
Cisco Talos coined the term “Cracktivator software” to reference counterfeit or modified software for pirated versions of Windows applications.
One of our teammates, James Nutland, led the research to look into cracked versions of the Microsoft Windows operating system and other Microsoft applications such as Office.
Both products use Microsoft key management service (KMS), which typically allows organizations to activate systems on their own network. Cracktivators co-opt this service by altering the system to allow pirated keys. The term could also apply to other applications that have been modified or pirated in some way.
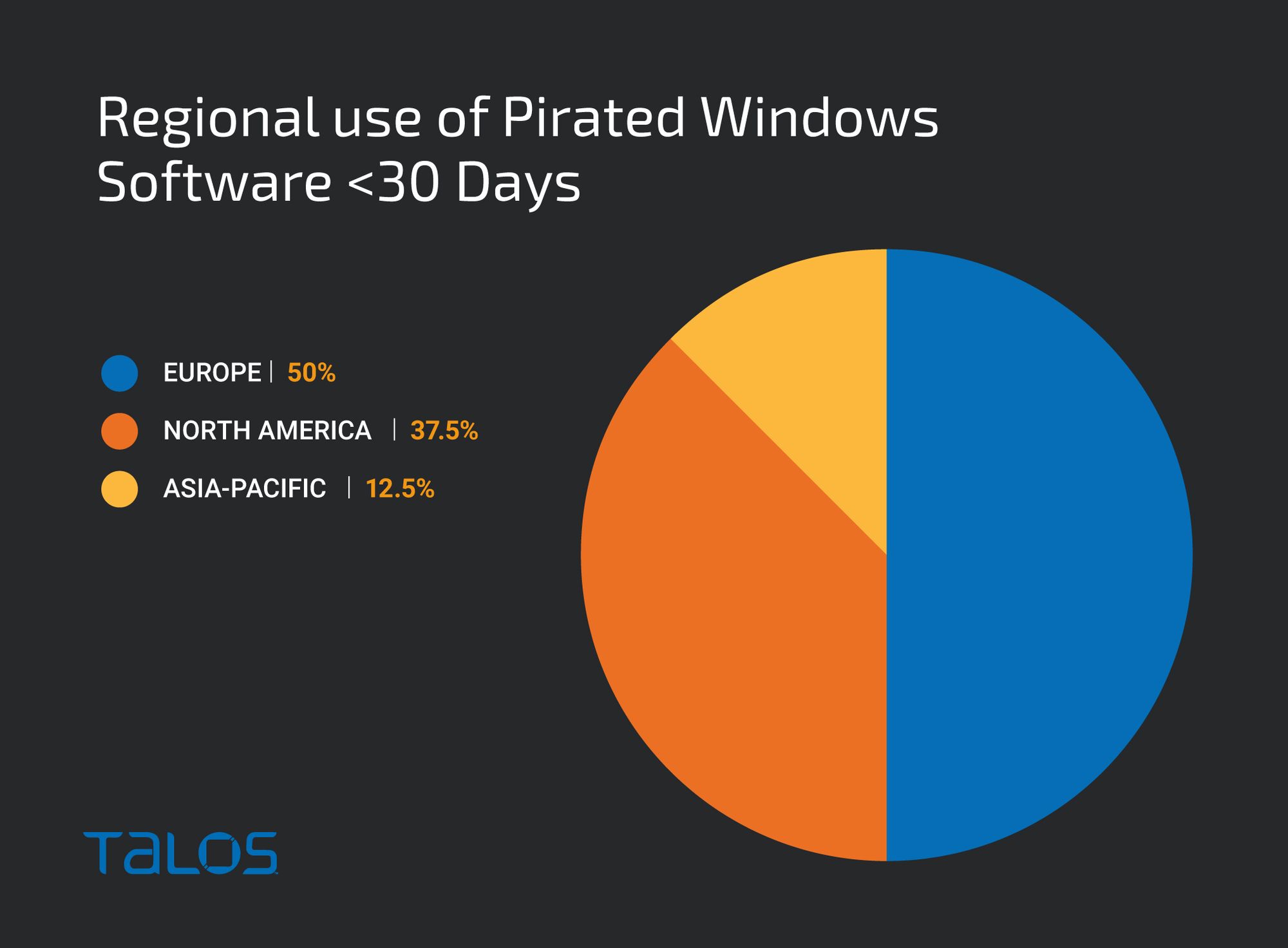
The use of Cracktivator software is a growing trend around the world. A notable majority of the organizations using cracked software are in Europe, especially Eastern Europe, in a broad range of industries. During Talos’ Ukrainian Task Force’s threat hunting operations, which is focussed on critical infrastructure, we uncovered a substantial number of organizations running this type of illegitimate software.
According to Talos data, North America also shows a variety in industry types using Cracktivator software, with the highest prevalence being in manufacturing and education, and, to a lesser extent, construction, financial services and retail. In the Asia Pacific region, the industries using Cracktivator software are predominantly within the manufacturing and government sectors.
However, there seems to be less overall Cracktivator usage in Asia Pacific than in Europe and North America, which is a shift. Asia Pacific used to have a large presence of pirated enterprise software, though we are still unsure as to the exact reason why they’ve moved away from cracked software.
The security risks of using Cracktivator software
Aside from the fact that using pirated software is illegal, the use of it brings many security risks. These include not having access to critical updates or security patches, which can leave users more open to attacks that target known vulnerabilities within Windows applications.
During our research, we also found that other threats, such as remote access trojans (RATs) and cryptocurrency mining malware, are also commonly found on systems running Cracktivator software. We’ve detected that adversaries are bundling these types of threats into modified software as a method of initial access.
In this situation, the user is typically unaware of any built-in malware when they download the cracked software (typically via torrent sites). In fact, Cracktivator software looks and sounds, in most cases, like the real thing. This is largely because threat actors don’t want users to spot anything amiss, so they can carry out whatever malicious intentions they may have (for example, establishing a backdoor to systems).
Why do organizations use Cracktivator software?
This is a complicated question, as there are many reasons as to why organizations choose (or in some cases, turn a blind eye) to using Cracktivator software. Poor security hygiene is one reason. Organization’s may not have the appropriate tools for security training, unable to spread awareness to employees about the risks of using such software.
Another reason is that certain people or departments may be under a time crunch to deliver a piece of work. Purchasing an illegitimate license may help speed up the completion of these deliverables or be cheaper than buying an actual license.
Unfortunately, while users are typing away on their Word document to get that board report in on time, there is typically a lot of malicious activity going on in the background. Therefore the short-term gains are never worth the long-term pains.
Recommendations on how to address the growing trend of Cracktivator software use
- Regularly update all software and systems with legitimate, licensed versions.
- Employ robust cybersecurity solutions to detect and mitigate threats, including installing endpoint detection response (EDR) solutions.
- Regularly monitor internal systems for any suspicious activity, such as unusual PowerShell and Netsh utility usage.
- Conduct cybersecurity awareness and training programs to inform staff about the risks associated with downloading and using cracked software.
- Block and/or monitor traffic reaching out to the associated IOCs.
- Monitor and prevent unnecessary and/or unauthorized use of system administration tools, such as remote access software.
- Ensure sensitive systems are properly segmented and not exposed to the internet to prevent lateral movement from compromised machines.
Talos’ Head of Strategic Analysis David Liebenberg recently appeared on the CyberWire podcast to talk about Talos’ Cracktivator research. Check out the conversation:
If you’d like to continue to learn more about the basics of the topics we cover on the Talos blog, read the rest of our entries in The Need to Know series.
