2023-11-9 20:38:31 Author: securityaffairs.com(查看原文) 阅读量:4 收藏
CISA adds SLP flaw to its Known Exploited Vulnerabilities catalog
Pierluigi Paganini
November 09, 2023

US CISA added the vulnerability CVE-2023-29552 in the Service Location Protocol (SLP) to its Known Exploited Vulnerabilities catalog.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) added the vulnerability CVE-2023-29552 (CVSS score: 7.5) in the Service Location Protocol (SLP) to its Known Exploited Vulnerabilities catalog.
The Service Location Protocol (SLP) is a legacy service discovery protocol that allows computers and other devices to find services in a local area network without prior configuration.
The vulnerability CVE-2023-29552 is a denial-of-service (DoS) issue, it can be exploited by an unauthenticated, remote attacker to register arbitrary services. An attacker can exploit the flaw to use spoofed UDP traffic to conduct a denial-of-service attack with a significant amplification factor.
According to Binding Operational Directive (BOD) 22-01: Reducing the Significant Risk of Known Exploited Vulnerabilities, FCEB agencies have to address the identified vulnerabilities by the due date to protect their networks against attacks exploiting the flaws in the catalog.
Experts recommend also private organizations review the Catalog and address the vulnerabilities in their infrastructure.
CISA orders federal agencies to fix this flaw by November 29, 2023.
The vulnerability was disclosed by Bitsight and Curesec in April, 2023. Researchers from Bitsight and Curesec reported that attackers exploiting this flaw can leverage vulnerable instances to launch massive Denial-of-Service (DoS) amplification attacks. The experts pointed out that the flaw can allow achieving an amplification factor as high as 2200 times, which is one of the largest amplification attacks ever reported.
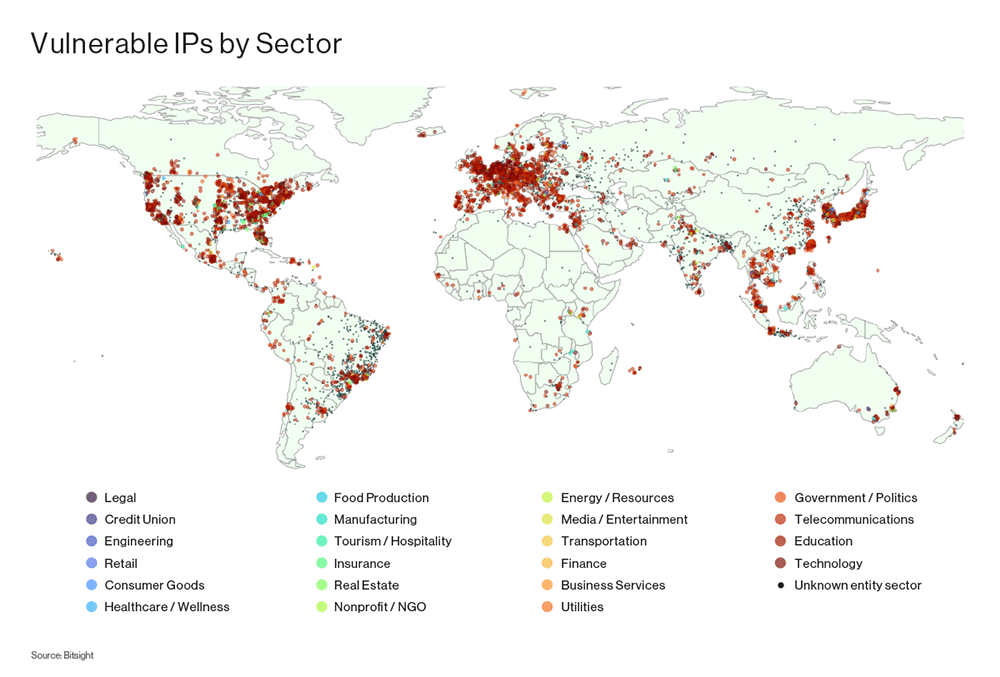
The vulnerability impacts more than 2,000 organizations worldwide and over 54,000 SLP instances that are publicly exposed to the Internet, including VMWare ESXi Hypervisor, Konica Minolta printers, Planex Routers, IBM Integrated Management Module (IMM), SMC IPMI, and 665 other product types.

Bitsight reported the flaw to the U.S. Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency (CISA) and impacted organizations.
In a reflective DoS amplification attack, the attacker sends small requests to a server with the spoofed source IP address of the victim. In turn, the server replies to the victim’s IP address, sending much larger responses than the requests, generating large amounts of traffic to the victim’s system.
The experts warn that threat actors will start conducting reflective DoS amplification attacks leveraging CVE-2023-29552 in the coming weeks.
Most of vulnerable SLP instances are in the U.S., the U.K., Japan, Germany, Canada, France, Italy, Brazil, the Netherlands, and Spain.
“To protect against CVE-2023-29552, SLP should be disabled on all systems running on untrusted networks, like those directly connected to the Internet. If that is not possible, then firewalls should be configured to filter traffic on UDP and TCP port 427. This will prevent external attackers from accessing the SLP service.” concludes the report.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, CISA)
如有侵权请联系:admin#unsafe.sh