This blog is part of a series where my goal is to offer you a practical overview of SAP Integ 2023-11-10 12:53:22 Author: blogs.sap.com(查看原文) 阅读量:6 收藏
This blog is part of a series where my goal is to offer you a practical overview of SAP Integration Suite, Advanced Event Mesh. As I continue to write more blogs, I will provide summaries on the page below.
Advanced Event Mesh: Create your first event broker
Authentication
SAP Integration Suite, Advanced Event Mesh provides various types of client authentication for producers and consumers to connect to the broker.
- Basic
- OAuth
- Certificate
Basic authentication is the default mode, and you can activate the others yourself. On your broker, click on “Authentication” in the Event Broker Service Settings.

Enable your preferred client authentication method, save the changes, and navigate to Access Control.

On Access Control, you can configure profiles (roles) to restrict access and authorizations on the broker. You can also create clients for basic authentication, set up certificates, and configure OAuth.

To create a user for basic authentication, navigate to Client Usernames and click on the create button.

Inform profiles (roles) and set a password. After that, you will be able to authenticate on the broker with your new user.

You can test the user connection using the ‘Try me’ panel.

For OAuth authentication, the broker requires you to have an OAuth provider, as the platform does not have one. You can have more than one OAuth profile, meaning more than one OAuth provider set up to authenticate your applications. Since I don’t have any, I’m using the BTP XSUAA service to demonstrate how it works.
Create a XSUAA service.


Generate credentials to obtain the OAuth endpoint, client ID, and secret for testing.

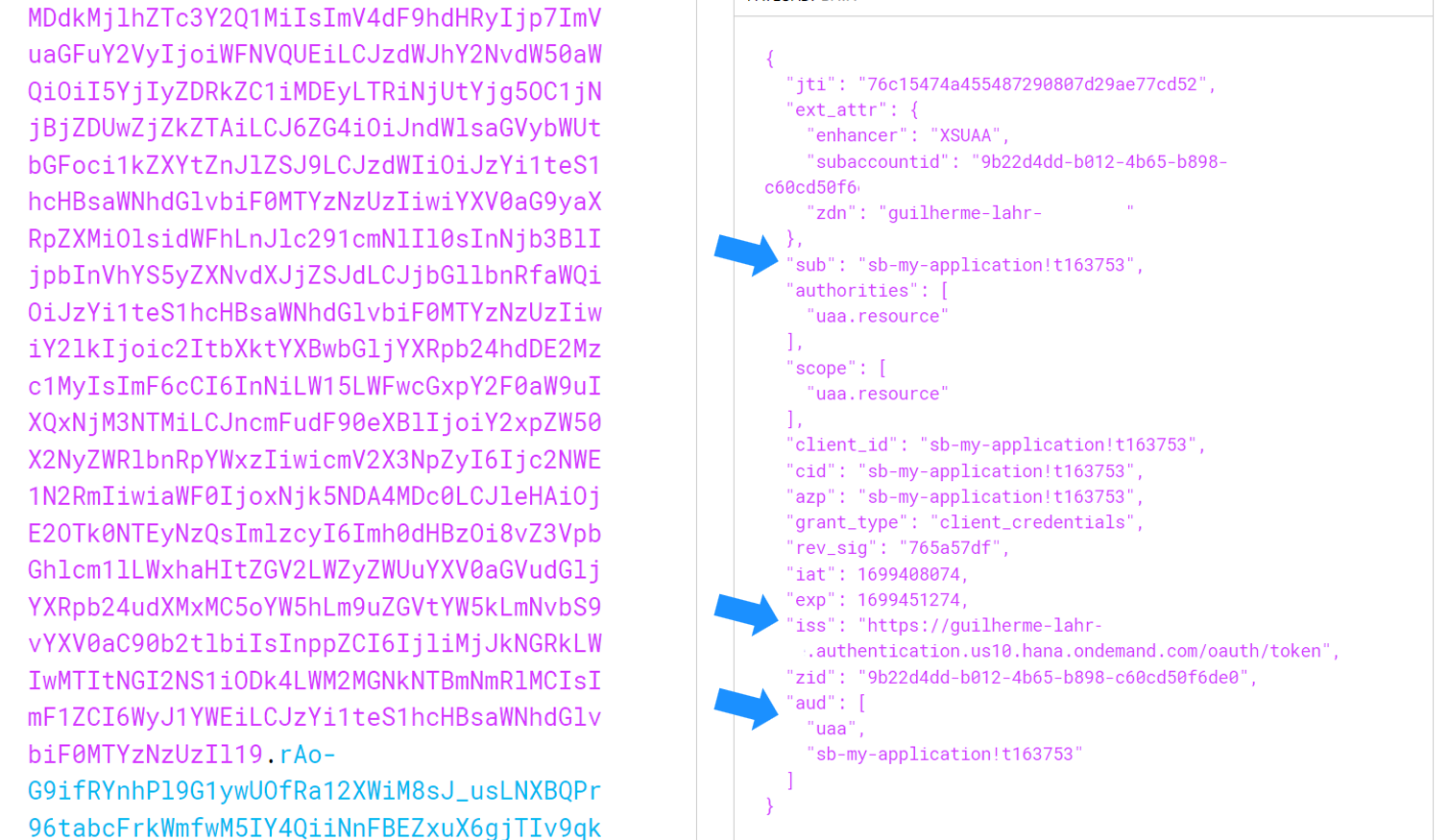
If you are using another OAuth Provider and are unsure about the structure of your token, you can obtain one using Insomnia / Postman and then visit jwt.io to analyze it.

Structure of the token.

Back to AEM, create an OAuth profile.

Set the OAuth role as ‘Resource Serve.’ In the structure of the token, there is a property named ‘iss,’ which is the issuer identifier. Use it to fill in the corresponding field in AEM.
There are a few endpoints that we need to fill in. Since the OAuth provider on BTP has a discovery endpoint, we can simply use it and skip the others. Check yours by adding /.well-known/oauth-authorization-server.

Specify groups and the username claim name.
‘sub‘ refers to the subject, usually the user ID.
‘aud‘ refers to the audience; I’m using it as a group and using its value (‘uaa‘) to control authorizations on the broker.
You can also enable the broker to validate your token.

As the OAuth profile is done, it is required to create an authorization group to validate access. It uses information inside the ‘aud‘ property. In my case, I just have two values: ‘uaa‘ and the application name (sb-my-application!t163753). Since I want a common configuration for all my applications connecting to the broker, I will use ‘uaa‘ as my authorization group.


Your client application must first obtain the OAuth token using the XSUAA services and then send it to the broker. The broker will validate the token on BTP.
In your code, change the ‘authenticationScheme’ property to ‘OAUTH2’ and pass the token as ‘idToken’.

On the ‘Clients’ tab, you can identify how many applications are connected to your broker.

In the next blog, we will explore Event Mesh.
如有侵权请联系:admin#unsafe.sh