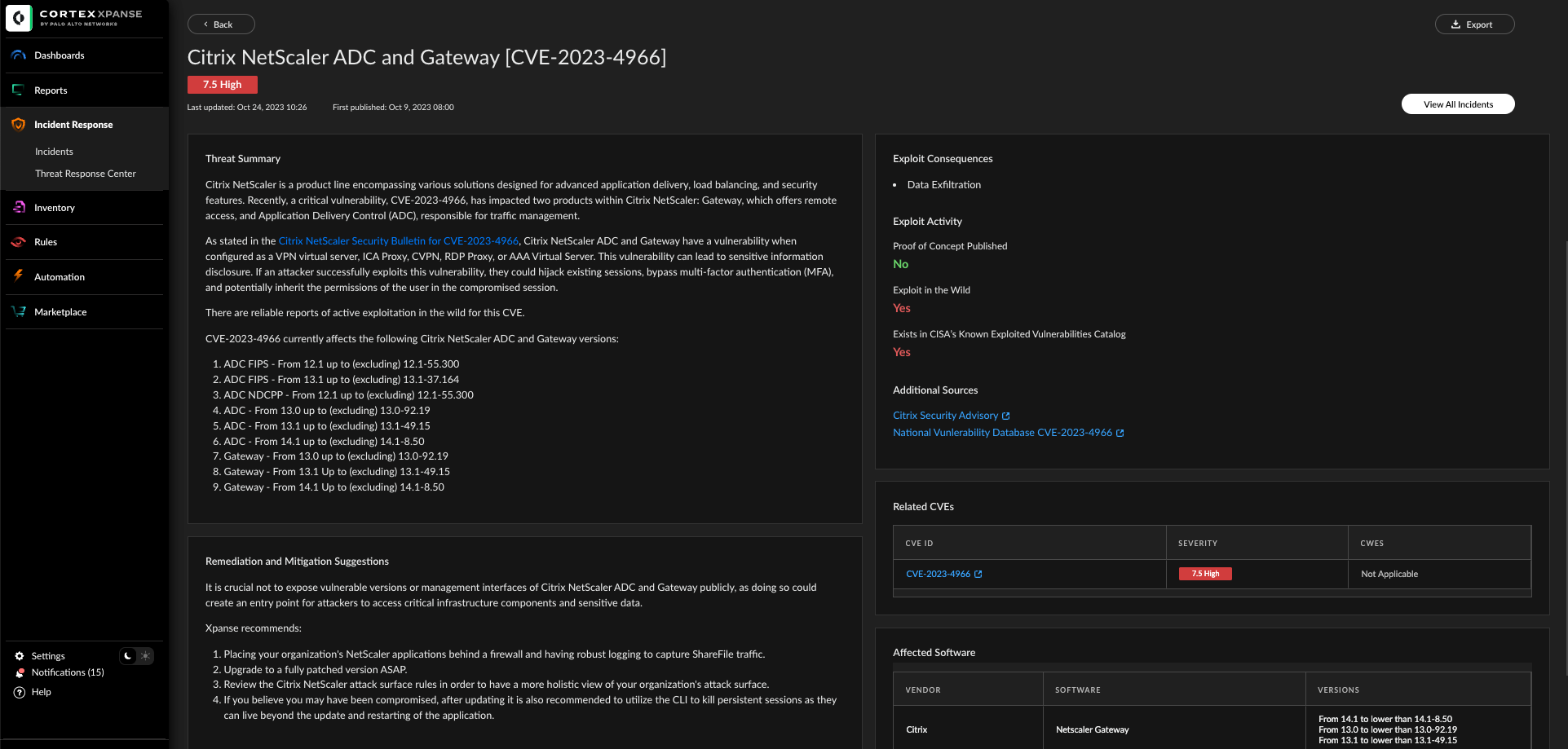
Executive SummaryOn Oct. 10, 2023-11-2 06:0:59 Author: unit42.paloaltonetworks.com(查看原文) 阅读量:53 收藏

Executive Summary
On Oct. 10, 2023, Citrix published a patch for their Netscaler ADC and Netscaler Gateway products. One particular vulnerability that this patch is meant to mitigate has come to be known as Citrix Bleed (CVE-2023-4966).
