2023-11-17 22:0:26 Author: www.sentinelone.com(查看原文) 阅读量:11 收藏
The Good | FBI Takes Down IPStorm Botnet
A botnet that had been running since 2019 infecting thousands of internet-connected devices around the world has been taken down, the FBI said this week. IPStorm was operated by Sergei Manikin, a Russian and Moldovan national, who has also pleaded guilty to three counts of computer fraud.
Unlike traditional botnets, IPStorm used a peer-to-peer network protocol known as Interplanetary File System (IPFS) to store and share data in a distributed file system, making it more resilient and harder to disrupt. Infected devices were turned into proxies for malicious activity by clients that Manikin sold access to through his public websites proxx.io and proxx.net.
By routing their internet traffic through the botnet, clients could conduct malicious activities anonymously. According to the FBI, customers paid hundreds of dollars a month to rent access to the botnet. Manikin is thought to have had over 23,000 paying customers and admitted to banking at least half a million dollars from the scheme.

Initially targeting Windows systems, over the years IPStorm expanded to targeting most major platforms, including macOS, Linux and Android devices across Asia, Europe and both North and South America, infecting at least 13,500 devices.
In announcing the take down, the FBI said that it had dismantled Manikin’s infrastructure, but their actions did not extend to informing victims or removing the botnet malware from infected devices.
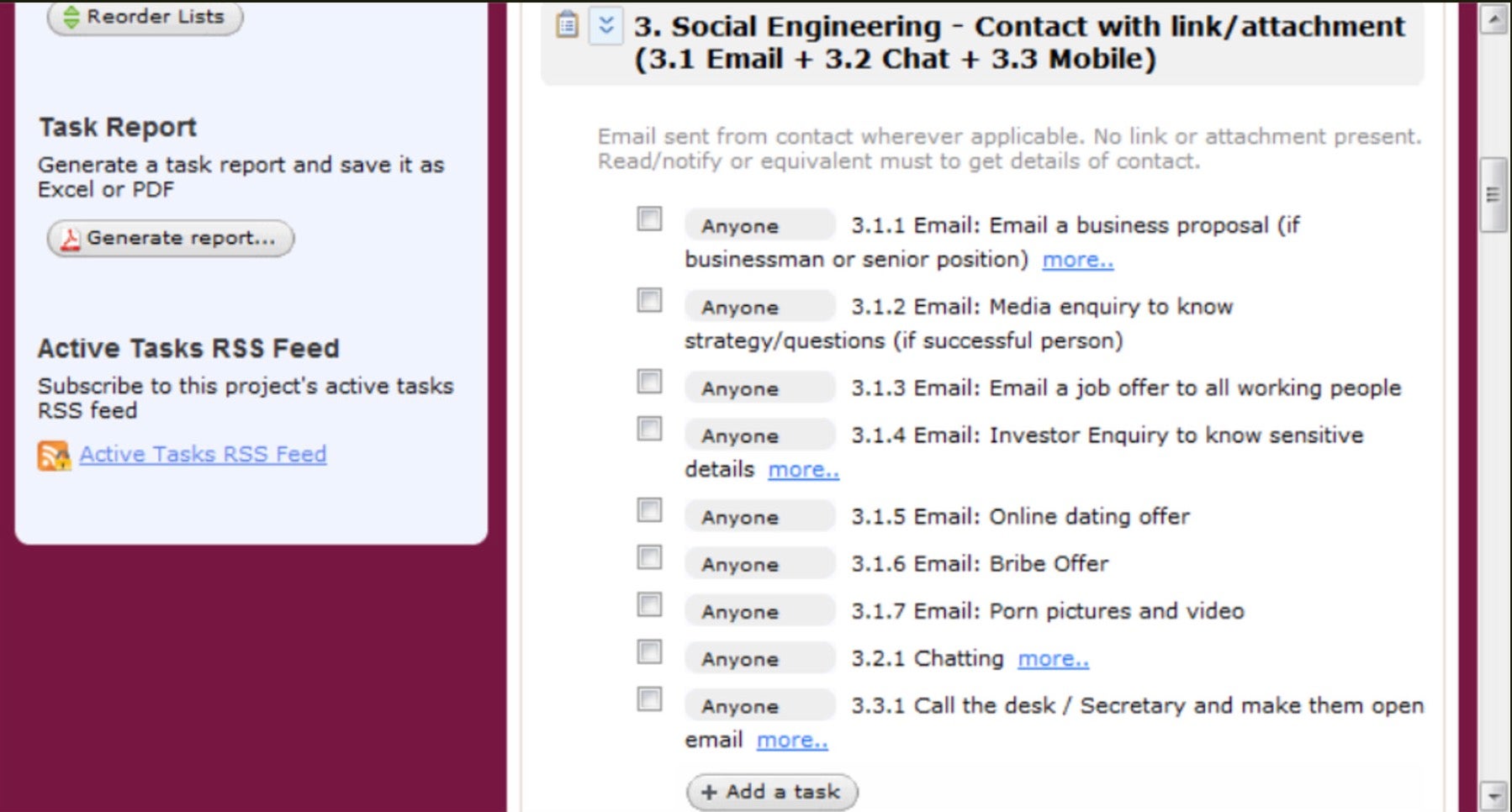
The Bad | Educational Startup Turned Into Cyber Espionage Actor
Research from Reuters and SentinelLabs this week revealed how an educational startup that began life teaching coding skills rapidly transformed into a global cyber espionage threat actor. Reuters revealed how Appin Security Group became a significant player in the Hack-for-Hire business and allegedly engaged in multiple high-profile hacks.
The company, founded by Rajat and Anuj Khare, was formed in 2003, and began as an educational outfit offering technology training courses in programming, robotics and cybersecurity. Between 2009 and 2013, the company was involved in offering offensive security and hack-for-hire operations.
Representatives of the Khare’s have denied engaging in illicit activities; however, researchers say that Appin developed a comprehensive set of hacking tools capable of spying, hacking email accounts and advanced social engineering. High profile operations included targeting Russian oligarch Boris Berezovsky, Malaysian politician Mohamed Azmin Ali, and U.S. House Intelligence Committee Chairman Kristi Rogers.
