Automating the enforcement of least-privilege access brings numerous advantages to companies, encompassing heightened security, heightened operational efficiency, and improved compliance.
By automating the process of granting and revoking access, organizations can drastically diminish the risk of unauthorized privileges, ensuring that employees possess only the resources essential for their specific roles. This minimizes the attack surface and reduces the potential consequences of security incidents.
Additionally, automation eliminates the necessity for laborious manual procedures, enabling employees to swiftly acquire the necessary access. By streamlining the processes of access requests, approvals, and provisioning, companies can enhance operational efficiency while alleviating the administrative workload on IT and security teams.
Problems with Manual Provisioning
In many organizations, IT and security teams contend with constrained resources and a backlog of responsibilities. Assigning individuals to manually evaluate temporary elevation requests is not the most efficient allocation of skilled resources and can lead to natural delays. Coupled with the stress and frustration experienced by requestors justifying their needs and waiting for permissions, this results in a recurrent, stressful situation that does not align with business requirements.
Achieving Least-Privilege Access in the Cloud
A centralized automated system for requesting and granting permissions, monitoring their utilization, and ultimately revoking privileges can be immensely helpful. An automated Just-In-Time (JIT) mechanism can bridge gaps created by manual processes and reduce friction and administrative overhead. Automated monitoring and auditing of JIT access prove valuable in verifying the absence of inadvertent misconfigurations and facilitating rapid incident investigations when necessary.
The following are three action items every organization should follow:
1. Utilize Self-Service Access
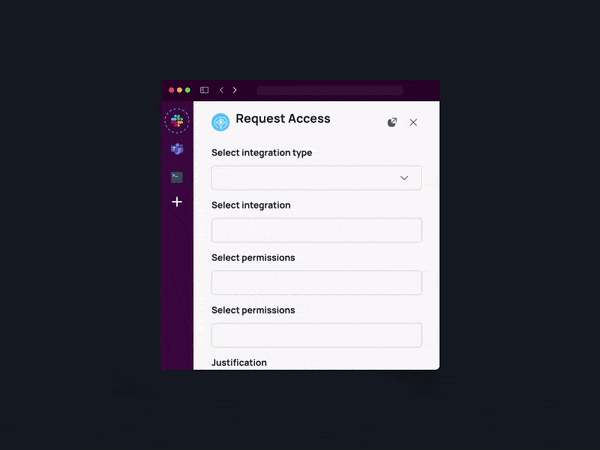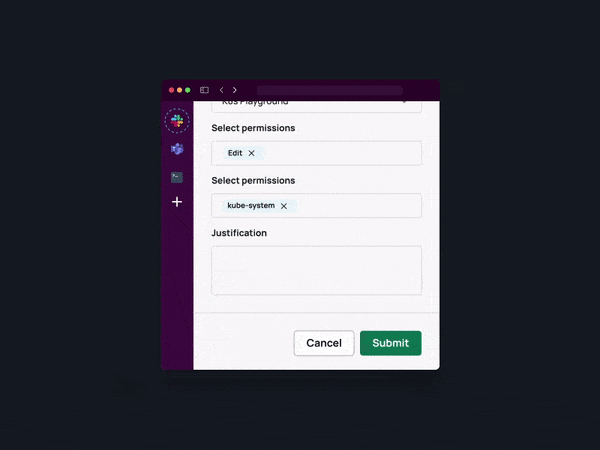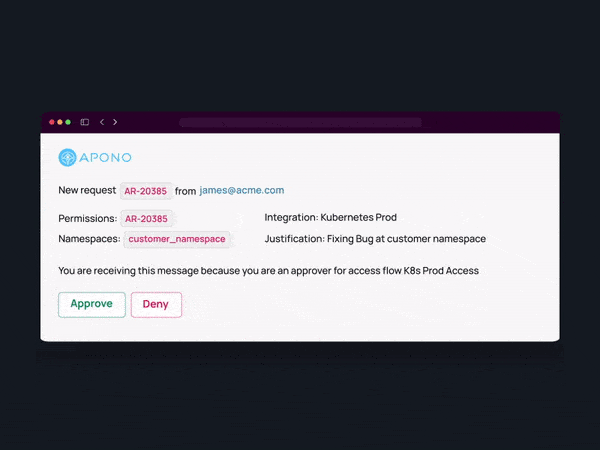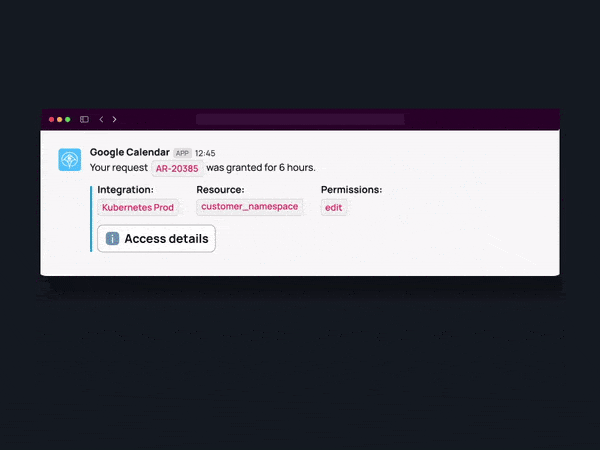
Implementing a self-service approach to access management is pivotal in empowering the workforce and diminishing reliance on IT and security teams. By offering employees a user-friendly self-service portal, companies can facilitate access requests to cloud resources, applications, and data as needed.
