2023-10-7 21:25:58 Author: securityboulevard.com(查看原文) 阅读量:5 收藏
Welcome to the 12th post in our weekly series on the new 2023 OWASP API Security Top-10 list, with a particular focus on security practitioners. In this series we are taking an in-depth look at each category – the details, the impact and what you can do about it. To see previous posts you might have missed, click here.
This post will put a spotlight on Injection, which used to be its own category (OWASP API8:2019) but has now been subsumed into OWASP API10:2023 (Unsafe Consumption of APIs).
TL;DR
API injections involve malicious data or code being inserted into an API, posing risks like unauthorized access and data breaches. Our data show injections constitute the largest single API risk group, so we recommend you treat them as a critical part of your API security program.
The Details
An API injection attack, often referred to as Injection, is a type of security vulnerability that occurs when an attacker is able to manipulate or inject malicious code into an API request. This malicious code is typically designed to exploit the API’s processing mechanism and execute unintended actions on the server. However, the most recent OWASP Top-10 2021 moved client-side injections (aka Cross-Site Scripting or XSS) into the Injection class (A03:2021). So, it seems that since 2021 injections are officially not a server-side threat anymore.
While we’ve counted more than 50 injection-related CWEs in our vulnerability data, the most common API injection attacks we saw in our most recent API ThreatStats™report included:
- Cross-Site Scripting (CWE-79), also known as XSS, is where untrusted data is improperly handled, allowing attackers to inject malicious scripts into web pages.
- SQL Injection (CWE-89), also known as SQLi, is where untrusted data is used to construct SQL queries without proper validation or sanitization.
- Improper Input Validation (CWE-20), is quite simply where user input is not adequately validated, which can impact both raw data and metadata.
Note the first two – XSS and SQLi – accounted for over 40% of all injection-related CVEs analyzed in Q2-2023, or over 12.5% of all vulnerabilities examined. And even if we ignore XSS, server-side injections remain the most dangerous threat for APIs (based on Risk X Likelihood analysis), as discussed in our 2022 Year-End API ThreatStats™ Report.
By the way, Injection Attacks are also no. 1 in our ChatGPT generated API Security Top-10, based on analysis of the most complete set of API security bulletins, bug bounty reports, CVEs, and exploits data gathered over the past 25 years.
What’s the Impact?
API injection attacks can have severe consequences on the targeted application, potentially leading to data breaches, data manipulation, unauthorized access, and even system compromise. The impact varies depending on the type of injection attack and the specific vulnerabilities present, but it can result in:
- Unauthorized access to sensitive data.
- Data corruption or deletion.
- Execution of arbitrary code on the server.
- Complete compromise of the application or server.
The press is rife with examples of API Injection attacks, including the recent MOVEit vulnerabilities which have impacted 2000+ organizations and 62M+ people so far, or the infamous Log4j vulnerability reported in late-2021 which is still plaguing some organizations.
What Can You Do About It?
To prevent API injection attacks and protect your application, you should follow security best practices, including:
- Input Validation and Sanitization: Ensure that all user input, including data sent via API requests, is properly validated and sanitized. Reject any input that doesn’t conform to the expected format or contains suspicious characters.
- Parameterized Queries: When interacting with databases, use parameterized queries or prepared statements to separate user input from SQL queries.
- Escaping Data: If you’re embedding user input in API responses or other parts of the application, make sure to properly escape the data to prevent cross-site scripting (XSS) attacks.
- Allowlisting: Define and enforce strict allowlists for input and output data. Only allow specific data formats, characters, or values that are expected.
- Rate Limiting and Access Controls: Implement rate limiting to prevent abuse of your API and restrict access to authorized users only. Use authentication and authorization mechanisms to control who can access what resources.
- API Security Testing: Regularly perform security testing on your APIs, including penetration testing and code reviews, to identify and fix vulnerabilities.
- API Gateway and WAF: Consider using an API gateway and a Web Application Firewall (WAF) to help filter out malicious requests.
- API Security Solutions: Consider using Web Application and API Protection (WAAP) solutions to safeguard against various injection attacks.
- Monitoring and Detection: Continuously monitor API traffic for signs of injection vulnerabilities and attacks.