According to the research, Appin’s success was built on a sophisticated approach to managing and acquiring infrastructure, including purchasing mobile spyware from external contractors as well as developing in-house hacking tools, exploits and malware. The company offered clients an easy-to-use portal where they could make and manage requests for hacking operations.
SentinelLabs said that better international cooperation and legal frameworks were needed to effectively address the problem of private sector offensive actors, a market which has burgeoned in recent years in light of advancing technologies and growing demand for digital espionage services. Governments, businesses and high-profile individuals need to proactively protect themselves against such formidable actors.
The Ugly | ALPHV Files SEC Complaint Against Victim
Ransomware actor ALPHV has taken extortion to the next level by filing a complaint against one of its victims with the Securities and Exchange Commission (SEC), MeridianLink, whose data is listed on the ALPHV leak site.
According to reports, representatives of ALPHV say they breached MeridianLink on November 7th, in a data theft operation without ransomware. The attackers say the victim became aware of the breach the same day, but did not inform the SEC within 4 days – a new requirement that has yet to come into force. MeridianLink has since stated that the attack only came to light three days later on November 10th.
Today DissentDoe reported that ALPHV ransomware group submitted an official SEC complaint against MeridianLink for them not disclosing the breach … which was performed by ALPHV…
ALPHV shared the official SEC complaint with DissentDoe
More info: https://t.co/J5dEH3tyKU pic.twitter.com/maxplzJQQi
— vx-underground (@vxunderground) November 15, 2023
It seems unlikely that the complaint – filed under Item 1.05 of Form 8-K – will be upheld. Aside from the fact that MeridianLink disputes the date when it became aware of the breach, the rules are not set to come into effect until December.
It has been reported that MeridianLink was quick to patch the vulnerability used in the breach but has not proceeded with any ransom negotiations to date. The filing of the SEC complaint may be an attempt to generate more publicity about the breach, putting pressure on the victim by way of raising concerns about the stolen data among its clients and partners.
The incident underscores the lengths threat actors will go to achieve a payout. Extortion of businesses that fail to adequately secure their networks has developed rapidly since the initial phase of ransomware as simple file lockers. Data exfiltration and double extortion through leveraging public perception is the new playbook. Bringing regulatory compliance into the mix may be a little premature in this case, but the message to businesses should be clear: prevention is the primary cure in enterprise security.
如有侵权请联系:admin#unsafe.sh