Given the increasing number of regulations for protecting personal and sensitive information such as intellectual property, PII and PHI, every business is concerned with data security compliance. What can we do to address this ongoing challenge?
Data security compliance requires widespread enforcement of security controls to comply with global regulations, as well as strong visibility of data usage and activity to provide auditors. It’s a foundational part of any business’ security strategy – and one that is increasingly difficult to account for when considering how many different ways data is accessed, such as cloud, web, endpoint, email and more.
Understanding how data flows through an organization is essential to figuring out how to protect it and comply with policies like GDPR, HIPAA or PCI DSS.

WEB PAGE
Data Security Everywhere
The basics of data security compliance
Here are some steps organizations should take to improve their data security compliance:
- Identify all sources of data. This includes both internal data, such as customer records, employee data, financial data, and external data, such as data from social media, customer surveys, and marketing campaigns.
- Map the flow of data. Once you have identified all sources of data, you need to map how that data is flowing through the organization. This includes identifying all systems and applications that data is stored in and used by.
- Identify sensitive data. Once you have mapped the flow of data, you need to identify all sensitive data. This includes data that is subject to compliance regulations, as well as data that is proprietary or confidential.
- Assess the risks. Once you have identified sensitive data, you need to assess the risks to that data. This includes identifying potential threats, such as unauthorized access, data breaches, and cyberattacks, as well as the potential impacts of those threats.
- Implement security controls. Once you have assessed the risks, you need to implement security controls to mitigate those risks. This may include implementing technical controls, such as firewalls and intrusion detection systems, as well as administrative controls, such as security policies and procedures.
Enforce compliance with Data Security Everywhere
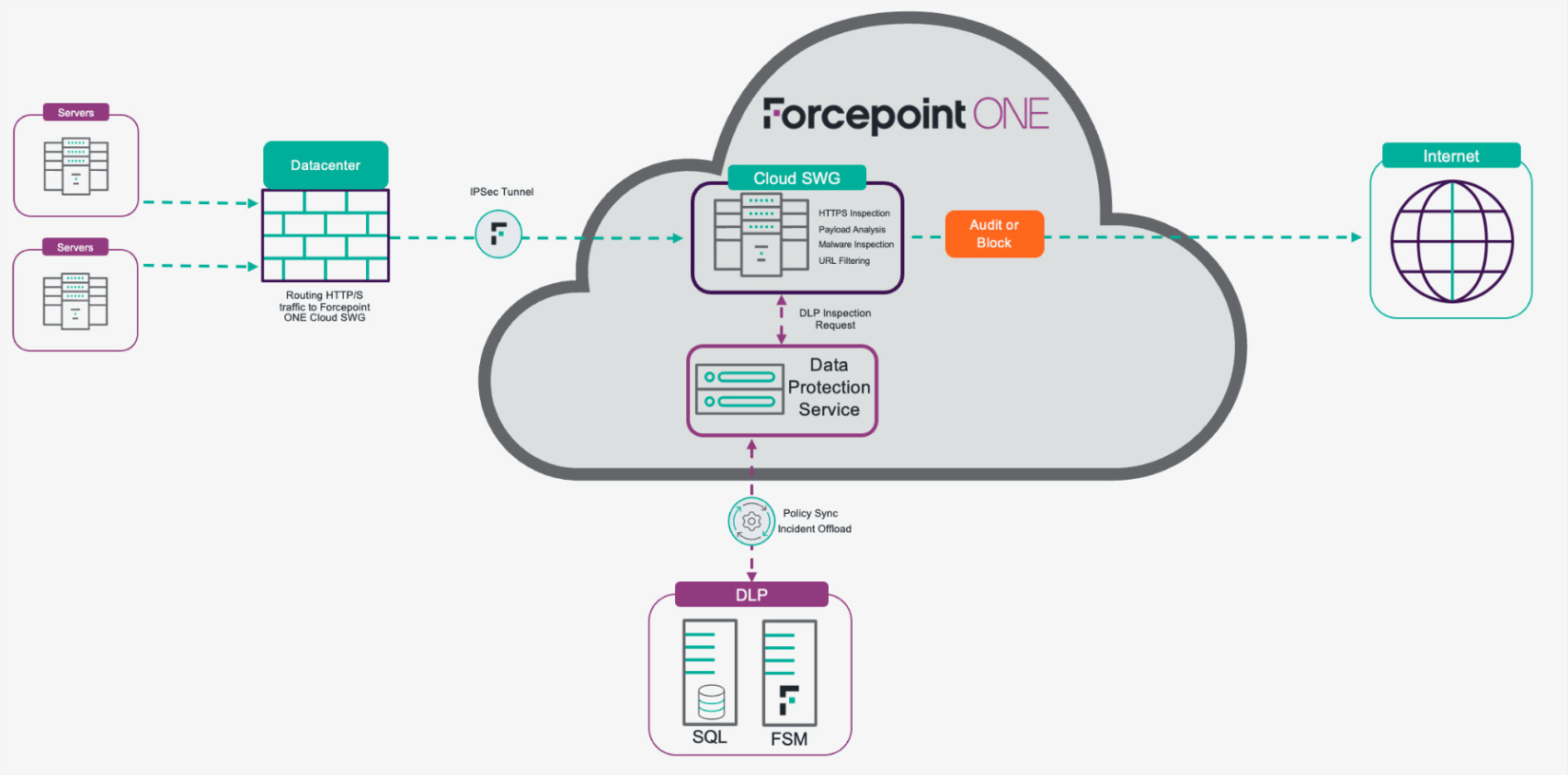
After understanding the flow of data, let's expand on "Map the flow of data" to include system and application communication with the external world via web protocols (HTTPS). This is important because we need to protect both users and systems from data exfiltration scenarios.
