Loading...

Today we’re excited to announce Cloudflare’s partnership with Jamf to extend Cloudflare’s Zero Trust Solutions to Jamf customers. This unique offering will enable Jamf customers to easily implement network Data Loss Prevention (DLP), Remote Browser Isolation (RBI), and SaaS Tenancy Controls from Cloudflare to prevent sensitive data loss from their Apple devices.
Jamf is a leader in protecting Apple devices and ensures secure, consumer-simple technology for 71,000+ businesses, schools and hospitals. Today Jamf manages ~30 million Apple devices with MDM, and our partnership extends powerful policy capabilities into the network.
“One of the most unforgettable lines I’ve heard from an enterprise customer is their belief that ‘Apple devices are like walking USB sticks that leave through the business’s front door every day.’ It doesn’t have to be that way! We are on a mission at Jamf to help our customers achieve the security and compliance controls they need to confidently support Apple devices at scale in their complex environments. While we are doing everything we can to reach this future, we can’t do it alone. I’m thrilled to be partnering with Cloudflare to deliver a set of enterprise-grade compliance controls in a novel way that leverages our combined next-generation cloud-native infrastructures to deliver a fast, highly-available end user experience.”
- Matt Vlasach, VP Product, Jamf
Integrated access with Jamf Security Cloud
Jamf’s Apple-first Zero Trust Network Access (ZTNA) agent, Jamf Trust, is designed to seamlessly deploy via Jamf Pro with rich identity, endpoint security, and networking integrations that span the Jamf platform. All of these components work together as part of Jamf Security Cloud to protect laptop and mobile endpoints from network and endpoint threats while enabling fast, least-privilege access to company resources in the cloud or behind the firewall.
