The Good | International Operation Takes Down Multi-Layered Qakbot InfrastructureQakbot, a long-es 2023-9-1 21:0:23 Author: www.sentinelone.com(查看原文) 阅读量:17 收藏
The Good | International Operation Takes Down Multi-Layered Qakbot Infrastructure
Qakbot, a long-established malware and botnet infrastructure in the cyber threat ecosystem, was toppled this week after a successful global operation led by US authorities.
Dubbed “Operation Duck Hunt”, the joint operation involved redirecting the botnet’s communication to FBI-controlled servers. The FBI seized the botnet’s critical infrastructure along with approximately $8.6 million in cryptocurrency and were able to uninstall the malware from some 700,000 infected devices – 200,000 of which were situated in the US.
In its first form circa 2008, Qakbot (aka Qbot, Quackbot, Pinkslipbot, and TA750) emerged as a banking trojan aimed at pilfering banking credentials, website cookies, and credit card data for financial fraud. Over time, the trojan evolved into a C2-based malware delivery service for other threat actors, providing initial network access for ransomware attacks, data theft, and a diverse range of malicious cyber activities. Qakbot has been observed partnering with various ransomware operators including BlackCat, Black Basta, Conti, REvil, and RansomEXX.
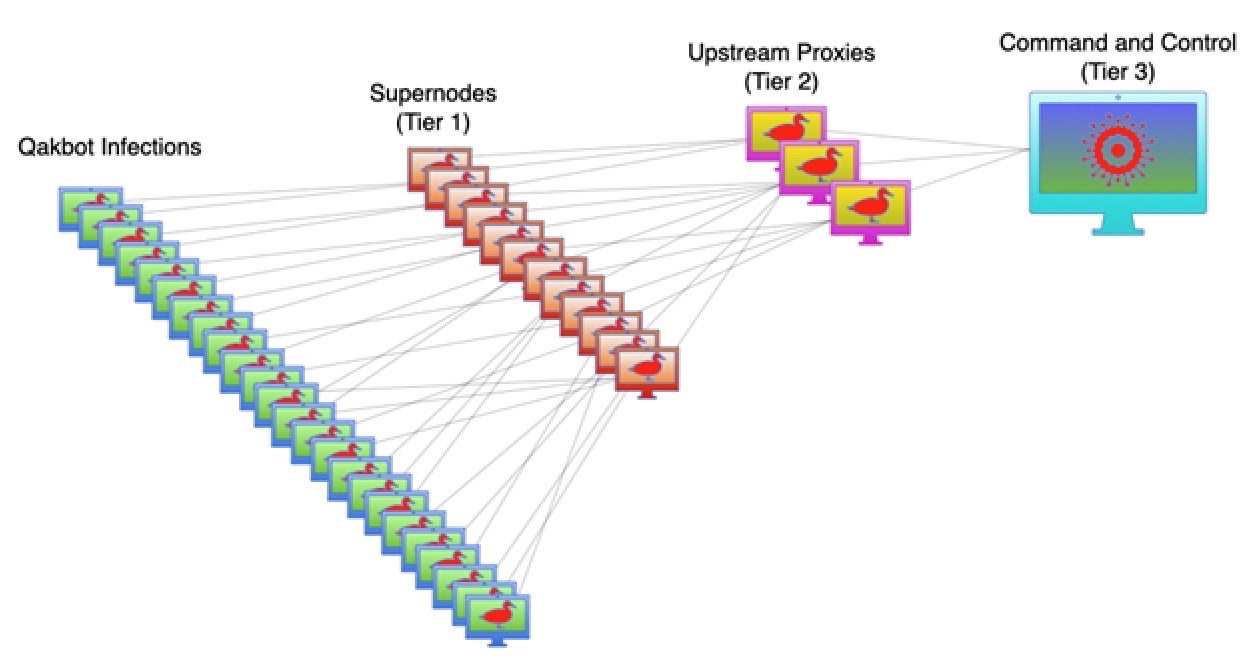
Qakbot victims span organizations across several sectors including governments and healthcare providers. Propagation of the malware relies on phishing campaigns, incorporating tactics like reply-chain email attacks, where cybercriminals hijack email threads, respond with their own messages, and embed malicious attachments that install the Qakbot malware to the victim’s device.
Major takedowns like this one do much to shake up the cybercrime ecosystem, even though it is expected that threat groups will evolve and regroup. However, the success of Operation Duck Hunt underscores how effective global law enforcement collaboration can be in the ongoing fight against cyber threats.
The Bad | Ransomware Operators Target Critical Citrix NetScaler Vulnerability
Unpatched, Internet-facing Citrix NetScaler systems are under further attack this week by unconfirmed threat actors in what appears to be an ongoing ransomware campaign. The attack chain involves exploiting a critical code injection vulnerability, tracked as CVE-2023-3519 (CVSS score: 9.8), which affects NetScaler ADC and Gateway servers and could enable unauthenticated remote code execution (RCE).
So far, the vulnerability has been used to perform a domain-wide attack where payloads were injected into legitimate executables such as the Windows Update Agent (wuauclt.exe) and the Windows Management Instrumentation Provider Service (wmiprvse.exe). Citrix’s security bulletin recommends customers to install the patched versions of NetScaler ADC and NetScaler Gateway immediately to minimize potential threats.
Alongside the exploit, the attackers have also employed tactics such as distributing obfuscated PowerShell scripts, PHP web shells, and leveraging a malware staging service called BlueVPS. The pattern of these attacks closely resembles a campaign reported in early August, in which around 2,000 Citrix NetScaler systems were backdoored.
According to cybersecurity researchers, the attacks from this week and earlier last month may be tied to the FIN8 hacking group, which specializes in ransomware campaigns targeting retail, food services, and hospitality industries.
This surge in ransomware attacks coincides with the trend of cybercriminals exploiting low-hanging security vulnerabilities found in popular software. Ransomware groups such as FIN8 also continue to use customized and/or updated malware strains to refine their attack methodologies and encrypt stolen data faster, highlighting the need for organizations to focus their cybersecurity strategy on real-time detection and response capabilities.
The Ugly | China-Backed Actors Attack Local Government Agencies Using Barracuda Flaw
Chinese threat actors are currently suspected of launching a chain of targeted attacks on local government and government-affiliated organizations globally through a zero-day vulnerability (CVE-2023-2868, CVSS score: 9.8) in the Barracuda Email Security Gateway (ESG).
Security researchers this week revealed that a significant portion of the breached appliances belonged to North American-based agencies from all levels of government including state, provincial, county, tribal, and municipal. While local government targeting makes up about 7% of all affected organizations, this figure rises to nearly 17% within the US alone.

The primary motivation behind the attacks was espionage. The threat actor, tracked as UNC4841, engaged in targeted data exfiltration from systems linked to prominent users in government and high-tech sectors.
The vulnerabilities in the Barracuda ESG were first disclosed on May 20, with the company issuing patches and remote fixes. However, it was later discovered that the zero-day had been exploited since at least October 2022, employing new malware variants like SeaSpy, Saltwater, and SeaSide to gain unauthorized access.
While Barracuda has not found evidence of new ESG appliances being compromised after patching, the law enforcement authorities warn that the patches are insufficient, and the vulnerability continues to be exploited. Barracuda customers are advised to isolate and replace any compromised appliances quickly, check their networks for indications of potential breaches, and rotate all enterprise-privileged credentials to minimize the risk of attacks.
如有侵权请联系:admin#unsafe.sh