
2023-11-10 22:0:0 Author: www.tenable.com(查看原文) 阅读量:23 收藏

It’s “Critical Infrastructure Security and Resilience Month” – check out new resources from the U.S. government to better protect these essential organizations. Plus, the U.K.’s cyber agency is offering fresh guidance for mitigating the quantum computing threat. In addition, do you need a generative AI policy in your company? An ISACA guide could be helpful. And much more!
Dive into six things that are top of mind for the week ending November 10.
1 - U.S. focuses on critical infrastructure security in November
If critical infrastructure security is in your wheelhouse, November is a special month for you. Why? Again this year, the White House has declared November to be “Critical Infrastructure Security and Resilience Month.”
Although critical infrastructure protection encompasses various threats, such as natural disasters, it’s no surprise that a significant portion of the proclamation is devoted to preventing cybersecurity attacks.
“We know that to protect our critical infrastructure we must improve our cybersecurity,” the document reads.

As part of the effort, the Cybersecurity and Infrastructure Security Agency (CISA) called on all involved with critical infrastructure security to “resolve to be resilient.”
CISA also published a “Critical Infrastructure Security and Resilience Month Toolkit” that includes recommendations for private sector organizations, risk management agencies, state and local governments, and members of Congress.
The toolkit also contains links to many resources; communication templates for promoting “Critical Infrastructure Security and Resilience Month”; and an FAQ about protecting critical infrastructure.
To get more details, check out:
- The White House’s “Proclamation on Critical Infrastructure Security and Resilience Month, 2023”
- CISA’s announcement
- The home page for “Critical Infrastructure Security and Resilience Month”
- The “Critical Infrastructure Security and Resilience Month Toolkit”
CISA's Dr. David Mussington kicks off Critical Infrastructure Security Month
2 - “Shields Ready” campaign promotes critical infrastructure security
And as part of “Critical Infrastructure Security and Resilience Month,” CISA, the Department of Homeland Security and the Federal Emergency Management Agency (FEMA) have launched the “Shields Ready” campaign. It urges critical infrastructure organizations to beef up their resilience so they’re better prepared for cyberattacks and other threats.

Recommendations for critical infrastructure operators from the “Shields Ready” campaign include:
- Identify your most critical systems and assets, as well as the systems they depend on
- Assess the threats that could disrupt your operations and their consequences
- Draft strategic risk-management plans as well tactical incident response plans
- Test your incident response and recovery plans
The “Shields Ready” campaign complements other existing critical infrastructure security campaigns from CISA and FEMA.
To get more details about “Shields Ready,” check out:
- The joint announcement “DHS Unveils New Shields Ready Campaign to Promote Critical Infrastructure Security and Resilience”
- The “Shields Ready” homepage
- The “Shields Ready” factsheet
3 - U.K.’s cyber agency offers guidance about quantum threat
Is the threat from future quantum computers on your radar screen yet? By all accounts, it should be. The latest warning comes from the U.K. National Cyber Security Centre (NCSC).
Although “quantum resistant” algorithms are in the works, cybercriminals are swiping confidential data now to decrypt it later with quantum computers, which are expected to be available by around 2030.
In its new guidance, the NCSC offers best practices for mitigating the risk these powerful computers will pose to data encrypted with today’s public-key cryptographic (PKC) algorithms. The NCSC advice focuses on helping organizations adopt “post-quantum cryptography” or (PQC).
Also known as “quantum resistant” cryptography, these algorithms will be able to protect data from attacks that use quantum computers, but migrating to this new technology won’t be a simple process.
“These algorithms will not necessarily be drop-in replacements for the current PKC algorithms in protocols or systems, so system owners should begin planning for the migration to PQC,” reads the new NCSC white paper titled “Next steps in preparing for post-quantum cryptography.”
In short, while these new algorithms aren’t yet ready for prime time, organizations should start laying the groundwork for their adoption now.