This nickname was given because the vulnerability can leak sensitive information from the device’s memory, which can include session tokens. Attackers can then use these credentials to gain a foothold into systems via session hijacking. At the time of the patch, Citrix was unaware of ongoing attacks using this vulnerability but has since stated that they have observed threat actors using it.
The Unit 42 Incident Response and Managed Threat Hunting teams have observed ransomware groups exploiting Citrix Bleed. The Managed Threat Hunting team has also observed what appeared to be remote executions from Netscaler gateways in association with exploitation of this vulnerability.
Using Cortex Xpanse device signature data, our researchers observed nearly 8,000 IP addresses advertising a vulnerable version of NetScaler Gateway and 6,000 IPs advertising NetScaler ADC devices. The largest number (3,100) of these devices are located in the United States, 800 are in Germany, 450 in China and 400 in the United Kingdom.
Palo Alto Networks customers receive protection from and mitigation for CVE-2023-4966 in the following ways:
- Organizations can engage the Unit 42 Incident Response team for specific assistance with this threat and others.
- The Unit 42 Managed Threat Hunting team can be engaged to continuously hunt for this and other threats hiding in your infrastructure.
- The Next-Generation Firewall with the Advanced Threat Prevention security subscription can help block the attacks with best practices.
- The Advanced WildFire machine-learning models and analysis techniques have been reviewed and updated in light of Citrix Bleed.
- Cortex Xpanse has published a new Threat Response Event for CVE-2023-4966 that can help identify generally exposed instances and those with known insecure versions.
- Cortex XDR and XSIAM help detect and protect against post-exploitation activities.
Palo Alto Networks also recommends patching against this vulnerability as well as CVE-2023-4967, with the software update provided by Citrix.
| Vulnerabilities Discussed | CVE-2023-4966 |
Table of Contents
Details of the Vulnerability
Current Scope of the Attack
Unit 42 Managed Threat Hunting Observations
Interim Guidance
Conclusion
Palo Alto Networks Product Protections for Citrix Bleed
Unit 42 Managed Threat Hunting Recommendations
Next-Generation Firewalls and Prisma Access With Advanced Threat Prevention
Advanced WildFire
Cortex Xpanse
Cortex XDR and XSIAM
Indicators of Compromise
Details of the Vulnerability
Citrix Bleed (CVE-2023-4966) is a sensitive information disclosure vulnerability affecting Citrix Netscaler Gateway and Netscaler ADC products with a CVSS score of 9.4. It was patched by Citrix on Oct. 10, 2023.
This vulnerability can allow an unauthenticated attacker to steal session tokens via a specially crafted request and gain access to vulnerable systems. There was also a publication from security firm Assetnote that provides specific details as well as proof of concept (PoC) code to exploit this vulnerability.
Citrix reports that the following products are affected by this vulnerability:
- NetScaler ADC and NetScaler Gateway 14.1 before 14.1-8.50
- NetScaler ADC and NetScaler Gateway 13.1 before 13.1-49.15
- NetScaler ADC and NetScaler Gateway 13.0 before 13.0-92.19
- NetScaler ADC 13.1-FIPS before 13.1-37.164
- NetScaler ADC 12.1-FIPS before 12.1-55.300
- NetScaler ADC 12.1-NDcPP before 12.1-55.300
CVE-2023-4966 has also recently been added to the CISA Known Exploited Vulnerabilities Catalog. This catalog contains vulnerabilities that are known to be frequent vectors of attack.
Current Scope of the Attack
At the time of patch publication for CVE-2023-4966, Citrix stated that the vulnerability had been found internally and that they were unaware of attacks targeting it. However, they have since stated that they have received reports of attacks using this vulnerability for session hijacking. As such, they have advised people to immediately apply the patch to affected devices.
There are also public reports of various attackers using this vulnerability to hijack session tokens and use them to gain access. It’s also been reported that Python scripts have been distributed to ransomware affiliates to exploit and gain access to victim networks. The combination of these sensitive access systems and publicly available PoC code makes the exposure of this vulnerability extremely sensitive.
The Unit 42 Incident Response and Managed Threat Hunting teams have observed ransomware groups exploiting Citrix Bleed. Additional MTH observations are described in the following section.
Unit 42 Managed Threat Hunting Observations
The Unit 42 Managed Threat Hunting team observed multiple compromised users executing reconnaissance commands and dropping additional tooling on VDI hosts. This activity appeared to be remote executions from Netscaler gateways that were potentially exploited by threat actors.
