The need for integrated cybersecurity solutions has never been more pressing. With the growing complexity of cyber threats, having siloed security tools is no longer an option. This is where the synergy between Smart SOAR and Darktrace comes into play, offering an integrated platform for automated threat hunting and incident response.
Out-of-the-box, Smart SOAR integrates with Darktrace, a leader in AI-driven cybersecurity, to offer a set of commands that automate and streamline various aspects of threat hunting and management. In this article, we’ll review three workflows that cover real-time threat detection and acknowledgment, threat hunting, and post-incident analysis.
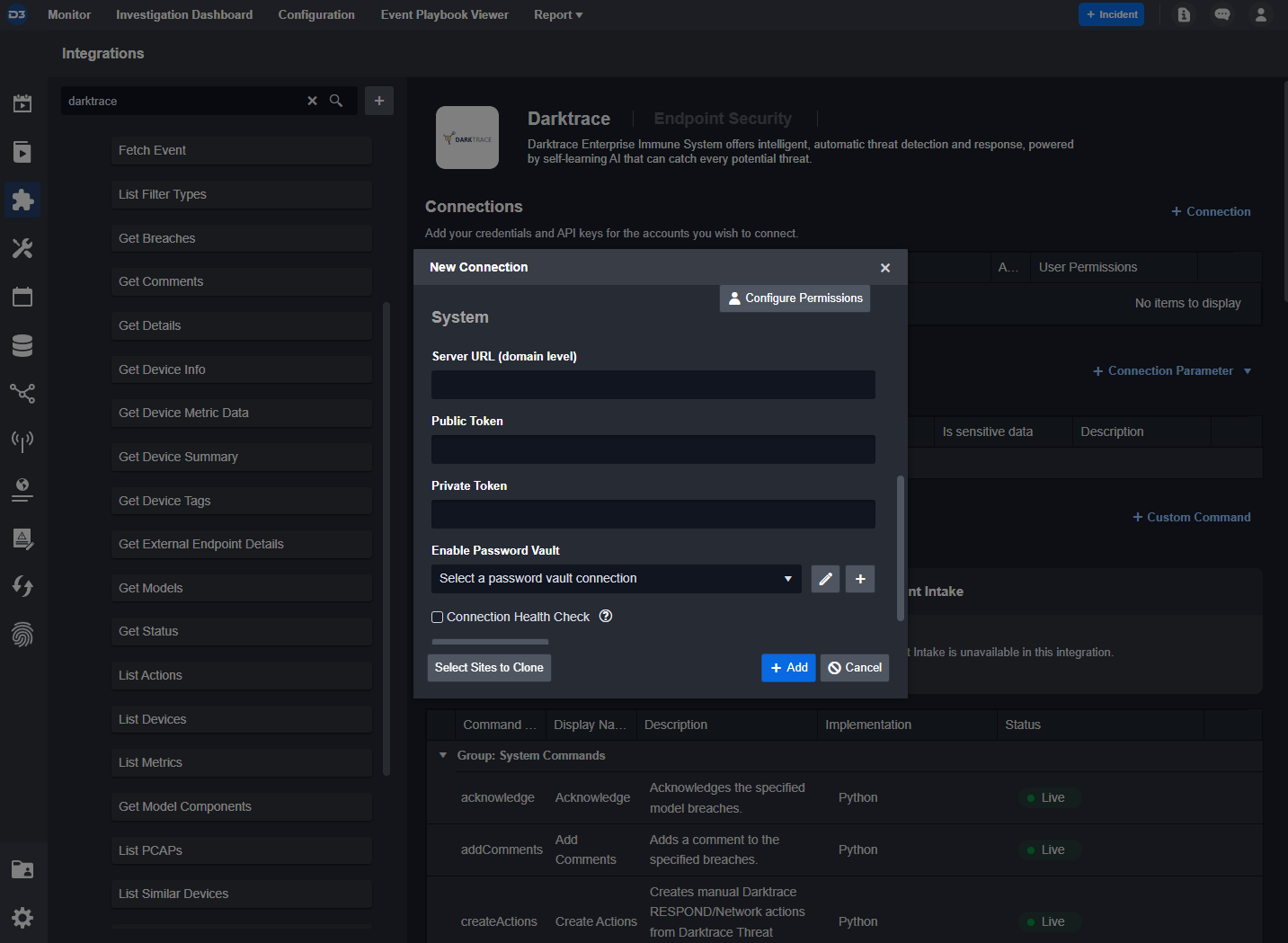
Setting up the Connection
The input parameters for a new connection to Darktrace are:
- Server URL
- Public Token, and
- Private Token
Once these are added and the connection passes successfully, each of the 29 out-of-the-box commands are ready to use.
Workflow 1: Real-Time Threat Detection and Acknowledgement
This workflow is designed for real-time response to detected breaches. It begins by gathering details on detected breaches so that the user can acknowledge the ones that need addressing. This changes the status of the breach in Darktrace from within Smart SOAR. The workflow then lists actions that have already been initiated on specific devices and breaches. If any required actions are missing, the Create Action command can be triggered to complete the containment.

Workflow 2: In-Depth Device Analysis for Threat Hunting
This workflow focuses on proactive threat hunting through comprehensive device analysis. It starts by enumerating all devices on the network, gathering detailed information and metrics on selected devices. The workflow also fetches and allows modification of device tags within Darktrace for categorization or further analysis. This provides a deep dive into the network, aiding in the early identification of potential threats.
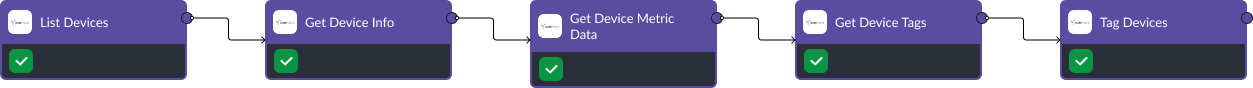
Workflow 3: Post-Incident Analysis and Reporting
This workflow aims to provide a detailed analysis after a security event has occurred. It searches for and retrieves information about past security breaches, compiles any added comments or notes, and generates Packet Capture (PCAP) files for forensic analysis. The workflow then lists all PCAPs associated with the case for a comprehensive post-mortem.
Takeaway
The integration between Smart SOAR and Darktrace enables organizations to automate intricate tasks related to threat detection, incident response, and post-incident analysis. With this integration, not only are hours of manual work saved, but the automation standardizes security procedures, minimizing room for error.
The post Why Smart SOAR is the Best SOAR for Darktrace appeared first on D3 Security.
*** This is a Security Bloggers Network syndicated blog from D3 Security authored by Pierre Noujeim. Read the original post at: https://d3security.com/blog/darktrace-smart-soar-integration-spotlight/