2023-11-3 16:59:29 Author: securityaffairs.com(查看原文) 阅读量:6 收藏
MuddyWater has been spotted targeting two Israeli entities
Pierluigi Paganini
November 03, 2023

Iran-linked cyberespionage group MuddyWater is targeting Israeli entities in a new spear-phishing campaign.
Iran-linked APT group MuddyWater (aka SeedWorm, TEMP.Zagros, and Static Kitten) is targeting Israeli entities in a new spear-phishing campaign, Deep Instinct’s Threat Research team reported. The phishing messages were aimed at deploying a legitimate remote administration tool called Advanced Monitoring Agent. This is the first time that the Iranian APT has employed the N-able’s remote monitoring software. The experts observed the threat actors targeting two Israeli organizations.
“On October 30th Deep Instinct identified two archives hosted on “Storyblok” containing a new multi-stage infection vector.” reads the report published by Deep Instinct. “It contains hidden files, an LNK file that initiates the infection, and an executable file designed to unhide a decoy document while executing Advanced Monitoring Agent, a remote administration tool.”
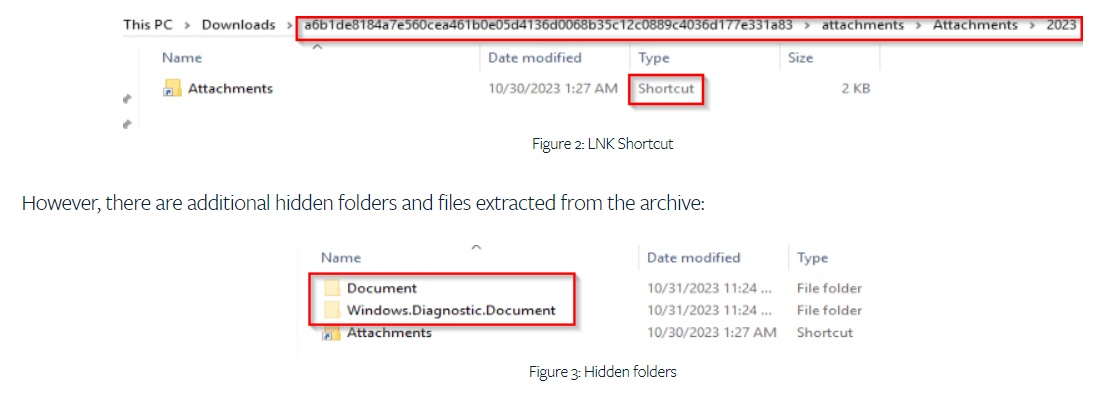
Upon extracting the archive, several folders must be navigated until a LNK shortcut appearing as another folder named “Attachments.” Experts also noticed additional hidden folders and files extracted from the archive.

Once the victim opens the LNK file, the infection chain starts by executing an executable (“Diagnostic.exe”) from one of the hidden directories.
The file “Diagnostic.exe” is used to execute a second executable, called “Windows.Diagnostic.Document.EXE,” which is located in the hidden directory named “.end” under a “Windows.Diagnostic.Document” hidden directory.
The executable “Windows.Diagnostic.Document.EXE” is a signed, legitimate installer for “Advanced Monitoring Agent.”
“In addition to executing the remote administration tool, “Diagnostic.exe” also opens a new Windows Explorer window of the hidden “Document” folder. This is done to fool the victim that opened the LNK file into thinking that it was indeed a folder.” continues the report.
The threat actors used an official memo from the Israeli Civil Service Commission as a decoy document.
The document describes what to do in case a government worker expresses opinions against the Israeli state on social networks.
“MuddyWater continues to attack Israeli targets in various ongoing campaigns.” concludes the report. “In this campaign, MuddyWater employs updated TTPs. These include a new public hosting service, employing a LNK file to initiate the infection, and utilizing intermediate malware that mimics the opening of a directory while executing a new remote administration tool.”
The first MuddyWater campaign was observed in late 2017, when the APT group targeted entities in the Middle East.
The experts called the campaign ‘MuddyWater’ due to the confusion in attributing a wave of attacks that took place between February and October 2017 targeting entities in Saudi Arabia, Iraq, Israel, United Arab Emirates, Georgia, India, Pakistan, Turkey, and the United States to date. The group evolved over the years by adding new attack techniques to its arsenal. Over the years the APT group also has also targeted European and North American nations.
The group’s victims are mainly in the telecommunications, government (IT services), and oil sectors.
In January 2022, US Cyber Command (USCYBERCOM) officially linked the MuddyWater APT group to Iran’s Ministry of Intelligence and Security (MOIS).
According to the joint report published by UK and US agencies, MuddyWater is targeting organizations in multiple sectors, including telecommunications, defense, local government, and oil and natural gas in Asia, Africa, Europe, and North America.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, IRAN)
如有侵权请联系:admin#unsafe.sh