2023-10-18 21:0:54 Author: securityboulevard.com(查看原文) 阅读量:9 收藏

Discover the history, types, and threats of QR codes, including quishing and QRLJacking. Learn why QR phishing is effective and how it exploits user trust, convenience, and bypasses security filters.
Understanding QR Codes: A Brief History
QR codes, or quick response codes, have become ubiquitous in recent years. These two-dimensional barcodes were invented by a Japanese automobile manufacturing company in 1994 and were initially used to track vehicle parts during the manufacturing process. However, it wasn’t until the smartphone era that QR codes gained widespread popularity.
QR codes offer several advantages over traditional barcodes, including the ability to store a large volume of data, the ability to be scanned even if partially damaged, and the convenience and speed of data transmission. As a result, QR codes have found their way into various aspects of our lives, from advertising and marketing campaigns to contactless payments and accessing websites with ease. It’s now more common to see restaurant menus on a QR code rather than traditional printed menus.
Types of QR Codes: Static vs. Dynamic
There are two main types of QR codes: static and dynamic. Static QR codes contain information that does not change, such as a website URL or contact information. On the other hand, dynamic QR codes allow for the updating or changing of the data they store. These codes redirect users to a unique URL that points to a server where the information is stored, making them ideal for situations where content needs to be frequently updated, such as event details or promotional offers.
Quishing: QR Code Threats
Quishing, a blend of QR code and phishing techniques, manipulates QR codes for cyberattacks. It has emerged as a growing threat with the widespread adoption of QR codes during the pandemic.
A typical quishing attack involves the following steps:
- The attacker generates a QR code embedded with either a phishing link or malware download.
- The malicious QR code gets distributed through various channels like phishing emails, ads, social media, restaurant menus, posters, etc.
- A victim scans the fake code, believing it came from a legitimate source.
- The scan either sends the user to a phishing site to steal login credentials, financial data, or other sensitive information. Or it downloads malware onto the device to compromise it.
- Through phishing or malware installation, the attacker gains access to the victim’s data or infected device.
Quishing exploits the convenience of QR codes for large-scale attacks. In August 2023, researchers uncovered a phishing campaign that used malicious QR codes to target a large number of companies, including a major U.S. energy firm.

Photo: A screenshot of a phishing email containing a malicious QR code
QRLJacking: Session Attacks
QRLJacking, or quick response code login jacking, is a social engineering method that exploits the “login with QR code” feature used by many apps and websites. It can lead to full account hijacking. A typical QRLJacking attack unfolds as follows:
- The attacker creates a phishing site mimicking the login page of the target app or site, including a fake QR code they control.
- The attacker sends the phishing link to victims via email, SMS, messaging apps, etc.
- The victim opens the link on their mobile device and scans the fake QR code, believing it is legitimate.
- Scanning logs the victim into the attacker’s phony session instead of the real app.
- The app associates the victim’s account with the attacker’s session and sends sensitive data like access tokens.
- The attacker gains full control of the victim’s account.
QRLJacking takes advantage of frequently expiring QR login codes. The attacker extracts real-time codes using tools like Evil QR browser extension to maintain an active phishing session.
In an August 2023 blog post, cybersecurity researcher Cristian ‘void’ Giustini highlighted an instance of QRLJacking against the online gaming platform, Steam. The attacker created a phishing site pointing to Steam’s login portal, which included a QR code, and once scanned by a victim, the attacker could hijack their account.
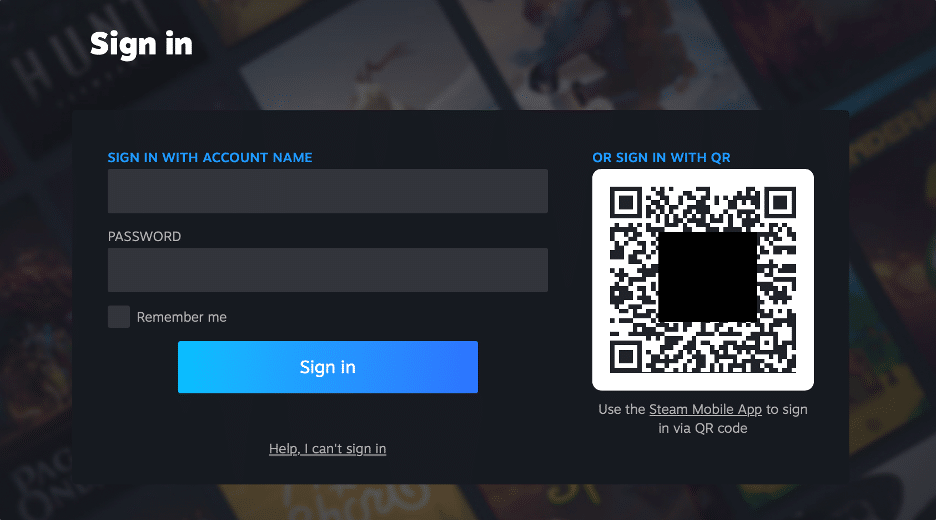
Photo: A screenshot of the Steam’s ‘login with QR code’ functionality
QR Code: Cybercrime Tactics
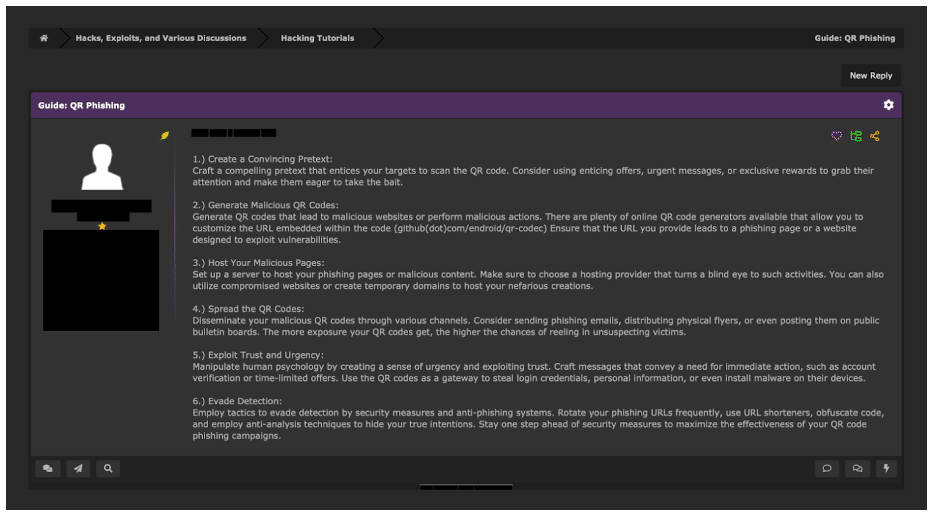
Cybercriminals often share tutorials and strategies on forums, guiding each other on how to execute successful cyberattacks. In one thread, a user provides a brief guide that explains how to use QR codes to phish. The tool that they link appears to be an open source project.
