
2023-10-28 06:25:27 Author: securityboulevard.com(查看原文) 阅读量:10 收藏
The Security Operations Center (SOC) serves as a hub for an organization’s cybersecurity efforts. It is tasked with the responsibility of defending against unauthorized activities in the digital landscape. A SOC specializes in activities including monitoring, detection, analysis, response, and restoration.
On average, SOC teams receive 4,484 alerts daily and spend nearly three hours each day manually triaging these alerts. Furthermore, security analysts are unable to deal with 67% of the daily alerts received, a 2023 study reveals. Even the most well-resourced SOCs can’t keep up with the massive amounts of security alerts they receive without leveraging automation. Investigating threats manually can impact their overall threat response times, which has a whole load of adverse second-order effects. This explains why mature security teams use advanced SOC automation tools such as Smart SOAR to respond to cyber threats. It improves their agility, precision, and efficiency, transcending the limitations of manual operations.
In the following sections, we will delve into the transformative impact of SOC automation. We will explore seven real-world examples, break down playbooks, and outline workflows that can revolutionize how your SOC operates, benefiting not just your security team but the entire organization.
Security Operations Center (SOC) Defined
Gartner defines SOC (pronounced sock) as “as a team, often operating in shifts around the clock, and a facility dedicated to and organized to prevent, detect, assess and respond to cybersecurity threats and incidents, and to fulfill and assess regulatory compliance.” Other terms that might refer to a SOC, or elements within it, include:
- Computer Security Incident Response Team (CSIRT)
- Computer Incident Response Team (CIRT)
- Computer Incident Response Center (CIRC)
- Computer Security Incident Response Center (or Capability) (CSIRC)
- Cybersecurity Operations Center (CSOC)
- Computer Emergency Response Team (CERT)
- Digital Forensics and Incident Response (DFIR)
- Incident Response Team (IRT)
- Information Security Operations Center (ISOC)
- Security Response Center (SRC)
There are plenty of alternatives to building and staffing an in-house SOC. SOC models include virtual, hybrid, distributed, co-managed, command, multifunction, follow-the-sun, and fusion. We’ll break these down along with a SOC’s roles and responsibilities in a future post.
7 Advanced SOC Automation Use Cases
SOAR simplifies and speeds up the handling of repetitive and manual cybersecurity tasks, enabling SOC teams to quickly and accurately respond to threats. There are many security and non-security automation use cases possible within the Smart SOAR platform. Let’s walk you through some examples here.
Alert Triage
Manual alert triage costs organizations $3.3 billion annually in the U.S. alone, a recent study reveals. D3’s Event Pipeline, a global playbook that ships with Smart SOAR, essentially performs the tasks of a Tier 1 analyst, but at a much greater scale. With no human intervention, it can process hundreds of alerts each minute, to normalize, de-duplicate, consolidate, triage, enrich, and decide whether to dismiss or escalate them. The outcomes unlocked for D3’s customers are phenomenal. In a recent workshop, an executive from Master MSSP High Wire Networks said that they went from handling around 144,000 alerts to focusing on just about 200 alerts each month that needed analysts’ attention.
Automated Incident Reports
Smart SOAR can automatically generate an incident report from an incident with a high-level summary, investigation timeline, and data on malicious artifacts, among other details, which can be automatically or manually exported. This helps SOC teams save time, maintains consistency, and ensures stakeholders receive thorough, professional reports.
Phishing Detection and Response
Phishing is a significant pain point for enterprises, exploiting human error to gain sensitive information. Look at these three SOAR-driven incident response playbooks that automate dozens of tasks per alert related to enrichment, containment, recovery, and reporting by leveraging Smart SOAR’s integrations with major EDR, firewall, and IAM (Identity and Access Management) vendors.
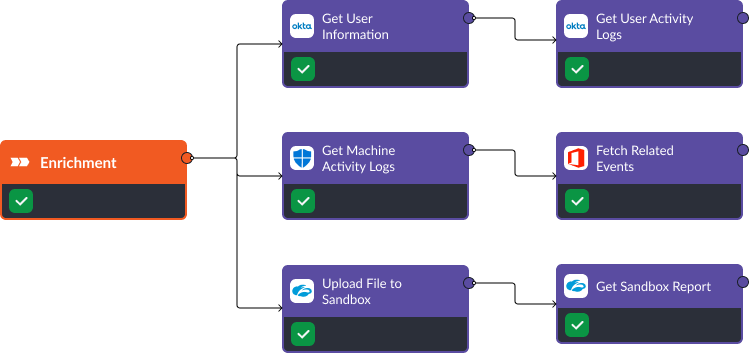
Asset Vulnerability Analysis & Remediation
This Smart SOAR workflow leverages our integration with Rapid7’s InsightVM to facilitate targeted asset vulnerability analysis by automating the process post-alert. A vulnerability scan is then initiated on this site, and upon completion, asset vulnerabilities are collated for review during the investigation. Smart SOAR can also ingest alerts from threat intelligence platforms for Common Vulnerabilities and Exposures (CVEs) and trigger an automated vulnerability remediation playbook that can patch affected systems.
Respond to Credential-Based Attacks
By combining IAM solutions with SOAR, you can counter credential-based attacks by automatically performing response actions such as disabling accounts, blocking IP addresses, resetting passwords, revoking access to sensitive resources, and updating security zones. Check out our integrations with Okta and Active Directory for more information.
Automated Threat Hunting
Threat hunting is now considered a foundational skill for the SOC. Smart SOAR automates threat hunting through scheduled automated workflows that search for Indicators of Compromise (IOCs) across the environment and continuously monitor threats with its ongoing surveillance capability. These functionalities expedite the identification and management of threats, making the process efficient and effective.
MSSP Use Case: Automated Client Onboarding
Managed Security Service Providers (MSSPs), typically onboard new clients manually, a process which could take weeks. Smart SOAR integrates with ITSM vendors like Zendesk to streamline this process down to a few minutes, by syncing customer information, creating a new tenant site, and pushing configurations such as playbooks and automation rules.
Smart SOAR: Unleash Your SOC Automation Strategy
As makers of the world’s leading independent Security Orchestration, Automation, and Response (SOAR) platform, we have a highly opinionated and data-backed perspective on its pivotal role in automating SOC processes. Smart SOAR has helped SOC teams increase response speeds by 10x or more, and reduce average remediation costs by 90%.
Beyond automation, SOAR enhances cross-departmental collaboration and simplifies compliance reporting, reinforcing the organization’s overall security posture. Its built-in flexibility allows for easy adaptation to emerging threats and technologies, making SOAR not just an add-on, but a foundational element that keeps your SOC agile and ahead of evolving cybersecurity challenges. Schedule a demo with us to discuss your SecOps challenges and uncover the robust solutions tailored to meet your unique security demands.
The post SOC Automation Explained: 7 Real-World Examples appeared first on D3 Security.
*** This is a Security Bloggers Network syndicated blog from D3 Security authored by Shriram Sharma. Read the original post at: https://d3security.com/blog/soc-automation-examples/
如有侵权请联系:admin#unsafe.sh
