2023-11-23 04:0:37 Author: securityboulevard.com(查看原文) 阅读量:15 收藏
Author:
Kaustubh Jagtap, Product Marketing Director, SafeBreach
On November 21st, the Cybersecurity and Infrastructure Security Agency (CISA), Federal Bureau of Investigation (FBI), Multi-State Information Sharing & Analysis Center (MS-ISAC), and Australian Signals Directorate’s Australian Cyber Security Center (ASD’s ACSC) released an advisory highlighting the ongoing exploit of the Citrix Bleed Vulnerability (CVE-2023-4966) by Lockbit 3.0 affiliates. This vulnerability affects Citrix NetScaler web application delivery control (ADC) and NetScaler Gateway appliances. Detailed information is listed in US-CERT Alert AA23-325A – #StopRansomware: LockBit 3.0 Ransomware Affiliates Exploit CVE 2023-4966 Citrix Bleed Vulnerability.
According to the advisory, Boeing observed LockBit 3.0 threat actors actively exploiting CVE-2023-4966 to gain access to Boeing Distribution Inc. – a subsidiary of Boeing that is hosted in a separate network environment from the parent Boeing company. Based on previously available information, LockBit 3.0 affiliates have targeted organizations of various sizes across several critical infrastructure verticals including, education, energy, financial services, food and agriculture, government and emergency services, healthcare, manufacturing, and transportation. As LockBit 3.0 affiliates are free to choose from a wide variety of available TTPs, attacks across organizations may vary in style.
Technical Details
By exploiting the Citrix Bleed vulnerability, LockBit 3.0 threat actors can bypass password requirements and multifactor authentication (MFA), allowing them to get access to active user sessions on Citrix NetScaler web application delivery control (ADC) and Gateway appliances. By performing a legitimate hijack of active user sessions, they can easily elevate their permissions, and move laterally to access available data and resources. Below are some of the technical details made available in the advisory.
The CVE-2023-4966 Vulnerability – This vulnerability was first identified in August 2023 and allows threat actors to bypass MFA and gain access to active user sessions. They gain this access by sending an HTTP GET request to the affected appliance allowing them to get a valid NetScaler AAA session cookie. After receiving this valid session cookie, they proceed by creating an authenticated session within the NetScaler appliance without a username, password, or access to MFA tokens. This vulnerability is known to affect the following software versions:
- NetScaler ADC and NetScaler Gateway 14.1 before 14.1-8.50
- NetScaler ADC and NetScaler Gateway 13.1 before 13.1-49.15
- NetScaler ADC and NetScaler Gateway 13.0 before 13.0-92.19
- NetScaler ADC and NetScaler Gateway version 12.1 (EOL)
- NetScaler ADC 13.1FIPS before 13.1-37.163
- NetScaler ADC 12.1-FIPS before 12.1-55.300
- NetScaler ADC 12.1-NDcPP before 12.1-55.300
Related Threat Actor Activity – Malware identified in this campaign is generated beginning with the execution of a PowerShell script (123.ps1) which concatenates two base64 strings together, converts them to bytes, and writes them to the designated file path. The resulting file (adobelib.dll) is then executed by the PowerShell script using rundll32. Following the execution, the DLL attempts to send a POST request to https://adobe-us-updatefiles[.]digital/index.php which resolves to IP addresses 172.67.129[.]176 and 104.21.1[.]180 Although adobelib.dll and adobe-us-updatefiles[.]digital have the appearance of legitimacy, the file and domain have no association with legitimate Adobe software and no identified interaction with the software.
Additionally, other observed activities include the use of a variety of TTPs commonly associated with ransomware activity. LockBit 3.0 affiliates have been observed using AnyDesk and Splashtop remote management and monitoring (RMM), Batch and PowerShell scripts, the execution of HTA files using the Windows native utility mshta.exe and other common software tools typically associated with ransomware incidents.
Important Note for SafeBreach Customers – Coverage for AA23-325A (Citrix Bleed Vulnerability)
As soon as details were made available, the SafeBreach Labs teams mapped existing attacks and added new attacks to the Hacker’s Playbook immediately. It is important to note that existing SafeBreach customers already had a wide amount of coverage against the IOCs and TTPs being leveraged by the LockBit 3.0 threat actors. Please run/ re-run the attacks listed below to ensure your environments are protected against this malware variant.