Through this partnership, Jamf customers can now dynamically steer select traffic to Cloudflare’s network using Magic WAN. This enables customers to unlock rich DLP capabilities, Remote Browser Isolation, and SaaS Tenancy Controls in a cloud-first, cloud-native architecture that works great on Apple devices.
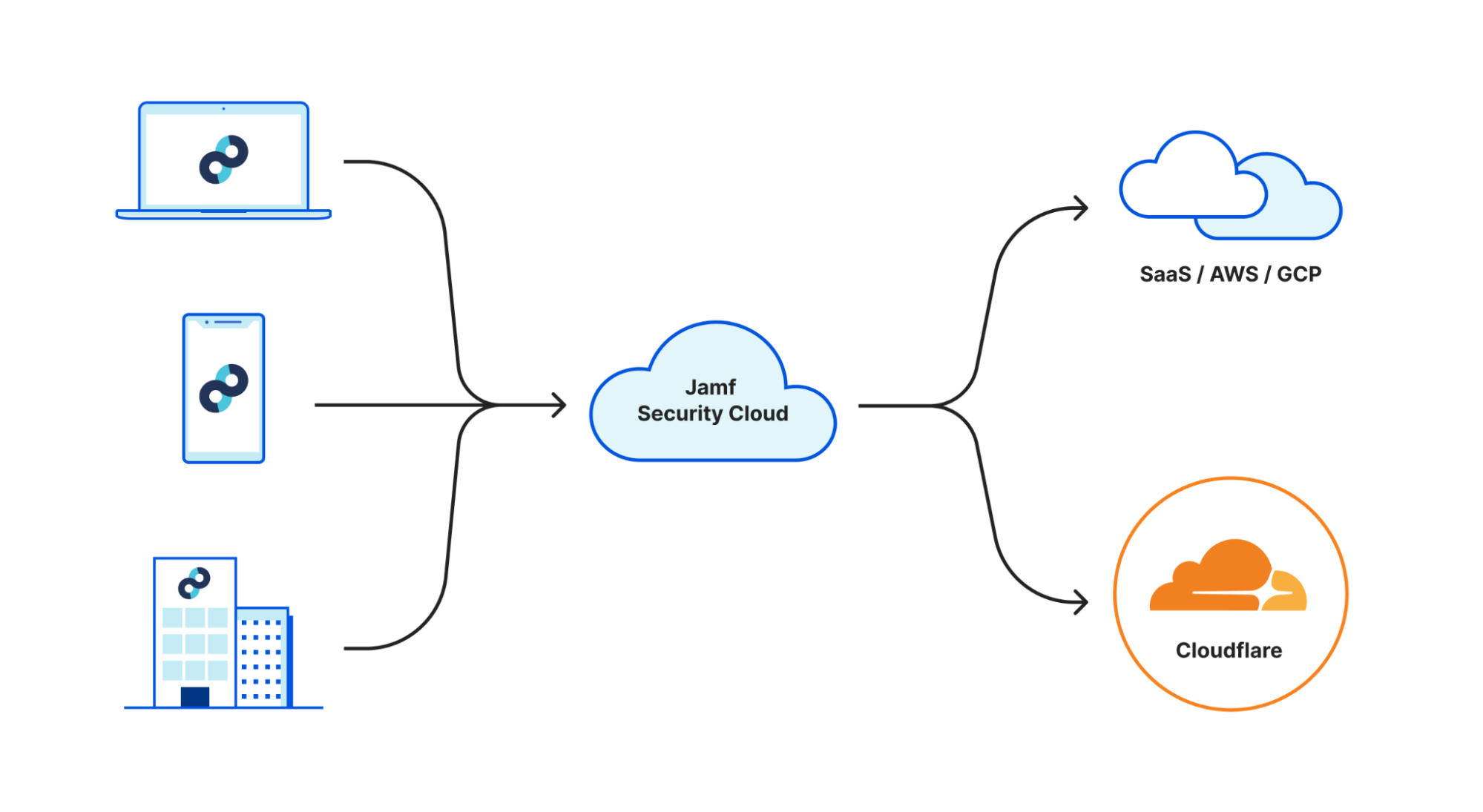
Seamless integration to protect company data
While content inspection policies can be created, they cannot be applied to HTTPS traffic since content payloads are encrypted. This is a problem for organizations as it is common for sensitive data to live within an encrypted payload and bypass IT content inspection policies. 99.7% of all requests use HTTPS today and the usage has been seeing a steady increase.
To address this visibility gap, organizations can decrypt packets using HTTPS inspection. With Cloudflare Gateway, SSL/TLS decryption can be performed to inspect HTTPS traffic for security risks. When TLS decryption is enabled, Gateway will decrypt all traffic sent over HTTPS, apply your HTTP policies, and then re-encrypt the request with a user-side certificate. Jamf is able to seamlessly enable this process on managed devices.
Protect sensitive data with Data Loss Prevention
With the corporate network and employees being boundless, it is harder than ever to keep data secure. Sensitive data such as customer credit card information, social security numbers, API tokens, or confidential Microsoft Office documents are easily shared beyond your network boundary, intentionally or otherwise. This is made worse as attackers are increasingly tricking well-intentioned employees to inadvertently share sensitive data with hackers. Such data leaks are not uncommon and usually result in costly reputational and compliance damages.
