
2023-10-19 22:4:23 Author: securityboulevard.com(查看原文) 阅读量:8 收藏

Russian Hacking Forum Trends
Initial access brokers (IAB) are sophisticated, focused, and specialized threat actors that focus on finding and gaining access to corporate environments. Once they compromise these environments, they auction off or sell the access on dark web forums.
To date in 2023, more than 100 companies across 18 industries had access to their IT infrastructure, cloud environments, networks, or applications sold on Russian hacking forums.
For this analysis Flare reviewed 3 months of IAB posts on the Russian hacking forum Exploit to identify trends around:
- Average “blitz” (buy it now price)
- Countries most represented in IAB posts
- Targeted industries
- Frequency of IT infrastructure access in industries classified as critical infrastructure
- Access types commanding highest prices
- Access types commonly obtained and sold
- Number and activity of threat actors in the Exploit ecosystem
Read our full report, Initial Access Brokers, Russian Hacking Forums, and the Underground Corporate Access Economy and/or keep reading for the highlights.
What are Initial Access Brokers (IABs)?
While most cybercrime activity focuses on consumer fraud, a small group of more sophisticated actors target corporate environments or enable others who target those environments. IABs actively operating on Russian hacking forums XSS and Exploit, reselling initial access to IT environments to ransomware gangs, affiliates, nation states, and other IABs.
Other categories of threat actors who target corporate environments and may purchase from IABs include:
- Stealer log vendors: distributed across Russian Market, Genesis Market, and public/private Telegram channels, likely a source for initial access that IABs use and expand upon
- Hacktivist groups: operating across Tor and Telegram, typically targeting NATO countries’ critical infrastructure and government agencies
- Ransomware gangs: distributing or providing to affiliates specific ransomware variants, likely linked to IABs
- Initial access brokers: actively operating on Russian hacking forums XSS and Exploit, reselling initial access to IT environments to ransomware gangs, affiliates, nation states, and other IABs
What’s in an IAB Post?
While IAB posts often mix English and Russian, they use specific terminology that can include and or all of the following information:
- Type/Тип доступа: Describes the type of access obtained, most commonly RDP or VPN access
- Industry/Деятельность Риелторы: Describes the industry of the victim company; Finance, Retail, and Manufacturing are the three most common targets
- Access Level/Права: Describes the level of privileges obtained
- Revenue: Describes the revenue of the victim company, often obtained from U.S. based data providers publicly available online
- Host Online: Often describes the number of hosts from the victim and sometimes includes antivirus and security systems in place
- Start: The starting price of the auction
- Step: The bid increments
- Blitz: The buy it now price
Post advertising RDP access for a U.S.-based organization
Price of Infrastructure Access: The Blitz
Threat actors do not consider all access equally valuable, as evidenced by auction pricing variances.
While roughly 33% of all auctions have a blitz price below $1,000, the distribution across the data provides insight into the impact that outliers have:
- $4,699.31: Average purchase price across all samples
- $1,328.23: Average purchase price after removing outliers
- $150-$120,000: Range of purchase prices across all listing
Higher-priced listings typically offered access to unique environments or particularly sensitive files.
Threat Actors and Geography
Although most IAB posts focused on US companies, these threat groups also targeted several other countries:
- US: 36.11%
- Australia: 6.94%
- UK: 5.56%
- France: 5.56%
Generally, US access sales align with global averages. Despite threat actors focusing on US companies, these listings did not fetch a higher price than their global counterparts.
Threat Actor and Industry Statistics
To gain insight into the proliferation of IABs, we reviewed how many threat actors were actively selling access to corporate networks on Exploit during this period. We identified 31 unique usernames selling access to corporate IT environments; however, the top seven actors were responsible for the majority (55.6%) of listings.