To get all the details of the NCSC’s guidance, check out:
- The “Next steps in preparing for post-quantum cryptography” white paper
- The blog “Migrating to post-quantum cryptography”
For more information about the quantum threat:
- “Cybersecurity of Quantum Computing: A New Frontier” (Carnegie Mellon University)
- “Will Quantum Computers Become the Next Cyber-Attack Platform?” (InformationWeek)
- “Quantum apocalypse: Experts warn of ‘store now, decrypt later’ hacks” (Silicon Republic)
- “Now Is the Time to Plan for Post-Quantum Cryptography” (DarkReading)
- Quantum Computing and Post-Quantum Cryptography FAQ (U.S. National Security Agency)
VIDEOS
Post-Quantum Cryptography: the Good, the Bad, and the Powerful (NIST)
What is Quantum Cryptography? An Introduction (TechTarget)
NIST Post Quantum Cryptography Update (Accredited Standards Committee X9)
4 - A temperature check on cloud security
During our recent webinar “Tenable & Ermetic: What’s Next and Needed for Truly Effective Enterprise Cloud Security,” we polled participants on various cloud security topics. Here’s what they said when we asked them what their biggest cloud security challenges are, who’s in charge of cloud security at their organization and more.
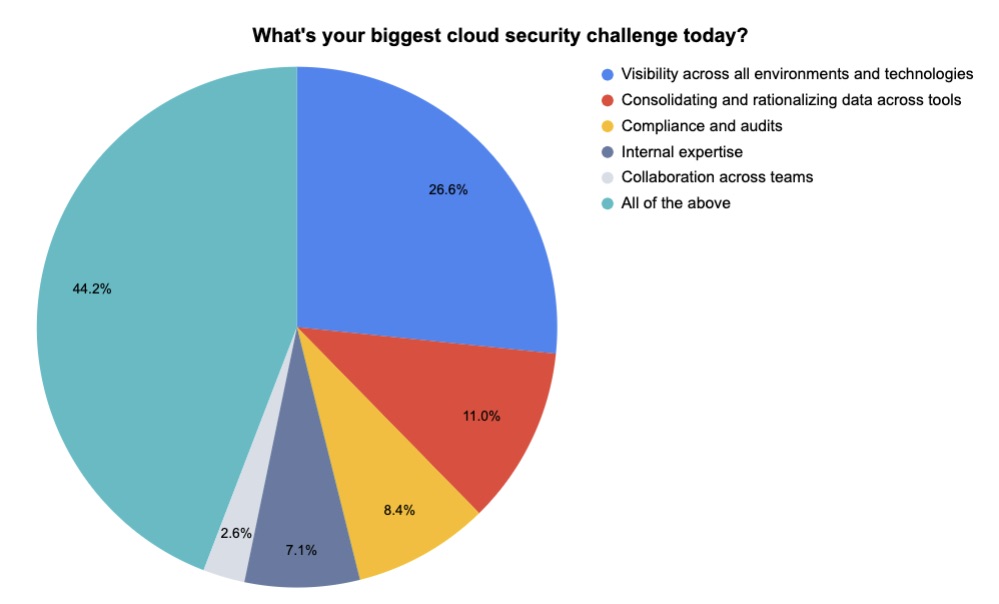 (154 respondents polled by Tenable in October 2023)
(154 respondents polled by Tenable in October 2023)
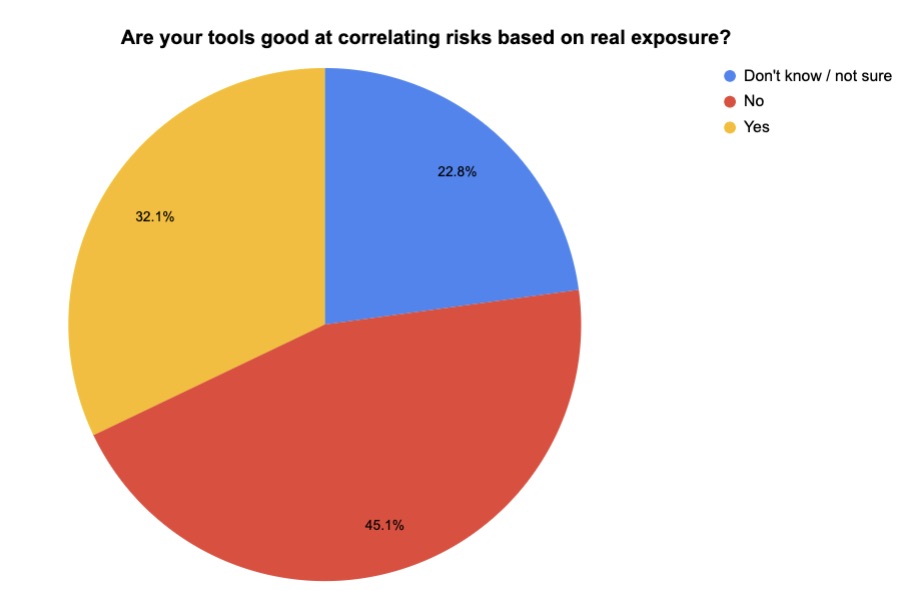 (162 respondents polled by Tenable in October 2023)