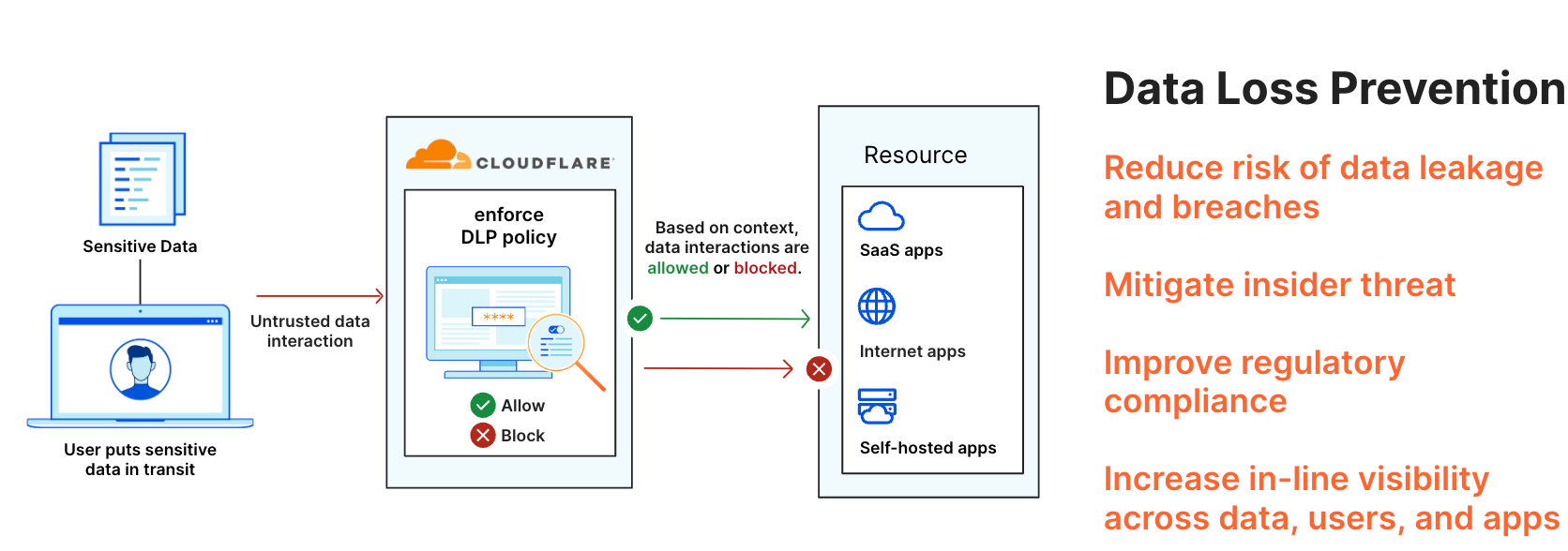
Cloudflare’s Data Loss Prevention (DLP) allows for policies to be built in with ease to keep highly sensitive data secure. Cloudflare also provides predefined profiles for detecting financial information such as credit card numbers and national identifiers such as social security numbers or tax file numbers in addition to credentials and secrets such as GCP keys, AWS keys, Azure API keys, and SSH keys. On top of that, Cloudflare DLP allows for the creation of expanded regex profiles to detect custom keywords and phrases.
Steps to implement Cloudflare DLP with Jamf:
- In Jamf’s Security Cloud portal, configure a Magic WAN interconnect to your Cloudflare account.
- Create an access policy to route traffic for DLP inspection via your Cloudflare Magic WAN interconnect
- Traffic may be matched by hostname, domain, or IP address/CIDR block
- To route all traffic for inspection, define
*for hostnames and0.0.0.0/0for IPs in the access policy. Note: this will be treated as the “gateway of last resort”, with other access policies matching first. - Optionally, enable “Restrict access when Jamf Trust is disabled” under the Security tab of the policy to prevent bypassing of DLP inspection for these resources.
- Configure a DLP policy in your Cloudflare One portal.
- In Jamf Pro, create a new Configuration Profile with the Cloudflare Gateway Root Certificate Authority and scope it to your target Apple devices.
Using Activation Profiles in Jamf Security Cloud, deploy Jamf Trust and supporting mobile configuration profiles to your end users to enable access to organization resources while enforcing DLP policies.
Isolate browser threats to thwart known and zero-day exploits
Firewalls, VPNs, network access controls help protect against attacks directed at internal networks. However, many attackers focus on exploiting web browsers due to their ubiquity and frequent use. Remote Browser Isolation aims to reduce an organization’s risk exposure by allowing access to any destination on the Internet, but protecting endpoints by using an isolated cloud environment to load content.
