Executive SummaryOn May 31, 2023-6-7 05:30:8 Author: unit42.paloaltonetworks.com(查看原文) 阅读量:105 收藏

Executive Summary
On May 31, Progress Software posted a notification alerting customers of a critical Structured Query Language injection (SQLi) vulnerability (CVE-2023-34362) in their MOVEit Transfer product. MOVEit Transfer is a managed file transfer (MFT) application intended to provide secure collaboration and automated file transfers of sensitive data.
In all cases the vulnerability was being exploited to upload a web shell onto the MOVEit Transfer server. The web shell also allowed threat actors to enumerate files and folders on the MOVEit Transfer server, read configuration information, download files, and create or delete MOVEit server user accounts.
Unit 42 Incident Response has several ongoing investigations where the initial point of compromise appears to be the exploitation of CVE-2023-34362. Although details are still being uncovered, the earliest evidence of exploitation is May 27.
We will provide unique indicators of compromise (IoCs) observed by Unit 42, as well as IoCs we have observed that have also been reported by other researchers, to highlight the reuse of infrastructure across victim organizations.
Palo Alto Networks Xpanse indicates there are at least 2,377 MOVEit servers exposing HTTP/HTTPs traffic over ports 80 and 443. This does not indicate whether the servers have been patched and it does not include servers running the web service over non-standard ports.
Progress Software has provided mitigation guidance that all MOVEit Transfer customers should seriously consider following.
Palo Alto Networks customers receive protections from and mitigations for CVE-2023-34362 in the following ways:
- Next-Generation Firewall with the Advanced Threat Prevention security subscription can help block the associated web shell.
- Advanced URL Filtering can block known IoCs.
- A Cortex XSOAR response pack and playbook can automate the mitigation process.
- Cortex XDR and XSIAM agents help protect against post-exploitation activities described in this blog using Behavioral Threat Protection, Anti-Webshell Protection and multiple additional security modules.
- Cortex Analytics has multiple detection models that help detect post-exploitation activities, with other relevant coverage by the Identity Analytics and ITDR modules.
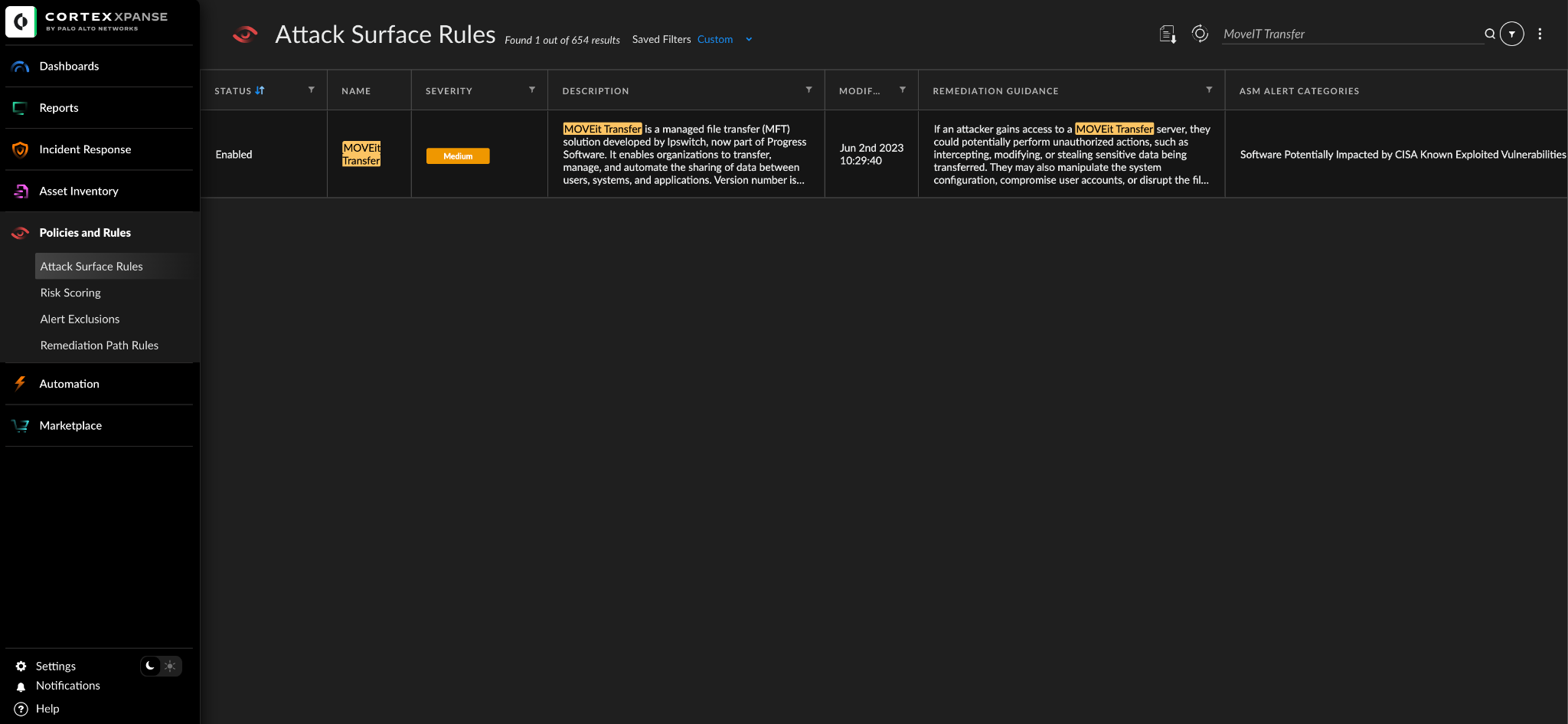
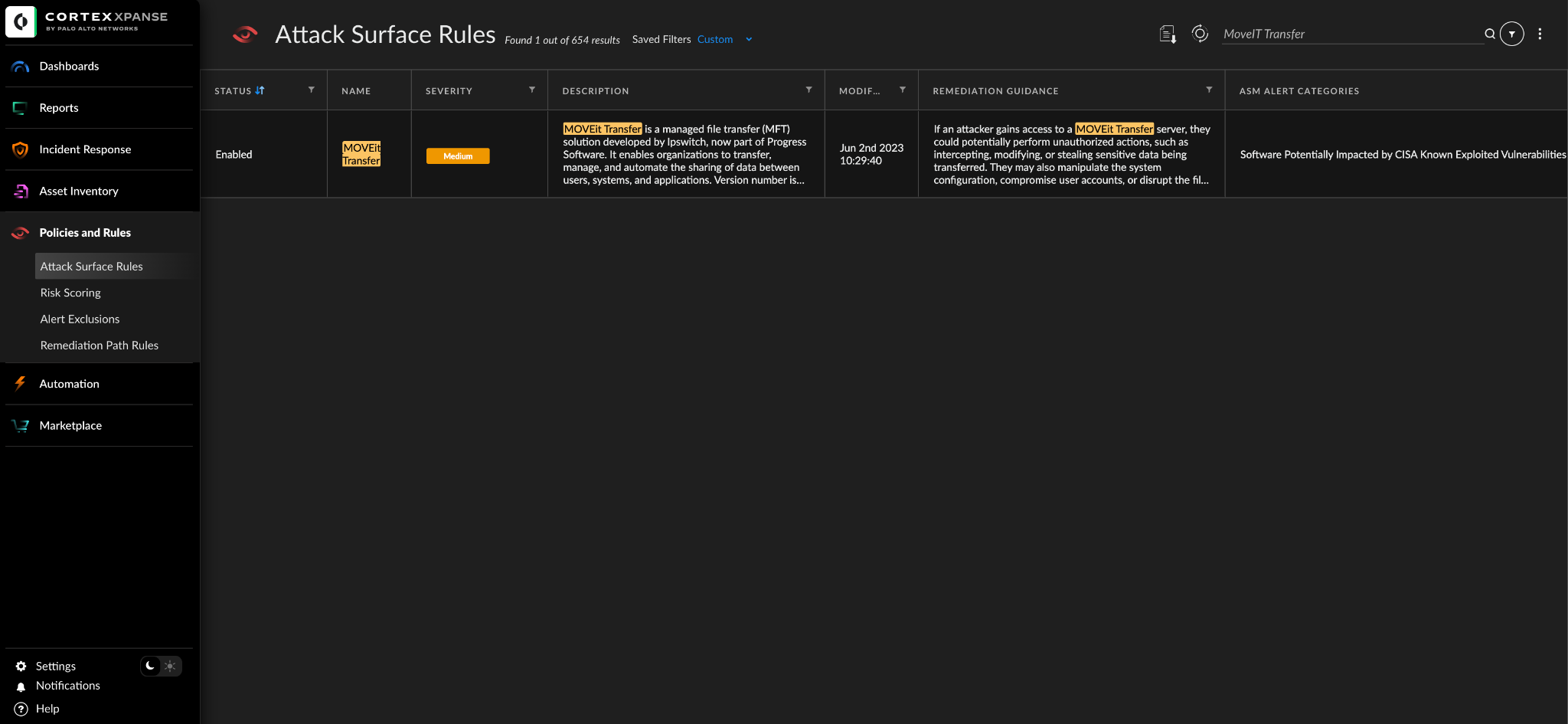
- Cortex Xpanse customers can identify external facing instances of the application through the “MOVEit Transfer” attack surface rule.