NEW Behavioral Attacks Related to LockBit 3.0 Ransomware
- #1693 – Collect Windows system data using CMD
- #1011 – Discover Linux system information using Bash commands
- #6854 – Discover macOS system information
- #6996 – Steal Web Session Cookie (Windows)
- #6997 – Steal Web Session Cookie (Linux)
- #6998 – Steal Web Session Cookie (Mac)
NEW IOC-Based Attacks
- #9365 – Write LockBit3 (downloader) (974068) ransomware to disk
- #9366 – Pre-execution phase of LockBit3 (downloader) (974068) ransomware (Windows)
- #9367 – Transfer of LockBit3 (downloader) (974068) ransomware over HTTP/S
- #9368 – Transfer of LockBit3 (downloader) (974068) ransomware over HTTP/S
- #9369 – Email LockBit3 (downloader) (974068) ransomware as a compressed attachment
- #9370 – Email LockBit3 (downloader) (974068) ransomware as a compressed attachmen
- #9371 – Write LockBit3 (dll) (bcc994) ransomware to disk
- #9372 – Transfer of LockBit3 (dll) (bcc994) ransomware over HTTP/S
- #9373 – Transfer of LockBit3 (dll) (bcc994) ransomware over HTTP/S
- #9374 – Email LockBit3 (dll) (bcc994) ransomware as a compressed attachment
- #9375 – Email LockBit3 (dll) (bcc994) ransomware as a compressed attachment
NEW Vulnerability Exploitation Attack
- #9364 – Remote exploitation of Citrix Bleed vulnerability CVE-2023-4966 (WAF)
Existing IOC-Based Attacks Related to LockBit 3.0 Ransomware
- #8101 – Write LockBit3 (62db) ransomware to disk
- #8102 – Transfer of LockBit3 (62db) ransomware over HTTP/S
- #8103 – Transfer of LockBit3 (62db) ransomware over HTTP/S
- #8104 – Email LockBit3 (62db) ransomware as a compressed attachment
- #8105 – Email LockBit3 (62db) ransomware as a compressed attachment
- #8106 – Write LockBit3 (da37) ransomware to disk
- #8107 – Transfer of LockBit3 (da37) ransomware over HTTP/S
- #8108 – Transfer of LockBit3 (da37) ransomware over HTTP/S
- #8109 – Email LockBit3 (da37) ransomware as a compressed attachment
- #8110 – Email LockBit3 (da37) ransomware as a compressed attachment
- #8111 – Write LockBit3 (ab92) ransomware to disk
- #8112 – Transfer of LockBit3 (ab92) ransomware over HTTP/S
- #8113 – Transfer of LockBit3 (ab92) ransomware over HTTP/S
- #8114 – Email LockBit3 (ab92) ransomware as a compressed attachment
- #8115 – Email LockBit3 (ab92) ransomware as a compressed attachment
- #8116 – Write LockBit3 (ea95) ransomware to disk
- #8117 – Transfer of LockBit3 (ea95) ransomware over HTTP/S
- #8118 – Transfer of LockBit3 (ea95) ransomware over HTTP/S
- #8119 – Email LockBit3 (ea95) ransomware as a compressed attachment
- #8120 – Email LockBit3 (ea95) ransomware as a compressed attachment
- #8121 – Write LockBit3 (5a56) ransomware to disk
- #8122 – Transfer of LockBit3 (5a56) ransomware over HTTP/S
- #8123 – Transfer of LockBit3 (5a56) ransomware over HTTP/S
- #8124 – Email LockBit3 (5a56) ransomware as a compressed attachment
- #8125 – Email LockBit3 (5a56) ransomware as a compressed attachment
- #8126 – Write LockBit3 (0bd7) ransomware to disk
- #8127 – Transfer of LockBit3 (0bd7) ransomware over HTTP/S
- #8128 – Transfer of LockBit3 (0bd7) ransomware over HTTP/S
- #8129 – Email LockBit3 (0bd7) ransomware as a compressed attachment
- #8130 – Email LockBit3 (0bd7) ransomware as a compressed attachment
- #8131 – Write LockBit3 (32ce) ransomware to disk
- #8132 – Transfer of LockBit3 (32ce) ransomware over HTTP/S
- #8133 – Transfer of LockBit3 (32ce) ransomware over HTTP/S
- #8134 – Email LockBit3 (32ce) ransomware as a compressed attachment
- #8135 – Email LockBit3 (32ce) ransomware as a compressed attachment
- #8136 – Write LockBit3 (3f6e) ransomware to disk
- #8137 – Transfer of LockBit3 (3f6e) ransomware over HTTP/S
- #8138 – Transfer of LockBit3 (3f6e) ransomware over HTTP/S
- #8139 – Email LockBit3 (3f6e) ransomware as a compressed attachment
- #8140 – Email LockBit3 (3f6e) ransomware as a compressed attachment
- #8962 – Write LockBit3 (7a51) ransomware to disk
- #8963 – Pre-execution phase of LockBit3 (7a51) ransomware (Windows)
- #8964 – Transfer of LockBit3 (7a51) ransomware over HTTP/S
- #8965 – Transfer of LockBit3 (7a51) ransomware over HTTP/S
- #8966 – Email LockBit3 (7a51) ransomware as a compressed attachment
- #8967 – Email LockBit3 (7a51) ransomware as a compressed attachment
What You Should Do Now
The playbook has been updated with new attacks that map to the IOCs identified in this US-CERT Alert. SafeBreach customers can now validate their security controls against these TTPs and IOCs in multiple ways.
