IntroductionAs a cybersecurity company, Kaspersky is constantly dealing with known an 2023-10-24 18:0:1 Author: securelist.com(查看原文) 阅读量:24 收藏
Introduction
As a cybersecurity company, Kaspersky is constantly dealing with known and brand-new malware samples. As part of our crimeware reporting service, we provide our customers with technical reports on the evolution of existing crimeware families, as well as newly emerging ones. In this article, we share excerpts from our reports on malware that has been active for less than a year: the GoPIX stealer targeting the PIX payment system, which is gaining popularity in Brazil; the Lumar multipurpose stealer advertised on the dark web; and the Rhysida ransomware supporting old Windows versions.
To learn more about our crimeware reporting service, please contact us at [email protected].
GoPIX
In Brazil the PIX payment system is becoming more and more popular. Unsurprisingly, cybercriminals are jumping on the bandwagon, trying to abuse the system for their profit. A good example of this is GoPIX, a malware campaign that has been active since December 2022.
The attack cycle begins when a potential victim searches for “WhatsApp web”. The cybercriminals employ malvertising: their links are placed in the ad section of the search results, so the user sees them first. If they click such a link, a redirection follows, with the user ending up on the malware landing page. Then something interesting takes place: the criminals use a fraud prevention solution, IP Quality Score, to determine whether the visitor is a real user or a bot. If all is good (from the attacker point of view), a fake WhatsApp download page is shown and the user is tricked into downloading the malware.
Again, something interesting happens, as there are two URLs the malware can be downloaded from. Which URL is used depends on whether port 27275 is open on the user machine. This port is used by the Avast safe banking software. If this software is detected, a ZIP file is downloaded that contains an LNK file embedding an obfuscated PowerShell script that downloads the next stage. If the port is closed, this is skipped and the next stage (an NSIS installer package) is downloaded. The sole purpose of this seems to be to bypass the Avast software and make sure the malware is downloaded onto the system.
The NSIS installer package contains some PowerShell scripts, downloads additional ones and also downloads the malware (GoPIX). After decrypting the payloads and executing different shellcodes, the malware dropper is finally loaded using the sRDI (Shellcode Reflective DLL Injection) project that can be found on GitHub. The malware dropper then starts the “svchost” process in a suspended state and injects GoPIX into it.
GoPIX is a typical clipboard stealer malware that steals PIX “transactions” used to identify payment requests and replaces them with a malicious (attacker controlled) one which is retrieved from the C2. The malware also supports substituting Bitcoin and Ethereum wallet addresses. However, these are hardcoded in the malware and not retrieved from the C2. GoPIX can also receive C2 commands, but these are only related to removing the malware from the machine.
As one would expect, most of the infections that we see are from Brazil.
Lumar
Lumar (not to be confused with Lumma, which we reported on previously) is a brand-new stealer that is rapidly gaining popularity in underground communities. It was advertised in July 2023 by a user called “Collector,” who advertised the new stealer as having the following capabilities:
- Capturing Telegram sessions;
- Harvesting passwords, cookies, autofills, etc;
- Retrieving files from the user’s desktop;
- Extracting data from various cryptographic wallets;
The full list of capabilities we provided in our private report on Lumar.
Despite having all these functionalities, the malware is relatively small in terms of size (only 50KB), which is partly due to the fact that it is written in C.
When executed, the malware resolves functions using CRC32. It then checks the OS UI language and terminates if it is set to a language used in a CIS country. After this, the initial information-gathering process starts where information on the CPU, memory, keyboard layout, etc. is sent to the C2. Next, Lumar starts three different threads, each one looking for specific data:
- .txt, .doc, .jpg, .rdp, .xls, etc files;
- browser cookies and cached passwords;
- files associated with cryptocurrency wallets.
The data is then gathered, zipped and sent to the C2.
The C2 is hosted by the malware author as they are selling the whole package as a MaaS. In order to log in, a username and password are required. Once logged in, there are three tabs:
- Home;
- Stats (victim statistics);
- Logs (exfiltrated information, which can be downloaded as a ZIP file).
Furthermore, the C2 panel supports downloading the latest version of Lumar and Telegram setup (the buyer will be notified of any new incoming data via Telegram).
Rhysida
Rhysida is a relatively new ransomware variant that appeared in May this year according to our telemetry. It has all the typical characteristics of many modern ransomware families: it’s distributed as Ransomware as a Service (RaaS), runs a hidden TOR service, uses LibTomCrypt, etc.
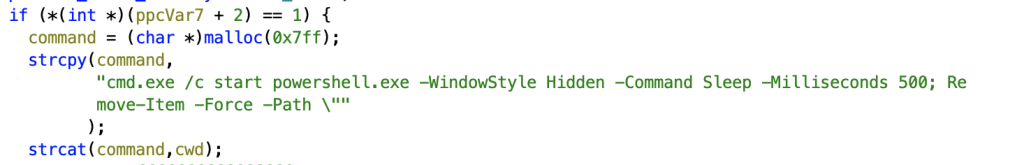
However, there are a few peculiarities about Rhysida that are worth noting. First of all, self-deletion is achieved by executing a PowerShell command on the system.
Secondly, it still supports Windows versions prior to Windows 10, as the Documents and Settings folder is excluded from the encryption process. Thirdly, the malware is written in C++ and compiled using MinGW with shared libraries by default. This means that these libraries must be present on the system at the time of execution.
As mentioned above, Rhysida is relatively new, which is evident from the number of victims on its onion site, but also from the fact that the onion server configuration initially contained bugs, exposing sensitive data. The group behind Rhysida fixed these bugs fairly quickly.
Conclusion
Cybercriminals adapt to the trends, and develop new malware every now and then. As new apps and services, such as the PIX payment system, grow popular, crimeware authors add it to their list of targets, so families like GoPIX stealer are born. The emerging malware is often advertised on the dark web among less skilled criminals, and distributed as MaaS, allowing its authors to grow rich quickly and endangering legitimate organizations again and again. To keep ahead of the evolving threats, businesses need to constantly monitor the threat landscape.
If you’d like to stay up to date on the latest TTPs being used by criminals, or have questions about our private reports, please contact us at [email protected].
Indicators of compromise (MD5s)
GoPix
EB0B4E35A2BA442821E28D617DD2DAA2
6BA5539762A71E542ECAC7CF59BDDF79
333A34BD2A7C6AAF298888F3EF02C186
Lumar
5fc82bd3590eae30c26f1a42f4e711f4
46b892398cfb1a1c59683fc8abfcc5fc
Rhysida
0c8e88877383ccd23a755f429006b437
274be1fac3bab38af7483a476a2dea90
36d142294f1ca4c4768dbe15b6553975
如有侵权请联系:admin#unsafe.sh