- XQL queries provided below can be used with Cortex XDR to help track attempts to exploit this CVE.
- Organizations can engage the Unit 42 Incident Response team for specific assistance with this threat and others.
| Vulnerabilities Discussed | CVE-2023-34362 |
Table of Contents
Details of the Vulnerability
Current Scope of the Attack
Interim Guidance
Unit 42 Managed Threat Hunting Queries
Conclusion
Palo Alto Networks Product Protections for CVE-2023-34362
Next-Generation Firewalls and Prisma Access With Advanced Threat Prevention
Cloud-Delivered Security Services for the Next-Generation Firewall
Cortex XSOAR
Cortex XDR and XSIAM
Cortex Xpanse
Indicators of Compromise
Details of the Vulnerability
On May 31, Progress Software posted a notification alerting customers of a critical vulnerability (CVE-2023-34362) in their MOVEit Transfer product. CVE-2023-34362 is a SQLi vulnerability that enables threat actors the ability to potentially elevate privileges, view and download data from the database server, and potentially enable the theft of Azure system settings and the associated key and containers.
Both Huntress and Mandiant have written blogs in the days preceding the CVE assignment, detailing their observations of the ongoing campaign to exploit this vulnerability. Mandiant has identified “multiple cases where large volumes of files have been stolen from victims' MOVEit transfer systems.” So far our internal investigation findings are consistent with both those of Huntress and Mandiant.
Unit 42 researchers have seen the web shell in the D:\MOVEitDMZ\wwwroot\human2.aspx directory, which differs slightly from the directory reported by Huntress. We’ve also seen the precompiled .NET DLLs in the C:\Windows\Temp directory.
For example, we’ve observed the file path C:\Windows\Temp\erymbsqv\erymbsqv.dll, where the random characters of the folder and file names are dynamically generated and different across compromised hosts. Additional indicators of compromise (IoCs) not mentioned in the Progress, Huntress or Mandiant blogs are included below.
Note: The IoCs below do contain IP addresses mentioned in the Progress, Huntress and Mandiant blogs because we think it’s important to highlight the reuse of infrastructure across victim organizations.
Current Scope of the Attack
Unit 42 Incident Response has several ongoing investigations where the initial point of compromise appears to be the exploitation of CVE-2023-34362. Although details are still being uncovered, the earliest evidence of exploitation is May 27.
Mandiant has also reported they have several ongoing investigations where exploitation of CVE-2023-34362 was responsible for the initial compromise and deployment of web shells as early as May 27. Huntress reported in their blog that they had one client affected.
Mandiant and Microsoft have both reported they believe there is a likelihood that the attacks are attributed to the Cl0p ransomware gang. Organizations that have been compromised can likely expect extortion communications to follow in the near future.
Palo Alto Networks Xpanse indicates there are at least 2,377 MOVEit servers exposing HTTP/HTTPs traffic over ports 80 and 443. This does not indicate whether the servers have been patched and does not include servers running the web service over non-standard ports.
Interim Guidance
Below is a summary of the mitigations that Progress Software recommends. Please refer to the linked blog for a detailed list and explanation of the mitigation process.
- Disable all HTTP and HTTPs traffic to the MOVEit Transfer host.
- Review, delete and reset any unauthorized files and user accounts.
- Apply the relevant patch.
- Verify all malicious files and user accounts have been deleted/reset.
- Reset the service account credentials again.
- Re-enable all HTTP and HTTPs traffic to the MOVEit Transfer environment
- Continually monitor network, endpoints and logs for IoCs reported in relation to the current campaign.
The Unit 42 team also recommends that any organization that did have the MOVEit Transfer web interface exposed should assume it has been potentially compromised. We strongly recommend that affected organizations perform a forensic analysis of the server to ensure it was not compromised.
Unit 42 Managed Threat Hunting Queries
The Unit 42 Managed Threat Hunting team continues to track any attempts to exploit this CVE across our customers, using Cortex XDR and the XQL queries below. Cortex XDR customers can also use these XQL queries to search for signs of exploitation.