(162 respondents polled by Tenable in October 2023)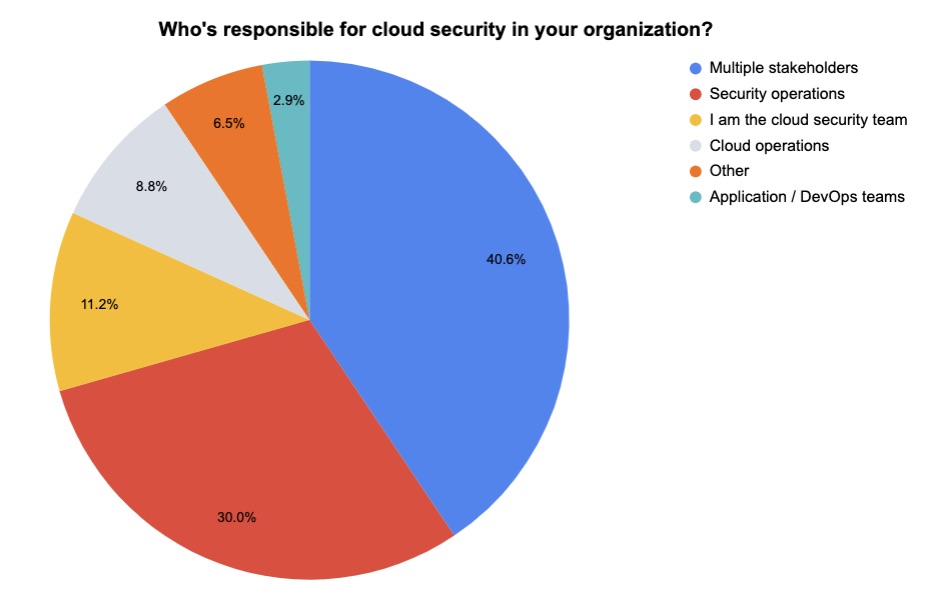
(170 respondents polled by Tenable in October 2023)
Want to find out what was discussed at the “Tenable & Ermetic: What’s Next and Needed for Truly Effective Enterprise Cloud Security” webinar? Watch it on demand!
5 - ISACA finds most orgs need a GenAI policy, offers guidelines
As a technology that’s seeing rapid evolution and robust adoption, generative AI represents a challenge for those tasked with drafting policies for its use.
If you work in cyber, compliance or risk management, chances are you’re involved in creating guardrails for your organization’s secure, compliant and legal use of generative AI.
If so, you might find relevant insights and recommendations in the new guide from ISACA titled “Considerations for Implementing a Generative Artificial Intelligence Policy.”
Here’s a small sampling of key considerations ISACA recommends should be taken into account:
- Are your generative AI systems secure and compliant with privacy regulations?
- Does the policy address ethical issues to ensure, for example, that the generative AI system doesn't create or reinforce biases?
- What are acceptable terms of use?
- Are there guidelines in place for proper data handling?
- How will the policy encourage transparency?
Along with the guide, ISACA conducted a poll that found that most organizations are using generative AI without having drafted an acceptable usage policy.
