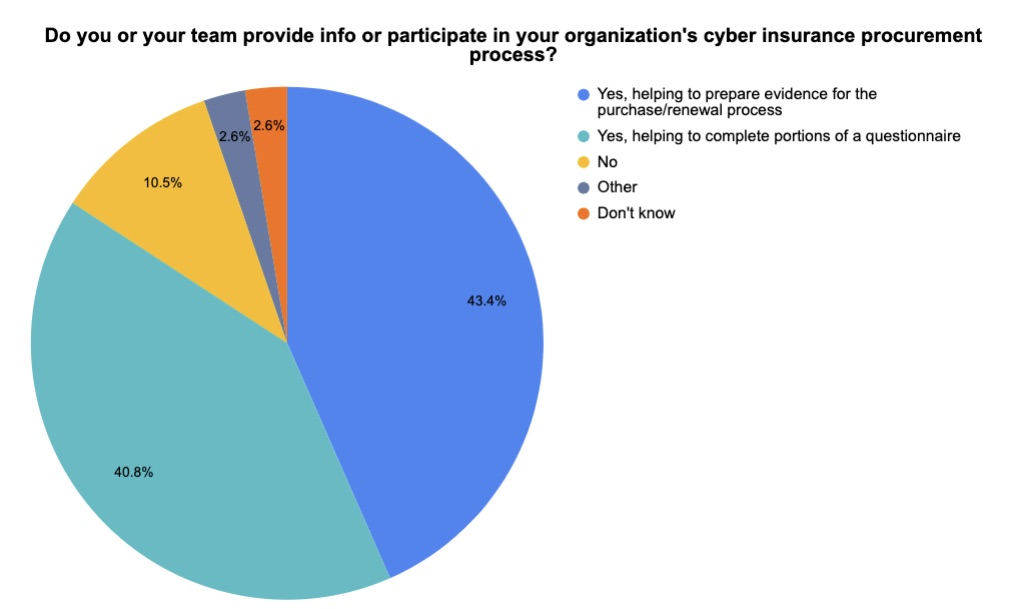
(59 respondents polled by Tenable in November 2023 – more than one answer was allowed)
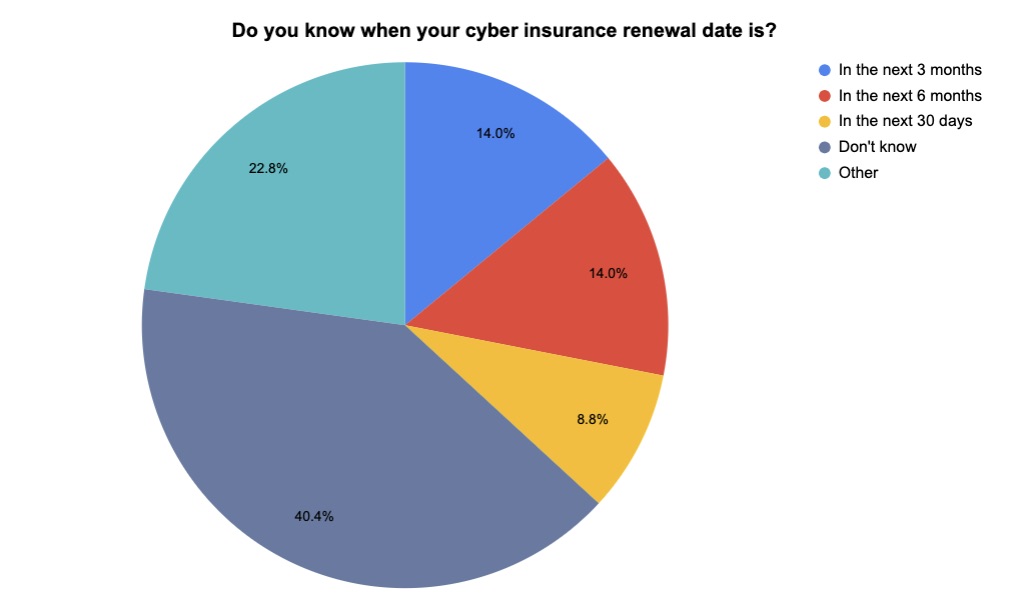
(57 respondents polled by Tenable in November 2023)
Interested in learning how you can optimize cyber insurance coverage for your business? Watch the webinar on-demand!