// Description: Look for MOVEit IIS process writing an aspx file to disk. Review the results for possible web shells. config case_sensitive = false | dataset = xdr_data | filter event_type = ENUM.FILE AND event_sub_type in (ENUM.FILE_WRITE,ENUM.FILE_CREATE_NEW, ENUM.FILE_RENAME) | filter actor_process_image_name = "w3wp.exe" AND actor_process_command_line contains "moveit" and action_file_extension in ("aspx") | fields _time, agent_hostname, event_type, event_sub_type, actor_process_image_path, actor_process_command_line, action_file_path, action_file_sha256 |
// Description: Look for MOVEit IIS worker process spawning child processes. Review the results for suspicious commands. config case_sensitive = false | dataset = xdr_data | filter event_type = ENUM.PROCESS AND event_sub_type = ENUM.PROCESS_START | filter actor_process_image_name = "w3wp.exe" AND actor_process_command_line contains "moveit" | fields _time, agent_hostname, event_type, event_sub_type, actor_process_image_path, actor_process_command_line, action_process_image_path, action_process_image_command_line, action_process_image_sha256 |
Conclusion
Although the number of exposed servers is relatively small, Unit 42 recommends organizations using MOVEit Transfer follow Progress Software’s mitigation guidance immediately. There are already reports of CVE-2023-34362 being exploited in the wild and there will likely be reports of more organizations who are affected in the near future.
Palo Alto Networks has shared our findings, including file samples and indicators of compromise, with our fellow Cyber Threat Alliance (CTA) members. CTA members use this intelligence to rapidly deploy protections to their customers and to systematically disrupt malicious cyber actors. Learn more about the Cyber Threat Alliance.
Palo Alto Networks Product Protections for CVE-2023-34362
Palo Alto Networks customers can leverage a variety of product protections and updates to identify and defend against this threat.
If you think you may have been compromised or have an urgent matter, get in touch with the Unit 42 Incident Response team or call:
- North America Toll-Free: 866.486.4842 (866.4.UNIT42)
- EMEA: +31.20.299.3130
- APAC: +65.6983.8730
- Japan: +81.50.1790.0200
Next-Generation Firewalls and Prisma Access With Advanced Threat Prevention
- Next-Generation Firewall with the Advanced Threat Prevention security subscription can help block the associated web shell via the following Threat Prevention signature: 81868
Cloud-Delivered Security Services for the Next-Generation Firewall
Known IoCs are marked as malicious by Advanced URL Filtering.
Cortex XSOAR
Cortex XSOAR has released a response pack and playbook for CVE-2023-34362 to help automate and speed the mitigation process.
This playbook automates the following tasks:
- Collection of all relevant IoCs and detection signatures
- Running investigation queries to detect possible exploitation attempts
- Blocking IoCs
- Following the mitigation published for this vulnerability
Cortex XDR and XSIAM
Cortex XDR and XSIAM agents help protect against post-exploitation activities described in this blog using Behavioral Threat Protection, Anti-Webshell Protection and multiple additional security modules. Additionally, Cortex Analytics has multiple detection models that help detect post-exploitation activities, with other relevant coverage by the Identity Analytics and Identity Threat Detection and Response (ITDR) modules.
Cortex Xpanse
Cortex Xpanse customers can identify external facing instances of the application through the “MOVEit Transfer” attack surface rule. The rule is available to all customers with a default state of “On.”
Indicators of Compromise
Paths:
- D:\MOVEitDMZ\wwwroot\human2.aspx
- E:\MOVEitTransfer\wwwroot\human2.aspx
- C:\Windows\Temp\erymbsqv\erymbsqv.dll
human2.aspx
- c82059564d6e7a6f56d3b1597cdfe98dfc4e30a2050024bd744f12a3ef237bb5
- 24c7fae1b7c02ebd84cc3c78553fb3a68d0466575abea4c92b2f792b47c41ef3
- de4ad0052c273649e0aca573e30c55576f5c1de7d144d1d27b5d4808b99619cd
- 7a8f53c4143bacd2104ccd07a6be68d76cda1a6985b8573b7735858a542178bb
- 87ebfaf36fc7031bec477c70a86cb746811264f530d8af419767b9755e2b43e3
- 3ff0719da7991a38f508e72e32412a1ee498241bf84f65e973d6e93dc8fd1f66
- f994063b9fea6e4b401ee542f6b6d8d6d3b9e5082b5313adbd02c55dc6b4feb7
- bd45234763ef62f05d14b78c6497ed90706a271fad3b16a4ee6d99d178beedf3
- 3ff0719da7991a38f508e72e32412a1ee498241bf84f65e973d6e93dc8fd1f66
- f994063b9fea6e4b401ee542f6b6d8d6d3b9e5082b5313adbd02c55dc6b4feb7
- ba2cf96fc5884cd69ecfe5d73f872958159a12b02ca610223f089ee0b6c3d25d
- 6e1d3b5fcb4de48e1e06a68686817d13533f9740e315f4378bb5b9ef1fd1c7a9
- 2931994f3bde59c3d9da53e0062e4d993dc6fc655a1bd325e90af6dc494ed1fa
- f3543cd16de13214124bd7c91033c3cd3bbcf6587871257e699fd89df96fd86f
VirusTotal Livehunt human2.aspx and h2.aspx
- e8012a15b6f6b404a33f293205b602ece486d01337b8b3ec331cd99ccadb562e
- 2413b5d0750c23b07999ec33a5b4930be224b661aaf290a0118db803f31acbc5
- d477ec94e522b8d741f46b2c00291da05c72d21c359244ccb1c211c12b635899
- 929bf317a41b187cf17f6958c5364f9c5352003edca78a75ee33b43894876c62
- b9a0baf82feb08e42fa6ca53e9ec379e79fbe8362a7dac6150eb39c2d33d94ad
- 4359aead416b1b2df8ad9e53c497806403a2253b7e13c03317fc08ad3b0b95bf
- ea433739fb708f5d25c937925e499c8d2228bf245653ee89a6f3d26a5fd00b7a
- d49cf23d83b2743c573ba383bf6f3c28da41ac5f745cde41ef8cd1344528c195
- 387cee566aedbafa8c114ed1c6b98d8b9b65e9f178cf2f6ae2f5ac441082747a
- a1269294254e958e0e58fc0fe887ebbc4201d5c266557f09c3f37542bd6d53d7
- cf23ea0d63b4c4c348865cefd70c35727ea8c82ba86d56635e488d816e60ea45
- f0d85b65b9f6942c75271209138ab24a73da29a06bc6cc4faeddcb825058c09d
- c77438e8657518221613fbce451c664a75f05beea2184a3ae67f30ea71d34f37
- daaa102d82550f97642887514093c98ccd51735e025995c2cc14718330a856f4
- 3ab73ea9aebf271e5f3ed701286701d0be688bf7ad4fb276cb4fbe35c8af8409
- 93137272f3654d56b9ce63bec2e40dd816c82fb6bad9985bed477f17999a47db
- 5b566de1aa4b2f79f579cdac6283b33e98fdc8c1cfa6211a787f8156848d67ff
- 3a977446ed70b02864ef8cfa3135d8b134c93ef868a4cc0aa5d3c2a74545725b
- 348e435196dd795e1ec31169bd111c7ec964e5a6ab525a562b17f10de0ab031d
- 0ea05169d111415903a1098110c34cdbbd390c23016cd4e179dd9ef507104495
- 9d1723777de67bc7e11678db800d2a32de3bcd6c40a629cd165e3f7bbace8ead
- b1c299a9fe6076f370178de7b808f36135df16c4e438ef645[3a39565ff2ec272
- 9e89d9f045664996067a05610ea2b0ad4f7f502f73d84321fb07861348fdc24a
- 6015fed13c5510bbb89b0a5302c8b95a5b811982ff6de9930725c4630ec4011d
- fe5f8388ccea7c548d587d1e2843921c038a9f4ddad3cb03f3aa8a45c29c6a2f
- 702421bcee1785d93271d311f0203da34cc936317e299575b06503945a6ea1e0
- c56bcb513248885673645ff1df44d3661a75cfacdce485535da898aa9ba320d4
- 3c0dbda8a5500367c22ca224919bfc87d725d890756222c8066933286f26494c
- bdd4fa8e97e5e6eaaac8d6178f1cf4c324b9c59fc276fd6b368e811b327ccf8b
IPs:
- 5.252.191[.]241
- 5.252.191[.]103
- 5.252.189[.]210
- 5.252.189[.]130
- 5.252.190[.]119
- 5.252.190[.]100
- 5.252.190[.]117
- 5.252.191[.]31
- 5.252.190[.]244
- 165.227.147[.]215
- 209.97.137[.]33
User Agents:
- Mozilla/5.0+(Windows+NT+10.0;+Win64;+x64)+AppleWebKit/537.36+(KHTML,+like+Gecko)+Chrome/113.0.0.0+Safari/537.36
- Mozilla/5.0+(Windows+NT+10.0;+Win64;+x64;+rv:109.0)+Gecko/20100101+Firefox/114.0
- Mozilla/5.0+(Windows+NT+10.0;+Win64;+x64)+AppleWebKit/537.36+(KHTML,+like+Gecko)+Chrome/105.0.5195.54+Safari/537.36
Get updates from
Palo Alto
Networks!
Sign up to receive the latest news, cyber threat intelligence and research from us
如有侵权请联系:admin#unsafe.sh