The study, based on a poll of 2,300 pros who work in audit, risk, security, data privacy and IT governance, found that:
- Only 28% of polled organizations say they officially allow employees to use generative AI
- Only 10% have a formal, comprehensive policy for generative AI use
- More than one in four lack a policy and have no plans to draft one
- 54% provide no AI training at all to employees
- Employees are using generative AI systems at 41% of organizations
To get more details, check out:
- The guide “Considerations for Implementing a Generative Artificial Intelligence Policy”
- The study announcement “AI Policies are Low, Use is High, and Adversaries are Taking Advantage, Says New AI Study”
- The study’s infographic “Generative AI: The Risks, Opportunities and Outlook”
- The blog “ISACA AI Survey Results: What Do Infosec Professionals REALLY Need to Know?”
6 - CIS updates Benchmarks for macOS, Microsoft 365, others
The Center for Internet Security has announced the updates it made to its CIS Benchmarks in October, including new secure configuration recommendations for Microsoft 365 and for several versions of macOS and Windows Server.

Here’s the full list of updated CIS Benchmarks for October:
- CIS AlmaLinux OS 8 Benchmark v3.0.0
- CIS Azure Kubernetes Service (AKS) Benchmark v1.4.0
- CIS Fortigate 7.0.x Benchmark v1.2.0
- CIS IBM AIX 7.2 Benchmark v1.1.0
- CIS IBM z/OS V2R5 with RACF Benchmark v1.1.0
- CIS Apple macOS 11.0 Big Sur Benchmark v4.0.0
- CIS Apple macOS 12.0 Monterey Benchmark v3.0.0
- CIS Apple macOS 13.0 Ventura Benchmark v2.0.0
- CIS Microsoft 365 Foundations Benchmark v3.0.0
- CIS Microsoft Intune for Windows 10 Benchmark v2.0.0
- CIS Microsoft Intune for Windows 11 Benchmark v2.0.0
- CIS Microsoft Windows Server 2012 (non-R2) Benchmark v3.0.0
- CIS Microsoft Windows Server 2012 R2 Benchmark v3.0.0
- CIS Microsoft Windows Server 2016 STIG Benchmark v2.0.0
- CIS MongoDB 5.0 Benchmark v1.2.0
- CIS MongoDB 6.0 Benchmark v1.1.0
- CIS Oracle Linux 8 Benchmark v3.0.0
- CIS Oracle MySQL Enterprise Edition 8.0 Benchmark v1.3.0
- CIS Red Hat Enterprise Linux 8 Benchmark v3.0.0
- CIS Rocky Linux 8 Benchmark v2.0.0
To get more details, read the CIS blog “CIS Benchmarks November 2023 Update.” For more information about the CIS Benchmarks list, check out its home page, as well as:
- “How to use CIS benchmarks to improve public cloud security” (TechTarget)
- “How to Unlock the Security Benefits of the CIS Benchmarks” (Tenable)
- “CIS Benchmarks Communities: Where configurations meet consensus” (HelpNet Security)
- “CIS Benchmarks: DevOps Guide to Hardening the Cloud” (DevOps)
CIS Benchmarks (CIS)

Juan Perez
Juan has been writing about IT since the mid-1990s, first as a reporter and editor, and now as a content marketer. He spent the bulk of his journalism career at International Data Group’s IDG News Service, a tech news wire service where he held various positions over the years, including Senior Editor and News Editor. His content marketing journey began at Qualys, with stops at Moogsoft and JFrog. As a content marketer, he's helped plan, write and edit the whole gamut of content assets, including blog posts, case studies, e-books, product briefs and white papers, while supporting a wide variety of teams, including product marketing, demand generation, corporate communications, and events.
Related Articles
- Center for Internet Security (CIS)
- Cloud
- Cybersecurity Snapshot
- Exposure Management
- Vulnerability Management
Cybersecurity News You Can Use
Enter your email and never miss timely alerts and security guidance from the experts at Tenable.
Tenable Vulnerability Management
Formerly Tenable.io
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy.
Your Tenable Vulnerability Management trial also includes Tenable Lumin and Tenable Web App Scanning.
Tenable Vulnerability Management
Formerly Tenable.io
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy. Purchase your annual subscription today.
