
2023-9-28 11:36:8 Author: www.tenable.com(查看原文) 阅读量:18 收藏

Frequently asked questions relating to vulnerabilities in Apple, Google and the open source libwebp library.
Background
The Tenable Security Response Team has put together this blog to answer frequently asked questions (FAQ) to help provide clarity around recently disclosed vulnerabilities including CVE-2023-41064, CVE-2023-4863 and CVE-2023-5129 in an open source library called libwebp.
FAQ
What do these vulnerabilities have to do with Apple products?
On September 7, researchers at Citizen Lab published a blog post detailing their discovery of an iPhone zero-click, zero-day exploit chain in Apple iOS used to deploy a spyware known as Pegasus.
NEW: Last week, we @citizenlab captured a "zero-click" exploit used to install Pegasus on the latest version of iOS, 16.6. The exploit installed Pegasus without any interaction from the victim, and was virtually invisible https://t.co/MxPrAThwa1
— Bill Marczak (@billmarczak) September 7, 2023
What are the vulnerabilities that Apple patched?
Apple patched two vulnerabilities across several of its operating systems, including iOS and iPadOS [1, 2], watchOS and several versions of macOS [1, 2, 3]:
What is this exploit chain called and how severe is it?
The Citizen Lab dubbed this exploit chain BLASTPASS and it is considered a critical flaw because exploitation requires no interaction from a potential victim, making it a zero-click vulnerability.
In-the-wild exploitation involved attachments using Apple PassKit that contained malicious images delivered to the victim via iMessage.
What does this have to do with Google Chrome and other web browsers?
As part of the disclosure of these vulnerabilities, both Apple’s Security Engineering and Architecture (SEAR) team and The Citizen Lab notified Google about their findings on September 6 due to the potential for exploitation outside of Apple’s ecosystem.
Did Google also patch this vulnerability?
Yes, on September 11, Google published a patch for Google Chrome. However, they assigned a separate CVE for this vulnerability:
| CVE | Description |
|---|---|
| CVE-2023-4863 | Heap Buffer Overflow Vulnerability in WebP |
What is ImageIO or Image I/O?
ImageIO or Image I/O is a
frameworkthat allows programs to read and write image file formats, including
WebP. It is a part of Apple operating systems from iOS and iPadOS to macOS, and watchOS.
What is WebP or libwebp?
WebP is an
open-source image file format developed by Google, while libwebp is a library that was developed to allow programs to support the WebP file format. It is part of Google’s Chromium project, the open source web browser that Google Chrome and other browsers are based on.
How are CVE-2023-4863 and CVE-2023-41064 connected?
Based on the timeline of when CVE-2023-41064 was disclosed (September 7) and both Apple and The Citizen Lab’s proactive disclosure to Google on September 6, coupled with the fact that both issues are buffer overflow vulnerabilities in image processing frameworks/libraries (ImageIO, WebP), it would appear that both vulnerabilities are related. This is also corroborated by other independent research from
Matt Suicheand
Ben Hawkes.
We suspect that this is the same bug that Citizen Lab reported to Apple after detecting an NSO Group exploit chain called "BLASTPASS" that was used to attack on a Washington DC-based civil society organization.
— Ben Hawkes (@benhawkes) September 21, 2023
If this affects the libwebp library, does that mean other programs are also vulnerable?
Yes, applications or programs and operating systems that use libwebp as a dependency are also considered vulnerable to these flaws.
What does CVE-2023-5129 have to do with this?
On September 25, Google assigned a new CVE, CVE-2023-5129, to expand the impact of CVE-2023-4863, to cover libwebp more broadly versus specifically impacting Google Chrome.
