The Growing Threat Landscape Modern threat actors have proven their adaptability year after y 2023-8-9 20:53:51 Author: www.forcepoint.com(查看原文) 阅读量:24 收藏
The Growing Threat Landscape
Modern threat actors have proven their adaptability year after year, by exploiting unsuspecting users through various novel vectors. Image-based cyber-attacks represent one such vector that capitalizes on the abundant nature of visual content. Whether through steganography, image spoofing, or even malware-laden images, cybercriminals are finding innovative ways to exploit the trust placed in images, endangering personal privacy, organizational security, and data integrity.
Join specialist Humphrey Browning on August 16th for his “Preventing Image-Based Cyber Threats” webinar where he's discuss real-life use cases and do a live demo.
Recent High Profiled Image-Based Cyber Attacks
Russian hackers used BMW car ad to infiltrate Ukrainian Embassy.

This attack consisted of two key stages. The first was a Word document that contained an ad for an innocent Car Flyer; A BMW that had been sent out firstly by a Polish Diplomat that was intercepted by APT29 (Cozy Bear). Cozy Bear copied this Ad (and laced it with a link that when followed, an ISO was dropped to the disk. In case you missed it, check out this recent X-Labs analysis to see how this attack cold have been stopped.
1 year on from the James Webb Telescope Image attack
On August 31, 2023, Securonix Threat Labs published a threat research piece pulling back the curtain of a new malware attack. Involving a phishing email, a deceiving Microsoft Office attachment and the first full-colour image taken from the James Webb Telescope, SMACS 0723. The attack titled: GO#WEBBFUSCATOR is a complex, multi-stage malware attack designed to infiltrate your computer.
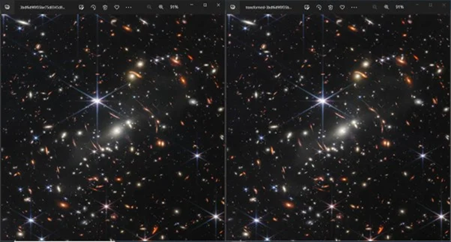
Can you tell the difference between the image on the left vs the image on the right? Hint: One of them contains a malicious malware attack.
No?
Neither can your antivirus or sanding boxing solutions. Checlkout this X-Labs post to learn more about this attack and how it could have been stopped.
Exploring Image-Based Attack Vectors
Steganography: Stealthily hiding malicious content within image files, steganography poses a serious threat. Leveraging images to secretly transmit sensitive information or launch attacks.
Image Spoofing's: Image spoofing involves manipulating images to deceive viewers. Image spoofing has been used for fraud, identity theft, and other malicious activities.
Malware-Laden Images: Where cybercriminals embed malware within image files to infect systems.
Defending Against Image-Based Threats
Educational Empowerment: Awareness is the first line of defense but cannot be relied upon. If we take the James Webb Telescope Image as an example, how do we ask our people to spot malware hidden in images, when even detection-based defenses can’t?
Prevention over Detection: As attackers employ increasingly sophisticated techniques, we must start to move away from the traditional defenses on which we have all relied upon for years. We simply cannot keep up with the ever-changing threat landscape by using the same rudimental techniques.
We must employ prevention-based technologies to protect our data.
In a world where digital content is integral to communication and expression, the rise of image-based cyber-attacks highlights the need for a comprehensive approach to cybersecurity. Our upcoming webinar, “Preventing Image-Based Cyber Threats” will shed light on the hidden dangers posed by image-based attacks and emphasized the importance of proactive defense measures.
By understanding the various attack vectors, staying informed about emerging threats, and implementing best practices, individuals and organizations can fortify their digital presence against constant evolving risks. As technology continues to advance, it is imperative that vigilance and preparedness evolve in tandem to keep our data and systems safe.
Join Humphrey Browning for the August 16 webinar “Preventing Image-Based Cyber Threats” as we dive into the hidden dangers within images and the potential risks they pose to individuals and organisations. This webinar will empower you with the knowledge and tools to recognise, prevent and mitigate image-based cyber threats effectively. He'll look at the examples I shared here, plus much more. See you then!
如有侵权请联系:admin#unsafe.sh