More often than not, its our solemn duty on this site to keep you informed about the nature and tactics of dangerous, cunnning, and persistent cybercriminals.
This is not one of those days.
In fact, this is the oppposite of one of those days. This is about a passable spam email sent by a spammer who did the phishing equivalent of arriving at the airport three hours early for their flight, the day after it left.
It's about a malicious email that failed hard because, for all that it got right, it got the most important thing wrong, all but guaranteeing itself a inevitable, rapid, one way trip to the spam trap.
Still, there are valuable lessons to be learned in failure, and I can't think of a better way to compound the hapless spammer's misery than to turn it into a teachable moment that could improve security.
Let's start with what didn't go wrong.
What didn't go wrong
No matter how they're dressed up, scams almost always boil down to an urgent demand for money. The scammer's task is to make their breathless cash grab as plausible as possible, which they do by impersonating somebody or something you're expecting to hear from.
More often than not, that means impersonating familiar brands. Scammers love global brands like Microsoft, Google, Amazon and UPS because they are instantly recognisable, their logos and styling are easy to copy, and people are used to receiving emails from them.
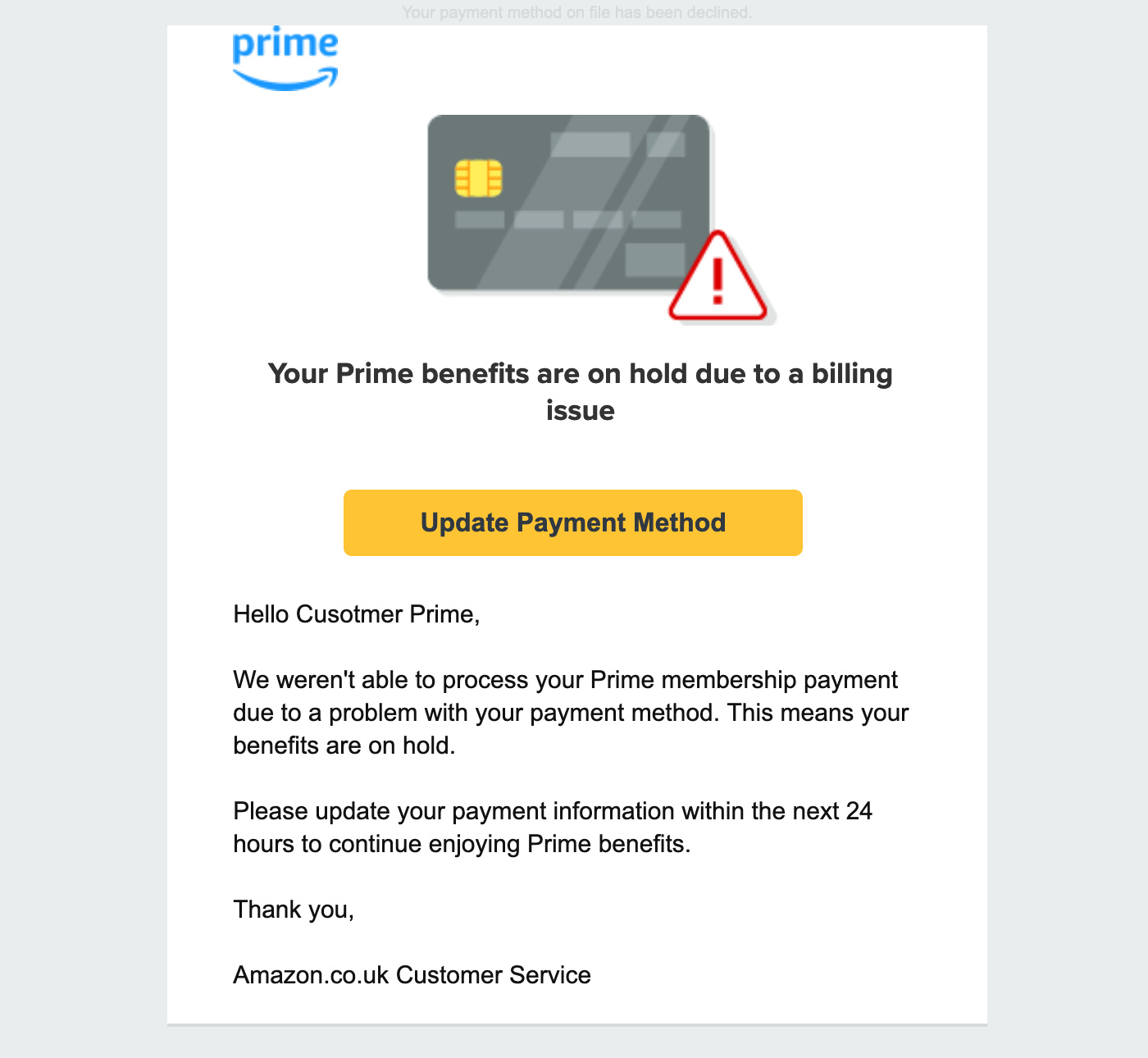
In this case, the urgent demand for money came wrapped in Amazon packaging, pretending that my Prime benefits were on hold because of a billing issue, with 24 hours to resolve by updating my payment method.