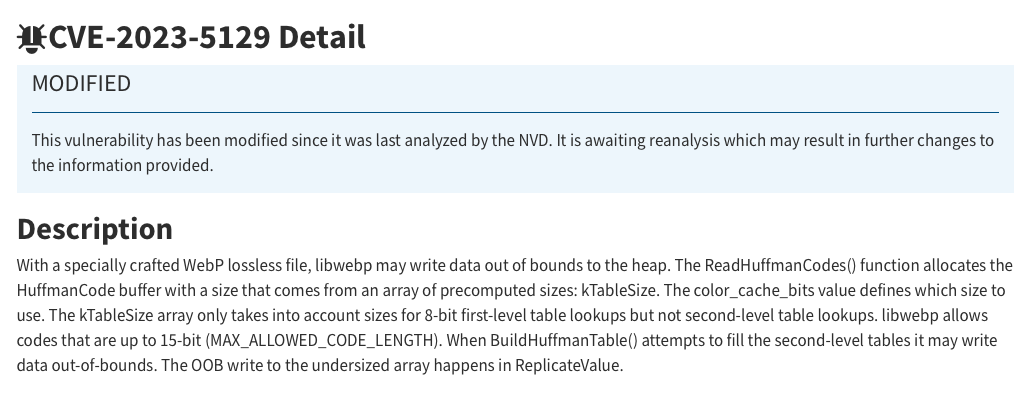
Google also assigned a maximum CVSSv3 score of 10.0 for this CVE.
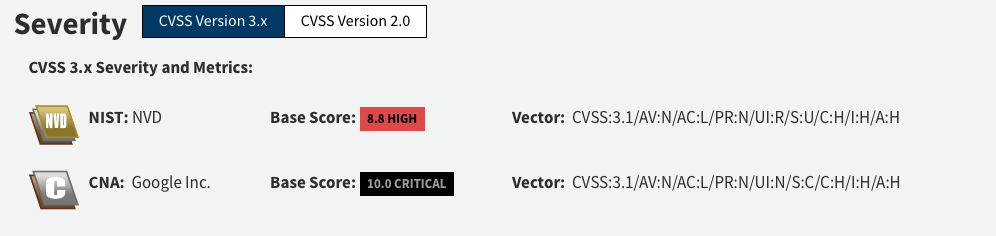
Did Google reject CVE-2023-5129 after assigning it?
Yes, on September 27, Google rejected CVE-2023-5129, citing it as a duplicate of CVE-2023-4863 and updated the description for CVE-2023-4863 to include the impact to libwebp itself while clarifying the critical impact to Chromium.
Google did not increase the CVSSv3 score for CVE-2023-4863, opting instead to add a note about it being of “Critical” per Chromium security’s severity scale.
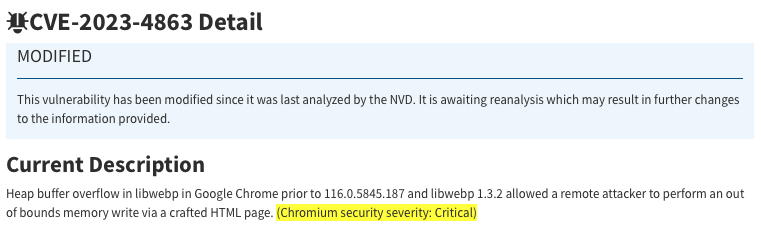
Why was CVE-2023-5129 rejected?
Google has not confirmed why it rejected the vulnerability. However, based on the fact that several vendors have already adopted CVE-2023-4863 as the CVE identifier when patching libwebp, it likely did not make sense to assign a new CVE for this versus expanding the impact of the original CVE.
How many applications or programs are affected by CVE-2023-4863?
Because libwebp is a library that is included in applications and programs or packages as a dependency, we do not know the full depth and breadth of how widespread it is. We know that several browsers, including Firefox and Thunderbirdas well as browsers based on Chromium including Microsoft Edge, Opera and Brave are affected by this vulnerability. Additionally, the library is included in the Electron open source framework that is used by a large number of applications including 1Password, Slack and more.
A list of affected Electron applications is being tracked by Michael Taggart here.