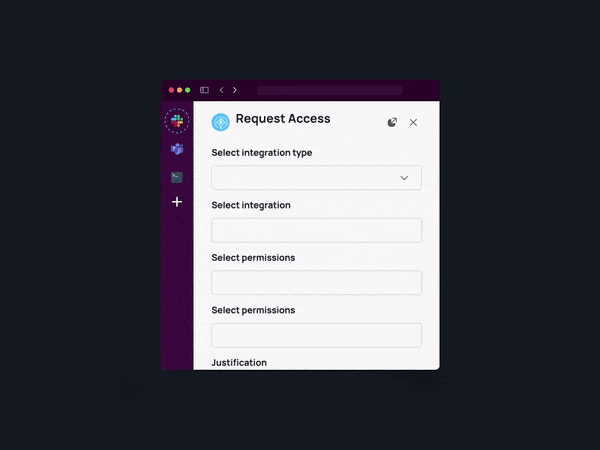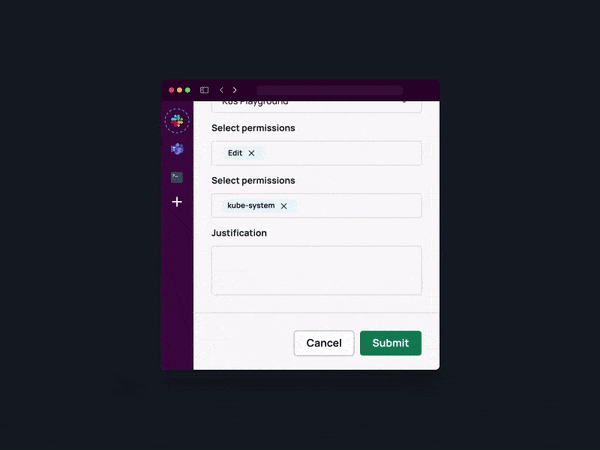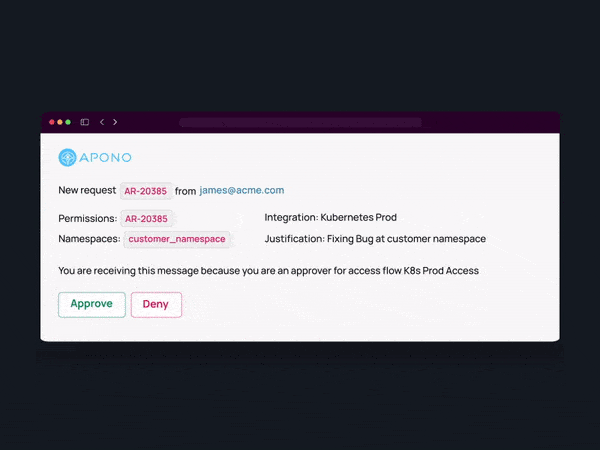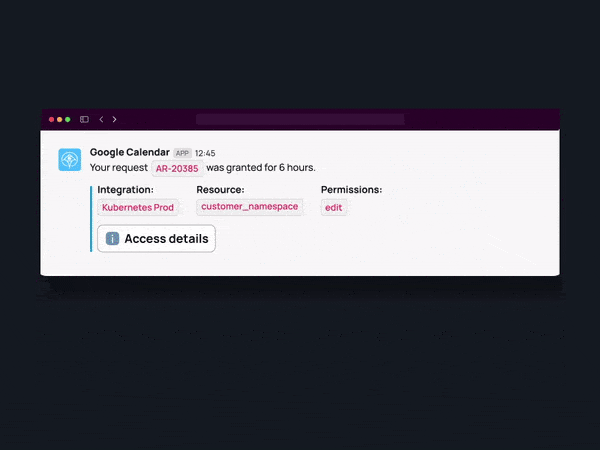
2. Implement Flexible No-Code Workflows
In access management, it is crucial to distinguish between privileged access and standard access. Privileged access pertains to elevated permissions granted to individuals necessitating administrative or special privileges for their duties, while standard access relates to regular user access for routine tasks. Automating least privilege access empowers organizations to differentiate between these access types and enforce more stringent controls on privileged accounts. By automating the provisioning and revocation of privileged access, companies can curtail the risk of misuse, insider threats, and unauthorized activities.
