
Users of SysAid on-premises should take action to deal with a vulnerability. SysAid is a widely used IT service management solution that allows IT teams to manage tasks.
Microsoft discovered an ongoing exploitation of a zero-day vulnerability in the SysAid IT support software in limited attacks by Lace Tempest. Lace Tempest is an initial access broker (IAB) usually associated with the Cl0p ransomware.
Once SysAid were notified by Microsoft on November 2, 2023, they started an investigation which confirmed that it was indeed a zero-day vulnerability. By definition, a zero-day vulnerability is any software vulnerability exploitable by hackers that doesn’t have a patch yet.
The investigation identified a previously unknown path traversal vulnerability leading to code execution within the SysAid on-prem software. Path traversal vulnerabilities allow attackers to read, and possibly write to, restricted files by inputting path traversal sequences like ../ into file or directory paths.
The attackers used the vulnerability to upload a web shell and other payloads into the web root of the SysAid Tomcat web service. Tomcat is an open-source web server and servlet developed by the Apache Software Foundation. A web shell is a malicious script used by an attacker with the intent to escalate and maintain persistent access on an already compromised web application.
The web shell provided the attacker with unauthorized access and control over the affected system. The attackers then used two PowerShell scripts to expand their hold. One to launch the Gracewire malware loader and the other to erase other evidence of the intrusion.
The Common Vulnerabilities and Exposures (CVE) database lists publicly disclosed computer security flaws. The CVE assigned to this vulnerability is:
CVE-2023-47246: a path traversal vulnerability that affects all SysAid On-Premises installations running versions before 23.3.36. SysAid Cloud customers are not affected by this vulnerability.
If you are a SysAid customer using a SysAid On-Prem server, you are under advise you to ensure that your SysAid systems are updated to version 23.3.36 or later, which includes the patches for the identified vulnerability.
Organizations using SysAid should apply the patch as soon as possible and look for any signs of exploitation prior to patching (see Indicators of Compromise below). The Lace Tempest group exploited the vulnerability in the SysAid software to deliver a malware loader for the Gracewire malware. Once this foothold is established, it’s usually followed by human-operated activity, including lateral movement, data theft, and ransomware deployment.
You should also review any credentials or other information that would have been available to someone with full access to your SysAid server and check any relevant activity logs for suspicious behavior.
IOCs
File:
b5acf14cdac40be590318dee95425d0746e85b1b7b1cbd14da66f21f2522bf4d Malicious loader
IPs:
81.19.138.52 GraceWire Loader C2
45.182.189.100 GraceWire Loader C2
179.60.150.34 Cobalt Strike C2
45.155.37.105 Meshagent remote admin tool C2
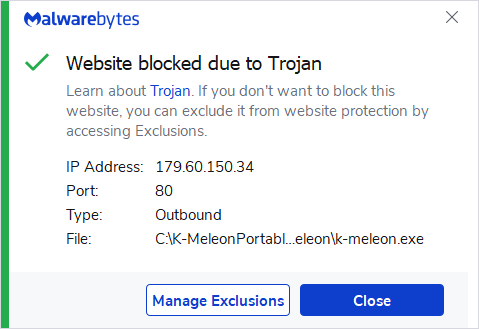
Malwarebytes blocks the Cobalt Strike C2 179.60.150.34
File Paths:
C:\Program Files\SysAidServer\tomcat\webapps\usersfiles\user.exe
C:\Program Files\SysAidServer\tomcat\webapps\usersfiles.war
C:\Program Files\SysAidServer\tomcat\webapps\leave
How to avoid ransomware
- Block common forms of entry. Create a plan for patching vulnerabilities in internet-facing systems quickly; and disable or harden remote access like RDP and VPNs.
- Prevent intrusions. Stop threats early before they can even infiltrate or infect your endpoints. Use endpoint security software that can prevent exploits and malware used to deliver ransomware.
- Detect intrusions. Make it harder for intruders to operate inside your organization by segmenting networks and assigning access rights prudently. Use EDR or MDR to detect unusual activity before an attack occurs.
- Stop malicious encryption. Deploy Endpoint Detection and Response software like Malwarebytes EDR that uses multiple different detection techniques to identify ransomware, and ransomware rollback to restore damaged system files.
- Create offsite, offline backups. Keep backups offsite and offline, beyond the reach of attackers. Test them regularly to make sure you can restore essential business functions swiftly.
- Don’t get attacked twice. Once you’ve isolated the outbreak and stopped the first attack, you must remove every trace of the attackers, their malware, their tools, and their methods of entry, to avoid being attacked again.
Our business solutions remove all remnants of ransomware and prevent you from getting reinfected. Want to learn more about how we can help protect your business? Get a free trial below.
