Author: Eric Avigdor, VP of Product Management, Votiro
Malware transmitted via email has been a persistent plague to organizations for decades. Every organization has email, and sending emails with toxic payloads requires little infrastructure or effort, making it an attractive avenue for attackers. This is why email is one of the top vectors for ransomware delivery, according to 2023 research by Verizon – which we discuss here.
Failing to protect against malware can lead to a breach costing US organizations an average of $9.44 million per incident. This is why Cybersecurity and Infrastructure Security Agency (CISA) conducted a study to discover if Content Disarm and Reconstruction (CDR) is an effective solution to mitigate embedded threats in emails.
In this article, we dive deep into CISA’s research, as presented during the 2023 RSA Conference, and discuss the findings that indicate how well CDR improves email security and how it can be effectively implemented in your environment.
CISA’s Research
CISA conducted a research pilot study in 2021 to determine the effectiveness of CDR in eliminating hidden threats in email. The focus of this study was explicitly on email security and compared the performance of CDR against a scenario with no security controls using a test set of known threats. It is worth noting that more advanced CDR solutions offer APIs and native integrations, enabling protection across many file ingestion channels and supporting a broader range of content formats than just email and email attachments.
Not All CDRs Are Created Equal
While the research provided by CISA is valuable for its design scope, it still leaves many unanswered questions. When conducting this assessment, it assumes all CDR solutions are created equally. Depending on the maturity level of the CDR solution, the resultant file created by the CDR may have a lower level of fidelity than the original, meaning that components such as formatting, layout, or macros may have been lost in the CDR process. These features, however, are retained by more advanced CDR solutions.
More Isn’t Always Better
It was also unclear why a serial approach was required to sanitize the email. This calls into question whether similar results could have been achieved using a single CDR solution as, in theory, the sanitization process of a single mature CDR solution should have generated a safe file in its output, which was then fed into the other CDRs. Reducing the number of CDRs involved in the process would have achieved faster sanitization and resulted in a lower cost of implementation. It’s much like washing a load of laundry twice, any dirt should have come out in the first wash thus, the second wash only slows the process and wears things out.
Putting CDR to the Test
With regards to the testing environment, it starts as a self-contained email system rather than a live version, utilizing a controlled personal storage table (PST) export containing emails with standard attachment file types to ensure the contents were consistent throughout the testing process. While this effectively controls the test data set, it does not accurately mimic the constant load a production CDR solution must perform under.
In this environment, the test PST was analyzed using static and dynamic antivirus (AV) analysis to create a baseline score. This score establishes that the test file contains hidden threats and the known quantity of these threats. Once the PST is processed through CDR it gets retested using the same battery of AV to show quantifiable proof of the amount of malicious content eliminated.
The configuration of the CDR solution for analysis was novel in this environment. Rather than testing a single CDR solution, CISA serially chained three different CDR solutions to create multiple rounds of sanitization before passing it off for a final set of static and dynamic analyses. By comparing the outcome of CDR sanitization to a baseline, CISA sought to determine if CDR is effective for email defense.

Figure 1: Process flow for evaluating
CDR efficacy.
CISA’s Findings
The study’s findings revealed that implementing CDR technology resulted in a significant reduction of 90% in malicious content that managed to bypass security measures. The static analysis results showed a remarkable 98% reduction in risk content, while dynamic analysis results showed a reduction ranging from 52% to 74%, depending on the file type. Both variations show CDR delivers a dramatic improvement in the number of threats in files, significantly reducing the amount present after CDR is applied.

Figure 2: 2021 Pilot Results:
second-round assessment results showing outcomes at each stage.
However, the email samples used in the study only included a limited selection of common file types such as GIF, PDF, Docx, xls, and ppt. While this provides a good baseline which most CDR solutions already cover, it falls short of encompassing modern organizations’ wide range of file types. Advanced CDR technologies offer broader coverage, sanitizing a wider variety of file types, including less common ones such as password-protected zip archives or profession-specific file types like CAD design files, 3d renderings, and more, thus providing enhanced protection against potential threats.

