2023-11-24 22:0:11 Author: www.sentinelone.com(查看原文) 阅读量:13 收藏
The Good | FTC Launches Series of Proactive Steps to Bolster U.S. Cybersecurity Efforts
Responding to an ever-evolving cyber threat landscape, the Federal Trade Commission (FTC) has unveiled two security initiatives, consolidating efforts to strengthen cyber defense measures and protect U.S. consumers.
Most recently, the FTC’s proactive stance extended into the realm of artificial intelligence (AI). Recognizing the emerging threat of AI-driven fraud and extortion through voice cloning, the FTC this week announced a Voice Cloning Challenge. This challenge serves as an innovative approach to encourage new ideas and technologies capable of detecting and mitigating the risks associated with voice cloning and AI manipulation. By fostering collaboration and incentivizing solutions spanning “product, policy, or procedures”, the FTC demonstrates a commitment to staying ahead of technological advancements and safeguarding consumers from developing and sophisticated cyber threats.
The FTC has launched a voice cloning challenge to spur ideas for how to prevent and detect voice cloning misuse. Submissions will be accepted from Jan. 2-12, with $25k for the winner. Learn more: https://t.co/yqPvvExbYw
— FTC (@FTC) November 22, 2023
Last week, the FTC proposed a new cyber disclosure rule after a data breach hit a Virginia-based prison. Reports say that Global Tel* Link Corp., a prison communications provider, failed to secure the sensitive information of incarcerated individuals and then neglected to notify all victims post-breach. After personal information of some 650,000 users were copied into a cloud service, it was left unencrypted with no firewall nor any access management software. Forensic analysis later revealed that billions of bytes of data