More Aggressive Time-to-Exploit Vulnerability Trends Affect Oracle and SAP Security Too

Mon, 10/16/2023 – 13:49
On September 28th, Mandiant published their Time-To-Exploit trends report, including several very insightful stats covering vulnerabilities exploited between 2021 and 2022. (It’s a great read on its own, and we recommend you review it!) Here at the Labs, we thought it would be a good idea to correlate the insights from that report and highlight how they relate to the observations the Onapsis Research Labs (“ORL”) have made on vulnerabilities affecting ERP Applications.
1 – Number of Exploited CVE(s) Continues to Increase
If we look at the National Vulnerability Database (“NVD”), it becomes very apparent quickly that the number of CVEs continues to increase year after year. Looking at the total number of CVEs and forecasting to the end of year, it gives us a clear growing trend.
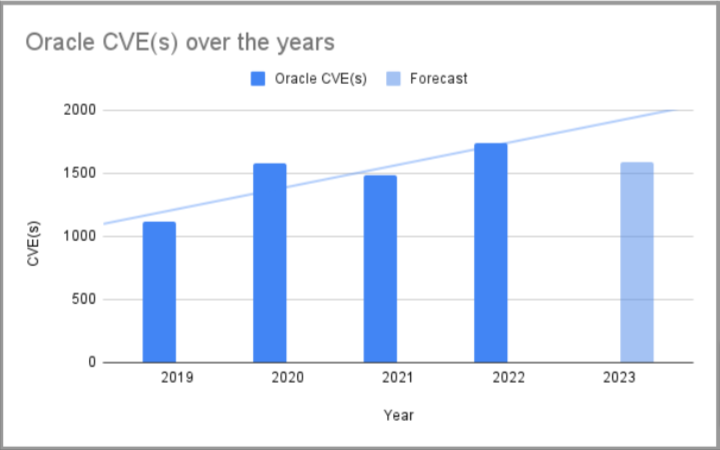
That trend holds true when it comes to the largest vendors of ERP Applications (i.e., SAP and Oracle). The Onapsis Research Labs continues to see the rising trends, albeit increasing at different rates for each of the vendors.

Image 1: Evolution of released CVE(s) over the years

Image 2: Evolution of released Patches for SAP over the years (1 Patch fixes 1 or more vulnerabilities)

Image 3: Evolution of released CVE(s) for Oracle over the years
Well, with these growing CVE numbers, it should come as no surprise that this increase in the number of CVEs has a growth effect on the number that are actually exploited in the wild.
2 – Time to Exploit Continues to Decrease
Additionally, Mandiant highlights an observable decrease in the time-to-exploit for the actively exploited vulnerabilities, meaning defenders have less time to respond to vulnerabilities, as they are actively exploited more quickly than ever before based on preceding historical timeframes.

