2023-10-26 00:10:19 Author: blogs.sap.com(查看原文) 阅读量:16 收藏
Transitioning from basic authentication to Mutual Transport Layer Security (mTLS) for authenticating against SuccessFactors APIs is a critical step forward in enhancing the security and reliability of data connections.
In addition to undergoing a deprecation process, basic authentication relies on a simple username and password. At the same time, mTLS offers a significantly higher level of security, making it a preferred choice for organizations that prioritize data protection.
This shift is essential for several compelling reasons:
First and foremost, mTLS authentication provides a robust defense against various security threats, including unauthorized access, data breaches, and identity theft. Furthermore, mTLS employs a certificate-based approach, making it virtually impossible for attackers to compromise sensitive data during authentication.
In addition to the security benefits, mTLS authentication enhances the overall reliability of your connections to SuccessFactors. Eliminating the need for recurring password changes and the associated maintenance reduces the likelihood of authentication-related downtime, ensuring a more consistent and seamless experience for both your applications and end users.
Below is a step-by-step explanation of the process for using mTLS in SuccessFactors extensions developed on SAP Business Technology Platform (BTP).
Having OpenSSL installed locally.
Generating a certificate is essential to establish mTLS connectivity between SAP BTP and the SAP SuccessFactors APIs.
When using the SAP BTP AppRouter, only destination client certificates of type p12 are supported.
As a result, it is necessary to generate a .pem certificate, within the SAP BTP Destination service, and then convert the same into p12 format.
The procedure is explained below.
#1 – Generation of PEM certificate in the SAP BTP cockpit
- Under Connectivity -> Destinations, click on Certificates.

2. Click on Generate Certificate

3. Fill in the certificate details

The Certificate Common Name must be set to the API user that has the API consumption authorization in SuccessFactors.
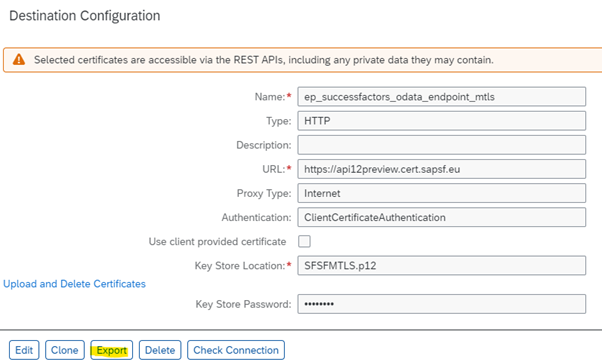
#2 – Create a new destination

The URL must contain the .cert API endpoint. The list of SuccessFactors API endpoints can be found here.
The authentication mechanism should be ClientCertificateAuthentication.
Key Store Location must point to the certificate generated in step #1.
Under Additional Properties, the following header should be added:
URL.headers.successfactors-companyid = <sfsf_company_id>
#3 – Export PEM certificate and save it locally
#4 – Split the Public and Private Keys
- Unzip the exported file
- On a text editor (e.g.: Notepad++), open the .pem file
- Remove the private key from the .pem file and save it in a different file, with .pem format
- Remove any empty lines at the end of the .pem file
- At this point in time, you should have two .pem files – one containing the public certificate chain and another containing the private key.
#5 – Generate the p12 certificate using OpenSSL
Run the following OpenSSL command
openssl pkcs12 -export -out <nameofp12file>.p12 -in <publiccerticate>.pem -inkey <privatekey>.pem
where <publiccertificate>.pem is the .pem file extracted from the BTP, without the private key and <privatekey>.pem is the file obtained in the previous step.
#6 – Upload p12 certificate to the BTP subaccount
Go back to the BTP subaccount and click on Certificates

Upload the p12 certificate generated in the previous step.

#7 – Update the destination to use the P12 certificate

#8 – Upload the certificate in SAP SuccessFactors Security Center
Finally, go to SAP SuccessFactors -> Security Center -> X.509 Public Certificate Mapping

And upload the certificate public key (<publiccertificate>.pem obtained in step #4).

The integration Name must be Business Technology Platform and the Login Name must the the API user in SuccessFactors.
Overall, making the move from basic authentication to mTLS for SuccessFactors APIs not only fortifies your data protection measures but also supports regulatory compliance, improves reliability, and future-proofs your authentication strategy. It’s a vital step toward safeguarding your critical HR and workforce data in an increasingly interconnected and data-driven world.
Using Mutual Transport Layer Security (mTLS) | SAP Help Portal
mTLS integration with SAP SuccessFactors and SAP BTP | SAP Blogs
SAP BTP destination using Client Certificate authentication to SAP SuccessFactors | SAP Community
https://www.npmjs.com/package/@sap/approuter#destination-service
https://userapps.support.sap.com/sap/support/knowledge/en/2215682
如有侵权请联系:admin#unsafe.sh