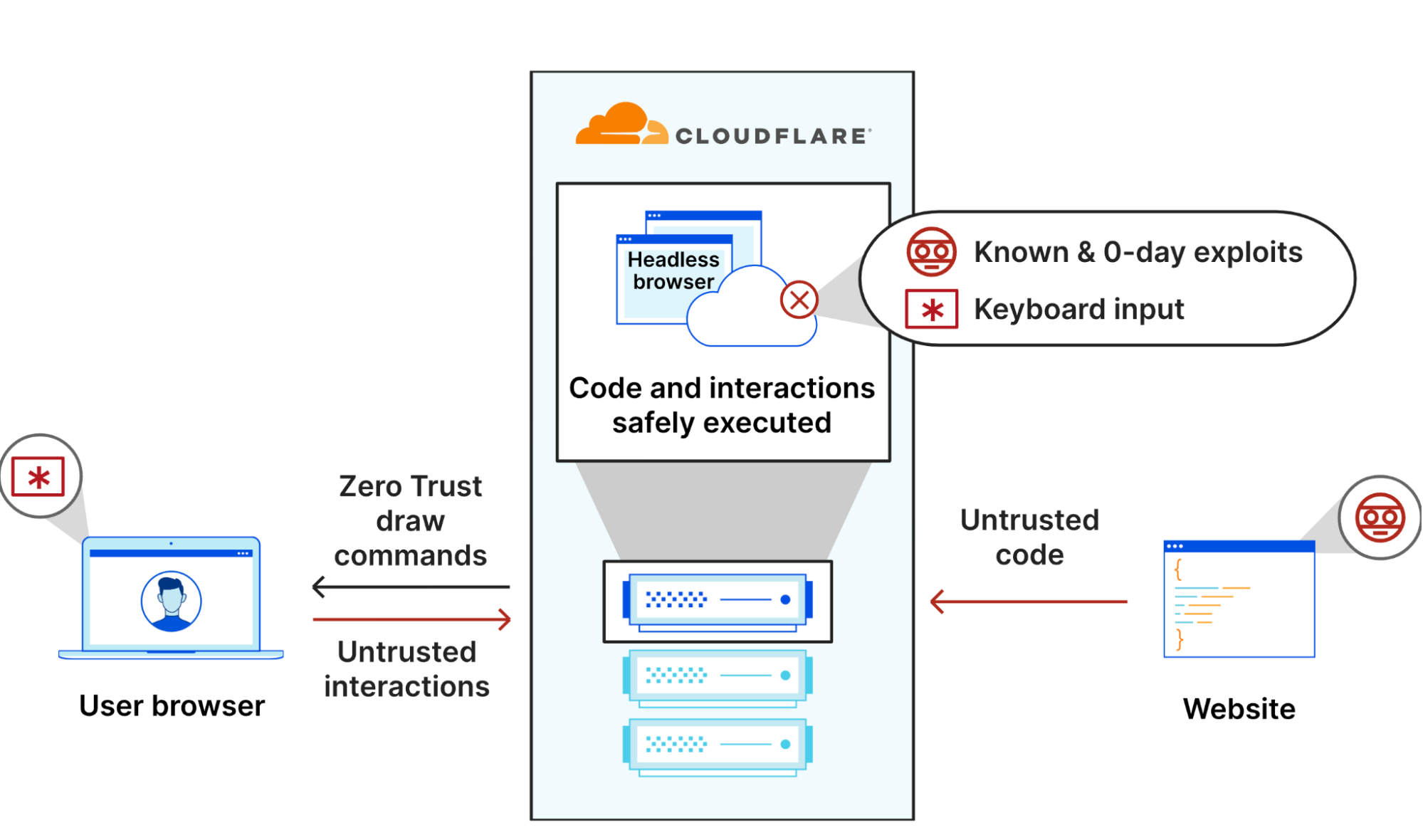
This works by actually loading web pages – and all of their potentially dangerous scripts and code – in a headless Chromium browser in Cloudflare’s global network. The visual and interactive elements that are loaded remotely are sent back to the user’s device via “draw” commands, essentially rendering visual objects in the browser as the user would expect. If a known or zero-day exploit is loaded, the user’s device is completely protected.
Another benefit of Remote Browser Isolation is granular, browser-specific Data Loss Prevention controls. This includes restricting download, upload, copy-paste, keyboard input, and printing functions on all or specific websites.