Timeline
The following is a timeline related to all three vulnerabilities highlighted in this FAQ. It was last updated on September 27.
| Date | Details |
|---|---|
| September 6, 2023 | Apple Security Engineering and Architecture (SEAR) and The Citizen Lab notifies Google about a critical vulnerability in the WebP library (libwebp) |
| September 7, 2023 | The Citizen Lab publishes blog post detailing discovery of zero-click, zero-day exploit chain against iPhones dubbed BLASTPASS |
| Apple publishes patches for several operating systems including iOS and iPadOS, watchOS and macOS to address the flaws disclosed by The Citizen Lab | |
| Apple assigns CVE-2023-41064 (ImageIO), CVE-2023-41061 (Wallet) for the exploit chain | |
| September 11, 2023 | Google publishes a Stable Channel Update for Desktop versions of Chrome on Mac, Linux and Windows to address the vulnerability disclosed on September 6. |
| Google assigns CVE-2023-4863 to address the impact of this vulnerability in WebP in Chromium | |
| Apple publishes a patch for previous versions of iOS and iPadOS as well as macOS Big Sur and Monterey | |
| September 25, 2023 | Google assigns CVE-2023-5129 to expand impact of this vulnerability to libwebp |
| September 27, 2023 | Google rejects CVE-2023-5129, marking it as a duplicate of CVE-2023-4863 |
| Google modifies the entry for CVE-2023-4863 to highlight impact to both Google Chrome and libwebp |
Identifying affected systems
A list of Tenable plugins to identify affected systems can be located on the individual CVE page for each of the CVEs mentioned here:
These links will display all available plugins for these vulnerabilities, including upcoming plugins in our Plugins Pipeline.
Get more information
- BLASTPASS: NSO Group iPhone Zero-Click, Zero-Day Exploit Captured in the Wild
- About the security content of iOS 16.6.1 and iPadOS 16.6.1
- Google Chrome: Stable Channel Update for Desktop
- Google quietly corrects previously submitted disclosure for critical webp 0-day
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable One, the Exposure Management Platform for the modern attack surface.

Satnam Narang
Satnam joined Tenable in 2018. He has over 15 years experience in the industry (M86 Security and Symantec). He contributed to the Anti-Phishing Working Group, helped develop a Social Networking Guide for the National Cyber Security Alliance, uncovered a huge spam botnet on Twitter and was the first to report on spam bots on Tinder. He's appeared on NBC Nightly News, Entertainment Tonight, Bloomberg West, and the Why Oh Why podcast.
Interests outside of work: Satnam writes poetry and makes hip-hop music. He enjoys live music, spending time with his three nieces, football and basketball, Bollywood movies and music and Grogu (Baby Yoda).
Related Articles
- Exposure Management
- Vulnerability Management
Cybersecurity News You Can Use
Enter your email and never miss timely alerts and security guidance from the experts at Tenable.
Tenable Vulnerability Management
Formerly Tenable.io
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy.
Your Tenable Vulnerability Management trial also includes Tenable Lumin, Tenable Web App Scanning and Tenable Cloud Security.
Tenable Vulnerability Management
Formerly Tenable.io
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy. Purchase your annual subscription today.
65 assets
Choose Your Subscription Option:
Thank You
Thank you for your interest in Tenable.io. A representative will be in touch soon.
Try Tenable Nessus Professional Free
FREE FOR 7 DAYS
Tenable Nessus is the most comprehensive vulnerability scanner on the market today.
NEW - Tenable Nessus Expert
Now Available
Nessus Expert adds even more features, including external attack surface scanning, and the ability to add domains and scan cloud infrastructure. Click here to Try Nessus Expert.
Fill out the form below to continue with a Nessus Pro Trial.
Buy Tenable Nessus Professional
Tenable Nessus is the most comprehensive vulnerability scanner on the market today. Tenable Nessus Professional will help automate the vulnerability scanning process, save time in your compliance cycles and allow you to engage your IT team.