With Forcepoint Data Security Everywhere, it is possible to protect users and servers/systems by controlling server communication with our Forcepoint ONE SWG and preventing sensitive data from leaving the premises on open connections. In turn, organizations can easily enforce their data security compliance strategy.
Here are some specific examples of how Forcepoint Data Security Everywhere can be used to protect servers/systems:
- Controlling server communication: Forcepoint ONE Security Service Edge (SSE) can be used to control server communication by filtering traffic and blocking unauthorized connections. This can help to prevent data breaches and other security incidents.
- Preventing sensitive data from leaving the premises: Data Security Everywhere can be used to prevent sensitive data from leaving the premises on open connections. This can be done by creating policies that block sensitive data from being transferred from servers to unauthorized destinations.
See our high-level architecture for accomplishing these scenarios and use cases:
- Use case 1: Prevent data theft from servers with limited web access.
- Use case 2: Use your existing DLP investment to expand data security policies to more channels.
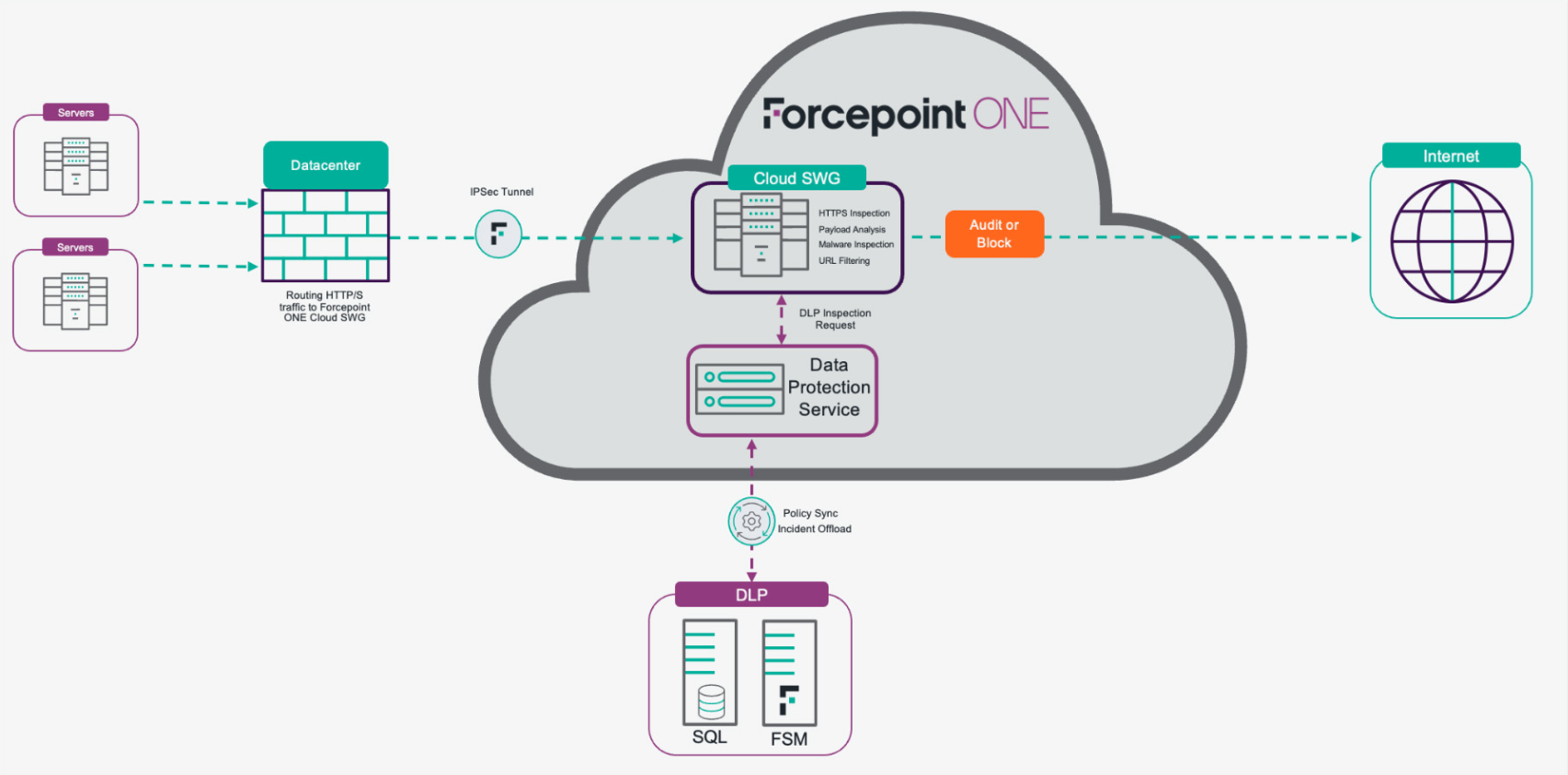
Overall, Forcepoint DSE provides a comprehensive solution for protecting both users and servers/systems from data loss and meeting data security compliance needs.

Erik Scoralick
Erik Scoralick is a Leader for Americas Strategic Solution Architects at Forcepoint and has been working in the cybersecurity market for over 13 years. During this time, he worked for various security vendors gaining a broad experience across several security domains such as Network, Endpoint,...
Forcepoint is the leading user and data protection cybersecurity company, entrusted to safeguard organizations while driving digital transformation and growth. Our solutions adapt in real-time to how people interact with data, providing secure access while enabling employees to create value.