read file error: read notes: is a directory 2023-10-19 08:30:30 Author: unit42.paloaltonetworks.com(查看原文) 阅读量:35 收藏
This post is also available in: 日本語 (Japanese)
Executive Summary
On Oct. 16, 2023, Cisco published a security advisory detailing an actively exploited privilege escalation zero-day vulnerability impacting Cisco IOS XE devices. The vulnerability (CVE-2023-20198) has a criticality score of 10, according to the National Vulnerability Database, and it would allow an attacker to create an account with the highest privileges possible.
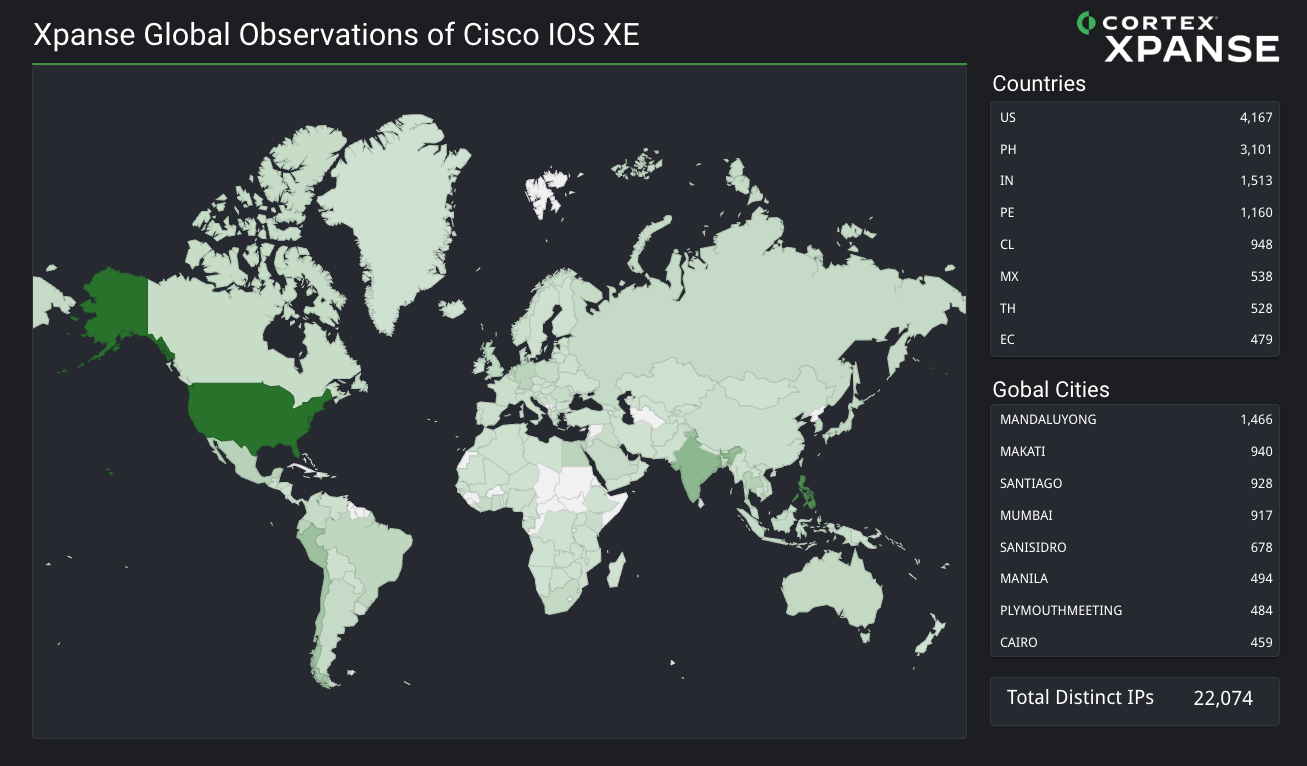
According to our attack surface telemetry, analysts have observed 22,074 implanted IOS XE devices since at least 18 October 2023.