was exposed to the attacker with some making it onto the dark web. Due to a 9-month delay by Global Tel* Link Corp., thousands of inmates were unable to obtain credit freezes and take necessary precautions. The FTC is now requiring such providers and its subsidiaries to create new data security programs focused on minimizing human errors, implementing MFA, and notifying all affected users and facilities of future data breaches within 30 days.
The Bad | Rhysida RaaS Claims Responsibility For Cyberattack on British Library
Days before Halloween, the British Library was hit with a major IT outage, affecting its online systems and services, website and onsite services following a cyberattack. Last Friday, the institution confirmed that they had suffered a ransomware attack and that the library’s many services continued to be afflicted.
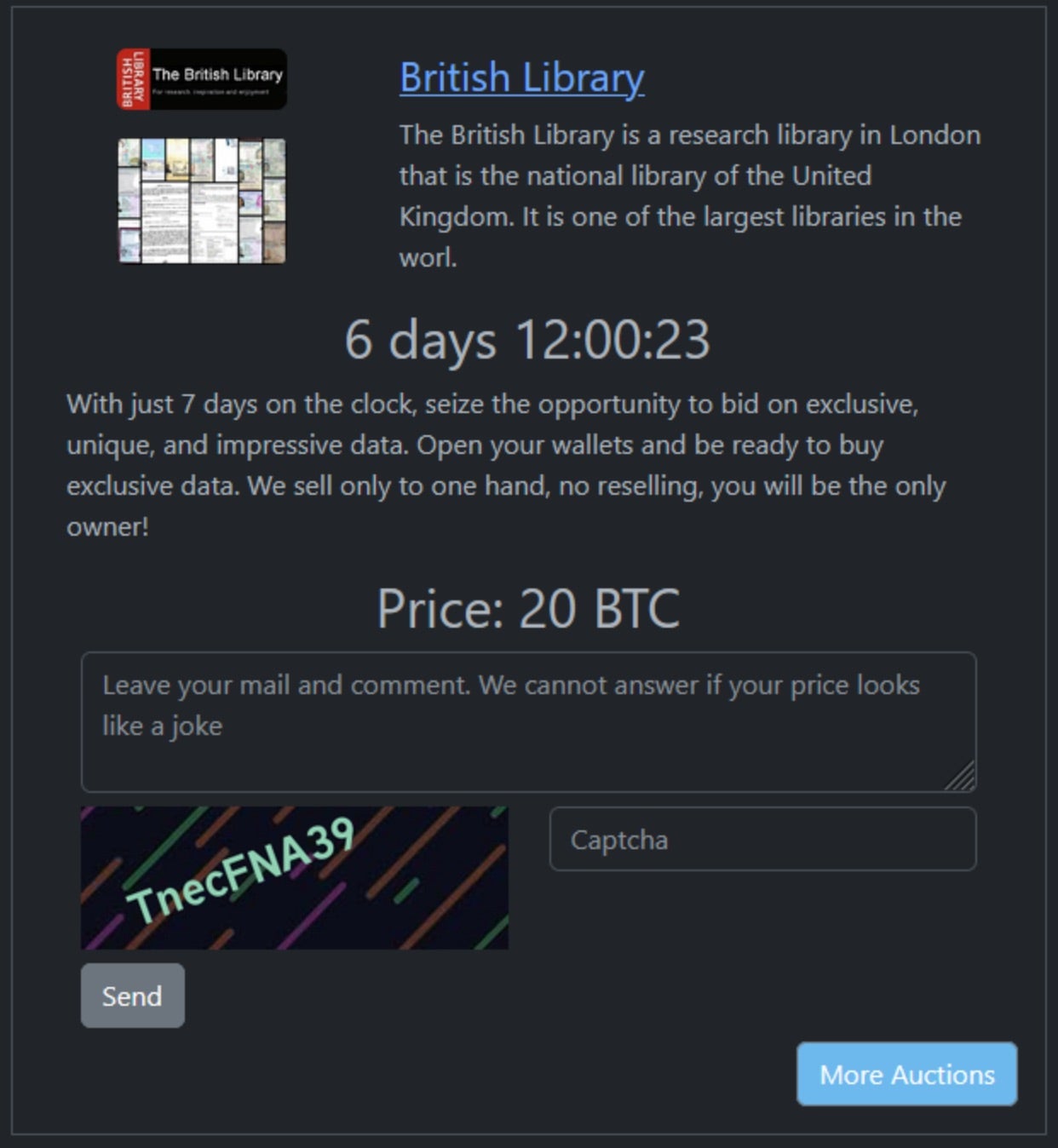
In a disturbing turn, the Rhysida ransomware gang claimed responsibility for the attack this week and is now auctioning off stolen data from the national library’s systems. The gang is soliciting bids over the course of a week, presenting a low-resolution screenshot of purportedly stolen ID scans as ‘proof’ of stolen data. Both the FBI and CISA have issued a joint warning about the opportunistic nature of Rhysida’s attacks that emphasize the far-reaches of its Ransomware-as-a-Service (RaaS) model.
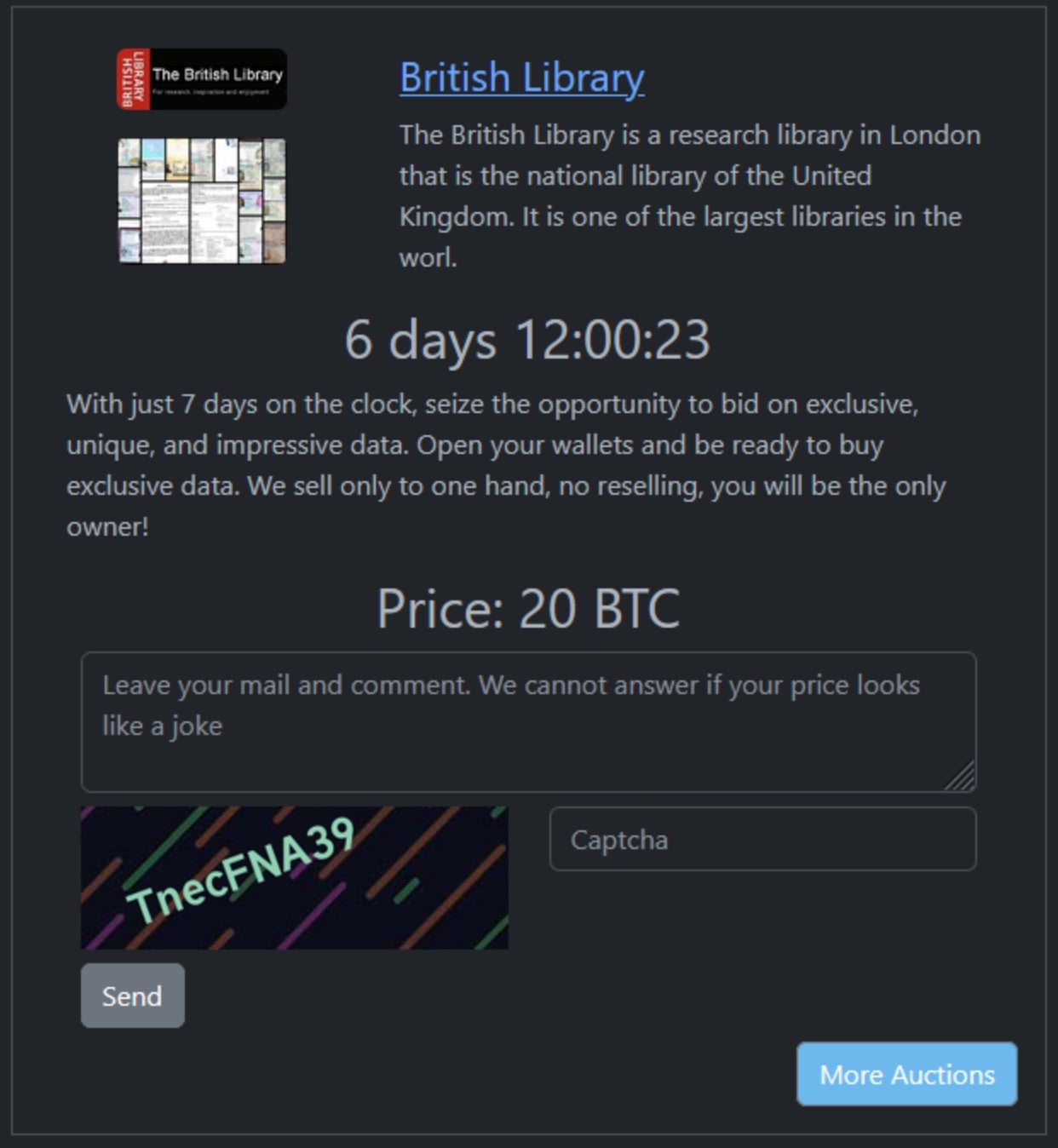
The Rhysida ransomware group was first observed in May 2023, following the emergence of their victim ‘support’ chat portal hosted on Tor. According to the FBI and CISA, the group is focused on “targets of opportunity” across all critical sectors. Their RaaS model allows Rhysida to lease out ransomware tools and infrastructure leading to profit shares being split between the group and any affiliates.
