TETRA (Terrestrial Trunked Radio) is a digital voice and text radio communications protocol often used by authorities and industry in European and many countries other than the USA. A major advantage to a digital communications protocol like TETRA is it's ability to be secured via encryption.
Recently the security researchers at Midnight Blue in the Netherlands have discovered a collection of five vulnerabilities collectively called "TETRA:BURST" that apply to almost every TETRA network in the world. These two most critical vulnerabilities allow TETRA to be easily decrypted by consumer hardware.
The first critical vulnerability is designated CVE-2022-24401 is described as decryption oracle attack.
The Air Interface Encryption (AIE) keystream generator relies on the network time, which is publicly broadcast in an unauthenticated manner. This allows for decryption oracle attacks.
The second vulnerability CVE-2022-24402 notes that a backdoor has been built into TEA1 encrypted TETRA, which allows for a very easy brute force decryption.
The TEA1 algorithm has a backdoor that reduces the original 80-bit key to a key size which is trivially brute-forceable on consumer hardware in minutes.
Midnight Blue are due to release more technical details about the vulnerabilities on August 9 during the BlackHat security conference. Due to the sensitivity of the findings, the team have also held back on their findings for over 1.5 years, notifying as many affected parties as possible, and releasing recommended mitigations. It's unclear at the moment how many TETRA providers have implemented mitigations already.
Below is a demonstration of the TEA1 CVE-2022-24402 attack on TETRA, and if you are interested the Midnight Blue YouTube channel also contains a video demonstration for the CVE-2022-24401 decryption oracle attack.
Demo: TETRA TEA1 backdoor vulnerability (CVE-2022-24402)
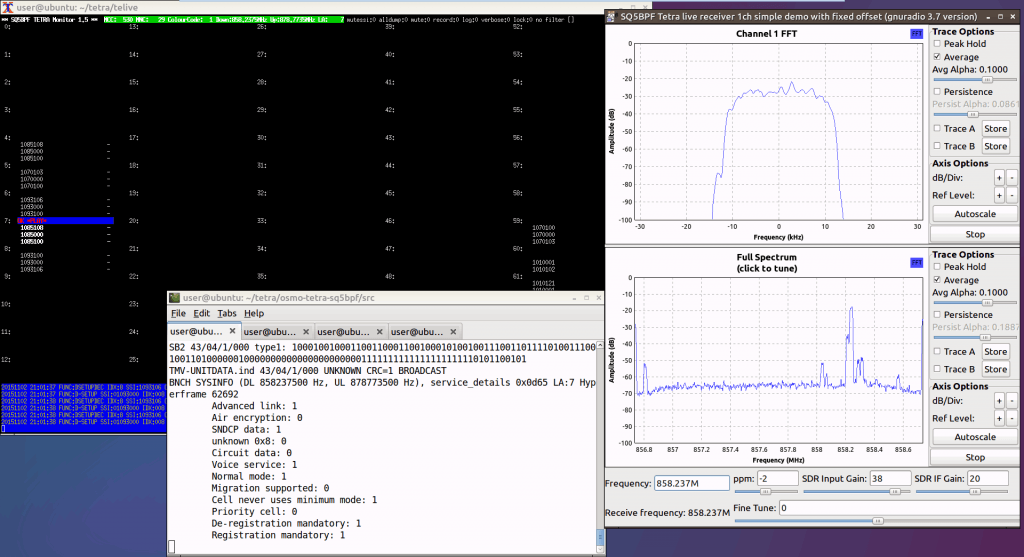
Currently, it is possible to decode unencrypted TETRA using an RTL-SDR with software like TETRA-Kit, SDR# TETRA Plugin, WinTelive, and Telive. In the video the research team appear to use Telive as part of their work.
We also note that in the past we've run several stories about Dejan Ornig, a Slovenian researcher who was almost jailed because of his research into TETRA. Dejan's research was much simpler, as he simply discovered that many Police radios in his country had authentication turned off, when it should have been on.