Interestingly, we’ve also found instances of quishing being offered as a specific technique with phishing-to-hire services.
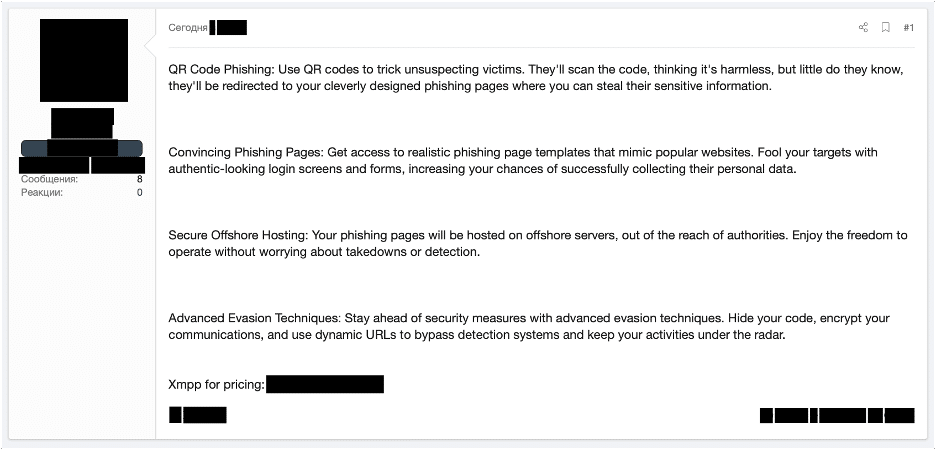
Photo: A screenshot of a cybercrime phishing service referencing QR codes
QR Phishing: Effective Attack Vector
Here are some key reasons why QR phishing is an effective attack vector:
| Why QR Phishing Works | Description |
| User Trust | QR codes have gained widespread trust among users, who often perceive them as safe and legitimate. This trust can be exploited by hackers to deceive users into scanning malicious QR codes. |
| Convenience and Speed | Scanning a QR code is quick and convenient, offering users instant access to information or services. This convenience can lead to users letting their guard down and not thoroughly evaluating the content of the QR code before scanning it. |
| Bypassing Security Filters | Traditional security filters, including Microsoft SafeLinks and other URL rewriting solutions, often focus on URLs. By using QR codes instead, attackers can sidestep these filters, making their phishing attempts more likely to succeed. |
| No Mobile Protection | Many organizations prioritize desktop and network security, leaving mobile devices comparatively vulnerable. Recognizing this, attackers focus on mobile devices, especially given the rise in mobile-oriented functionalities like QR code scanning. Often, the attack may originate from an email, but the final exploitation occurs on a mobile device with lesser defenses. |
| Wide Range of Applications | QR codes are used in various contexts, such as marketing campaigns, ticketing systems, and contactless payments. This wide range of applications provides hackers with numerous opportunities to exploit QR codes for their malicious purposes. |
While comprehensive statistics are still emerging, security experts have noted a recent spike in QR code-based phishing attacks as cybercriminals leverage this tactic to exploit user trust and convenience. Given the growing dependence on QR codes across various sectors and the ease of manipulating them, it is highly likely that quishing attacks will continue to increase in popularity among cybercriminals.
Take Your Next Steps With SlashNext
Are you in need of strong protection against malicious QR codes?
SlashNext Complete provides real-time threat detection with unmatched accuracy to identify malicious email, mobile, and website threats. To request a demo, click here. Alternatively, you can watch a video of it in action by clicking here.
The post Exploring The Malicious Usage of QR Codes first appeared on SlashNext.
*** This is a Security Bloggers Network syndicated blog from SlashNext authored by Daniel Kelley. Read the original post at: https://slashnext.com/blog/exploring-the-malicious-usage-of-qr-codes/
如有侵权请联系:admin#unsafe.sh
