
2023-10-3 02:55:34 Author: securityboulevard.com(查看原文) 阅读量:12 收藏
By Ofri Ouzan & Yotam Perkal, Rezilion Security Research
On September 27th, 2023 Google released an update including 10 security fixes. Notably, one of these fixes, identified as CVE-2023-5217, was highlighted for having an existing exploit in the wild. On October 2nd, 2023, CISA added this vulnerability to their KEV Catalog, signifying that it is being actively exploited in the wild. While the likelihood of exploitation isn’t clear yet, this classification makes the vulnerability an urgent concern that requires immediate attention.
CVE-2023-5217 is classified as a heap buffer overflow vulnerability with a high CVSS score of 8.8. This particular vulnerability allows remote attackers to execute heap corruption through the use of a crafted HTML page. Similarly to CVE-2023-4863 Initially, this vulnerability was associated with Chrome. However, further investigation revealed that it resides in the libvpx library of the WebM VP8/VP9 Codec SDK.

If this sounds familiar, you’re absolutely right!
It bears a striking resemblance to our recent research on CVE-2023-4863 released less than two weeks ago. These two vulnerabilities share numerous similarities:
- Both CVEs are heap overflow vulnerabilities
- Both share the same CVSS score – 8.8.
- Both were disclosed by Google and were initially believed to affect only Chrome,
- Both later had their CPE values updated to reflect their association with webmproject libraries that are dependencies of many other software products (libwebp & libvpx).,
- Both involve attackers using crafted HTML pages as their attack vector.
- Furthermore, they both have existing exploits in the wild and are codec libraries serving the same purpose – encoding and decoding various formats.
Rezilion analysis reveals that there are several common Linux applications that contain or use the vulnerable libvpx package as a dependency. Examples include: gstreamer1-plugins-good, gstreamer-plugins-bad-free, ffmpeg-libs, libgd3, Microsoft vcpkg, Telegram and Telegram Desktop, FFmpeg, SmartTubeLegacy, Openai Retro, Google ExoPlayer, Natron.
While libvpx seems to be less widespread than libwebp, Rezilion has also identified the vulnerable library in several container images’ latest versions, collectively downloaded and deployed over 100 million times such as elixir, erlang, silverpeas, gazebo, ros, and nuxeo.

The Vulnerability
This is a heap buffer overflow vulnerability in the libvpx package of WebM VP8/VP9 Codec SDK. Heap is a data structure that stores data of a running program, the data is stored in a variable amount that won’t be known until the program is running.
Heap buffer overflow occurs when data is written beyond the allocated boundaries of a program’s memory heap, potentially leading to a denial of service or remote code execution
The libvpx package of WebM VP8/VP9 Codec SDK is a free software video codec library from Google and the Alliance for Open Media (AOMedia). It serves as the reference software implementation for the VP8 and VP9 video coding formats.
Actual Attack Surface
While the vulnerability initially seems to target Chromium-based applications, it then realized to target every application relying on the ubiquitous libvpx package of WebM VP8/VP9 Codec SDK. There are multiple applications, software, libraries, and containers relying on this package making the attack surface wider than just Google Chrome.
Organizations with SBOM (Software Bill of Materials) solutions in their environment are advised to query the SBOM for any package using a vulnerable version of libvpx as a dependency. It is especially important to make sure that the system libvpx library is patched as several applications such as Chromium for example, are built against the system libvpx library.
Affected Systems Breakdown:
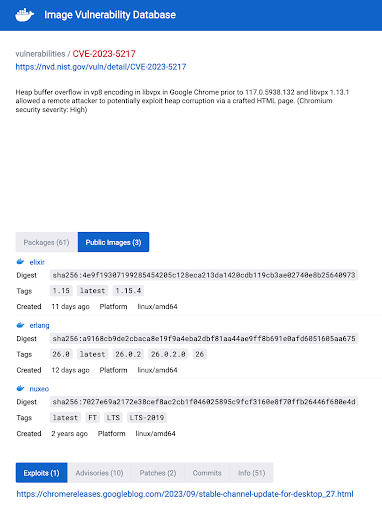
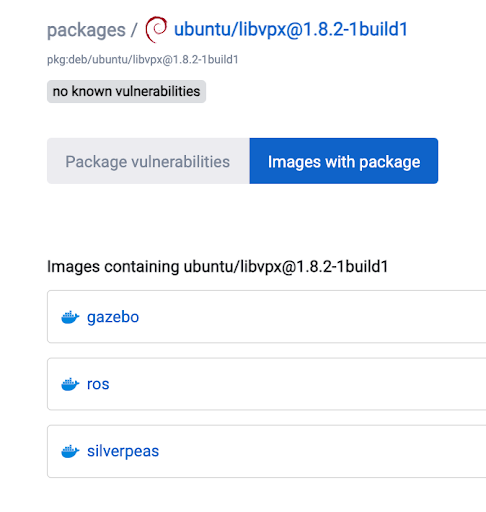
A list of packages that depend on the “libvpx” package according to Arch Linux:
avidemux-cli, ffmpeg (requires libvpx.so), ffmpeg4.4 (requires libvpx.so), gst-plugins-good, handbrake, handbrake-cli, lib32-libvpx, mencoder, mplayer, qt5-webengine, qt6-webengine, qt6-webengine, shotcut, thunderbird, toxcore, virtualbox, xpra, av1an (optional), baresip (optional), vlc (optional), avidemux (make), baresip (make), gstreamer (make), handbrake (make), mplayer (make), ovenmediaengine (make), virtualbox (make), vlc (make)
The vulnerability was fixed in libvpx version 1.13.1 and in chrome version 117.0.5938.132.