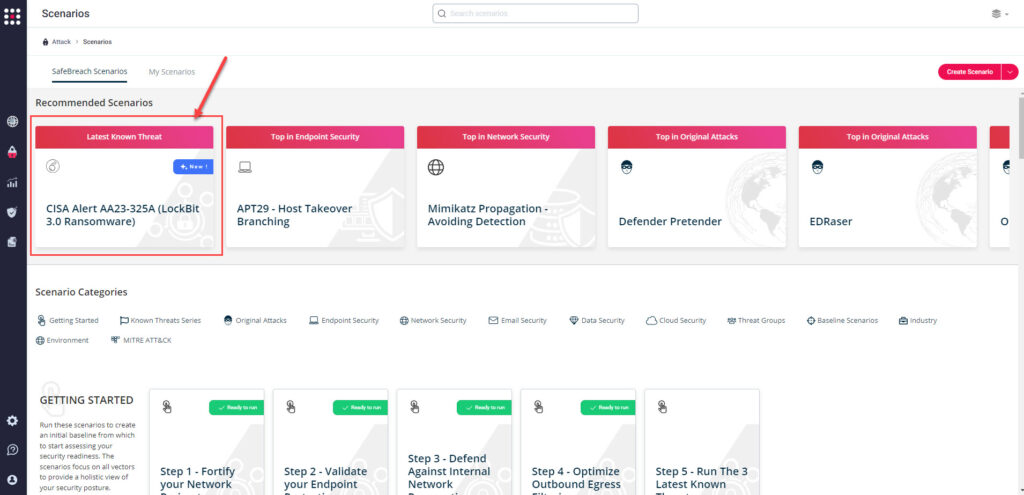
Method 1 – You can go to the “SafeBreach Scenarios” page and choose the AA23-325A (LockBit 3.0 Ransomware) scenario from the list of available scenarios.
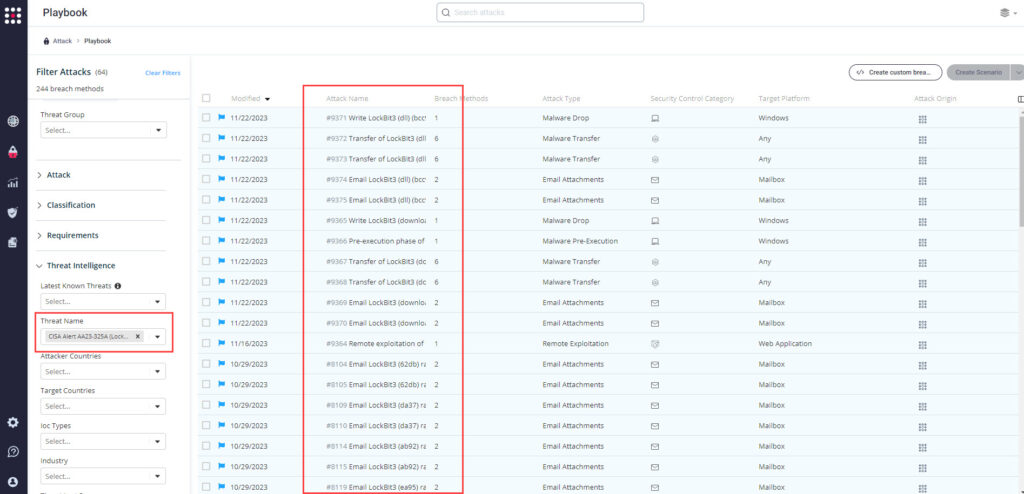
Method 2 – From the Attack Playbook, select and filter attacks related to US-CERT Alert AA23-325A. Additionally, you can refer to the list above as well to ensure a comprehensive level of coverage.