Image 4: Evolution of Time To Exploit over the years
N-day vulnerabilities are published, known security flaws that may or may not have vendor-issued security patches (e.g., from SAP or Oracle) available. When it comes to these N-day vulnerabilities, even when a primary exploitation was broadly distributed across the time span of 6 months, the data shows that the first exploitation of a vulnerability is still more likely to happen within the first month of the vulnerability becoming known.
While this data uses average time-to-exploit across multiple vulnerabilities, it nevertheless aligns well with our own observations around the typical SAP or Oracle exploits we’ve reported on in the past, such as the RECON vulnerability. In the case of RECON, we detected active exploitation as soon as 72 hours after the patch release by SAP (more information here).
3 – The Number and Variety of Exploited Targets by Threat Actors is Increasing Rapidly
Microsoft, Google, and Apple continue to be the most exploited vendors year-over-year, according to Mandiant. However, what’s interesting from the period of data presented by Mandiant is that other vendors than those three actually accounted for more than 50 percent of the overall vulnerabilities exploited. Historically, this is the first time this has happened, and it points to increased interest in exploiting applications and software that are not managed by three large operating system and application software vendors with dynamic, well-funded threat research and product security teams.
As stated in the report, “Actors increasingly target a wider variety of software, including those less regularly prioritized for speedy remediation. As a result, there is a potentially higher likelihood that attackers are able to find success in targeting less ubiquitous software than they would if they were to target more common products, such as Microsoft operating systems or various browsers.”
Onapsis Research Labs maintains a Threat Intel Cloud, tracking various ERP systems and software applications in real time and observing threat actor behavior to better understand their underlying tactics, techniques, and procedures for business-critical application software vulnerability attacks. As noted above with the rise in CVEs and patches released by some of the ERP vendors we follow, the Labs continue to see more aggressive and more plentiful attacks on the critical application layer from these ERP vendors across our honeypot network. Ultimately, this aligns with Mandiant’s data and demonstrates that threat actors have greater access to critical systems (e.g., from digital transformation and cloud enterprise portals) as well as greater knowledge and sophistication to expand their arsenal of attacks beyond Microsoft Windows or a Chrome browser.
It is also noteworthy to mention that in August of this year, CISA included SAP and Oracle vulnerabilities within their cybersecurity advisory for the top routinely exploited vulnerabilities of 2022. While this was the first appearance of these vulnerabilities to this list, we, at the Onapsis Research Labs, fear that it won’t be the last appearance. In fact, at this rate, we anticipate this number to grow over the coming years.
4 – Older Vulnerabilities are Still Valuable Targets for Threat Actors
Unsurprisingly, a still significant number of vulnerabilities were detected as exploited after six months of becoming known; some of them were found to be exploit targets years after that. While there always tends to be a preference for zero-days or even more recently published N-day vulnerabilities, threat actors are finding opportunities to target older and well-known vulnerabilities. Mandiant states, “A key takeaway from this is that while threat actors generally prefer newer vulnerabilities, they will not completely shy away from vulnerabilities due to age and public knowledge; threat actors still value using already known and documented vulnerabilities as opposed to discovering new ones.”
The Onapsis Research Labs has continuously observed the active exploitation of these older, well-known, and often well-publicized vulnerabilities spanning a number of years – from ICMAD (CVE-2022-22536, patched in 2022) to RECON (CVE-2020-6287, patched in 2020) to even the Invoker Servlet vulnerability (CVE-2010-5326, patched 13 years ago).
So, What Do We Do With This Data Now?
Mandiant’s report and its wealth of data combined with our own observations and threat research from the Onapsis Research Labs demonstrate that both software vendors and the organizations that use them still have a lot of work ahead of them. For software vendors, greater application complexity, digital transformations in the cloud (which offer greater ingress), and the booming “black-hat business” (e.g., ransomware) create growing challenges in locking down security and managing the growing number of vulnerabilities discovered. For organizations and users, keeping up with these vulnerabilities can be a challenging endeavor, made even more daunting if you’re providing patch management for critical, “can’t go down” critical ERP systems.
How do we solve this? Threat intelligence, technology, and automation for better attack surface visibility and more efficient and effective risk-driven vulnerability management programs.
Focusing on our ERP targets for a minute, the more aggressive push by threat actors to exploit vulnerabilities there (rather than targeting Microsoft, Google, or Apple) requires our defenders to be better prepared to prevent compromises due to the higher likelihood of exploitation of known vulnerabilities.
In general, the Onapsis Research Labs frequently advises our customers to…
- Identify your ERP applications, modules and components to better understand your attack surface and threat landscape. (For SAP, we’ve actually released an open-source Java Endpoint Analyzer that helps identify open endpoints. Give it a try!)
- Understand which vulnerabilities are present in and which patch notes are applicable to your environment. Set up a plan to prioritize and then tackle these security weaknesses in the most effective way possible. (The Onapsis Platform is great for helping teams understand where they’re vulnerable and what they should patch first.)
- Recognize that vulnerabilities affecting other vendors not named Microsoft, Apple, or Google are growing targets for threat actors and, in most cases, are a blind spot for organizations. (This is frequently the case for vulnerabilities affecting SAP and Oracle business applications.)
- Consider merging business-critical application security more cohesively into your existing vulnerability management and detection and response security programs. This helps provide important visibility into the direct threats to your most critical ERP systems. (The Onapsis Platform is the only SAP endorsed solution that addresses these processes in an integrated way with your existing stack.)
*** This is a Security Bloggers Network syndicated blog from onapsis.com/ authored by ltabo. Read the original post at: https://onapsis.com/blog/aggressive-time-to-exploit-vulnerability-trends-affect-oracle-and-sap-security