In this incident, we observed remote PowerShell sessions that spawned cmd.exe and executed various reconnaissance commands, such as the following:
- "C:\Windows\system32\whoami.exe" /all
- "C:\Windows\System32\Wbem\WMIC.exe" qfc get
- C:\Windows\system32\cmd.exe /c tasklist /FI "windowtitle eq Telnet
REDACTED_INTERNAL_IP"|findstr "cmd.exe" - cmd.exe /k "echo q|telnet REDACTED_INTERNAL_IP 80&exit"
- cmd /c "ping -n 1 -w 1 REDACTED_INTERNAL_IP && echo true || echo false"|
- taskkill /f /im cmd.exe
- net localgroup administradores
- net user administrador
In addition, the threat actor downloaded multiple tools into the VDI hosts, using Chrome or Microsoft Edge browsers. Among the tools, we observed the following:
- A binary called s.exe, which appeared to be XScan, a red teaming tool developed by Xteam that is capable of scanning vulnerabilities:
- s.exe -h REDACTED_INTERNAL_IP/24 -finger -vulnscan -webtimeout 6 -t 100 -debug
- An attempt to start a simple HTTP server listening on port 8000:
- python -m http.server 8000
- Installation of mRemoteNG, a utility designed for handling remote connections to other systems:
- "C:\Windows\System32\msiexec.exe" /i
- "C:\Users\Public\Libraries\mRemoteNG-Installer-1.76.20.24615.msi"
While this activity took place over the course of a week, the threat actor did not manage to move laterally outside of the VDI hosts.
Interim Guidance
Citrix has advised that there is no workaround for this vulnerability and strongly recommends patching the affected software immediately.
Unit 42 recommends prioritizing public-facing Netscaler Gateway and Netscaler ADC instances and applying patches to the affected products immediately.
Conclusion
Due to the ease of exploitation caused by the publicly availability of PoC code and the internet facing posture of these products, Palo Alto Networks recommends following Citrix’s guidance and immediately patching affected Citrix Netscaler products. Prioritize public-facing instances of these products or consider disabling if a patch cannot be immediately applied.
Palo Alto Networks and Unit 42 will continue to monitor the situation for updated information.
Palo Alto Networks customers receive protection from our products, as listed below. We will update this threat brief as more relevant information becomes available.
Palo Alto Networks Product Protections for Citrix Bleed
Palo Alto Networks customers can leverage a variety of product protections and updates to identify and defend against this threat.
If you think you might have been compromised or have an urgent matter, get in touch with the Unit 42 Incident Response team or call:
- North America Toll-Free: 866.486.4842 (866.4.UNIT42)
- EMEA: +31.20.299.3130
- APAC: +65.6983.8730
- Japan: +81.50.1790.0200
Unit 42 Managed Threat Hunting Recommendations
By installing Cortex XDR agents on Citrix guests, VDI instances and widely throughout the environment, Cortex XDR will be able to provide detection, prevention and telemetry for any activity or attempted lateral movement that occurs after exploitation. The Unit 42 MTH team can be engaged to continuously hunt for threats hiding in your infrastructure, allowing you to take action before damage occurs.
Next-Generation Firewalls and Prisma Access With Advanced Threat Prevention
Next-Generation Firewall with the Advanced Threat Prevention security subscription can help block the attacks with best practices via the following Threat Prevention signature: 94483
Advanced WildFire
The Advanced WildFire machine-learning models and analysis techniques have been reviewed and updated in light of Citrix Bleed.
Cortex Xpanse
Cortex Xpanse has published a new Threat Response Event for CVE-2023-4966 that includes Attack Surface Rules for detecting Citrix Netscaler Gateway and Citrix Netscaler ADC, as shown in Figure 1. This Threat Response Event can identify both generally exposed instances and those with known insecure versions.