For more information about cyber insurance:
- Federal Trade Commission’s page on cyber insurance
- “Time and effort to obtain cyber insurance increasing for US businesses” (CSO)
- “Cyber insurance claims spiked in first half of 2023 as ransomware attacks surged” (The Record)
- “How To Obtain the Right Cybersecurity Insurance for Your Business” (Tenable)
- “What is cyber insurance?” (TechTarget)
VIDEOS
How Would Cyber Insurance Companies Cover Catastrophic Hacks? (The Wall Street Journal)
The Role of Cyber Insurance in Improving Cybersecurity (George Washington University)
2023 Cyber Insurance Market Update (Fitch Ratings)
6 - FCC program would protect schools, libraries from cyberattacks
A new program has been proposed to help U.S. schools and libraries boost their cybersecurity as they face a growing number of attacks and struggle to defend themselves against hackers.
The U.S. Federal Communications Commission’s (FCC) “Schools and Libraries Cybersecurity Pilot Program” would focus on protecting the broadband networks and the data of K-12 schools and libraries.
“Predictions are that K-12 schools and libraries will continue to be prime targets for malicious actors, primarily because they are data-rich environments that tend to lag behind in terms of their available resources and cybersecurity program maturity,” reads the 74-page proposal.
The FCC outlined three main goals for the proposed pilot program:
- Boosting the security of broadband networks and data funded by the FCC’s E-Rate program, which makes telecom and IT services more affordable for schools and libraries
- Measuring the costs and effectiveness of cybersecurity and advanced firewall services and equipment
- Determining how other federal resources could be used to help schools and libraries address cybersecurity threats
For more information about cyberattacks against schools and libraries:
- “After school hacks, ransomware criminals expose kids’ private files online” (PBS)
- “7 Data Breaches That Left Schools in the Lurch” (Education Week)
- “Ransomware Attacks at Libraries: How They Happen, What to Do” (Public Libraries Online)
- “Even public libraries aren't safe from ransomware, as Canada's biggest is hit” (TechRadar)

Juan Perez
Juan has been writing about IT since the mid-1990s, first as a reporter and editor, and now as a content marketer. He spent the bulk of his journalism career at International Data Group’s IDG News Service, a tech news wire service where he held various positions over the years, including Senior Editor and News Editor. His content marketing journey began at Qualys, with stops at Moogsoft and JFrog. As a content marketer, he's helped plan, write and edit the whole gamut of content assets, including blog posts, case studies, e-books, product briefs and white papers, while supporting a wide variety of teams, including product marketing, demand generation, corporate communications, and events.
Related Articles
- Cloud
- Cybersecurity Snapshot
- Exposure Management
- Government
- Risk-based Vulnerability Management
Cybersecurity News You Can Use
Enter your email and never miss timely alerts and security guidance from the experts at Tenable.
Tenable Vulnerability Management
Formerly Tenable.io
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy.
Your Tenable Vulnerability Management trial also includes Tenable Lumin and Tenable Web App Scanning.
Tenable Vulnerability Management
Formerly Tenable.io
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy. Purchase your annual subscription today.
100 assets
Choose Your Subscription Option:
Thank You
Thank you for your interest in Tenable.io. A representative will be in touch soon.
Try Tenable Nessus Professional Free
FREE FOR 7 DAYS
Tenable Nessus is the most comprehensive vulnerability scanner on the market today.
NEW - Tenable Nessus Expert
Now Available
Nessus Expert adds even more features, including external attack surface scanning, and the ability to add domains and scan cloud infrastructure. Click here to Try Nessus Expert.