In response to the data leak, the British Library has confirmed the compromise of HR documents and advised users to reset passwords as a precautionary measure. While evidence suggests leaked HR information, the library asserts no indication of broader user data compromise so far. To date, the British Library sees more than 11 million visitors to their website annually and over 16,000 users accessing both onsite and digital collections of over 150 million items. The ongoing issues stemming from this attack zeros in on much-needed defense of critical cultural and national institutions against persistent threat groups targeting organizations of opportunity.
The Ugly | Sensitive PII Leaked Online After U.S. Nuclear Energy Center is Breached
The 5,700-strong workforce of Idaho National Laboratory (INL) fell victim to a cyberattack this week when the contents of their HR database were leaked online. INL is a nuclear research center housing 50 experimental reactors operated by the U.S. Department of Energy. The center holds a vast portfolio, being involved in research on nuclear waste processing, robotics, bioenergy, advanced vehicle testing, light water reactors, and more. This is the latest attack on U.S. critical sectors; a growing trend where threat actors seek to compromise many through a single entity and leverage sensitive data for exuberant ransoms.
After gaining access to INL servers supporting the research center’s Oracle HCM system, the data breach was claimed by a hacktivist group called ‘SiegeSec’, already known in the cyber threat arena for their previous attacks on NATO and Atlassian. Consistent with their past breaches, SiegeSec took to various hacker forums and their Telegram channel to post stolen data from allegedly “hundreds of thousands” of employees, system users, and citizens.