Steps to implement Remote Browser Isolation:
- In Jamf’s Security Cloud portal, configure a Magic WAN interconnect to your Cloudflare account.
- Configure an Access policy and specify the domains or hostnames to be rendered via remote browser isolation in the Cloudflare network
- Be sure to include *.browser.run as a hostname in your Jamf access policy.
- Configure the access policy to route traffic via the Cloudflare MagicWAN interconnect you configured above.
- If you would like to subject all traffic that doesn't match another Jamf Access Policy, define * as the hostname to route all remaining traffic to RBI.
- Optionally, enable “Restrict access when Jamf Trust is disabled” under the Security tab of the policy to prevent bypassing of RBI routing for the defined destinations.
- In your Cloudflare One console, enable Non-identity on-ramps in your Cloudflare One portal.
- Configure a Remote Browser Isolation policy in your Cloudflare One portal.
- In Jamf Pro, create a new Configuration Profile with the Cloudflare Gateway Root Certificate Authority and scope it to your target Apple devices.
Using Activation Profiles in Jamf Security Cloud, deploy Jamf Trust and supporting mobile configuration profiles to your end users to enable access to organization resources while enforcing remote browser isolation routing.
Safeguarding data with SaaS Tenancy Control for cloud services
Companies often rely on platforms like Google Workspace or Microsoft 365 for business collaboration and productivity, while individuals use these services for their personal use.
Allowing users to access these cloud services with both business and personal credentials from the same corporate endpoint poses a significant risk for unauthorized data access and loss. Imagine a scenario where an employee can log in into the corporate account of a SaaS application, download sensitive files, and then login into their personal account on the same company device to upload the stolen files to their personal SaaS application account.
Cloudflare's Gateway HTTP policies provide SaaS Tenancy Control to ensure that users can only log in to admin-defined SaaS provider tenants with their enterprise credentials, effectively blocking login ability to personal accounts or other business tenants within the defined SaaS provider.
Jamf's Access Policies serve as the initial assessment, determining if the users are authorized for the targeted cloud application and if they are requesting access from a company-sanctioned device.
Cloudflare's Gateway HTTP policy then processes the requests forwarded from Jamf to define the domains that are permitted to log in to that SaaS provider.
Steps to implement SaaS Tenancy Control:
- In Jamf’s Security Cloud portal, configure a Magic WAN interconnect to your Cloudflare account.
- Configure one or more Access policies that define the SaaS providers for which you would like to enable tenant controls. Use the below pre-defined SaaS app access policy templates for the respective SaaS provider:
- “Microsoft Authentication” for Microsoft 365
- “Google Apps” for Google Workspace
- “Dropbox” for Dropbox and Dropbox for Business
- “Slack” for Slack
- To ensure these policies are enforced on any network, enable “Restrict access when Jamf Trust is disabled” under the Security tab of the policy to prevent bypassing of these tenancy controls.
- Configure SaaS Tenant Control in your Cloudflare One portal.
- In Jamf Pro, create a new Configuration Profile with the Cloudflare Gateway Root Certificate Authority and scope it to your target Apple devices.
- Using Activation Profiles in Jamf Security Cloud, deploy Jamf Trust and supporting mobile configuration profiles to your end users to enable access to organization resources while enforcing remote browser isolation routing.
How to get started
If you are a Cloudflare customer and are interested in using this integration, please reach out to your account team with your questions and feedback.
If you are new to Cloudflare or Jamf and interested in using this integration with the Cloudflare Zero Trust product suite, please fill up this form and someone from our team will contact you.
We protect entire corporate networks, help customers build Internet-scale applications efficiently, accelerate any website or Internet application, ward off DDoS attacks, keep hackers at bay, and can help you on your journey to Zero Trust.
Visit 1.1.1.1 from any device to get started with our free app that makes your Internet faster and safer.
To learn more about our mission to help build a better Internet, start here. If you're looking for a new career direction, check out our open positions.


