
2023-11-11 01:38:52 Author: securityboulevard.com(查看原文) 阅读量:3 收藏

Before cybercriminals can steal sensitive data, they need unauthorized access to an organization’s systems and networks. As Ransomware-as-a-Service (RaaS) models evolve the threat landscape, initial access brokers (IABs) help threat actor groups selling ransomware by supplementing the malicious technology infrastructure with the access necessary to deploy the attack. Security teams defending against these attacks need a layered defense that considers all the different criminal entities involved in modern-day attacks.
By understanding what initial access brokers do and how they fit into RaaS models, security teams can improve their monitoring and detection capabilities.
What are Initial Access Brokers (IABs)?
Initial access brokers (IABs) are cyber threat actors who specialize in compromising networks so they can sell the access in underground forums across the dark web and illicit Telegram channels. IABs are often highly sophisticated and specialized threat actors who gain access to highly sensitive IT infrastructure.
IABs focus on gaining unauthorized access to networks by using various techniques, including:
- Phishing emails
- Brute-force attacks
- Password spraying
- Social engineering
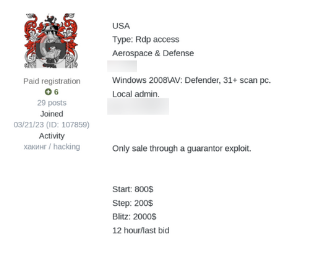
As organizations adopt more cloud-native technologies, compromising networks becomes more lucrative for malicious actors who specialize in gaining initial access. According to the MITRE ATT&CK Framework, initial access consists of the various techniques that attackers use when trying to gain a foothold within a network that later allows them to compromise sensitive data. As specialists, IABs create a business model focused on selling this access to other threat actors.
What are Credential Markets?
Credential markets on the dark web and illegal Telegram channels are where threat actors buy and sell stolen credentials that can include any of the following:
- User names
- Passwords
- Email addresses
- Other sensitive information
Once an IAB gains unauthorized access to a corporate network, they post the credentials on the market and look for other threat actors who want to use them when deploying an attack.
How Initial Access Brokers Gain Access
To protect against IABs, security teams need to know how the threat actors typically gain initial access.
Social Engineering
IABs use social engineering tactics to trick users into taking an action that’s against their best interests. Some examples of social engineering attacks include:
- Phishing: sending fake emails that appear to come from trusted sources, like vendors or non-profit organizations, that include malicious attachments or links
- Spear phishing: targeting specific people or groups within an organization and sending them fake emails that include malicious attachments or links
- CEO fraud: collecting information about a member of the senior leadership team to use when impersonating them as a way to trick people into providing information or performing a financial transaction
- Pretexting: impersonating a trusted person or entity to trick users into providing credentials, like pretending to be a member of the IT department trying to reset a password
Weak Passwords
Using automated tools, IABs systematically “guess” at combinations of emails and passwords to gain unauthorized access to internet-facing systems and applications, including:
- Software-as-a-Service (SaaS) applications
- Virtual Private Networks (VPNs)
- Remote Desktop Protocols (RDP)
- Secure Shell (SSH)
By gaining unauthorized access this way, IABs bypass network defenses and evade detection, making it harder for organizations to prevent other malicious actors from using the stolen credentials.
Vulnerabilities
Exploiting vulnerabilities in an organization’s IT infrastructure is another way that IABs gain initial access. Typically, they scan a target company’s network to identify:
- IP addresses with open ports
- Services running unpatched software
By automating these processes, they can operationalize their activities. For example, many IABs use Shodan, a search engine for vulnerable servers, so they can identify vulnerable IP addresses and prioritize attacking them.
How IABs Fit Into the Ransomware-as-a-Service (RaaS) Ecosystem
IABs are not a new type of threat actor, but they are becoming more sought after among the threat actor underground community. As organizations accelerated their cloud strategies, initial network access became increasingly important to malicious actors. Since IABs have a specialized skill set, they can make more money selling credentials to other threat actors than they would make if they perpetrated their own attacks.
The RaaS Model
The RaaS model mimics the Software-as-a-Service model, meaning that malicious actors sell ransomware packages and the associated infrastructure to other cybercriminals with two primary stakeholder identities:
- Operator: creates and sells the malicious code, campaign infrastructure, and services
- Affiliate: purchases the ransomware and deploys the attack
By selling the ransomware, the operators make more money than if they deployed it themselves. Meanwhile, it allows less technically experienced cybercriminals to deploy attacks.
IABs: Critical to RaaS
To exfiltrate data as part of a double extortion ransomware attack, malicious actors need to gain unauthorized access to the target victim’s networks. Ransomware operators purchase the initial access from IABs for several reasons, like the ability to:
- Provide affiliates with a comprehensive product that includes the access and malware
- Focus on updating the malicious code to evade signature-based security tools
- Scaling their criminal business operations to generate more revenue
RaaS Operators: Critical to IABs
IABs also benefit from these symbiotic relationships. IABs often start by advertising and selling their credentials on the dark web. However, as they gain a reputation within the community, they often begin working with one RaaS operator, essentially receiving a retainer for working exclusively with one group. This relationship protects the IABs by limiting their communications across the broader cybercrime ecosystem, ultimately hiding them from law enforcement or security teams monitoring the dark web.
How to Protect Against IABs
To protect against IABs, security teams need defense-in-depth strategies that include:
- Applying security updates regularly: Updating software, operating systems, and applications mitigates the risk that IABs will exploit known vulnerabilities.
- Implement email security: Using email security solutions that can detect and block malicious links and attachments can mitigate risks associated with phishing attacks.
- Provide security awareness training: Including a discussion of IABs, their strategies, and their impact in employee cybersecurity training modules can mitigate risks arising from human error because users have more information about what to look for.
- Enforce Multi-Factor Authentication (MFA): Adding another layer of security with MFA mitigates risks arising from IABs compromising weak passwords to gain unauthorized access.
- Monitor the dark web and illicit Telegram channels: Monitoring threat actor conversations can help identify previously unknown credential theft mitigating risks arising from IABs selling these to RaaS operators.
How Flare Can Help Monitor for External Threats
Flare collects and aggregates high-quality structured data from thousands of sources and provides automated event contextualization using AI language models. Our Continuous Threat Exposure Management (CTEM) platform monitors diverse sources that include Telegram, the traditional dark web (Tor), and I2P so that security teams can identify compromised credentials being sold online and optimize their threat detection tools with actionable alerts across our vast dataset. Organizations can begin enriching their security program in 30 minutes.
Flare enables security teams to gain key insights into their dark web exposure, enabling them to make threat-based decisions about their cybersecurity programs. Check out our free trial to learn more.
The post Initial Access Brokers (IAB): What You Need to Know appeared first on Flare | Cyber Threat Intel | Digital Risk Protection.
*** This is a Security Bloggers Network syndicated blog from Flare | Cyber Threat Intel | Digital Risk Protection authored by Flare. Read the original post at: https://flare.io/learn/resources/blog/initial-access-brokers/
如有侵权请联系:admin#unsafe.sh
