2023-10-30 23:21:42 Author: securityaffairs.com(查看原文) 阅读量:14 收藏
Wiki-Slack attack allows redirecting business professionals to malicious websites

eSentire researchers devised a new attack technique, named Wiki-Slack attack, that can be used to redirect business professionals to malicious websites.
eSentire Threat Response Unit (TRU) security researchers discovered a new attack technique, named Wiki-Slack attack, that can be used to redirect business professionals to malicious websites.
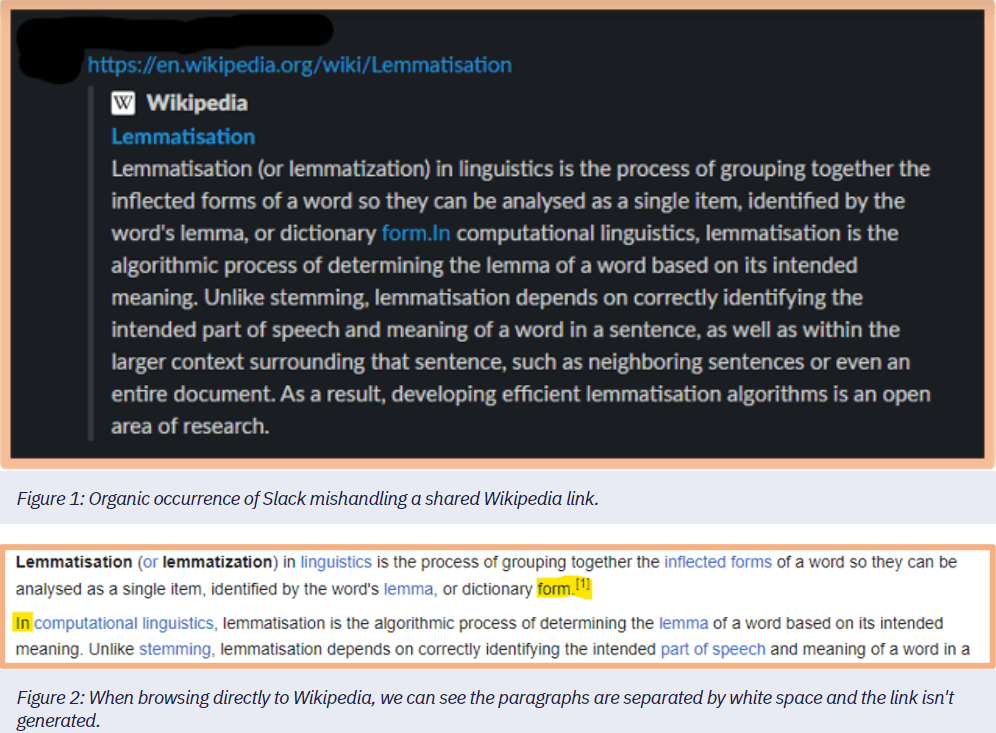
The attackers choose a subject in Wikipedia that can be of interest to the potential victims, then they will go to the first page of the Wikipedia entry and edit the page. The trick consists of adding a legitimate referenced footnote to the entry. The footnote allows to set the stage for a formatting error when the article is shared on Slack. Once certain additional conditions are met – made easy by small grammatical changes to the Wikipedia article, Slack will render a link that is not visible in the original Wikipedia article.
The researchers pointed out that the footnote itself is not malicious, but under certain additional conditions due to small grammatical changes to the Wikipedia article, Slack will render a link that is not visible in the original Wikipedia article.
“Once a business professional copies and pastes that Wikipedia entry in a Slack channel, the malicious link is rendered. If the grammar around the link is crafted well enough, Slack users are enticed to click it, leading them to an attacker-controlled website where browser-based malware lays in wait.” reads the post published by eSentire.
The three conditions that must be met are:
- The Wikipedia link must contain a reference at the end of the first paragraph.
- The first word of the second paragraph in the Wikipedia article must be a top-level domain (TLD) such as in, at, com, net, us, etc.
- The above two conditions must appear in the first 100 words of the Wikipedia article.
This leads Slack to mishandle the spacing between the first and second paragraph, resulting in the creation of a new link in Slack.

The researchers found more than 1,000 instances of this unintentional artifact.
eSentire furter elaborated that attackers could leverage Wikipedia statistics to choose pages that generate a high volume of traffic and use them to launch attacks with the Wiki-Slack technique.
The researchers explained that the Wiki-Slack attack is a numbers game, for this reason, leveraging ChatGPT or similar Large Language Model (LLM) an attacker can scale out the attack in a short time.
Organizations are recommended to be vigilant on browser-based attacks that can lead to malware infections. Employing endpoint monitoring, and building cyber resilience into their processes can allow organizations to limit the exposure to such kinds of attacks.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, Wiki-Slack Attack)
如有侵权请联系:admin#unsafe.sh