100 assets
Choose Your Subscription Option:
Thank You
Thank you for your interest in Tenable.io. A representative will be in touch soon.
Try Tenable Nessus Professional Free
FREE FOR 7 DAYS
Tenable Nessus is the most comprehensive vulnerability scanner on the market today.
NEW - Tenable Nessus Expert
Now Available
Nessus Expert adds even more features, including external attack surface scanning, and the ability to add domains and scan cloud infrastructure. Click here to Try Nessus Expert.
Fill out the form below to continue with a Nessus Pro Trial.
Buy Tenable Nessus Professional
Tenable Nessus is the most comprehensive vulnerability scanner on the market today. Tenable Nessus Professional will help automate the vulnerability scanning process, save time in your compliance cycles and allow you to engage your IT team.
Buy a multi-year license and save. Add Advanced Support for access to phone, community and chat support 24 hours a day, 365 days a year.
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy.
Your Tenable Vulnerability Management trial also includes Tenable Lumin and Tenable Web App Scanning.
BUY
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy. Purchase your annual subscription today.
100 assets
Choose Your Subscription Option:
Thank You
Thank you for your interest in Tenable.io. A representative will be in touch soon.
Try Tenable Web App Scanning
Formerly Tenable.io Web Application Scanning
Enjoy full access to our latest web application scanning offering designed for modern applications as part of the Tenable One Exposure Management platform. Safely scan your entire online portfolio for vulnerabilities with a high degree of accuracy without heavy manual effort or disruption to critical web applications. Sign up now.
Your Tenable Web App Scanning trial also includes Tenable Vulnerability Management and Tenable Lumin.
Buy Tenable Web App Scanning
Formerly Tenable.io Web Application Scanning
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy. Purchase your annual subscription today.
Try Tenable Lumin
Visualize and explore your exposure management, track risk reduction over time and benchmark against your peers with Tenable Lumin.
Your Tenable Lumin trial also includes Tenable Vulnerability Management and Tenable Web App Scanning.
Buy Tenable Lumin
Contact a Sales Representative to see how Tenable Lumin can help you gain insight across your entire organization and manage cyber risk.
Thank You
Thank you for your interest in Tenable Lumin. A representative will be in touch soon.
Request a demo of Tenable Security Center
Formerly Tenable.sc
Please fill out this form with your contact information.
A sales representative will contact you shortly to schedule a demo.
* Field is required
Request a demo of Tenable OT Security
Formerly Tenable.ot
Get the Operational Technology Security You Need.
Reduce the Risk You Don’t.
Request a demo of Tenable Identity Exposure
Formerly Tenable.ad
Continuously detect and respond to Active Directory attacks. No agents. No privileges.
On-prem and in the cloud.
Request a Demo of Tenable Cloud Security
Exceptional unified cloud security awaits you!
We’ll show you exactly how Tenable Cloud Security helps you deliver multi-cloud asset discovery, prioritized risk assessments and automated compliance/audit reports.
See
Tenable One
In Action
Exposure management for the modern attack surface.
See Tenable Attack Surface Management In Action
Formerly Tenable.asm
Know the exposure of every asset on any platform.
Thank You
Thank you for your interest in Tenable Attack Surface Management. A representative will be in touch soon.
Try Tenable Nessus Expert Free
FREE FOR 7 DAYS
Built for the modern attack surface, Nessus Expert enables you to see more and protect your organization from vulnerabilities from IT to the cloud.
Already have Tenable Nessus Professional?
Upgrade to Nessus Expert free for 7 days.
Buy Tenable Nessus Expert
Built for the modern attack surface, Nessus Expert enables you to see more and protect your organization from vulnerabilities from IT to the cloud.
Try Nessus Expert Free
FREE FOR 7 DAYS
Built for the modern attack surface, Nessus Expert enables you to see more and protect your organization from vulnerabilities from IT to the cloud.
Already have Nessus Professional?
Upgrade to Nessus Expert free for 7 days.
Buy Tenable Nessus Expert
Built for the modern attack surface, Nessus Expert enables you to see more and protect your organization from vulnerabilities from IT to the cloud.
如有侵权请联系:admin#unsafe.sh