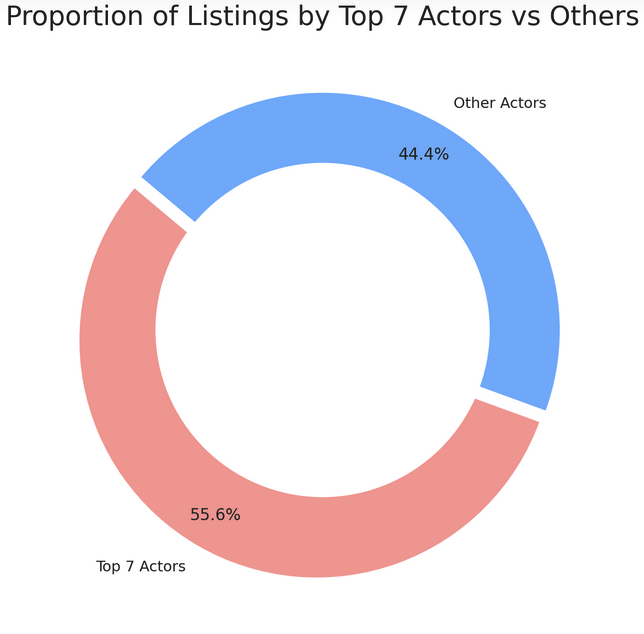
These findings suggest that gaining access to IT environments requires specially developed tactics, techniques, and procedures.
Initial Access Brokers and Industry
Industry greatly impacts the pricing in our sample data, with some industries selling for a much higher average prices than others.
After classifying organizations into 18 industries, we reviewed reviews the average blitz prices across them noting the following approximate values:
- Manufacturing: $2250
- Finance: $1800
- Media: $1700
- Construction: $1500
- Business services: $1100
- Retail: $750
U.S. Critical Infrastructure, IABs, and Types of Access
Access to the U.S. Critical Infrastructure is routinely sold on Exploit but not overrepresented compared to other industries. However, Construction and Business Services industries were the most affected.
Threat actors typically list the attack vector in their posts rather than the access type. The two most common attack vectors, making up 60% of the overall listings, were:
- Remote Desktop Protocol (RDP)
- Virtual Private Network (VPN)
When reviewing the limited data, the access types most commonly listed were:
- Administrator access to cloud environments (14 instances)
- Local administrator privileges (5 instances)
- “User in domain” (2 instances)
Additionally, listings around non-standard access typically included references to:
- Company specific Software-as-a-Service (SaaS) applications
- Specific data categories
- IT application
Risk Mitigations
In addition to typical security controls like multi-factor authentication (MFA) and user training, organizations should consider:
- Monitoring IAB forums like Exploit and XSS to identify compromised access to environments
- Monitoring for stealer logs across public and private Telegram channels, Russian Market, and Genesis Market
- Automating public GitHub secrets detection for data loss arising from developers copying/pasting code that contains credentials
IAB Research Considerations
When planning and executing the research, we made some important decisions that impacted the outcomes:
- We only reviewed data from May 1st to July 27th, 2023, providing us a sample size of 72 IAB events. While this sample size was sufficient to provide interesting data, it limits some statistical analysis.
- Posts varied in information based on the threat actor. Key data such as industry, level of access, type of access and other key elements were missing from a small number of listings in our sample. In these cases, data was listed as “unknown” for the analysis.
- We only reviewed IABs active on one dark web forum out of several forums where access brokers are active. Data discussed in this paper only focuses on the dark web forum Exploit.
How Flare Can Help
Flare’s proactive cyber threat exposure management solution constantly scans the online world, including the clear & dark web. With 4,000 cybercrime communities monitored, our platform provides data from 14 million stealer logs and 2 million threat actor profiles.
Since our platform automatically collects, analyzes, structures, and contextualizes dark web data, you gain the high-value intelligence specific to your organization for 10x faster dark web investigations.
Sign up for our free trial to test Flare yourself.
The post Threat Spotlight: Initial Access Brokers on Russian Hacking Forums appeared first on Flare | Cyber Threat Intel | Digital Risk Protection.
*** This is a Security Bloggers Network syndicated blog from Flare | Cyber Threat Intel | Digital Risk Protection authored by Flare. Read the original post at: https://flare.io/learn/resources/blog/threat-spotlight-initial-access-brokers-on-russian-hacking-forums/
如有侵权请联系:admin#unsafe.sh