Cisco recommends customers disable the HTTP Server feature on all internet-facing systems or untrusted networks.
Palo Alto Networks customers receive protections from and mitigations for the Cisco IOS XE Web UI Privilege Escalation Vulnerability in the following ways:
- Next-Generation Firewall with Advanced Threat Prevention security subscription should use best practices via the following Threat Prevention signatures:
- Organizations can engage the Unit 42 Incident Response team for specific assistance with this threat and others.
Palo Alto Networks also recommends following Cisco’s guidelines for all IOS XE devices.
| Vulnerabilities Discussed | CVE-2023-20198 |
Table of Contents
Details of the Vulnerability
Current Scope of the Attack
Interim Guidance
Conclusion
Palo Alto Networks Product Protections for Cisco IOS XE Privilege Escalation Vulnerability
Next Generation Firewall With Advanced Threat Prevention
Prisma Cloud
Details of the Vulnerability
Cisco disclosed a privilege escalation zero-day vulnerability on Oct. 16, 2023. This vulnerability impacts the Cisco IOS XE web user interface. If this feature is enabled, an attacker can create a new account with the highest privileges (level 15, full administrative access).
A non-persistent implant based on the Lua programming language has been observed in use alongside this vulnerability. The web server must be restarted for the implant to become active, according to Cisco Threat Intelligence.
Current Scope of the Attack

According to attack surface telemetry from Cortex Xpanse, analysts have observed at least 22,074 hosts containing the Lua-language implant. Figure 1 below shows a global heatmap displaying the potential global impact based on the unique IPs.
Interim Guidance
Cisco recommends customers disable the HTTP Server feature on all internet-facing systems or untrusted networks as the primary workaround solution for this vulnerability. Cisco’s Threat Intelligence team has provided checks and recommendations for this vulnerability.
Conclusion
Based on the amount of publicly available information, along with our own analysis, Palo Alto Networks recommends following Cisco’s recommendations immediately. For all potentially impacted organizations, we also recommend reviewing your systems for signs of a backdoor implant installation and new user account creation.
Palo Alto Networks and Unit 42 will continue to monitor the situation for updated information, release of proof of concept code and evidence of additional exploitation.
Palo Alto Networks has shared our findings, including file samples and indicators of compromise, with our fellow Cyber Threat Alliance (CTA) members. CTA members use this intelligence to rapidly deploy protections to their customers and to systematically disrupt malicious cyber actors. Learn more about the Cyber Threat Alliance.
Palo Alto Networks customers receive protection from our products, as listed below. We will update this threat brief as more relevant information becomes available.
Palo Alto Networks Product Protections for Cisco IOS XE Privilege Escalation Vulnerability
Palo Alto Networks customers can leverage a variety of product protections and updates to identify and defend against this threat.
If you think you might have been compromised or have an urgent matter, get in touch with the Unit 42 Incident Response team or call:
- North America Toll-Free: 866.486.4842 (866.4.UNIT42)
- EMEA: +31.20.299.3130
- APAC: +65.6983.8730
- Japan: +81.50.1790.0200
Next Generation Firewall With Advanced Threat Prevention
Next-Generation Firewall with the Advanced Threat Prevention security subscription can help block the associated attack and implant’s C2 traffic with best practices via the following Threat Prevention signatures: 86807, 94454
Prisma Cloud
The Cisco IOS XE software is not designed to be deployed on a cloud resource. Prisma Cloud is a SaaS security solution and has no capability to detect this vulnerability on a physical (bare-metal) appliance.
Prisma Cloud will continually update its detection methodology to include cloud-hosted software, applications and operating systems. Should Cisco IOS XE be made available as a cloud OS image, Prisma Cloud will incorporate this CVE into its detection framework.
Get updates from
Palo Alto
Networks!
Sign up to receive the latest news, cyber threat intelligence and research from us
如有侵权请联系:admin#unsafe.sh