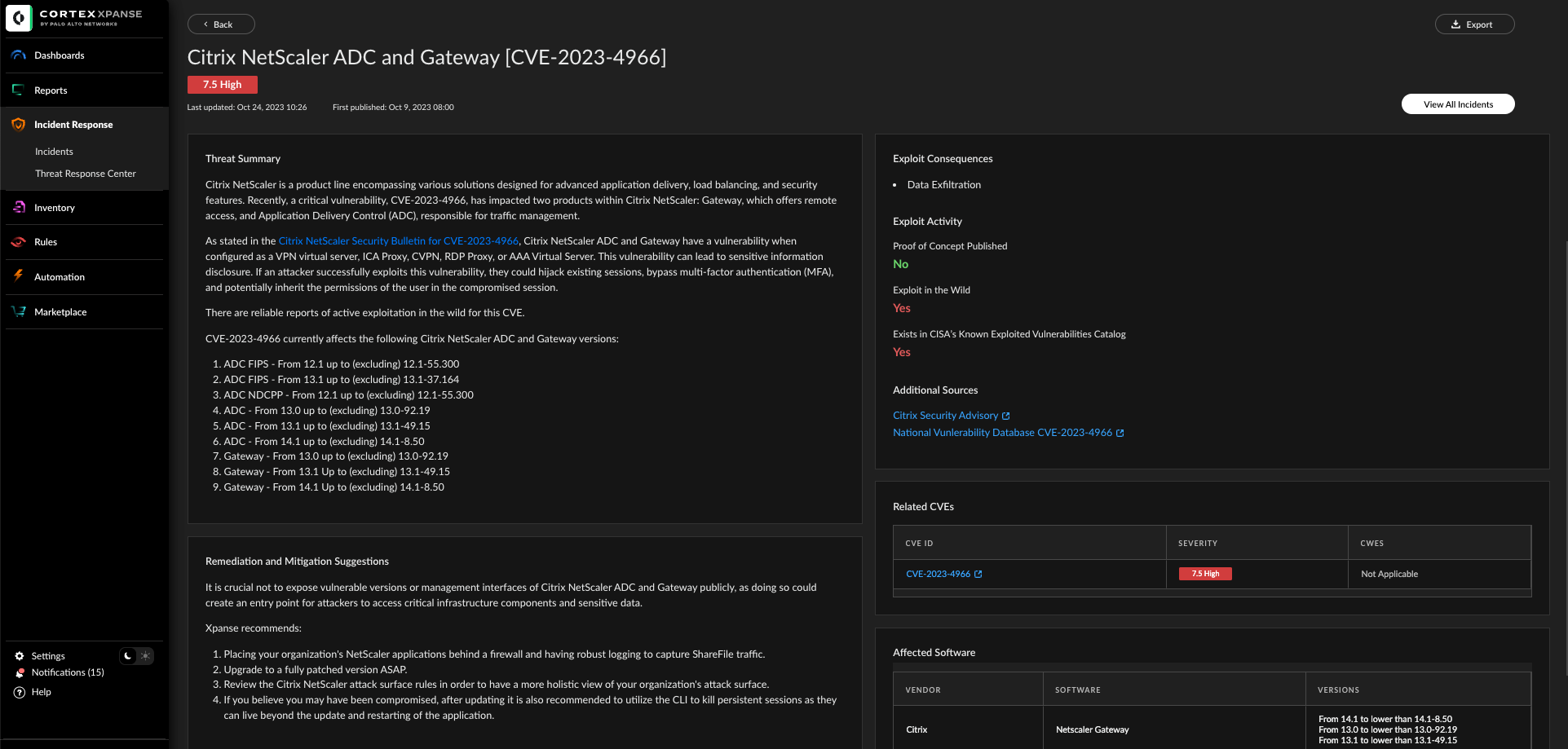
Cortex XDR and XSIAM
Cortex XDR and XSIAM agents help detect and protect against post-exploitation activities using the agent protection modules such as Behavioral Threat Protection, Anti-Webshell Protection, Credential Gathering Protection, analytics and more. XSIAM customers with the ASM module can also take advantage of the Cortex Xpanse detection capabilities outlined above.
Indicators of Compromise
- C:\Users\Public\Documents\s.exe - XScan
- C:\Users\Public\Documents\dsquery.exe - Tool designed to search for an active directory objects
- C:\Users\Public\Documents\dsget.exe - Tool designed to view active directory objects
- C:\Users\Public\Libraries\7z2301-x64.exe - 7zipinstall
- C:\Users\Public\Libraries\mRemoteNG-Installer-1.76.20.24615.msi
- C:\Users\Public\Libraries\python-3.12.0-amd64.exe - Python installed
Get updates from
Palo Alto
Networks!
Sign up to receive the latest news, cyber threat intelligence and research from us
如有侵权请联系:admin#unsafe.sh