Step-by-step configuration instructions of single sign on for SAP Fiori application with Azur 2023-10-11 13:47:45 Author: blogs.sap.com(查看原文) 阅读量:19 收藏
Step-by-step configuration instructions of single sign on for SAP Fiori application with Azure AD
Pre-requisite:
SSL need to be configured first before configuring for SAML2 authentication.
Configuration Steps:
Activating the Services
1. Goto Transaction SICF, enable below services
/sap/bc/saml2/cdc_ext_service
/sap/bc/webdynpro/sap/saml2
/sap/public/bc/icf/logoff
/sap/public/bc/sec/saml2
/sap/public/myssocntl
2. On the Maintain Services page, enter one of the service name from the list.
3. Right-click the service in the tree menu view, select Activate Service.
4. Prompt to activate the service, click Yes with tree option.
Enable SAML2 Local Provider Setting
1. Run the transaction SAML2 or open the URL
https://<FQDN>:<ICM_HTTPS_PORT>/sap/bc/webdynpro/sap/saml2?sap-client=100&sap-language=EN
Note : If you want to use webdispatcher then open the SAML2 URL through webdispatcher Url
https://<WEBDISPATCHER_FQDN>:<WEBDISPATCHER_ICM_HTTPS_PORT>/sap/bc/webdynpro/sap/saml2?sap-client=100&sap-language=EN
2. Click on Enable SAML2.0 Support and Select “Create SAML 2.0 Local provider”.
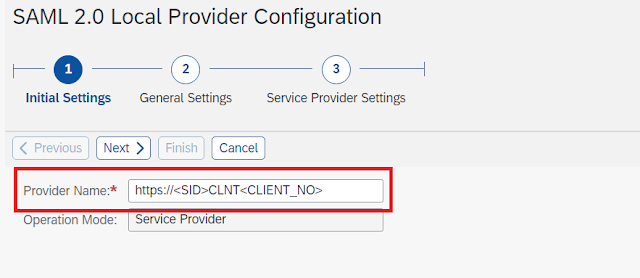
3. Enter the Provider Name https://<SID>CLNT<CLIENT_NO> on Initial setting screen. Click Next.
4. Choose Automatic in Selection Mode on Service Provider Settings and Select Finish.
5. After Click on Finish, it will be redirect you to Configuration Page.
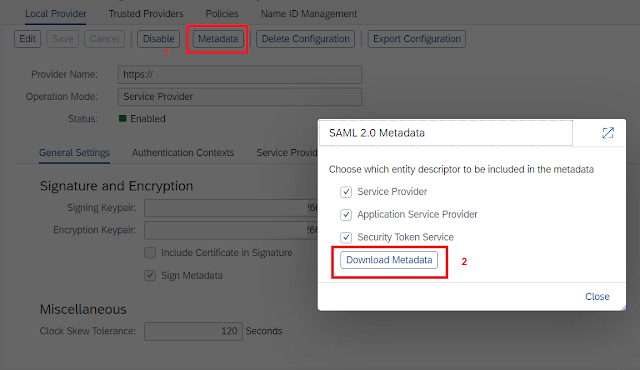
6. Click on Metadata button to get pop-up for the metadata download, then select Download Metadata.Make sure browser pop-up is allowed.
7. Now the RPT can be performed at Azure Enterprise Application, by either directly uploading the metadata.xml file or providing the details manually in enterprise application of fiori.

8. You can provide the identifier same as it has been created in step 3 in transaction SAML2

9. Provide the fiori sign-on url in the configuration and Click on save.

8. Configure the following user attributes & claims for application. To manage these attribute values, select Edit and set the Name identifier as Unspecified & source attribute as user.onpremisesamaccountname.

9. Now the signed certificate and federation can be downloaded from the section SAML Certificates

10. As a next step, open the SAML2 and click on Trusted Providers tab.
11. Select the the Upload Metadata File.
12. Upload the federation metadata xml which was downloaded in step 9
13. In the Next Step Metadata Verification, Upload the federation certificate downloaded in Step 9 and Click Next
14. In Signature and Encryption Step Choose the Digest Algorithm
15. In Authentication Requirements, Choose the shown and Click Finish.
16. First Click on Edit and then Add then select the Unspecified and then Save the setting as shown.


17. Then Click on Enable to activate the configuration.
18. Goto Transaction SICF , enter the service name or external alias example /sap/bc/ui2/flp and open the service
19. Select Logon Data Tab. Choose the Alternative Logon Procedure and set SAML Logon at 1 and Save.
20 . Test the Service by openeinf the fiori URL in the browser.
如有侵权请联系:admin#unsafe.sh