
2023-10-12 06:46:45 Author: securityboulevard.com(查看原文) 阅读量:6 收藏
Multiple vulnerabilities in popular and widespread applications have been disclosed recently, tracked as CVE-2023-36845, CVE-2023-40044, CVE-2023-42793, CVE-2023-29357, and CVE-2023-22515. These vulnerabilities, which affect several products and can be exploited to allow arbitrary code execution, bypass access controls, and escalate privileges, can be extremely dangerous and pose serious security risks.
Imperva customers who use Cloud WAF and WAF On-Prem with emergency feed updates are protected against these threats.
Half of these vulnerabilities are remote code execution bugs or RCE. RCE, a vulnerability that allows an attacker to run code on a target system without authorized access, has risen steadily over the last year. Since September 2022, RCE exploitation attempts have risen 56%, due in part to sophisticated attack tools, the frequency of vulnerable, unpatched devices, and the amount of data that can be stolen for financial gain in an RCE attack.
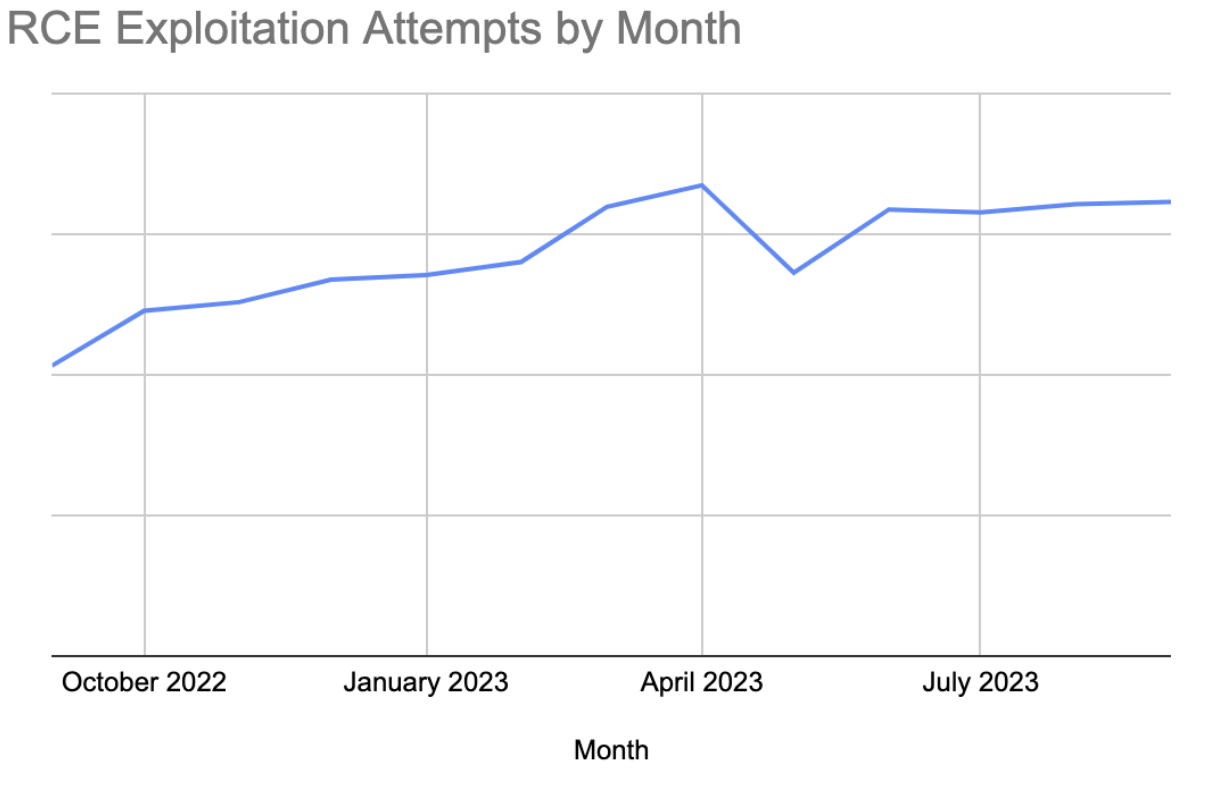
The two recently released RCE vulnerabilities are in Juniper and Progress systems. CVE-2023-36845, an unauthenticated RCE bug in Juniper J-Web, allows an unauthenticated attacker to perform remote code execution on the company’s switches and firewalls that are public-facing. Exploitation of this attack is pretty straightforward, making the attack complexity low and offering a low barrier of entry to hackers. This poses a real threat to organizations that rely on these appliances for network infrastructure.
Another vulnerability, CVE-2023-40044, is a deserialization RCE issue in WS_FTP server. The company behind the WS_FTP file-sharing software, Progress, also recently dealt with a vulnerability in its MOVEit software. The WS_FTP software uses a vulnerable function in the server. This function does not sanitize the user input properly and allows deserialization, ultimately achieving remote code execution on its servers, even with open-source tools like ysoserial.
This vulnerability has a severity rating of 10 out of 10, and Imperva has already seen over 11,000 exploitation attempts.
Three other recently mitigated vulnerabilities include authentication bypass in JetBrains TeamCity, and escalation of privilege in Microsoft SharePoint and Atlassian Confluence.