CVE-2023-44488
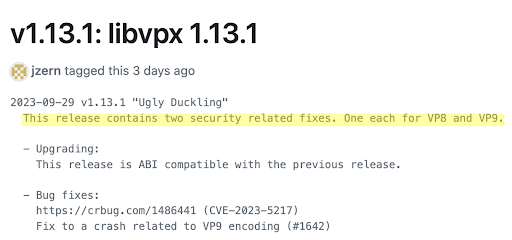
We’d also like to draw attention to CVE-2023-44488, another libvpx vulnerability that was listed in the NVD on September 30, 2023. As can be seen in the below image, version 1.13.1 of libvpx contains two separate security-related fixes. The first is CVE-2023-5217 affecting VP8, while the second is CVE-2023-44488 affecting VP.
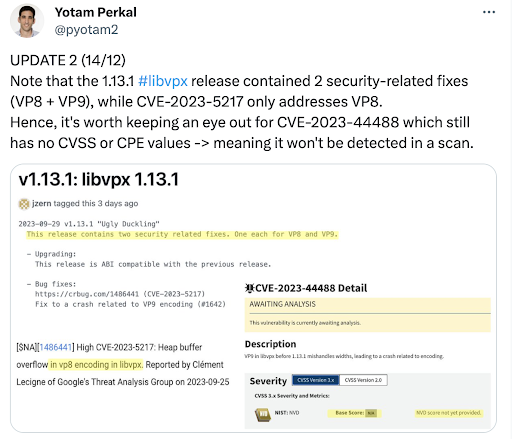
As explained in the below tweet, while its severity is yet to be known, since CVE-2023-44488 has not yet received a CVSS score or a CPE identifier, vulnerability scanners will currently not be able to identify it.
Recommendations
Since Google revealed there is an existing exploit in the wild for CVE-2023-5217, it is imperative to swiftly apply the provided patches to your systems. These patches have been specifically designed to address this critical vulnerability and should be deployed without delay.
Since libvpx is a dependency of multiple software products, it is advised to query your SBOM solution or asset inventory system for specific occurrences of libvpx in all of its vulnerable variations.
For software, applications, or packages that dynamically incorporate the libvpx package into their code, updating the system libvpx library to the latest version is crucial. After the update, it is advisable to restart these applications to ensure the changes take effect.
While safeguarding your systems is paramount, it’s essential to balance security with operational stability. When applying updates, be mindful of potential operational risks that could disrupt normal functioning. Plan and execute the update process carefully to minimize any adverse effects.
__________________________________
GET HELP WITH CVE-2023-5217
To help organizations work around potential blindspots in their ability to detect all instances of CVE-2023-5217 within their environment, Rezilion is now offering a free risk assessment program.
Through this opportunity, organizations can access Rezilion’s inherent Dynamic SBOM capability to simply query the dependency tree of any environment in which Rezilion is deployed to instantly identify instances of software components using vulnerable libvpx versions as a dependency.
For example, in this screenshot from the Rezilion platform, on the right-hand side, you can see examples of various components that are dependent on vulnerable versions of libvpx, including whether these components are actually in use (loaded to memory) or not:
No code, no agents, and no formal commitment is required to participate in the free risk assessment. Benefits of the program include:
- Pinpoint ALL instances of CVE-2023-5217 in your software and dependencies – fast – with instant search capabilities
- Know if instances are exploitable in your unique environments – not just exploitable in the wild – with the platform’s patented Runtime Analysis capabilities
- Get smart guidance on not just what and where to patch, but which version patch to use to avoid breaking your build
- Share a complete software bill of materials (SBOM) of your dynamic software environment – and its risks – to assure customers that you are in compliance with security policies and requirements
To learn more about the free risk assessment program, visit https://info.rezilion.com/lp/cve-2023-5217-risk-assessment.
The post The CVE-2023-5217 Deja Vu – Another Actively Exploited Chrome Vulnerability Affecting a WebM Project Library (libvpx) appeared first on Rezilion.
*** This is a Security Bloggers Network syndicated blog from Rezilion authored by rezilion. Read the original post at: https://www.rezilion.com/blog/the-cve-2023-5217-deja-vu-another-actively-exploited-chrome-vulnerability-affecting-a-webm-project-library-libvpx/
如有侵权请联系:admin#unsafe.sh