- Virtual Patching: Consider virtual patching with custom rules to address emerging injection vulnerabilities in changing applications and APIs. This can be integrated into CI/CD workflows for ongoing security.
- Patch Management: Regularly patch web applications and APIs to address any discovered vulnerabilities based on their development lifecycle.
- Security Headers: Implement security headers, such as Content Security Policy (CSP) and Cross-Origin Resource Sharing (CORS) headers, to mitigate certain types of attacks, like cross-site scripting (XSS) and cross-site request forgery (CSRF).
- Monitoring and Logging: Continuously monitor API traffic and log events for suspicious activities. Set up alerts for anomalies and unusual patterns in API usage.
By following these best practices and keeping your APIs secure, you can significantly reduce the risk of API injection attacks and protect your application and data from potential threats.
How Wallarm Can Help
Wallarm provides automatic detection and blocking of Injection vulnerabilities, including XSS, RCE, SQLi / NoSQLi, CRFLi, LDAPi, SSTi, SSI, Email Injection, XXE and more. Our monitoring nodes actively watch API traffic for these threats, while our vulnerability assessments identify weaknesses in your APIs and endpoints that could be exploited. This proactive approach helps safeguard your business-critical applications and minimizes security risks.
Learn More
Come back next week as we wrap up this weekly series of posts on the new 2023 OWASP Top-10 API Security Risks list – or click here to see previous posts you might have missed.
In the meantime, here are some other resources which might help on your journey to end-to-end API security:
- Solution Brief: OWASP API Security Top-10 2023 Reference Guide (PDF)
- Blog Post: OWASP API Security Top-10 Risks for 2023 Released
- Blog Post: OWASP API Security Top-10 for 2023 Risk Ratings
- On-Demand Webinar: A Practitioner’s Guide to the New 2023 OWASP API Security Update
- On-Demand Webinar: A CISOs Guide to the New 2023 OWASP API Security Update
- Research Report: 2022 Year-End API ThreatStats™ Report (blog and linked full report)
Protect Your APIs from OWASP API Security Top-10 Threats
Wallarm End-to-End API Security solution provides comprehensive protection against the OWASP API Security Top-10 threats. And in 2023, we’ve made it even easier for you!
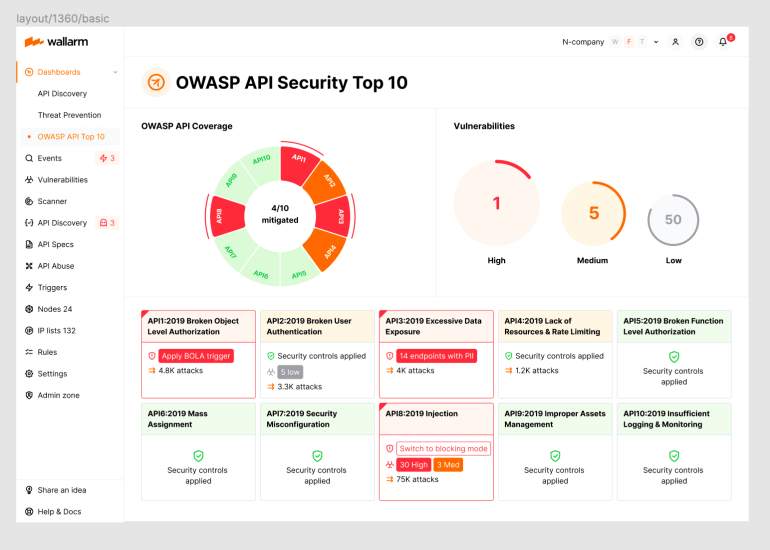
The Wallarm 2023 OWASP API Security Top-10 Dashboard provides you with complete visibility into the security state of your APIs, easy identification of your most critical security risks, and ability to immediately apply protective measures.

If you are interested in learning more about how we can help you protect your APIs, please schedule a demo with one of our security experts today!
The post 2023 OWASP Top-10 Series: Spotlight on Injection appeared first on Wallarm.
*** This is a Security Bloggers Network syndicated blog from Wallarm authored by wlrmblog. Read the original post at: https://lab.wallarm.com/spotlight-on-injection/
如有侵权请联系:admin#unsafe.sh