Flexible no-code workflows play a pivotal role in automating least-privilege access. These workflows enable organizations to define customizable approval sets based on various criteria, such as data sensitivity, identity provider (IdP) group membership, access duration, on-call schedules, completion of training, and open support tickets.
By tailoring approval workflows to align with the distinct needs of various teams, projects, and roles, organizations can strike a balance between security and operational efficiency. This approach guarantees that access is granted based on appropriate checks and balances while accommodating the specific requirements and urgency of different access requests.
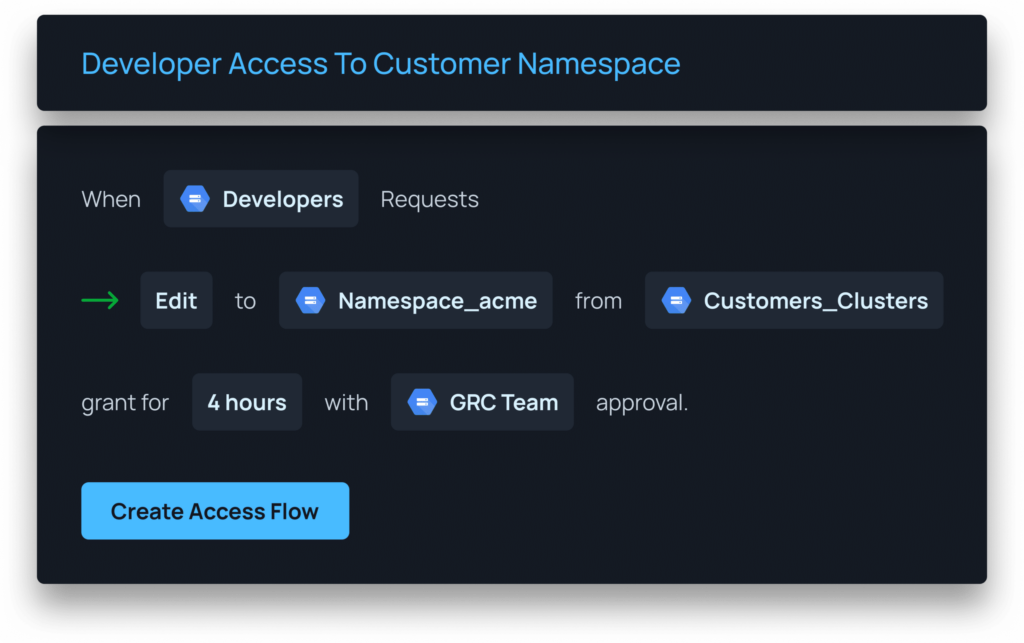
3. Enable Direct API Capabilities for Granular Provisioning
Fine-grained access control forms a cornerstone of least-privilege access, ensuring that employees only possess the permissions required to fulfill their specific responsibilities. Automating fine-grained access empowers organizations to define and enforce access permissions based on roles, responsibilities, and project prerequisites. This precision significantly reduces the potential impact of security incidents, as access is confined to the exact resources and actions required, minimizing the scope for lateral movement or unauthorized data exposure.
To achieve fine-grained permissions and efficient access provisioning, it is imperative to have direct API capabilities. APIs facilitate seamless integration with existing systems, applications, and identity providers, enabling real-time access provisioning and revocation.
Real-time provisioning of access enables JIT access, a crucial component of automated least-privilege access. Instead of granting continuous access to resources, JIT access authorizes permissions for a limited timeframe, precisely when needed. This approach minimizes the attack surface by narrowing the window of opportunity for potential threats. Through the implementation of JIT access, organizations can bolster security and guarantee that employees have access only when essential, mitigating the risk of unauthorized use or data exposure.
By harnessing APIs, organizations can automate the complete access management process, from request submission to approval, provisioning, and auditing. This high level of automation simplifies procedures for IT and security teams while ensuring accurate and timely access control.
About Apono
Apono is a leading provider of least-privilege access management solutions that enhance access control with dynamic mechanisms. With Apono’s platform, organizations can leverage Just-In-Time (JIT) access and Attribute-Based Access Control (ABAC) functionalities to achieve a more flexible and adaptable access management approach.
*** This is a Security Bloggers Network syndicated blog from Apono authored by Ofir Stein. Read the original post at: https://www.apono.io/blog/automating-least-privilege-access/
如有侵权请联系:admin#unsafe.sh
