2023-6-20 22:20:55 Author: www.sentinelone.com(查看原文) 阅读量:29 收藏
A Russian-speaking hacker has been making headlines recently after promoting a tool that the threat actor claims can bypass EDR and AV tools. The so-called ‘Terminator’ tool is said to be able to kill processes belonging to “all AVs/EDRs/XDRs”, which if used in conjunction with other malware, could allow threat actors to breach defenses. SentinelOne customers are protected from the Terminator EDR tool.
In this post, we take a look at how the tool works and how organizations can stay protected from it.

What is Terminator EDR Killer?
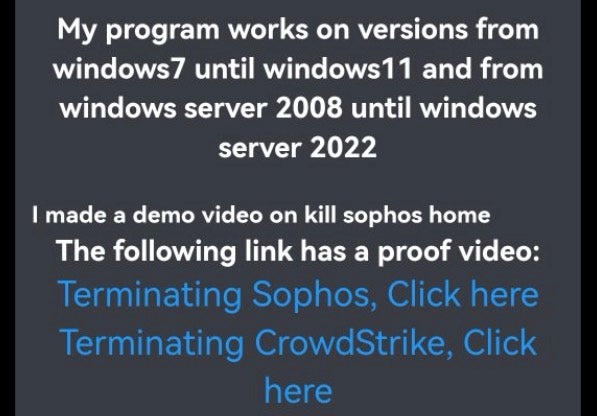
Late last month, a threat actor using the pseudonym “Spyboy” began promoting a malicious tool for sale on a Russian hacking platform, offering the tool for sale at prices ranging between $300 for a specific AV bypass and $3000 for a so-called “all-in-one” EDR killer.
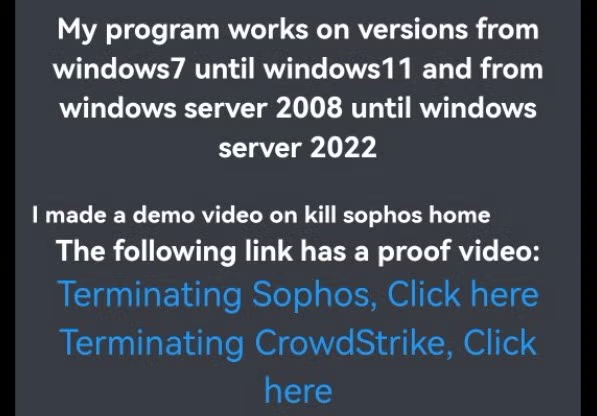
The threat actor’s videos demonstrating the tools on Sophos and CrowdStrike solutions were widely shared across social media, raising concerns among enterprise security teams that their organizations were at risk.
How the Terminator Tool Works
Terminator utilizes the Bring Your Own Vulnerable Driver (BYOVD) attack technique, which involves threat actors deploying drivers that are legitimately signed and can be successfully loaded into Windows systems.
However, these drivers have vulnerabilities that grant attackers the ability to execute attacker-provided code in kernel context. This puts the attackers in a privileged position, enabling them to circumvent the limitations imposed by the operating system on user processes. The consistent use of the BYOVD technique by threat actors has been observed over the past several years, leading to heightened awareness within the information security community regarding its existence and implications.
Terminator uses the BYOVD technique by deploying and loading vulnerable versions of Zemana anti-malware kernel drivers. This enables the execution of attacker-provided malicious code in kernel mode, thereby granting attackers the capability to terminate any system or user processes, including those associated with detection mechanisms.
SentinelOne Customers Protected
The SentinelOne Agent detects the execution of known Terminator samples, and we continue to monitor this malware family closely.
Organizations not protected by SentinelOne are advised to review the indicators of compromise below.
Indicators of Compromise
SHA1
16d7ecf09fc98798a6170e4cef2745e0bee3f5c7
3b8ddf860861cc4040dea2d2d09f80582547d105
628e63caf72c29042e162f5f7570105d2108e3c2
8dd52bfea92cbd91a042939a9cad69fdb666dfa3
8f4b79b8026da7f966d38a8ba494c113c5e3894b
a3d612a5ea3439ba72157bd96e390070bdddbbf3
a42018caa7243c54ecec35982790d96f38af90ea
adc5510dd775a4e846aba9fde84b5984d33768b4
b99a5396094b6b20cea72fbf0c0083030155f74e
c0d19461eb48b2bb66c0d2835370f491b35d24d2
c83075a691401c015566eff8b0d06c42410a9cbb
ce42d6114fef0a42aee5866c68d0a31170bb8fa7
db361424c040833576f1d7b3ee65005de0118227
dd4cd182192b43d4105786ba87f55a036ec45ef2
如有侵权请联系:admin#unsafe.sh