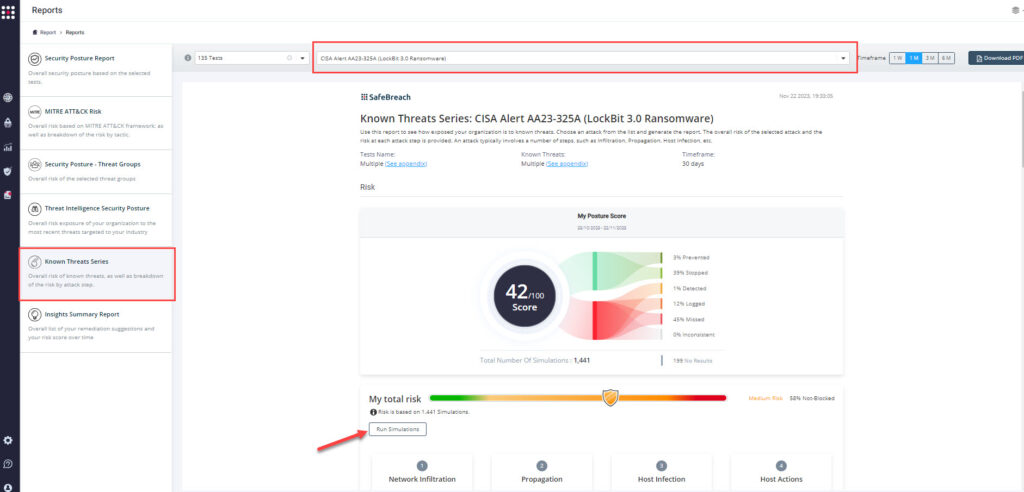
Method 3 – From the Known Attack Series report, select the AA23-325A (LockBit 3.0 Ransomware) report and select Run Simulations which will run all attack methods.
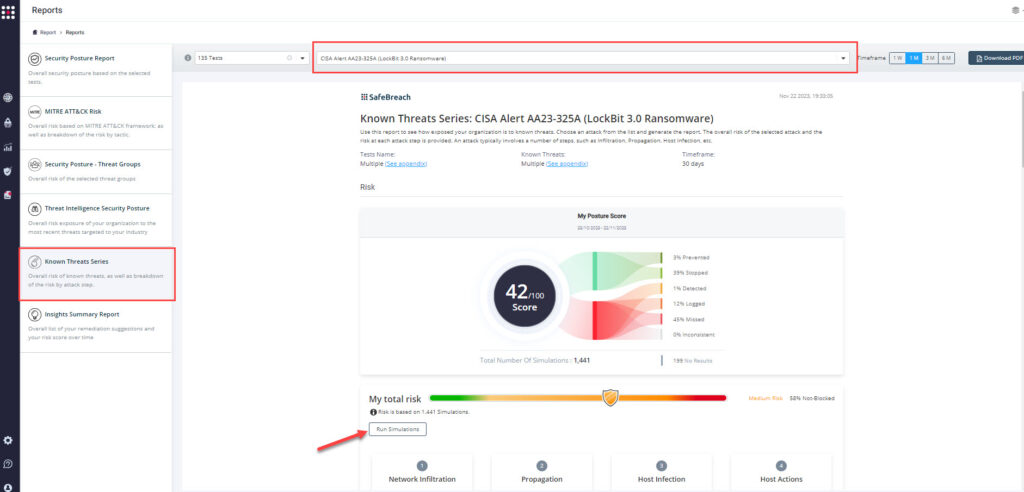
NOTE: CISA recommends continually validating your security program, at scale, in a production environment to ensure optimal performance against the growing threat of advanced cyber threats. Additional recommendations include:
- Isolate NetScaler ADC and Gateway appliances for testing until patching is ready and deployable.
- Secure remote access tools by implementing application controls to manage and control the execution of software.
- Strictly limit the use of RDP and other remote desktop services.
- Restrict the use of PowerShell.
- Enable enhanced PowerShell logging.
- For detailed information about mitigations and incident response, please refer to the full advisory
如有侵权请联系:admin#unsafe.sh