Fill out the form below to continue with a Nessus Pro Trial.
Buy Tenable Nessus Professional
Tenable Nessus is the most comprehensive vulnerability scanner on the market today. Tenable Nessus Professional will help automate the vulnerability scanning process, save time in your compliance cycles and allow you to engage your IT team.
Buy a multi-year license and save. Add Advanced Support for access to phone, community and chat support 24 hours a day, 365 days a year.
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy.
Your Tenable Vulnerability Management trial also includes Tenable Lumin and Tenable Web App Scanning.
BUY
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy. Purchase your annual subscription today.
100 assets
Choose Your Subscription Option:
Thank You
Thank you for your interest in Tenable.io. A representative will be in touch soon.
Try Tenable Web App Scanning
Formerly Tenable.io Web Application Scanning
Enjoy full access to our latest web application scanning offering designed for modern applications as part of the Tenable One Exposure Management platform. Safely scan your entire online portfolio for vulnerabilities with a high degree of accuracy without heavy manual effort or disruption to critical web applications. Sign up now.
Your Tenable Web App Scanning trial also includes Tenable Vulnerability Management and Tenable Lumin.
Buy Tenable Web App Scanning
Formerly Tenable.io Web Application Scanning
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy. Purchase your annual subscription today.
Try Tenable Lumin
Visualize and explore your exposure management, track risk reduction over time and benchmark against your peers with Tenable Lumin.
Your Tenable Lumin trial also includes Tenable Vulnerability Management and Tenable Web App Scanning.
Buy Tenable Lumin
Contact a Sales Representative to see how Tenable Lumin can help you gain insight across your entire organization and manage cyber risk.
Thank You
Thank you for your interest in Tenable Lumin. A representative will be in touch soon.
Request a demo of Tenable Security Center
Formerly Tenable.sc
Please fill out this form with your contact information.
A sales representative will contact you shortly to schedule a demo.
* Field is required
Request a demo of Tenable OT Security
Formerly Tenable.ot
Get the Operational Technology Security You Need.
Reduce the Risk You Don’t.
Request a demo of Tenable Identity Exposure
Formerly Tenable.ad
Continuously detect and respond to Active Directory attacks. No agents. No privileges.
On-prem and in the cloud.
Request a Demo of Tenable Cloud Security
Exceptional unified cloud security awaits you!
We’ll show you exactly how Tenable Cloud Security helps you deliver multi-cloud asset discovery, prioritized risk assessments and automated compliance/audit reports.
See
Tenable One
In Action
Exposure management for the modern attack surface.
See Tenable Attack Surface Management In Action
Formerly Tenable.asm
Know the exposure of every asset on any platform.
Thank You
Thank you for your interest in Tenable Attack Surface Management. A representative will be in touch soon.
Try Tenable Nessus Expert Free
FREE FOR 7 DAYS
Built for the modern attack surface, Nessus Expert enables you to see more and protect your organization from vulnerabilities from IT to the cloud.
Already have Tenable Nessus Professional?
Upgrade to Nessus Expert free for 7 days.
Buy Tenable Nessus Expert
Built for the modern attack surface, Nessus Expert enables you to see more and protect your organization from vulnerabilities from IT to the cloud.
Try Nessus Expert Free
FREE FOR 7 DAYS
Built for the modern attack surface, Nessus Expert enables you to see more and protect your organization from vulnerabilities from IT to the cloud.
Already have Nessus Professional?
Upgrade to Nessus Expert free for 7 days.
Buy Tenable Nessus Expert
Built for the modern attack surface, Nessus Expert enables you to see more and protect your organization from vulnerabilities from IT to the cloud.
Learn How Tenable Helps Achieve SLCGP Cybersecurity Plan Requirements
Tenable solutions help fulfill all SLCGP requirements. Connect with a Tenable representative to learn more.
如有侵权请联系:admin#unsafe.sh