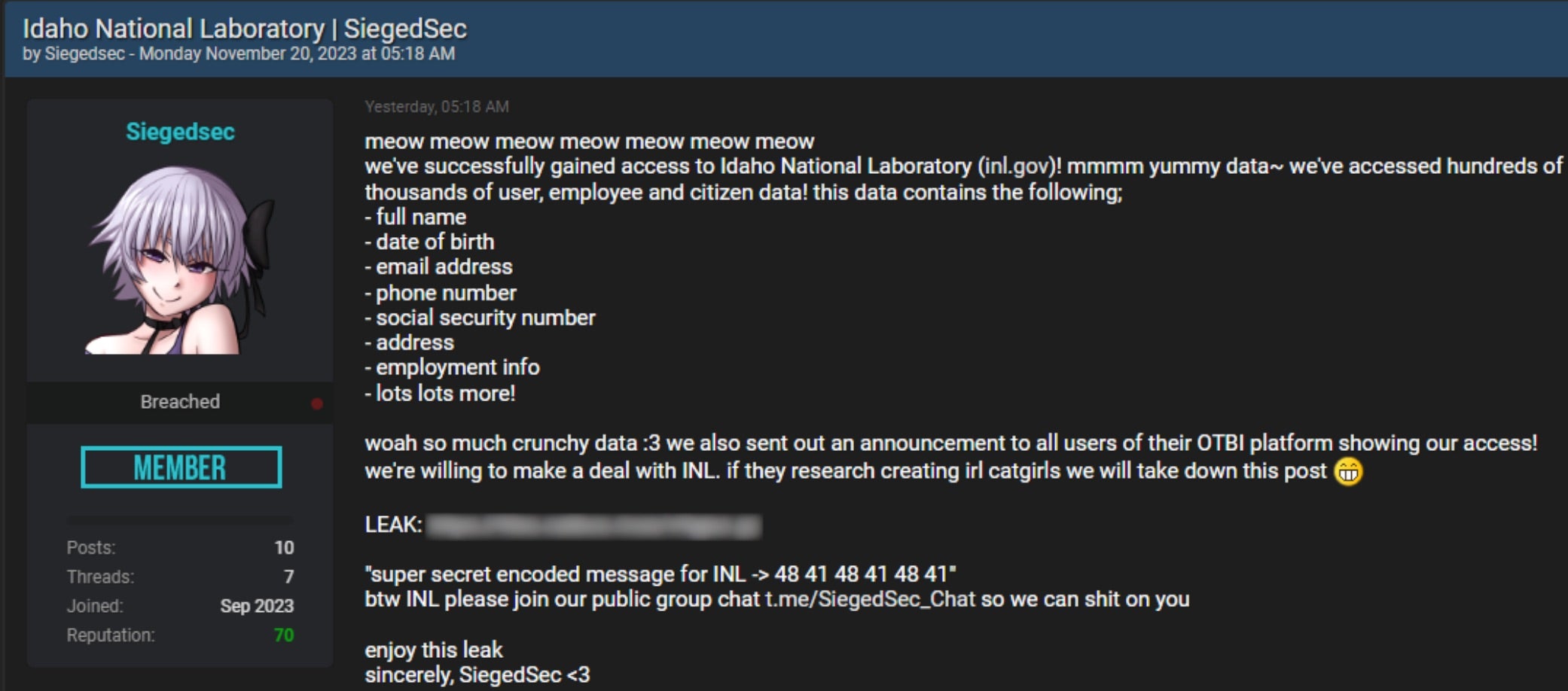
While INL has yet to release an official statement on the incident, a spokesperson has acknowledged the breach, confirming support from federal law enforcement agencies, including the FBI and CISA, and that investigations are underway. Affected employees have been told to freeze their credit, monitor financial accounts, and update critical passwords.
The attack on INL follows similar breaches from earlier this year where a Russian-based hacking group dubbed ‘Cold River’ targeted three American nuclear labs: Brookhaven (BNL), Argonne (ANL), and Lawrence Livermore National Laboratories (LLNL). Though SiegedSec has not disclosed any data related to INL’s nuclear research as of this writing, the incident underscores the heightened concerns around protecting U.S. critical infrastructure and essential services against advancing cyber threats.
如有侵权请联系:admin#unsafe.sh