2023-11-3 20:46:43 Author: securityboulevard.com(查看原文) 阅读量:4 收藏
This instructional article will demonstrate the 34SP doo configuration process of Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM) Signatures to ensure 34SP passes the DMARC alignment check and eliminate spam from your domain and increase security.
The SPF record identifies the mail servers and domains that are allowed to send email on behalf of your domain. The DKIM record, on the other hand, is a specially formatted DNS TXT record that stores the public key the receiving mail server will use to verify a message’s signature. These email authentication methods will be used to prove to ISPs and mail services that senders are truly authorized to send email from a particular domain and are a way of verifying your email sending server is sending emails through your domain.
The process of configuring SPF
To ensure proper SPF configuration for 34SP, reach out to 34SPF’s support team. They will be able to guide you through the process of configuring SPF settings for your domain accurately.
The process of configuring DKIM
In order to authenticate 34SP on DKIM, please follow these steps:
- Login to your account in your 34SP platform
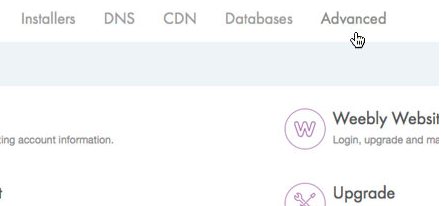
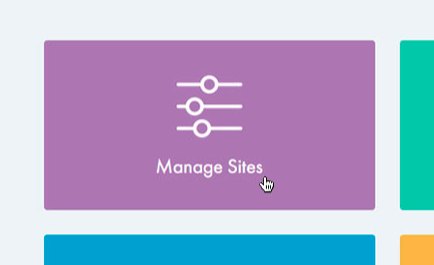
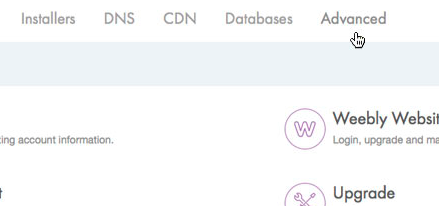
2. Choose Manage Sites > Advanced > DomainKeys Identified Mail in your dashboard
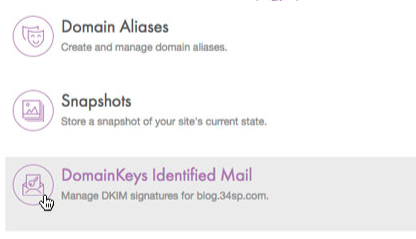
3. Click Enable DKIM
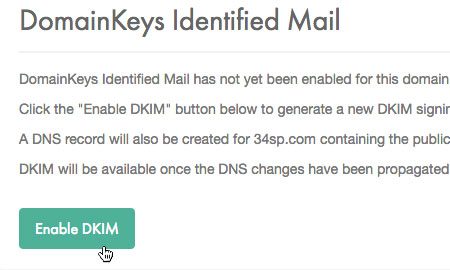
4. Please follow the on-screen instructions provided there and add the provided DKIM record in your DNS zone.
Congratulations, you now successfully authenticated your outgoing mail stream from 34SP with SPF and DKIM.
The post 34SP SPF and DKIM configuration: Step by Step guideline appeared first on EasyDMARC.
*** This is a Security Bloggers Network syndicated blog from EasyDMARC authored by EasyDmarc. Read the original post at: https://easydmarc.com/blog/34sp-spf-and-dkim-configuration-step-by-step-guideline/
如有侵权请联系:admin#unsafe.sh