Buy a multi-year license and save. Add Advanced Support for access to phone, community and chat support 24 hours a day, 365 days a year.
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy.
Your Tenable Vulnerability Management trial also includes Tenable Lumin, Tenable Web App Scanning and Tenable Cloud Security.
BUY
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy. Purchase your annual subscription today.
65 assets
Choose Your Subscription Option:
Thank You
Thank you for your interest in Tenable.io. A representative will be in touch soon.
Try Tenable Web App Scanning
Formerly Tenable.io Web Application Scanning
Enjoy full access to our latest web application scanning offering designed for modern applications as part of the Tenable One Exposure Management platform. Safely scan your entire online portfolio for vulnerabilities with a high degree of accuracy without heavy manual effort or disruption to critical web applications. Sign up now.
Your Tenable Web App Scanning trial also includes Tenable Vulnerability Management, Tenable Lumin and Tenable Cloud Security.
Buy Tenable Web App Scanning
Formerly Tenable.io Web Application Scanning
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy. Purchase your annual subscription today.
Try Tenable Lumin
Visualize and explore your exposure management, track risk reduction over time and benchmark against your peers with Tenable Lumin.
Your Tenable Lumin trial also includes Tenable Vulnerability Management, Tenable Web App Scanning and Tenable Cloud Security.
Buy Tenable Lumin
Contact a Sales Representative to see how Tenable Lumin can help you gain insight across your entire organization and manage cyber risk.
Thank You
Thank you for your interest in Tenable Lumin. A representative will be in touch soon.
Request a demo of Tenable Security Center
Formerly Tenable.sc
Please fill out this form with your contact information.
A sales representative will contact you shortly to schedule a demo.
* Field is required
Request a demo of Tenable OT Security
Formerly Tenable.ot
Get the Operational Technology Security You Need.
Reduce the Risk You Don’t.
Request a demo of Tenable Identity Exposure
Formerly Tenable.ad
Continuously detect and respond to Active Directory attacks. No agents. No privileges.
On-prem and in the cloud.
Try Tenable Cloud Security
Formerly Tenable.cs
Enjoy full access to detect and fix cloud infrastructure misconfigurations and view runtime vulnerabilities. Sign up for your free trial now. To learn more about the trial process click here.
Your Tenable Cloud Security trial also includes Tenable Vulnerability Management, Tenable Lumin and Tenable Web App Scanning.
Contact a Sales Rep to Buy Tenable Cloud Security
Contact a Sales Representative to learn more about Tenable Cloud Security and see how easy it is to onboard your cloud accounts and get visibility into both cloud misconfigurations and vulnerabilities within minutes.
Thank You
Thank you for your interest in Tenable.cs. A representative will be in touch soon.
See
Tenable One
In Action
Exposure management for the modern attack surface.
See Tenable Attack Surface Management In Action
Formerly Tenable.asm
Know the exposure of every asset on any platform.
Thank You
Thank you for your interest in Tenable Attack Surface Management. A representative will be in touch soon.
Try Tenable Nessus Expert Free
FREE FOR 7 DAYS
Built for the modern attack surface, Nessus Expert enables you to see more and protect your organization from vulnerabilities from IT to the cloud.
Already have Tenable Nessus Professional?
Upgrade to Nessus Expert free for 7 days.
Buy Tenable Nessus Expert
Built for the modern attack surface, Nessus Expert enables you to see more and protect your organization from vulnerabilities from IT to the cloud.
Try Nessus Expert Free
FREE FOR 7 DAYS
Built for the modern attack surface, Nessus Expert enables you to see more and protect your organization from vulnerabilities from IT to the cloud.
Already have Nessus Professional?
Upgrade to Nessus Expert free for 7 days.
Buy Tenable Nessus Expert
Built for the modern attack surface, Nessus Expert enables you to see more and protect your organization from vulnerabilities from IT to the cloud.
如有侵权请联系:admin#unsafe.sh