minute read

Global threat statistics
In the first half of 2023, the percentage of ICS computers on which malicious objects were blocked decreased from H2 2022 by just 0.3 pp to 34%.
That said, he percentage of attacked ICS computers dropped in Q1 2023, but then rose again in Q2 2023, reaching highest quarterly figure since 2022 – 26.8%.
Geography
The percentage of ICS computers on which malicious objects were blocked varied across countries from 53.3% in Ethiopia to 7.4% in Luxembourg.
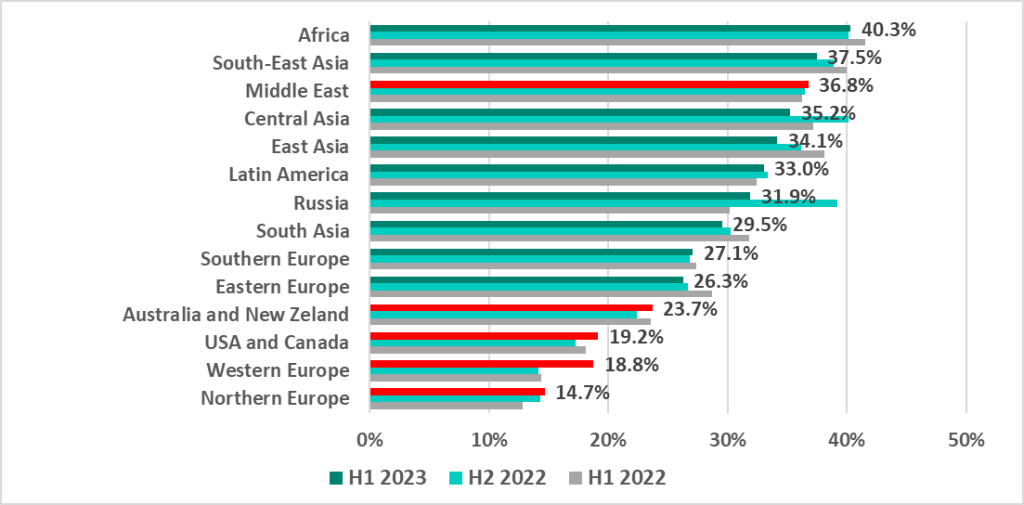
The percentage of computers on which malicious activity was prevented varied across regions from 40.3% in Africa to 14.7% in Northern Europe.
Australia and New Zealand, the United States and Canada, Western Europe, and Northern Europe historically have had the lowest percentages of ICS computers on which malicious objects are blocked.
In H1 2023, however, those were the very regions where the percentages of attacked ICS computers increased by the most percentage points.
H1 2023 changes in the percentages of ICS computers on which malicious objects were blocked, by region
Africa and the Asian regions where the percentage of ICS computers on which malicious objects are blocked historically has been high, showed a downward trend.
Individual industries
In H1 2023, the percentage of ICS computers on which malicious objects were blocked increased in engineering and ICS integration (by 2 pp), manufacture (by 1.9 pp) and energy (by 1.5 pp).
Building automation is still the leader among the industries under review.
Categories of malicious objects
Only one of the categories grew in H1 2023: denylisted internet resources. The percentage of ICS computers on which threats in this category are blocked has grown for the second half-year in a row.
Percentage of ICS* computers on which the activity of malicious objects of various categories was prevented
The percentages of ICS computers on which Spyware, Malicious documents, Malicious miners in the form of Windows executables, Ransomware were blocked had been declining since mid-2022:
Percentage of ICS computers on which the activity of malicious objects of various categories was prevented
In H1 2023, the percentage of ICS computers on which these categories of threats were blocked, dropped in virtually every region.
Main threat sources
The internet, email clients and removable devices remained the key sources of threats to computers in the operational technology infrastructure of organizations.
The full report has been published on the Kaspersky ICS CERT website.