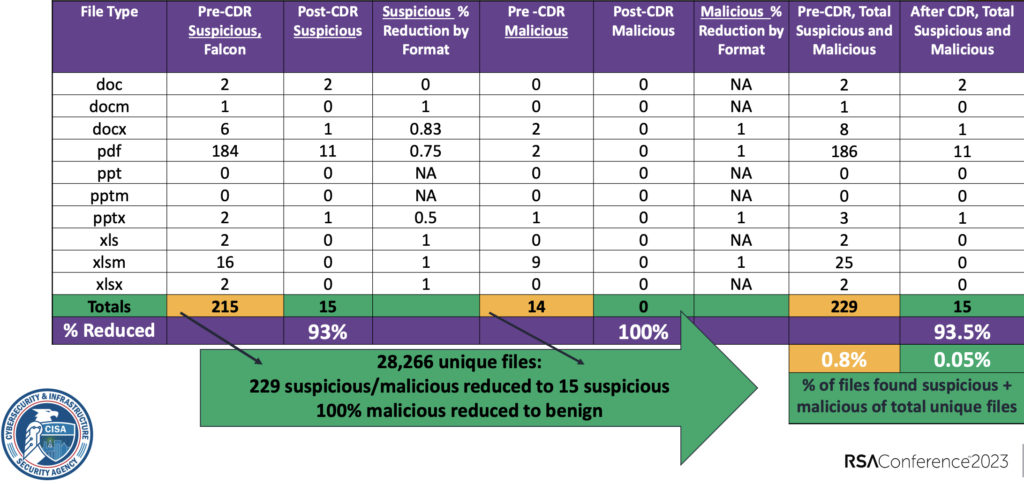
Figure 3: 2019 DHS Pilot Results:
breakout of initial results by file type.
What it Means
CISA emphasizes the critical importance of implementing a CDR-style solution, as their testing showed it directly addresses the primary vector for ransomware attacks. This echoes Gartner’s 2022 assessment of CDR providing a High Benefit to organizations that implement it. While CISA’s study recommended an isolation environment be used to mitigate hidden threats effectively, this phrasing overcomplicates the implementation. The CDR simply needs to sit between incoming email and the server, processing it before it ever makes it to the server. This creates a buffer of safety, preventing malicious content from being stored on the server.
CDR sanitizes files in real-time, which is faster than the time required for static or dynamic analysis, which in some cases may not be needed at all. While static and dynamic analysis focuses on known threats and threat-related behaviors, CDR sanitizes new variants with malicious behaviors unknown to the threat community.
One of the benefits of the testing is that CDR “exhaust” renders valuable intelligence. By escrowing off the original data and analyzing it periodically against known AV solutions, organizations can quantify the eliminated threats and determine the level of advanced protection the CDR provides.
Get Proven Value with CDR
CISA showed that CDR effectively stops hidden threats in email, but email is not the only channel that malware enters through. A well-prepared organization needs to consider all malware vectors, including files downloaded from web browsers, uploaded to cloud storage, and or shared across organizations via collaboration tools. This requires a CDR that integrates holistically throughout the IT organization.
Votiro is a category-leading CDR solution provider, helping organizations protect themselves from threats hidden in files. Votiro goes beyond traditional detection-based protections, taking a Zero Trust approach, and sanitizes all files that flow through it. Rather than requiring a unique tech stack with complex configurations and changes to your environment, Votiro delivers protection through APIs.
Contact us today to learn more about Votiro and how we can help your organization create a secure foundation. And if you’re ready to try Votiro for yourself, start today with a 30-day trial of the Votiro platform.
*** This is a Security Bloggers Network syndicated blog from Votiro authored by Votiro Team. Read the original post at: https://votiro.com/blog/insights-from-cisas-study-on-cdr/
如有侵权请联系:admin#unsafe.sh