CVE-2023-42793, a JetBrains TeamCity authentication bypass issue, allows an unauthenticated attacker to bypass any validation and create an admin account, granting access to the server and exposing the source code of proprietary software and intellectual property of organizations. This could potentially result in supply chain attacks if an attacker introduced malicious code into the company’s proprietary applications.
CVE-2023-29357 tracks an elevation of privilege vulnerability in Microsoft SharePoint Server. This bug, which could allow attackers to impersonate any user on the SharePoint server and gain administrative privileges, can lead to remote code execution on the server by sending a specially crafted HTTP request that contains a tampered JWT payload.
CVE-2023-22515 is a critical privilege escalation flaw affecting Confluence Data Center and Server versions 8.0.0 and later. It can be remotely exploited in low-complexity attacks without user interaction, allowing attackers to create unauthorized Confluence administrator accounts and gain access to Confluence instances.
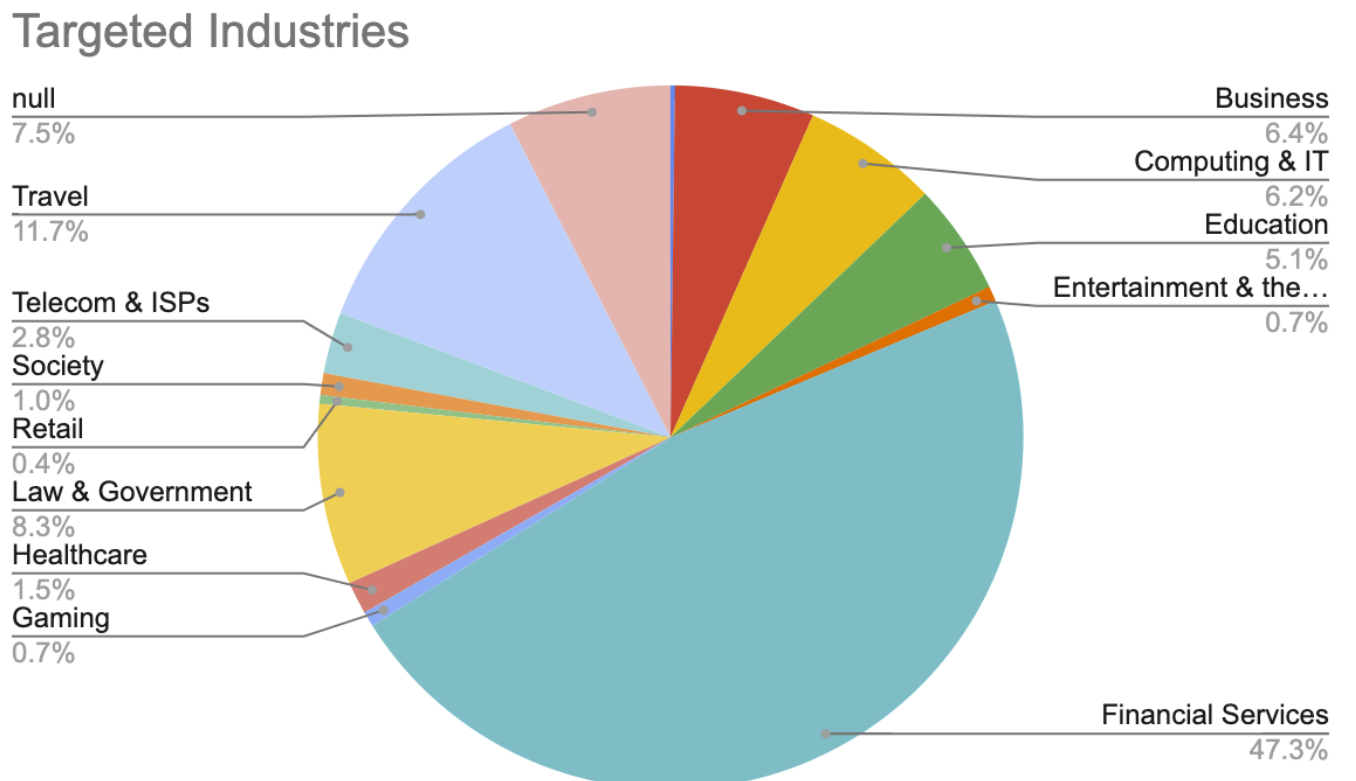
Imperva has seen almost 200,000 distinct attack attempts across all four vulnerabilities since these issues were disclosed, beginning on September 20. The financial services industry has been the primary target, at almost 50% of all attack attempts, which is double the average for all RCE attacks this year. Most attacks target US-based sites, at over 45%, followed by Japan at 7%.
Attack attempts have primarily come from the Go HTTP library, as well as regular and Tor-based bots.
As well as Imperva’s protection, all affected companies have released patches for these issues, and all users should update systems immediately. The patches can be found here:
The post Recent Vulnerabilities in Popular Applications Blocked by Imperva appeared first on Blog.
*** This is a Security Bloggers Network syndicated blog from Blog authored by Gabi Stapel. Read the original post at: https://www.imperva.com/blog/recent-vulnerabilities-in-popular-applications-blocked-by-imperva/
如有侵权请联系:admin#unsafe.sh