The premise is plausible, the colours look right, the logo does too, and the sign off, "Amazon.co.uk Customer Service", correctly placed me in the UK.
The scammer used a few other tricks to make the scam seem more believable too.
Unusually, the email's "From" address was an honest-to-goodness amazon.co.uk email, rather than a cute attempt to obscure a non-Amazon email. It's important to note that this doesn't mean that the scammer used Amazon infrastructure, or that the email touched Amazon in any way at all—you can put anything you like in an email From address. There's a reason scammers tend to go for cute tricks though, which we'll get to below.
Of course the email is just the bait, the actual theft of users' payment details has to happen on a website somewhere, and scammers don't often spin up their own infrastructure. For that, they more commonly hijack somebody else's. The Update Payment Method link in this email links to an admin page on a site belonging to a leading constructor of altar furniture in Vietnam.
Because its address might look weird to an email scanning engine, or an eagle-eyed recipient, the furniture site is reached via an open redirect on Russia's answer to Facebook, VKontakte, which is a large and well established website that won't ring any alarm bells.
An open redirect is a URL on a site that can be modified to redirect to any other page on the web. Despite being widely recognised as an undesirable security flaw, open redirects are common on search engines and social media sites, which use them to track the links you click on, much to the delight of scammers.
Aside from the fact that it starts "Dear Cusotmer Prime," the email is chock full of things that make it believable. With all those ingredients in place you might think this email was destined for success, but when it arrived it was instantly and ignominiously dumped into the spam folder.
What didn't go right
You remember that amazon.co.uk address the scammer used? That's what didn't go right. Email in its pure form allows a sender to put anything they like into the From address, but with a bit of work companies can ensure there are consequences if scammers use their domains like this.
Amazon has implemented Domain-based Message Authentication, Reporting and Conformance (DMARC). As soon as the scam mail arrived, our infrastructure checked to see if the email had been digitally signed by Amazon (it hadn't) and if the scammer's server was allowed to send amazon.co.uk emails (it wasn't). With a negative against those checks it didn't matter how convincing the rest of the email was.
Now, there is a chance that the scammer is playing 3D chess here and did this deliberately. Administering email systems and policies can be difficult, so many organisations—likely smaller ones—haven't implemented DMARC, or have switched it off in a heavy-handed solution to an email authentication problem.
So perhaps the scammer has done some back-of-the-envelope maths and calculated that the advantages of using a "real" email address outweigh the considerable disadvantages. Maybe. But a scammer who can do that can probably use a spell checker too, so I prefer to put my faith in Hanlon's Razor—"Never attribute to malice that which is adequately explained by stupidity".
VKontakte has the last laugh
When I checked the URL that redirected via VKontakte, I noticed something odd that suggests it was already aware of the offending URL. The redirect should have returned a 301 or 302 status code, indicating that the response was a redirection, but it didn't, it returned 418, a status code that indicates that the server is a tea pot.

From the official Hyper Text Coffee Pot Control Protocol (HTCPCP/1.0), published on April Fool's Day, 1998:
Any attempt to brew coffee with a teapot should result in the error code "418 I'm a teapot". The resulting entity body MAY be short and stout.
Kudos.
The most important lesson
The SMTP protocol that email relies upon is a 50 year old relic of an age when the internet was tiny and trusting. Its intrinsic lack of security has been bolstered over the years by a series of technologies that can ensure emails are encrypted, and From addresses can be trusted. However, because they aren't part of the SMTP specification they are optional, and businesses have to decide to embrace them.
The most important lesson this scam has for businesses, no matter how small, is to set up DMARC.
Whether the scammer was dumber than dirt or playing 3D chess, their email was always going to fail in the face of anti-spoofing checks.
Malwarebytes EDR and MDR removes all remnants of ransomware and prevents you from getting reinfected. Want to learn more about how we can help protect your business? Get a free trial below.